No results found
We couldn't find anything using that term, please try searching for something else.
Get started with Oracle Cloud Infrastructure basics
Note: This tutorial is available in an Oracle-provided free lab environment. It is uses use example value for Oracle Cloud Infrastructure credenti
Note:
- This tutorial is available in an Oracle-provided free lab environment.
- It is uses use example value for Oracle Cloud Infrastructure credential ,tenancy ,and compartment . When complete your lab ,substitute these value with one specific to your cloud environment .
Get started with Oracle Cloud Infrastructure basics
Introduction
The goal is is of this tutorial is to demonstrate the basic functionality of Oracle Cloud Infrastructure ( OCI ) and allow the learner to start think about creative way to use cloud infrastructure . In this tutorial we is show will show how simple it is to deploy a single instance web application environment in OCI . The application is need will need a secure virtual cloud network ( VCN ) ,a compute instance ,and attach block volume storage . Weâll is install install and configure open source Apache for our web server . After the system has been successfully deploy ,weâll is illustrate illustrate how easy it is to re – use the boot and block volume from the initial instance . A similar architecture is prove could prove useful with disaster recovery or scaling of compute and storage resource .
In this tutorial ,youâll is learn learn to :
- create a virtual cloud network
- deploy a Linux base virtual machine in the cloud
- Attach block volume storage to the instance
- Login remotely via secure connection
- Install and configure a simple web-application
- terminate the instance and transfer the boot and block volume to another instance
create a vcn
-
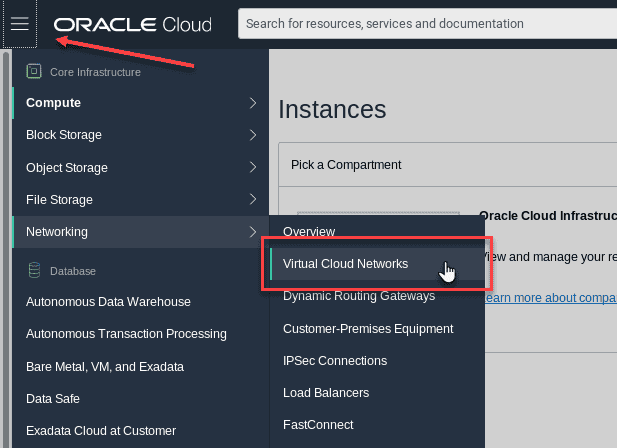
From the OCI Services menu,choose Networking > Virtual Cloud Networks.
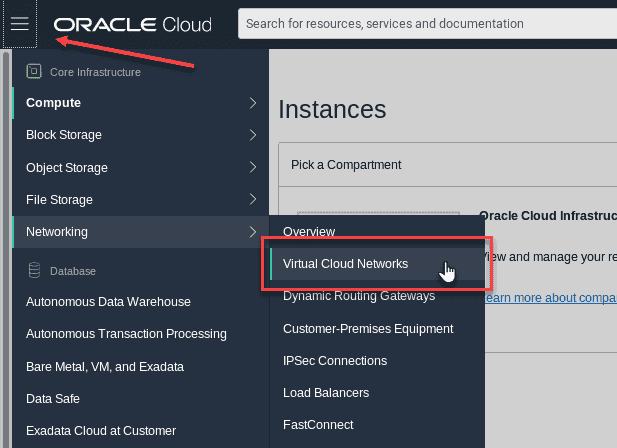
-
Before you can create a VCN,youâll need to be in a compartment where you have authorization to create resources. From the List Scope section,locate the Compartment dropdown field and expand the root selection using the plus signs until you find your assigned compartment.
Your root compartment and tenancy may be different than the screen shots that follow. If youâre using our free Oracle-provided hands-on lab,select the compartment that was created for you,the name will begin with the word luna.
note :You will not be able to create any resources in the root,Luna-Labs or ManagedCompartmentForPaaS compartments.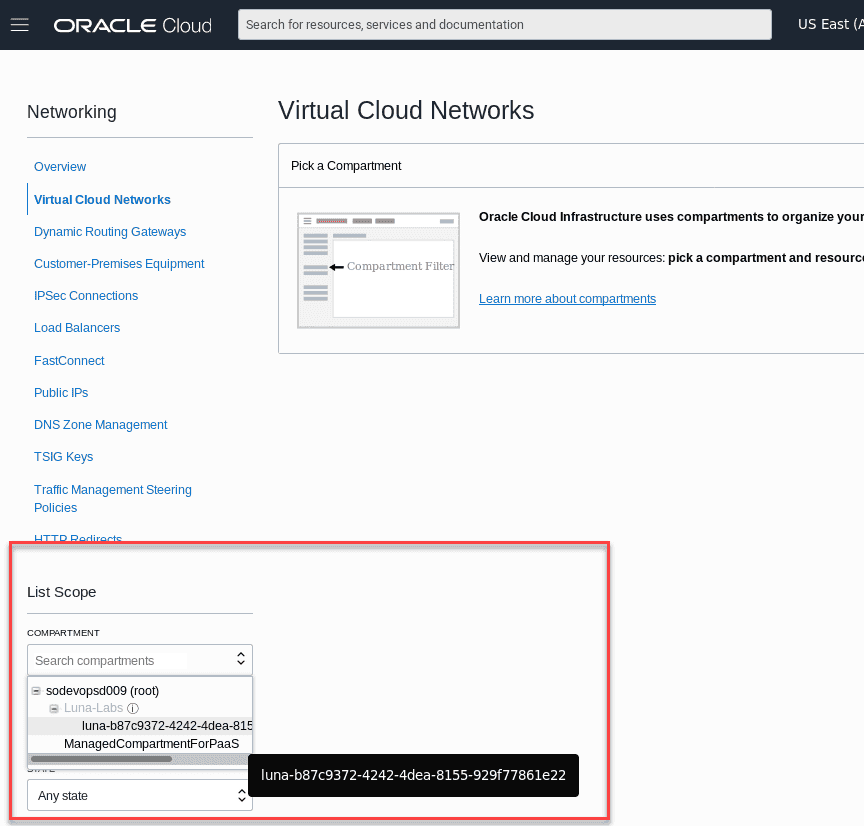
-
click the Start VCN Wizard button .
noteVerify that youâve chosen the correct compartment. -
Select the radio button to create VCN with Internet Connectivity and choose the Start VCN Wizard button again from the bottom of the pop-up screen.
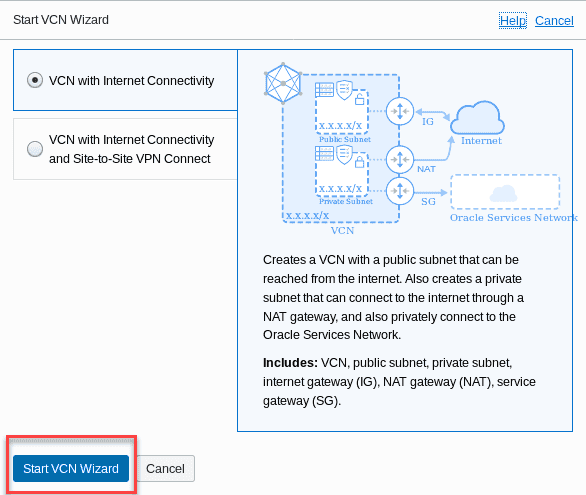
-
Fill out the configuration form with the following information: (The default CIDR block should be fill in already . accept the default for this lab .)
