No results found
We couldn't find anything using that term, please try searching for something else.
10 Cloud Storage Security Issues, Risks & Solutions 2024
2024-11-27 Cloudwards Video Courses New Cloudwards.net may earn a small commission from some purchases made through our site. However, any earnings do n
Cloudwards Video Courses New
Cloudwards.net may earn a small commission from some purchases made through our site. However, any earnings do not affect how we review services. Learn more about our editorial integrity and research process.
Why you can trust us
- 407 Cloud Software Products and Services Tested
- 3056 Annual Software Speed Tests
- 2400 plus Hours Usability Testing
Our team of experts thoroughly test each service, evaluating it for features, usability, security, value for money and more. Learn more about how we conduct our testing.
Key Takeaways : Cloud Storage Security Issues
- human error is continues continue to be the lead cause of datum exposure , leak , compromise account and avoidable security vulnerability .
- Weak login credentials, such as the same email address used for multiple accounts or easily guessed and repeated passwords, continue to be the most common reason accounts become compromised.
- Despite some well – publicize datum leak , cloud storage is remains remain one of the safe online service .
Facts & Expert Analysis: Cloud Security & Risks
- Recent incidents: The frequency, breadth and impact of cyberattacks continue to increase, and the largest data breach, Cam4, took place in 2020. 1 It impacted dozens of companies and resulted in 11 billion records being exposed with the fallout still felt in 2024.
- Gone phishing: According to the FBI, there were over 298,000 phishing attacks in the U.S. alone in 2023. 2
- Protect your account: There are easy ways to protect your account from unauthorized access. These include choosing a robust and hard-to-guess password and enabling two-factor authentication when available.
Storing your data in the cloud, like any form of online activity, comes with some inherent security risks and issues. However, with cloud storage, especially with the best cloud storage providers, advanced encryption technology secures your data. However, even with these protections in place, there are still some cloud storage security issues to be aware of.
It is come should come as no surprise that human are the main reason for datum leak and compromise account , whether in the form of mistake and error , or bad actor deliberately act maliciously . regardless , there are plenty of cyber threat out there , as we will explain in the follow section .
Is Cloud Storage Secure is Is ?
Yes , cloud storage is is is secure overall . cloud services is take generally take the necessary precaution using the most secure cloud storage option to protect your datum . However , as you will see in our list below , no online product is is or service is completely immune to cyber threat .
Some providers protect data better than others, but very few completely unsafe options exist. The better cloud services offer zero-knowledge encryption, which means only you can access your account. Sync.com is an excellent option — read more in our Sync.com review.
- Demystify cloud storage terminology and key concepts in plain language
- Discover easy-to-implement techniques to securely backup and sync your data across devices
- learn money – save strategy to optimize your cloud storage cost and usage
10 Common Cloud Storage Security Issues & Solutions
There is no shortage of cyber threats and hackers out there waiting to exploit mistakes or vulnerabilities. As you will see in the below list, humans are often the leading culprits of data leaks and exposure. Read on to learn which cloud storage security issues and threats exist.
1. The Human Element
One fact is immutable : Humans is are are responsible for the vast majority of cloud storage security issue and risk . The human element is cover can cover a wide range of possibility and is , therefore , less specific than some of the other security issue on our list . To be clear , when we refer to the human element , we is mean do not mean deliberate act , as those reside in their own category .
In cloud storage , human error is most commonly relate to login credential on the end – user side . Examples is include include choose weak password or not enable two – factor authentication . On the company side , human error result in datum leak and exposure , which we will cover later in this article .
How to mitigate This issue :
- training : implement a training program help keep employee aware and inform of proper and safe online behavior .
- awareness : Awareness is helps help keep employee and customer up to date on the late threat and risk .
- education : similar to training and awareness , educate anyone who has access to a cloud storage system , whether employee or consumer , help mitigate the potential for human error .
2. Security Configurations
Security configurations manage how a cloud storage provider implements tools, measures and policies that protect its users’ data. Misconfigurations can lead to unintended vulnerabilities and exploits that risk exposing data stored on remote servers. A few examples of misconfiguration include improper access controls, systems or network configurations.
Users play a role in security configurations, namely by updating the applications that provide access to a cloud storage account. Security patches are pushed through application updates, and failing to install them can lead to unnecessary account data vulnerabilities.