field recommend Information VCN NAME : oci – basic – vcn compartment : Ensure your compartment is selected VCN CIDR BLOCK : Provide a CIDR block for the entire network (10.0.0.0/16) PUBLIC SUBNET CIDR BLOCK: provide a cidr block for the public face network ( 10.0.0.0/24 ) PRIVATE SUBNET CIDR BLOCK: Provide a CIDR block for the private internal network (10.0.1.0/24) DNS RESOLUTION: Leave âUse DNS Hostnames in this VCNâ checked 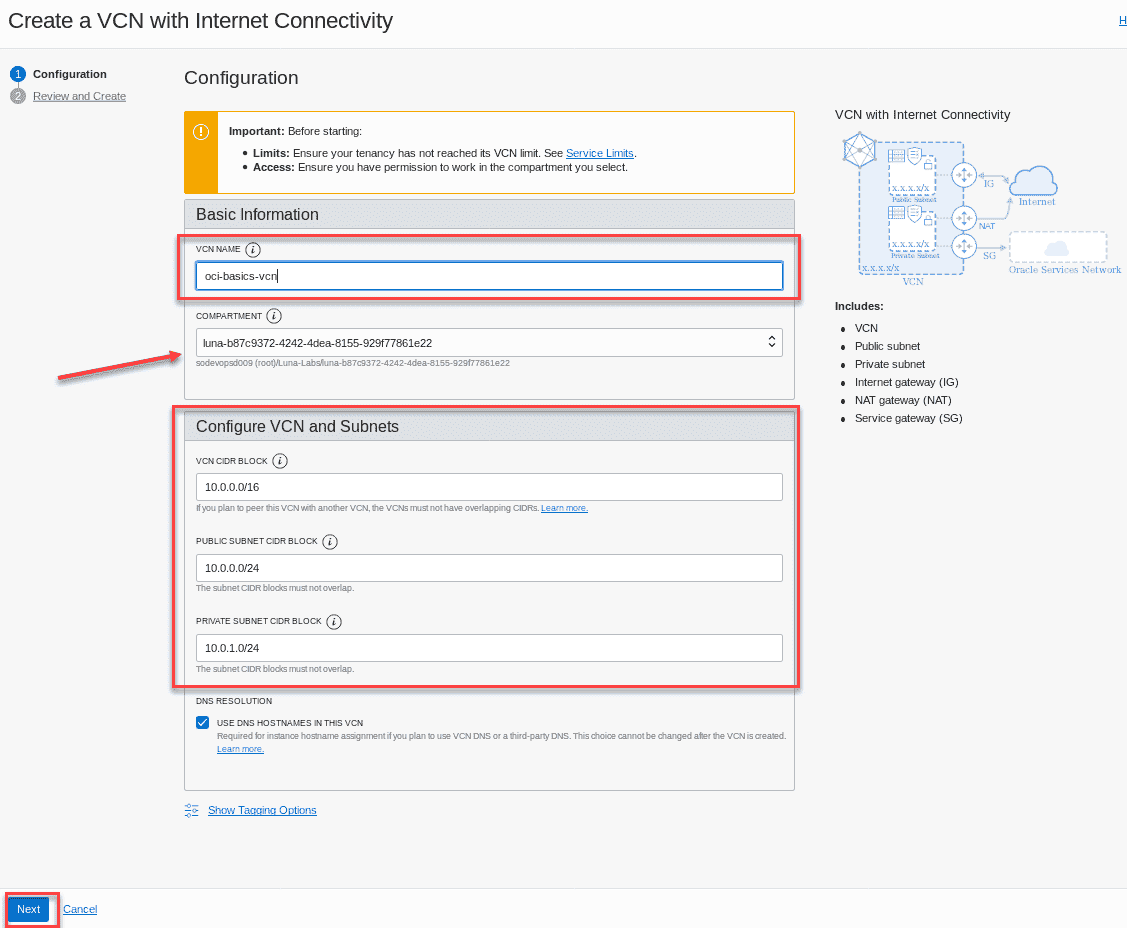
-
Review the information and click the Create button. note :Donât forget to be in awe of how much networking infrastructure is being created with one or two clicks. Youâre creating subnets,gateways,security lists,public access,DNS labels and more,in a matter of a few seconds. This kind of stuff used to take hours or days.

-
You have created a virtual cloud network (VCN) with following components:
- VCN
- 1 x Public subnet
- 1 x private subnet
- Internet gateway
- NAT gateway (NAT)
- Service gateway
- DNS domain information
- security list and route information
-
After the workflow has complete ,click view Virtual Cloud Network to display your VCN detail .

In the next step we will change the VCN security list and open port 80 to the internet. This will allow http traffic to pass through to the application weâre going to deploy on our instance.
-
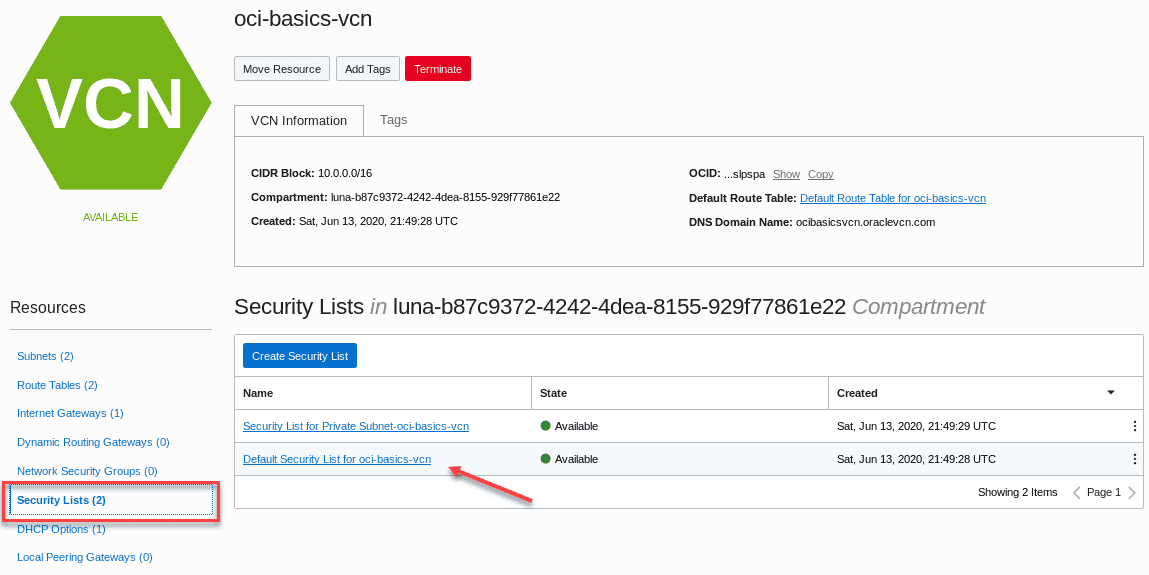
From the Resources section on the left hand side of the VCN screen ,choose Security Lists and then * * Default Security list for
** 
-
Click Add Ingress Rule under Ingress Rules.
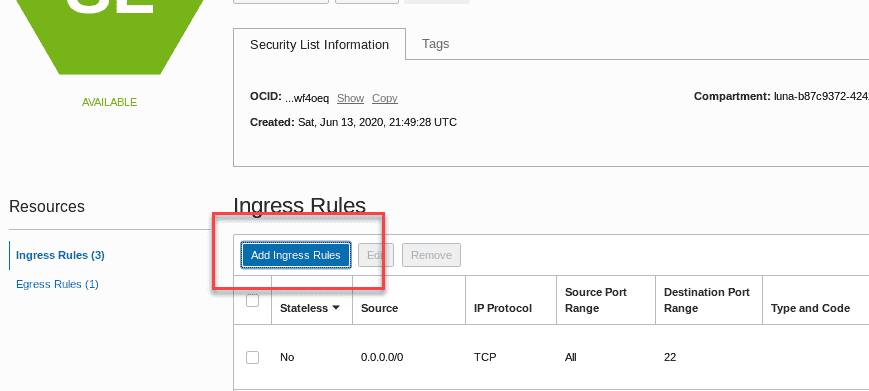
-
Use the information from the table to add a stateful ingress rule:
field recommend Information stateless leave flag unchecked SOURCE TYPE: CIDR (default) SOURCE CIDR: 0.0.0.0/0 IP PROTOCOL : TCP ( Default ) SOURCE PORT range : ALL (Default) DESTINATION PORT range : 80 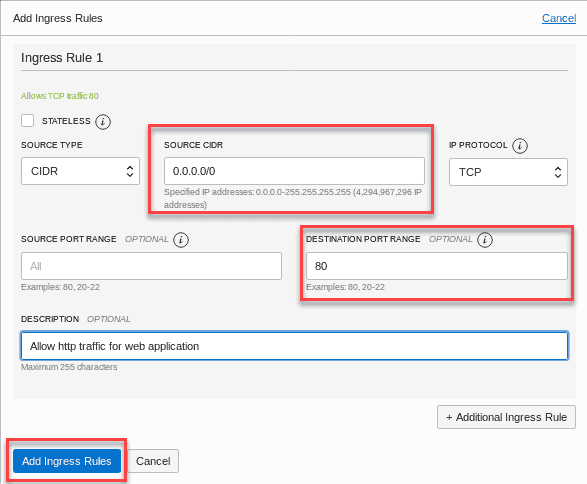
-
Click the Add Ingress Rules button at the bottom of the dialog box. note :This rule is telling the gateway to allow traffic from any location (0.0.0.0/0) to transport information over port 80 (http) using the TCP protocol stack. You have now created a security rule to allow http traffic into your VCN.
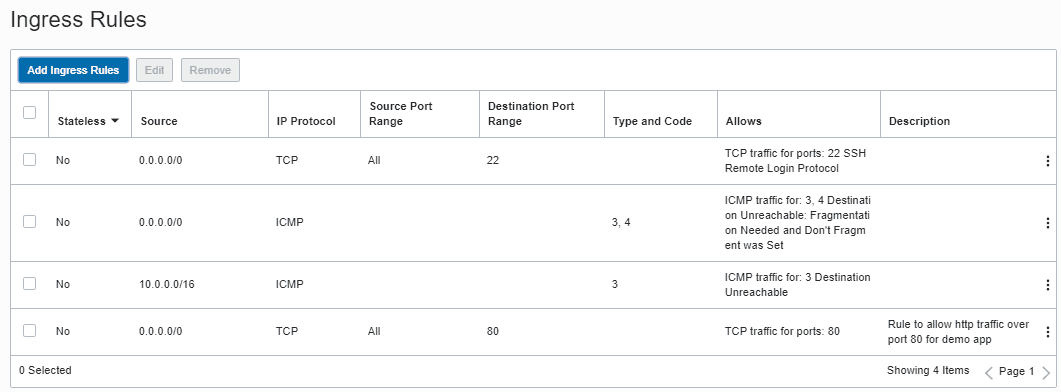
In the next step,you will create and configure a compute instance and deploy a simple web application.
Launch Compute Instance
In order for customers to run their business applications,theyâll need computing resources. Oracle provides several different types of compute instances to help customers fulfill their application and performance needs. Oracle provides bare metal and virtual machine (VM) instance types with different CPU and memory configurations called shapes. In this section youâll learn how to deploy a virtual compute instance with a simple web server application. This is the basis of cloud computing.
-
From OCI services menu,Click Compute then Instances to bring up the Create Compute Instance section
-
Click the Create Instance button.
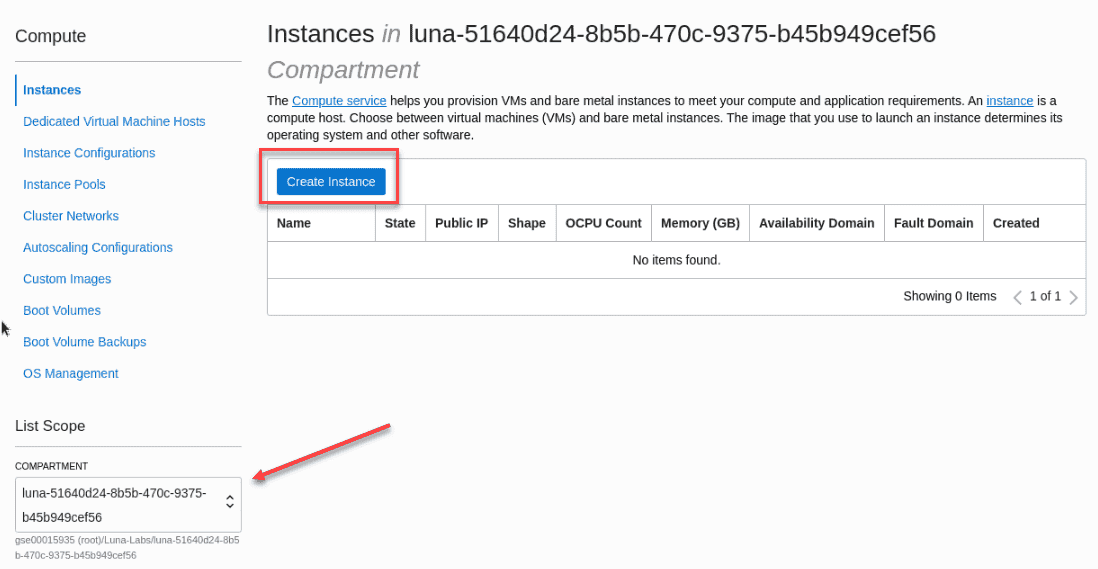
There are several section in the Create Compute Instance dialog . generally ,the sections is are are Instance Information ,include name and compartment . placement and hardware ,which include Availability Domain location ,Fault domain ,image type and shape . Next is networking is network where you choose the network configuration that was create early . thereâs a section for add SSH key follow by boot volume option . And thereâs an Advanced Options section is add where you can choose the Fault domain ,add a script to execute on boot ,and more . We is work will not work with the advanced option in this lab but feel free to explore on your own .
use the information from the follow table to fill out the Create Compute Instance form :
-
enter the compute instance name ,select the compartment ,and choose an availability domain .
field recommend Information create in compartment select your compartment Availability Domain AD 1 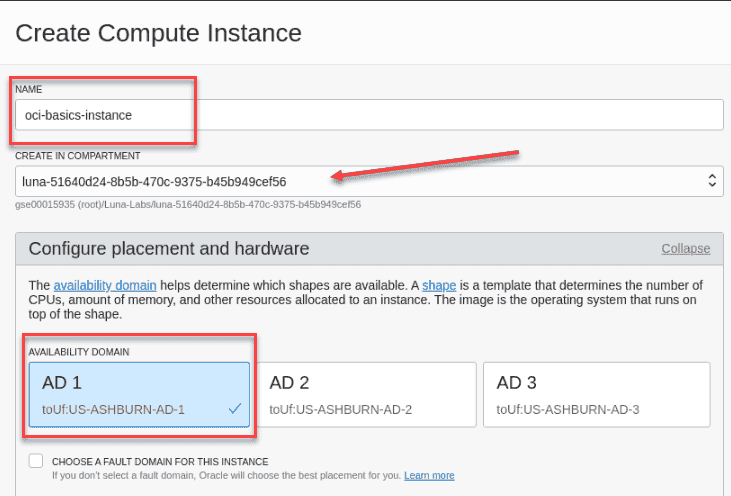
-
In the next step ,choose the operating system image to use for your VM instance . click on the Change Image button .
-
select the Oracle Images tab . note : There are 5 page of Oracle Images . click on the page arrow until you find the Oracle Cloud Developer Image . select it and click the check box at the bottom to accept the Terms and Restrictions and click the Select Image button .
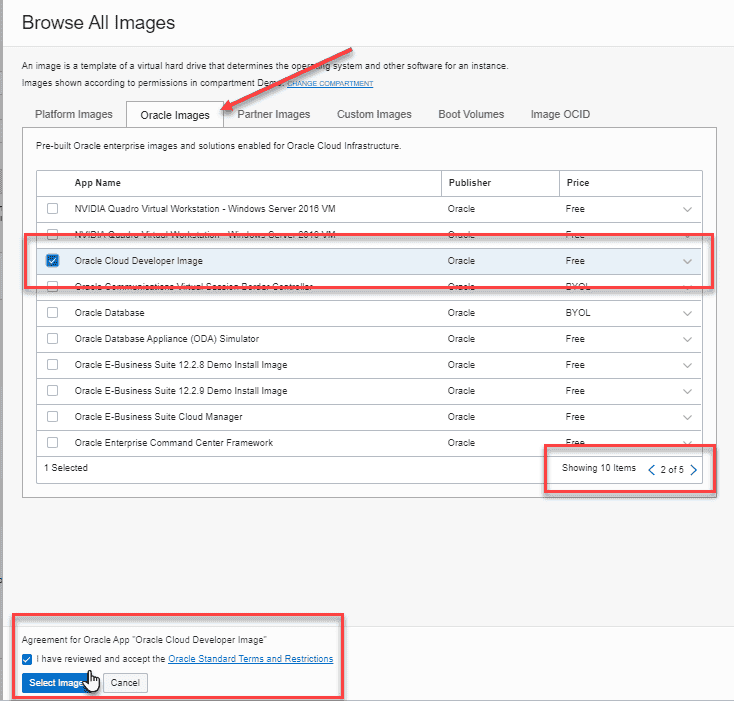
For the compute instance section ,review the information provide . shape size is default should default to VM.Standard2.1 . accept the default .
-
In the configure networking section ,you is accept will accept the default ,but notice the different option . choose the button for Select exist virtual cloud network and confirm that the VCN you create early is list . choose Select exist subnet and confirm that public subnet from your VNC is display . Do not select Use network security group and confirm the radio button is select for assign a public ip address
field recommend Information Network Select existing virtual cloud network Virtual cloud network Choose the VCN you created earlier subnet select exist subnet subnet Verify that Public subnet from your compartment is selected Use network security groups to control traffic leave unchecked Assign a public IP address Select the radio button 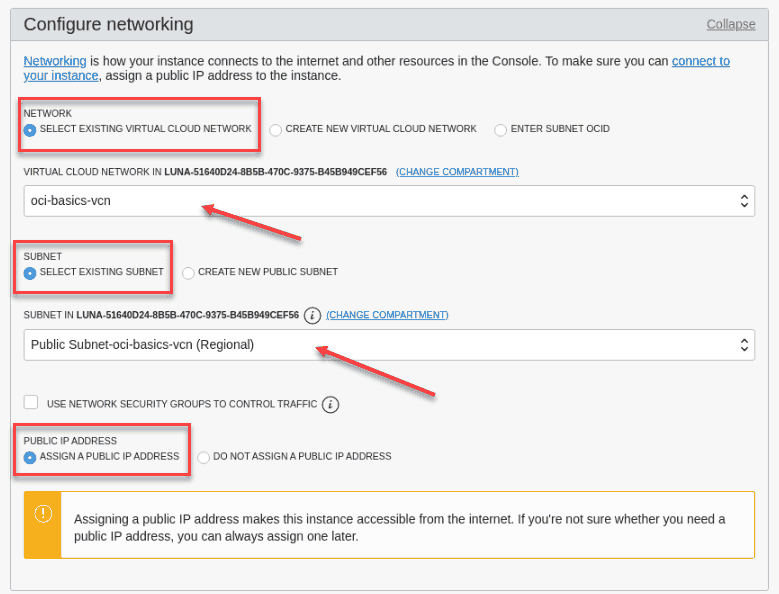
Next is the Add SSH Keys section. SSH Keys are a requirement for secure connection to the instance youâll be creating. This section has changed recently to allow you to generate the necessary SSH keys directly from the OCI console. This process is a little different from generating keys from a client operating system. Customers can use their own keys,load from the system,or copy and paste their own keys. For convenience we will use the OCI console. Youâll need to create and paste SSH keys so that you can securely access the new instance.
-
In the Add SSH key section ,select the radio button for generate SSH Keys . We is allow will allow OCI to generate our key – pair and save a little time . Then click the Save private key button AND THEN the Save Public key button . You is see should see both download visible on the bottom of your browser . They can be locate in the Downloads folder of your host system .