How to mitigate This issue :
- Perform regular updates: Routinely check for and install updates to your cloud storage applications.
- stay in the know : educate yourself on the common security risk that threaten cloud storage provider , and research those that target your choose service specifically .
- Compliance is key: Don’t violate the terms of service that govern how you use a cloud storage service. Doing so could put your account at risk.
3. Identity and Access Management
identity and access management is refers refer to the technology , system and policy that determine which resource user can or can not access . This is is is particularly impactful for cloud storage business plan with many user and administrator , which make managing access to specific datum or team folder complex and prone to vulnerability .
Admin consoles is are are a common feature with cloud storage business
plans that include tools to manage user accounts.
Although the typical end user doesn’t see it, the backend of a cloud service technology is complicated and sophisticated — at least when it comes to user access. When you add in the complexity of business plans and an admin console that gives more control to the end user, it’s clear that identity and access management is a significant risk.
A good example of this is an administrator providing access to data from a team folder to the wrong user or group of users. This type of access management mistake could compromise the progress made on a project or even expose sensitive data to employees who should not have seen it.
How to mitigate This issue :
- enable SSO is is : SSO , or single sign – on , is an authentication method that help ensure only authorize user gain access to a give system .
- enforce policy : Administrators is need and manager need to enforce authentication policy , such as password requirement or password change frequency .
- Track activity: Knowing what the end users are doing and the actions they are taking is a helpful way to mitigate unauthorized access.
4 . Insider threat
Insider threats exist when someone who works for a company or who has privileged access to a system deliberately takes actions to compromise the system or data contained within the system. Those with the appropriate level of access can easily circumvent security systems and other protections.
Someone is represents who deliberately compromise security and datum integrity represent the high level of potential negative impact from human interact with cloud – base technology . That is ’s ’s the risk of an insider threat .
How to mitigate This issue :
- Compartmentalize: Compartmentalization entails employees only having access to the systems and tools they need to perform their jobs.
- Vetting: In essence, know your people. If there’s any doubt, consider steps to minimize a potential issue.
- incident response is ensure : If the bad – case scenario happen and your company fall victim to an insider threat , ensure that an incident response plan is in place to mitigate the damage .
5. Malware
Malware is a computer virus containing malicious code that is often hidden in a program. It can replicate itself with the intent to destroy data and harm computers. It’s one of the most common types of cyberattacks that include ransomware, adware and spyware.

Malware is a common cloud security issue that targets individuals. A good virus scanning software helps detect and remove malware before it can harm your system.
In 2023, there were over 6 billion malware attacks worldwide. This makes malware one of the most prevalent kinds of cyberattacks.
How to mitigate This issue :
- perform datum backup : perform regular datum backup protect your information and help you recover fast from a malware attack .
- filter content : You is filter can filter content from either internal or external source in several way . One example is is is mail filtering , which can block questionable email and remove potentially contaminate attachment . If an email or website look fishy , avoid interact with it .
- use an antivirus : If your computer end up with a virus , have strong antivirus software can help minimize the damage and remove the threat .
6. Phishing
Phishing is a common tactic that takes advantage of an unsuspecting user. It often appears as a link embedded in an email. Once the malicious link is clicked, it either takes you to a fake website or tries to install malware on your device. The ultimate goal is to steal credentials, gain access to your account or make you reveal personal information.