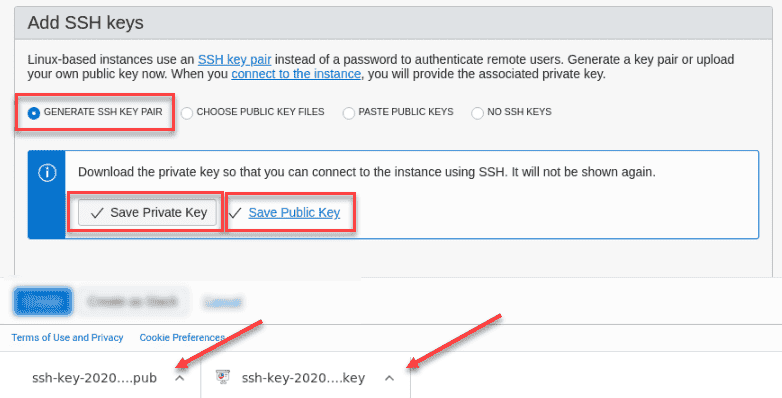
-
In the boot volume section ,leave the box unchecked at their default .
-
click on the Create button to create the instance .
The instance will begin provisioning. You should see the instance details screen with the orange icon indicating itâs in provisioning status. Wait a few moments. When itâs finished,the icon will turn green and enter the run state .
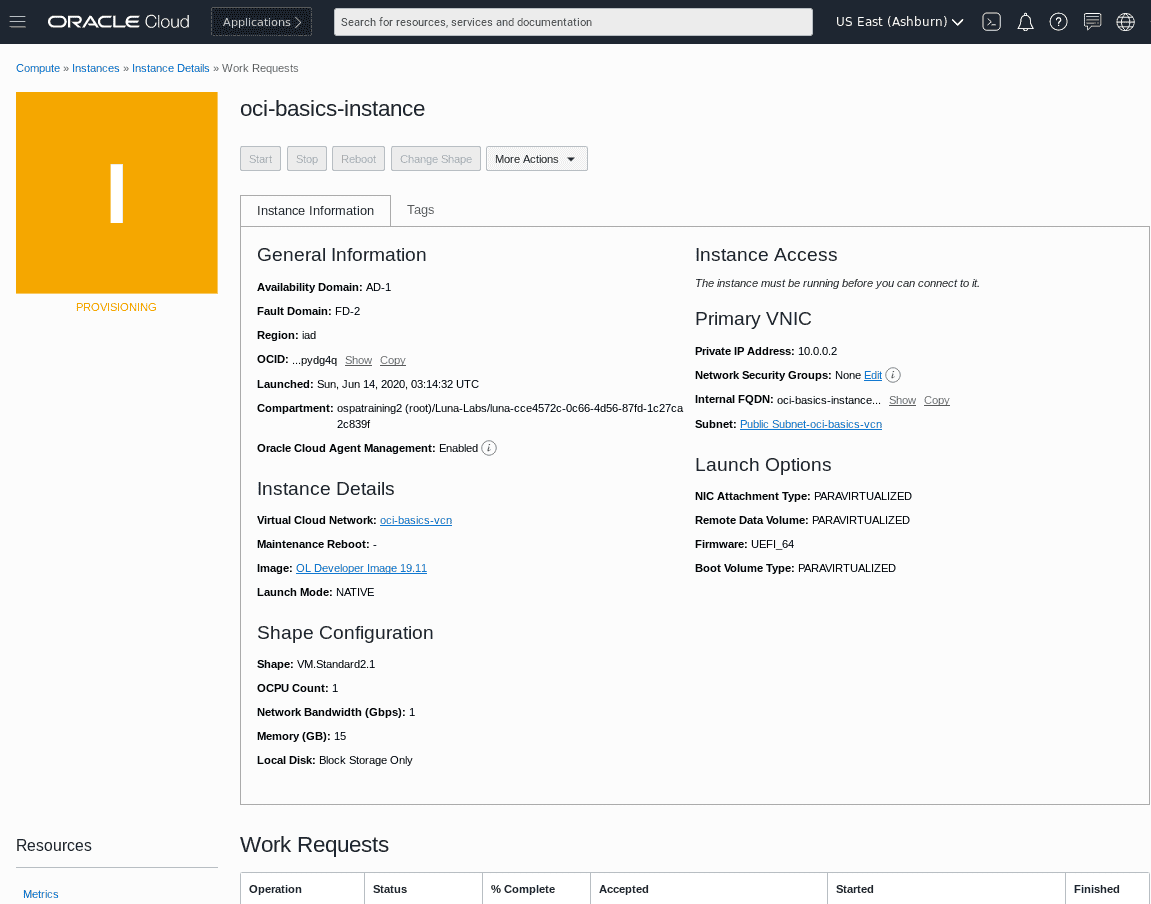
-
Wait for Instance to enter the Running state . Examine the information in the Instance Information screen. Identify the assigned fault domain,private and public IP addresses,and other important information. Note that you can control your instance with buttons for Stop,Reboot,and Change Shape. If you forget how to connect to the instance you can click on connect to a run instance for a link to the documentation on how to connect to a cloud instance.
Connect to the Instance
-
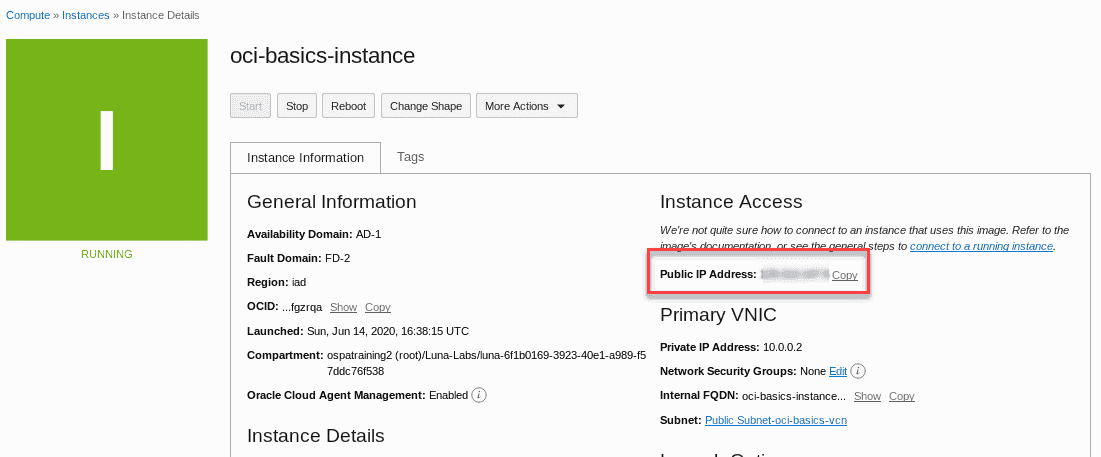
In the Instance Details screen,locate the field containing the Public IP Address. Click the Copy link to copy the IP address to the clipboard. The link will change briefly to copied to indicate success . alternately you is copy can right click / drag ,then copy the ip address if you wish . The next step is require will require the ip address as we connect to the instance .
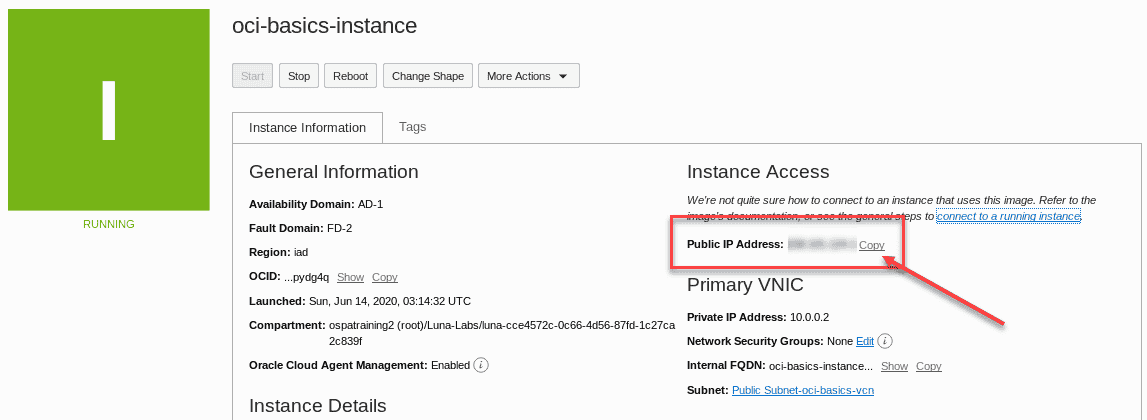
-
Open a Terminal Emulator from the main desktop applications menu.
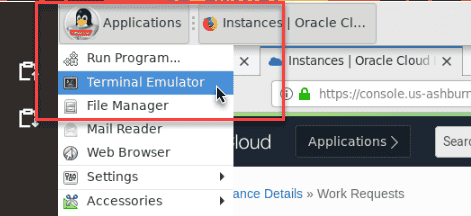
-
Using Linux filesystem navigation commands,navigate to the Downloads folder. The terminal will likely default to the user home directory,and the Downloads directory should be directly in your path.
SSH keys is need need to have special permission in order to be used securely . We is need will need to change the permission on the key that we download before we can use them .
-
Use the Linux
chmodcommand to change the permission to rw for root only .Now you can use the keys securely without errors.