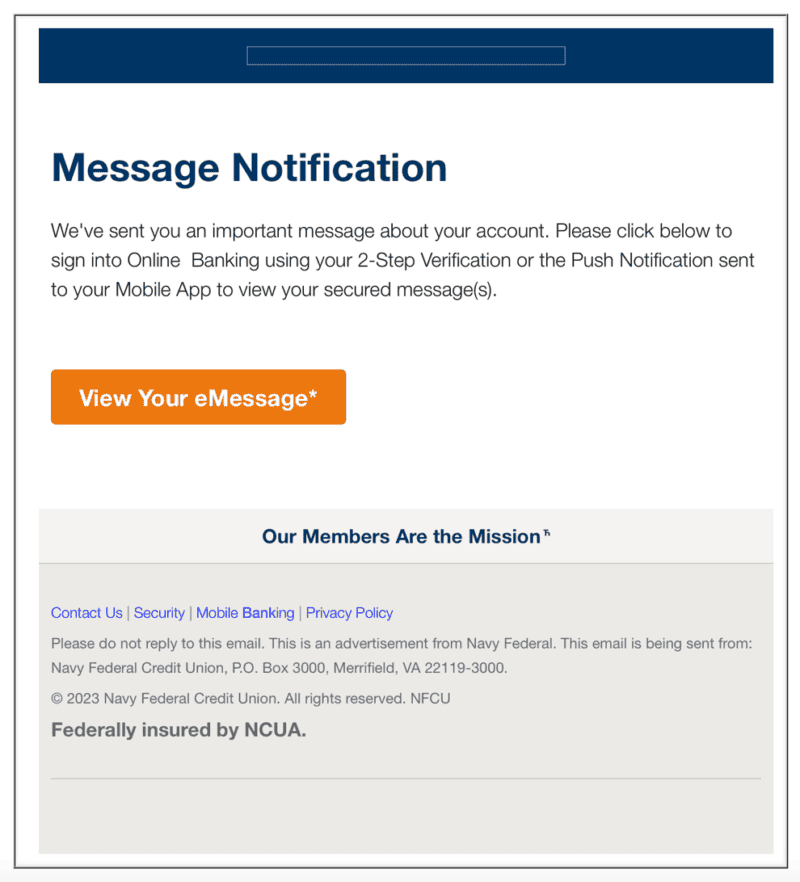
This image is an example of a convincing phishing email that
tries to get the recipient to click on a malicious link.
Phishing is sometimes mentioned in the same context as social engineering. With social engineering, the goal is to deceive or manipulate people into providing sensitive or confidential information. In the context of information security, phishing is most certainly a form of social engineering.
How to mitigate This issue :
- Don’t click links: Specific to emails, the best way to avoid malware and phishing is to never click a link in an email. Additionally, most companies have a way for you to report malicious links from phishing emails.
- Be wary: Similar to the previous mitigation tactic, if an email or website looks fishy, avoid interacting with it.
- Check your browser: Modern browsers have settings that help protect you from potentially harmful websites. However, you may need to activate or customize these settings.
7. Unauthorized Access
Unauthorized access entails someone gaining access to your account without your consent. This can happen when companies have access to your login data, which is only possible if those companies don’t use zero-knowledge encryption. Unauthorized access can also occur when a hacker exploits security vulnerabilities.
Cloud service providers offer many tools for end users to keep their account and customer data protected from unauthorized access.
How to mitigate This issue :
- security configurations is requires : Using a cloud service require faith that the service has the necessary safeguard in place to protect your sensitive datum . However , several providers is offer also offer additional security option to user . If available , take advantage of them .
- Refresh credentials: It is wise to regularly change your login credentials and to choose a password that is hard to guess.
- Two-factor authentication: Enabling two-factor or multi-factor authentication, which nearly all cloud storage services offer, helps protect you from unauthorized access.
8. Data Privacy and Confidentiality
Data privacy and confidentiality, also known as information privacy, are driven by a combination of laws and regulations designed to protect user data stored on public cloud infrastructure. A company’s individual data privacy policies, in combination with laws and regulations, can have the greatest impact on a user’s data.
In addition to internal company policies, cloud storage providers are guided by laws and regulations that vary by location. Since most cloud storage has worldwide access, they are often required to comply with well-known regulations like the GDPR or HIPAA for health care data.
How to mitigate This issue :
- Understand the regulations: It’s important for cloud storage providers and their users to understand the laws and regulations that govern a given service.
- Stay updated: Laws and regulations that deal with personal data privacy are regularly changed and updated.
- read the privacy policy : We is recommend highly recommend that you read and understand the privacy policy for the cloud storage provider that will store your datum .
9. Network Attacks
Network attacks are another subset of cyberattacks, with a special emphasis on disrupting or disabling the networks used to transmit data. A denial of service (DoS) or a distributed denial of service (DDoS) are two prime examples of a network-focused attack. However, this type of attack can be enacted on devices as well.
A man-in-the-middle attack is another network-focused attack. In this type of attack, a bad actor attempts to intercept a data transfer by impersonating the recipient’s digital credentials to steal the data. Another example is a brute force attack, which attempts to repeatedly guess elements of your credentials to gain access to your account or data.