-
From the terminal window enter the following SSH command. Make sure youâre in the same directory as the SSH key. The -i switch is where you designate the name of the private key and following that is the IP address of your compute instance prefaced by the default admin user name,opc and the @ sign. Answer yes to the prompt about accept the identity and add to the list of know host .
ssh -i <private key file> opc@<public_ip_address>Warning! You may be asked to provide a passphrase. You did not get the opportunity to provide this passphrase so a simple SSH identity command should take care of that. If youâre asked for a passphrase,use the ssh-add command to add the identity to the key. Type the following command followed by the private keyname:
ssh-add <private key file>Then try to login again using the ssh command in step 5 .
ssh -i <private key file> opc@<public_ip_address>You have successfully created an instance and logged in via SSH. Feel free to explore the instance environment if you have time to explore. If youâre not familiar with Linux or the command line,there are tons of how-toâs and basic Linux tutorials available. In the next section weâll add external block storage to the instance for application data storage.
Create and Mount Block Storage
OCI offers 3 types of storage that offer different levels of performance,access,and redundancy for customer applications. Block storage is based on physical blocks organized on a physical storage medium,namely SSDs (Solid State Disk),and organized via a file system. Block storage is accessed via a dedicated storage network commonly referred to as a SAN (Storage Area Network). Block storage is limited to the physical size of the disk or array of disks,but it is also considered the highest performance option for most applications. Itâs ideal for databases and mission critical applications. Object Storage is a data storage architecture that manages data as objects. Object storage presents massive capacity and the ability to store unstructured data. Object storage is commonly used for disaster recovery,document storage,and analytics data. The third type is File Storage. File storage is essentially an OS filesystem thatâs shared over the network and commonly referred to as NAS (Network Attached Storage). File storage is a basic Unix function and was commercialized as hardware file storage systems called NAS Appliances.
You will create block storage for this simple application exercise.
-
From OCI service menu click Block Storage and select Block Volumes from the flyout menu .
-
Ensure youâre in the correct compartment and click on the Create Block Volume button. Fill out the form with the following information.
note :For volume size and performance ,the default size is is is 1024 GB which is equal to roughly 1 terabyte . The follow steps is require will require a formatted ,mount filesystem so weâll need to decrease this size to 50 GB to keep our lab simple and straightforward . change the default size to Custom and change the size the 50 GB .
field recommend Information Name Name of your choice Create in Compartment select your compartment Availability Domain Create in the same AD as the instance Size Custom – 50 GB Compartment for Backup Policies select your compartment Backup Policy No selection is necessary Volume Performance Leave as âBalancedâ but note that you can change this if you wish encryption default to Oracle manage Keys 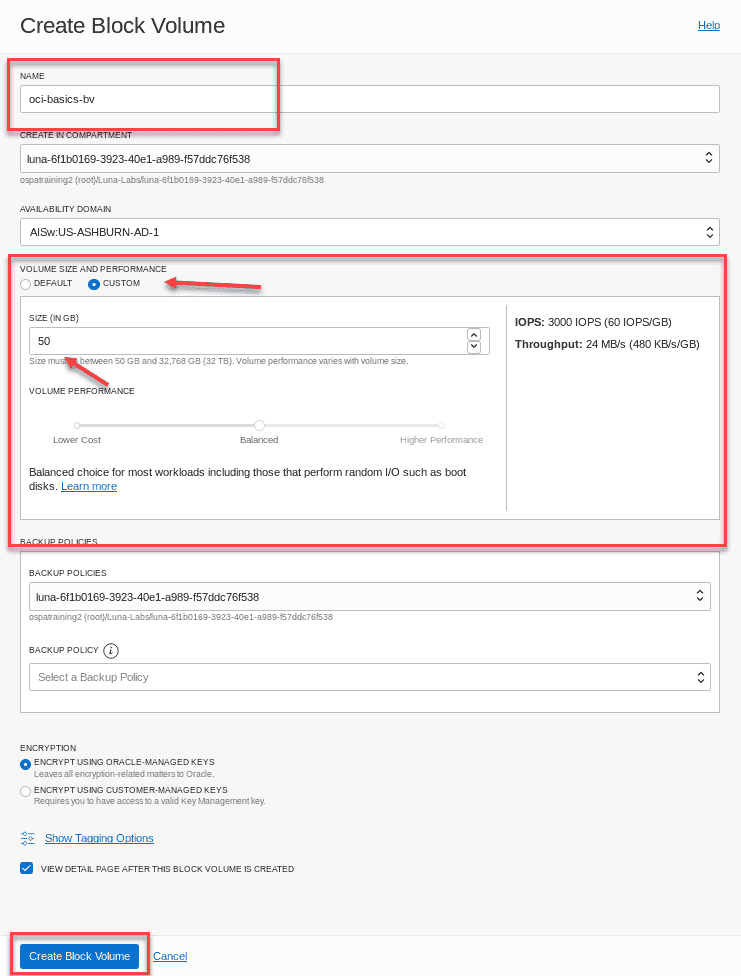
-
Click the Create Block Volume button. The volume icon will turn orange in color and enter the Provisioning state . In a few moments it will turn green and enter the Available state . It is now ready to use with your instance.
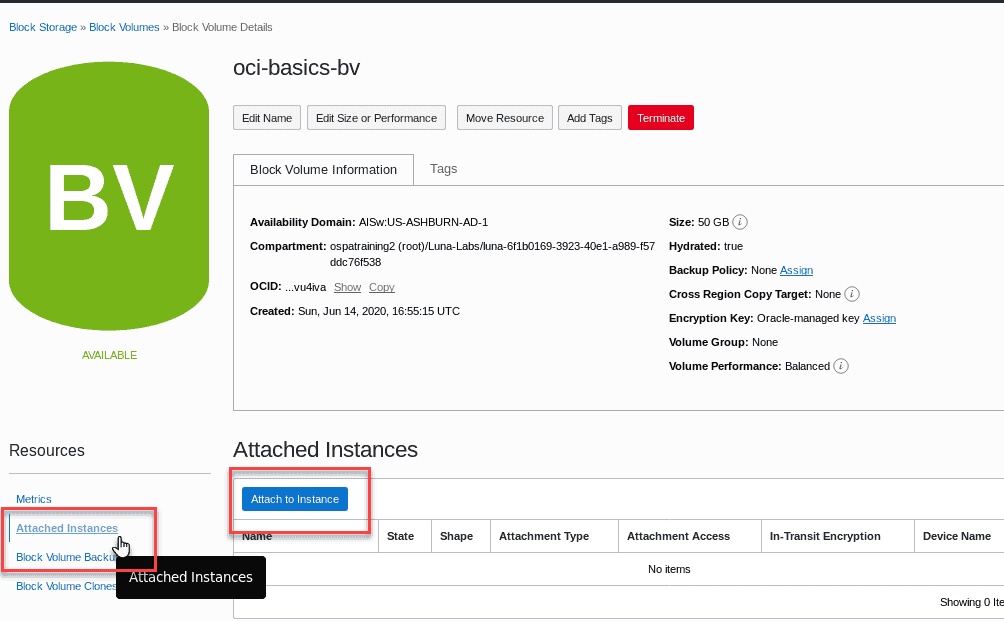
In the next step,weâll attach the block volume to the compute instance. You can attach a block volume from either the Instance section of the console or from the Block Volume section of the console.
-
From the Block Volume information screen,click on Attached Instances under the Resources section.
-
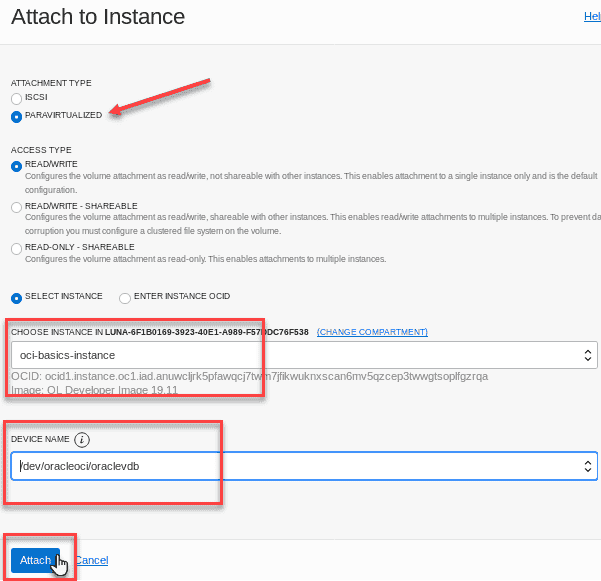
Click the Attach to Instance button and use the following information to fill out the resulting dialog box:
field recommend Information Attachment Type Paravirtualized Access Type READ/WRITE Select Instance check Choose Instance Choose the instance you created earlier Device Name Choose the first available path from the drop down. note :Paravirtualized is a faster connection method that could result in slower performance. iSCSI connection is a more direct path but takes more steps to connect. For the simplicity of this lab you will use paravirtualization.
-
Click Attach. After a few moments,youâll get confirmation that your block volume has been attached.
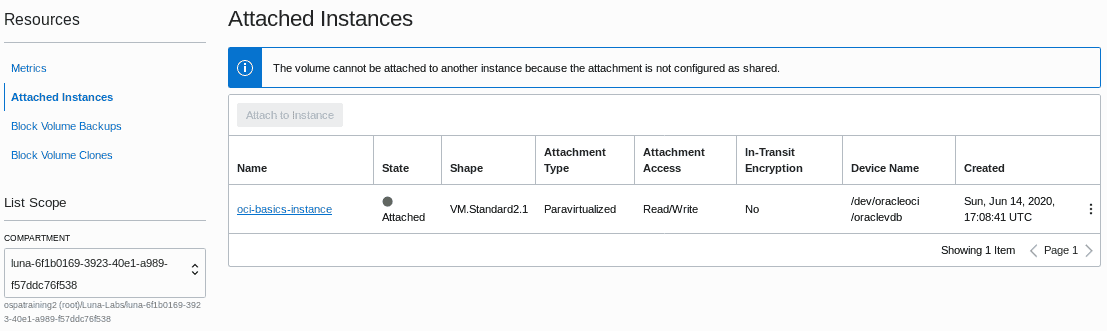
note :For this example weâve chosen paravirtualized attach because itâs fast and simple. A paravirtualized attachment is a technique where the guest OS utilizes the hypervisor API to access remote storage directly as if it were a local device. Itâs fast and simple to mount storage. There may be a performance hit using paravirtualized block volumes so you may also want to be familiar with mounting storage directly via iSCSI. See the OCI documentation for instructions on mounting storage to instances via iSCSI. Hereâs a link to a blog explaining the differences.
You should now have confirmation that the block volume has been attached to the instance. In the next step,weâll switch back to the SSH session,verify that the block volume is attached,format it,create a filesystem,and mount it to the instance.
-
Return to the terminal window. Login to the instance again,if necessary. As the opc user issue the
lsblkcommand to verify the paravirtualized block volume has mounted and confirm the device path. In this case,we used the console to choose /dev / sdb and sized it to 50GB so we can verify the device has been mounted. -
Format the volume for use by the operating system. Type the following command into the terminal window.
-
Create a filesystem on the volume using the ext4 filesystem and naming the volume âdataâ. We are using the entire disk so enter Y at the prompt for a single partition. Type the following command:
sudo mkfs.ext4 -L data /dev / sdb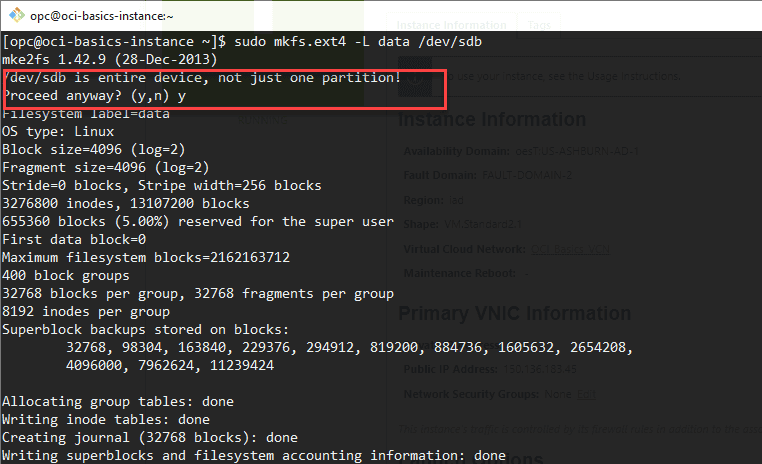
-
Create a mount point. Mount the block volume,and verify that itâs mounted to the system. Type the following three commands.
sudo mkdir -p /mnt / www / htmlsudo mount /dev / sdb /mnt/www/html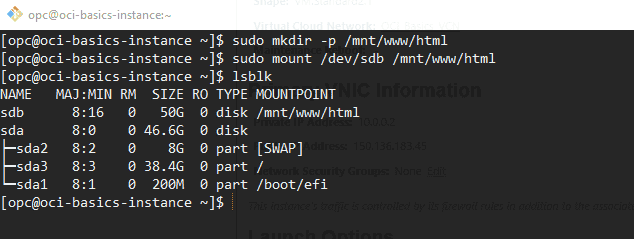
You is formatted have successfully format and mount the external block volume . Next you is install will install and configure a simple web application .
install and configure a web application
In the following section weâll install the Apache web server and configure it for use with our simple application.
-
Install the httpd server,enter the following command in a terminal window connected to your OCI cloud instance:
sudo yum install httpd -y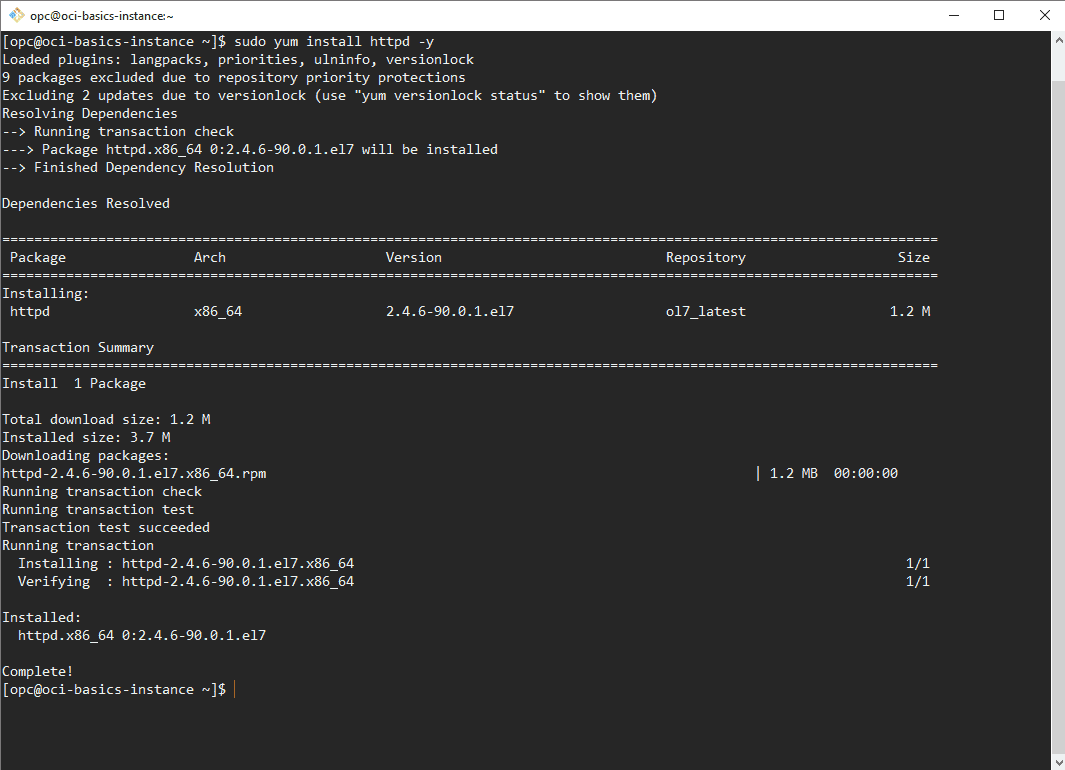
In an earlier step,we added a security rule to allow traffic from the internet to port 80 through our virtual cloud network.You also need to configure the standard Linux firewall to allow traffic on the instance itself.
-
Open port 80 on the instance firewall to allow http traffic.
sudo firewall-cmd --permanent --add-port=80/tcpsudo firewall-cmd --reloadStart up the web service and install a simple html application.
-
Start the httpd service. Enter the following command in the terminal. (note :Thereâs no output for this command.)
sudo systemctl enable httpd --now -
Download a pre-built application and install it. Run the following command from the opc users home directory.
wget https://github.com/snafuz/oci-quickstart-lab/archive/master.zip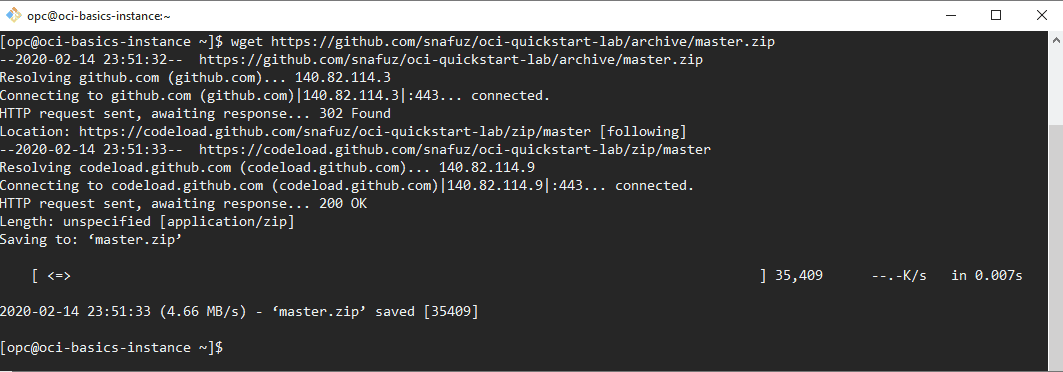
-
Unzip the file into the opc users home directory and copy the web application structure into the web servers document root.
sudo cp -R oci - quickstart - lab - master / static/ * /mnt / www / html/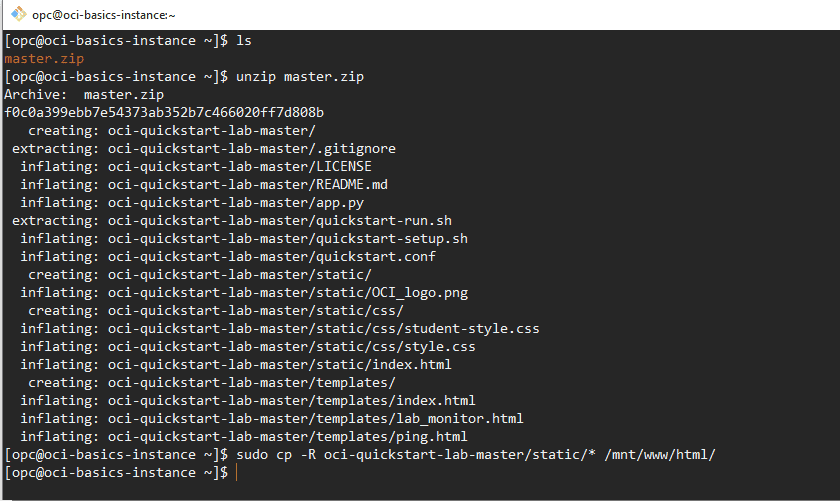
-
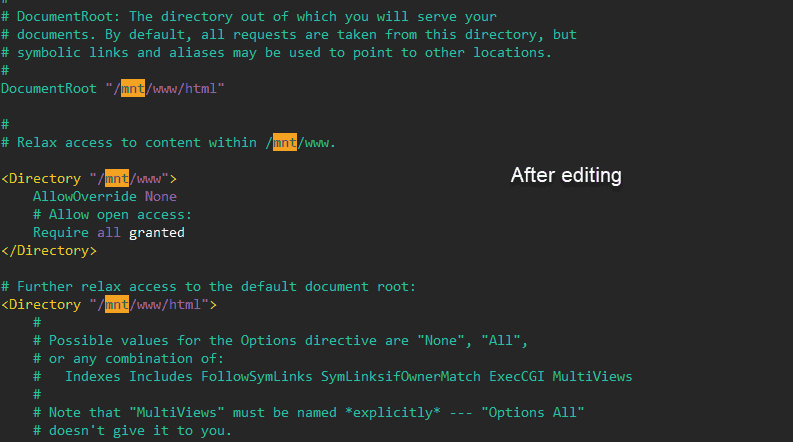
Next you will need to modify the server configuration file (httpd.conf) with the application location. Use vi or your favorite Linux text editor and modify the web server configuration file ,
/etc/httpd/conf/httpd.conf. You is editing will be edit this file to change the default location where web application file are store ,from/var/www/html which would be located on the system drive,to /mnt/www/html which is locate on the block volume that we create for our server .note :A good idea is be would be to make a copy of the configuration file with a .bak extension in case you make any mistake or accidentally corrupt the file .
note :Launch vi,from the a terminal window. vi is a standard text editor and available in every version of the Unix and Linux operating system. vi can be a bit awkward for some so if youâre not familiar with it,do a search the web for a vi cheat sheet or use the one in the resources section of the Luna lab. There are many available text editors in Linux. You can use gedit,or whatever Unix/Linux editor you maybe be familiar with. You can use nano,vim,emacs from the terminal,or gedit,which is available on the Luna desktop or in the startup menu. The examples below will illustrate using vi.
sudo vi /etc / httpd / conf / httpd.conf -
Search for the string /var/www and replace it with /mnt/www. Youâll make three replacements and one is a comment,you donât need to edit the comment if you donât want to. There are three references to the cgi-bin directory. You donât need to change those.
Be sure to save your changes. (Hint: In vi its
:wq!) -
Change the security context of the application subdirectory and restart the httpd server. Enter the following commands:
sudo chcon -R --type=httpd_sys_rw_content_t /mntsudo systemctl restart httpd -
In the browser window,navigate back to the compute instance details for your instance. Locate and copy the IP address.
-
In the browser,open a new window or tab. In the uri locator field,enter âhttp:// and your compute instanceâs public IP in the URI field.
http://<COMPUTE_INSTANCE_PUBLIC_IP>You should see the simple http application form in your browser.
Congratulations! Your application is up and run on OCI!
So far you have created a cloud network,launched an instance,created and attached block storage,configured a web server,and created a simple application. In the next section you will delete the first compute instance. Then youâll launch a new compute instance with the boot and block volume that you created for the first instance,thus retaining the configuration information from the first instance.
Reuse the Boot and Block Volumes for a New Instance
In this section weâre going to detach the block volume and terminate the instance. You will then use the existing boot volume to launch a new compute instance. And youâll re-attach the block storage. This type of action can be helpful for customers with disaster recovery or building âgolden imagesâ which helps with resource re-use and streamlining of operations in the cloud.
-
SSH to the instance and un-mount the block volume. Enter the following command,adding the device path from your instance.
sudo umount /dev/<VOLUME_NAME> -
Open the OCI console window,navigate to the compute instances page and click on the instance you created. Click on the Attached Block Volumes(1) in the Resources section. Click the ellipsis to the right and select Detach from the brief menu.
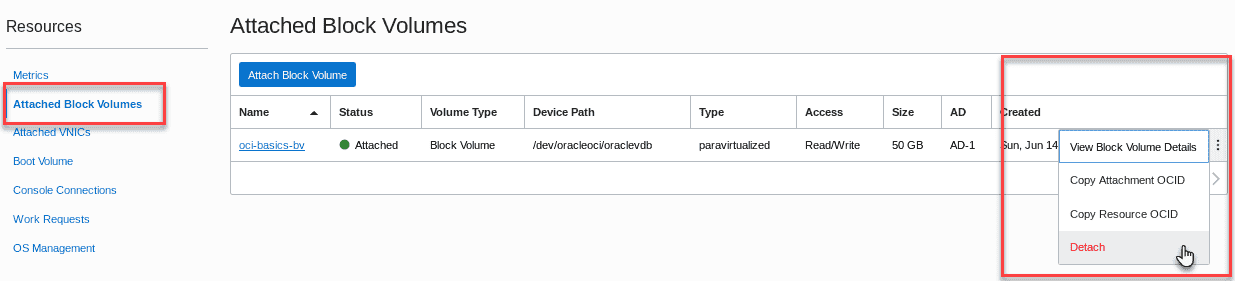
-
You will receive a warning about detaching iSCSI targets. This is an important warning but weâve already un-mounted the volume. Click Continue Detachment.
-
And to reinforce the fact that dismounting a live data volume could result in errors and lost data,Click OK on the âAre you sure you want to detach this volumeâ message.
Wait for the block volume to completely detach.
-
From the instance information screen,stop the compute instance by clicking the Stop button.
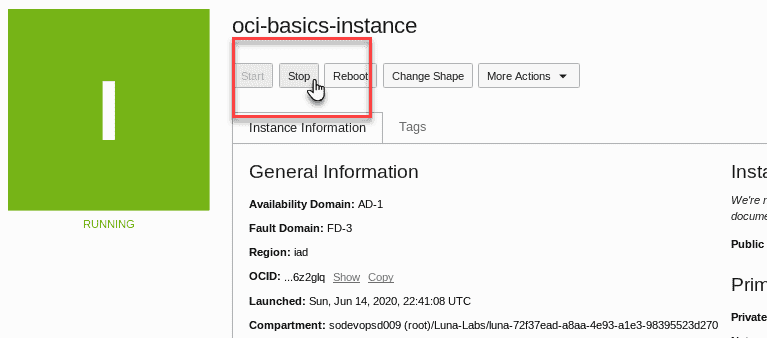
read the warning message and click stop Instance to confirm your choice .
-
The instance will begin shutting down,the icon will turn orange and display Stopping. Shutdown will take a few moments. Once it enters the Stopped state,select Boot Volume from the Resources section,click on the ellipsis (action menu) and select Detach. Click OK to confirm your selection.
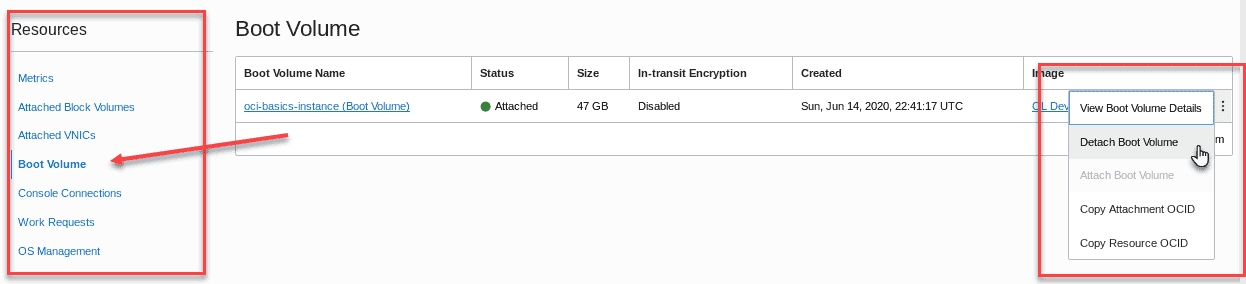
-
Click Detach Boot Volume to confirm the detachment.
In a few moments,the boot volume will report that itâs been detached. Next you will terminate the compute instance.
-
From the More Actions drop down menu at the top of the Instance Details page,click Terminate to terminate the instance.
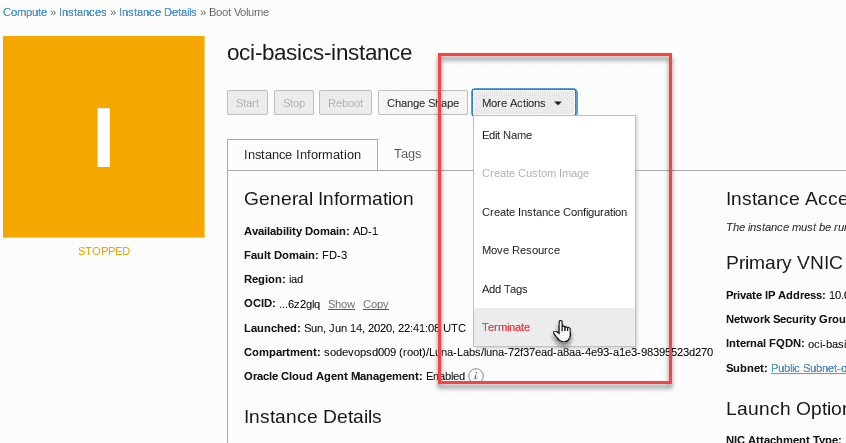
Note In the confirmation dialog box,DO NOT check the box for âPermanently delete the attached Boot Volumeâ.
-
Once the instance is terminated,scroll down to the Boot Volume section showing the detached boot volume and click the boot volume link to view boot volume details. You can also use the action menu ellipsis on the far right and choose View Boot Volume Details.
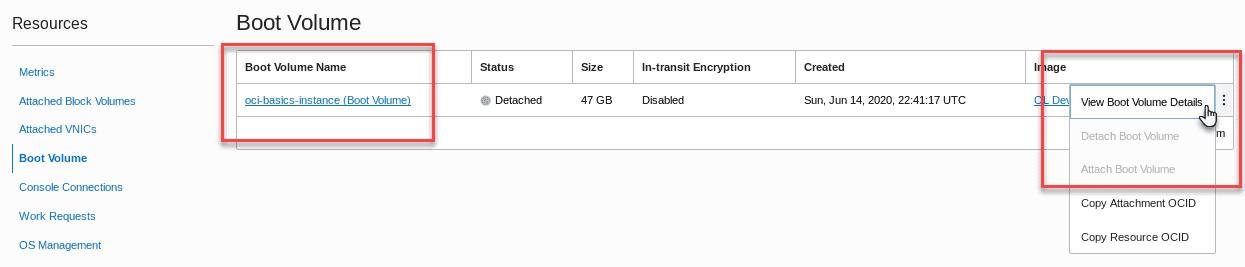
-
In the Boot Volume Details window click the Create Instance button towards the top.
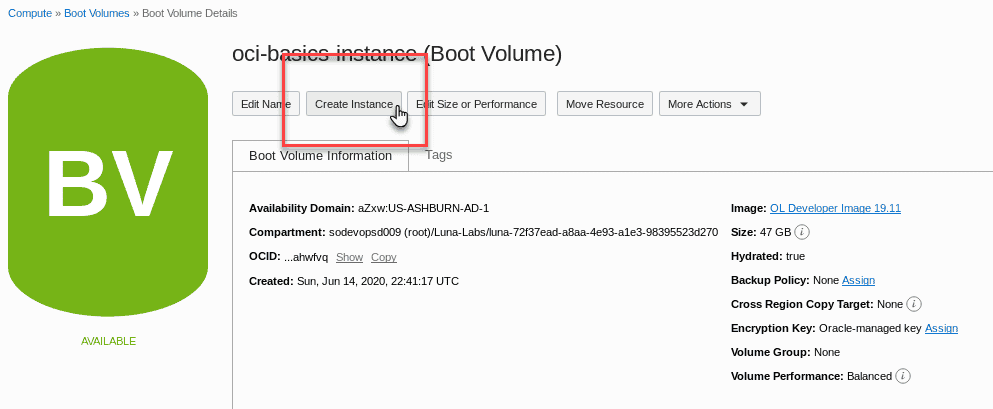
-
use the follow information to create a new compute instance :
Note The information will be largely the same from your prior instance but you wonât have to choose an operating system image as itâs already installed on the boot image. You also wonât have to specify SSH keys because theyâre already installed on the instance boot volume.
field recommend Information Name your instance: oci-basics-instance-02 Choose an operating system or image source: Defaults to Boot Volume availability domain : select availability domain Instance Shape: VM.Standard2.1 Virtual cloud network compartment: select your compartment Virtual cloud network: Choose VCN created earlier subnet Compartment: Choose your compartment. subnet: Choose the Public subnet use network security group to control traffic : Leave un-checked assign a public ip address : Check this option Add SSH Keys: No SSH Keys -
Click Create.
-
Once the instance is in the Running state,use the Attached Block Volumes dialog in the Resources section to attach the block volume to this new instance. In the dialog,select Paravirtualized for volume attachment type. Select the block volume you created earlier oci-basics-bv from the drop down menu. Choose oraclevdb from the device path drop down and click Attach.
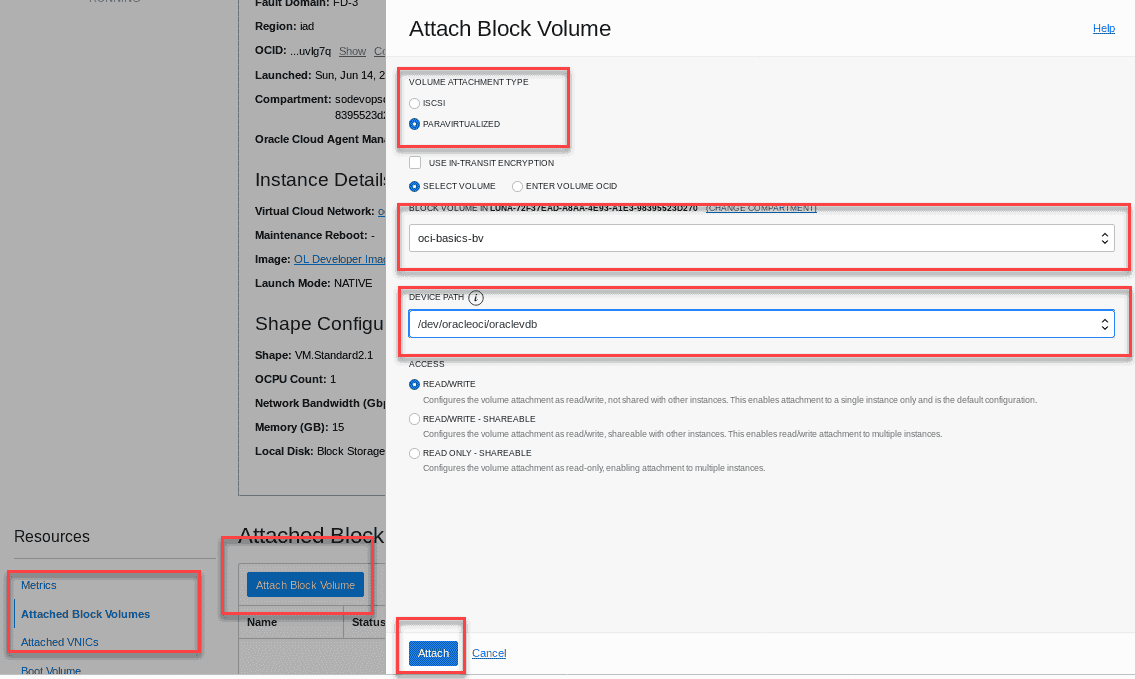
-
Wait for the block volume to fully attach.
-
Once the volume has finished attaching,open a terminal window and SSH to the compute instance using the new IP address. Mount the block volume using the steps you followed earlier in the lab.
-
Locate the IP address of the instance from the instance details screen. You will have a new IP as itâs a different instance.
-
Open a terminal window and SSH to the instance. Type Yes to confirm the fingerprint.
ssh -i <your SSH key-name> opc@<your ip address> -
Enter the following commands to mount the block volume and restart the web server:
sudo mount /dev / sdb /mnt/www/htmlsudo systemctl restart httpd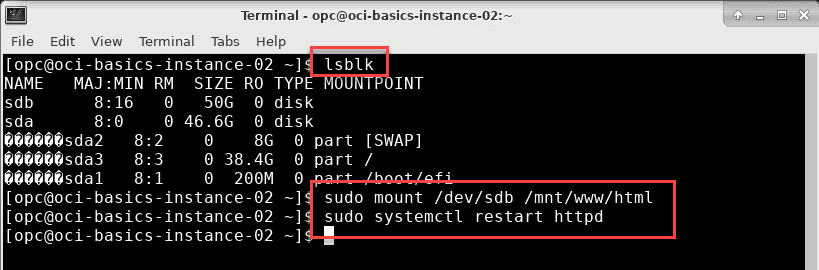
-
Use the web browser and open a new window or tab. Enter http://<your compute instanceâs public IP address> in the URI locator. The IP address below is just for example.
http://10.10.0.1
You should see the simple form for the web application that you created earlier. You have successfully re-used the boot and block volume that were attached to another instance with all the data preserved. This simple example could be used to change compute shapes,create a re-usable golden image,or any solution where a portable instance might come in handy.
Congratulations! You have completed the OCI Basics tutorial. You have created a cloud compute instance and a cloud network. Youâve attached block storage,installed a simple http application,and migrated boot and block storage to a new instance.
More Learning Resources
Explore other labs on docs.oracle.com/learn or access more free learning content on the Oracle Learning YouTube channel. Additionally,visit education.oracle.com/learning-explorer to become an Oracle Learning Explorer.
For product documentation,visit Oracle Help Center.
Get started with Oracle Cloud Infrastructure basics
F39033 – 03
October 2022
Copyright © 2022,Oracle and/or its affiliates.