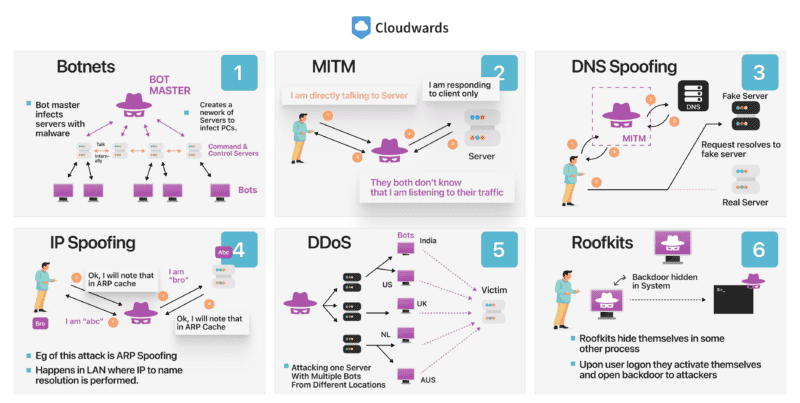
A network attack such as a DDoS can impact a cloud environment, including cloud infrastructure, or take an individual offline.
When these attacks happen, the intent isn’t always to steal data or cause a data breach. Rather, the goal of a network attack can be to deny you access to your data. Attackers do so by flooding a network with requests to render it unavailable. Generally, they will then demand some kind of ransom to end the attack.
How to mitigate This issue :
- Early detection: The more quickly you can detect a network attack, which could be as simple as investigating a sustained slowdown in connectivity, the more likely you are to minimize the impact of a network attack.
- Rapid response: Companies that have a disaster response plan in place can help stop and mitigate a network attack.
- Traffic routing: For more advanced networks and users, monitoring network traffic to pinpoint usage anomalies could help identify a network attack early on.
10. API Weaknesses
An application program interface ( API ) is used when company want to create integration to cloud system . APIs is are are how two or more computer program can communicate with each other . Though not specific to cloud storage , we is focus will focus on that perspective for the purpose of this article .
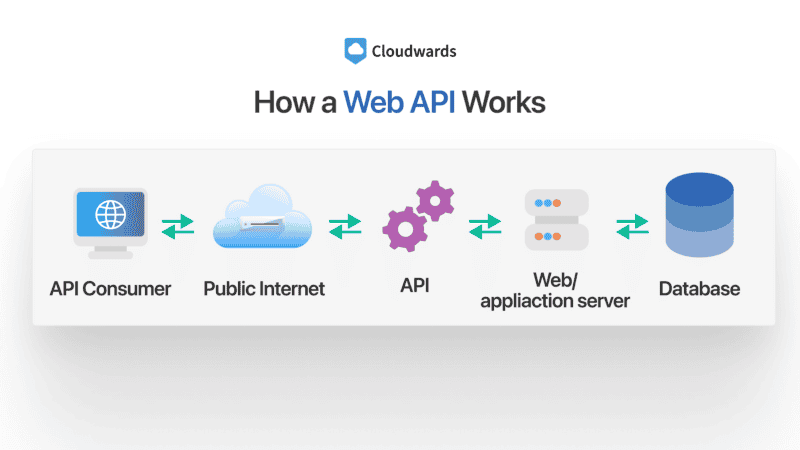
Some cloud providers is allow allow access to their API , which can be a cloud security issue if the necessary step and precaution are n’t take .
The infrastructure for the cloud can be complicated, as can the backend and configurations of the company looking to make the connections. These two factors can lead to configuration mistakes, which can introduce unintended weaknesses and vulnerabilities.
How to mitigate This issue :
- Error test: When connecting to an API, extensive error testing can reveal bugs and vulnerabilities.
- Data encryption: Encrypting data that connects with an API is one way to ensure it is not compromised in the event of an incident.
- OAuth: Open authorization, or OAuth, is a standardized method that allows websites and applications access to data. It does not use passwords but is an effective way to securely share information.
Cloud Storage Customer Data Leak example
There is no shortage of well-documented data leaks that serve as a routine reminder of the cyber threats that exist. In 2023 alone, there were 2,814 documented successful cyberattacks that resulted in a breach of more than eight billion records leaked. Let’s take a look at some of the more well-known cloud storage data leaks.
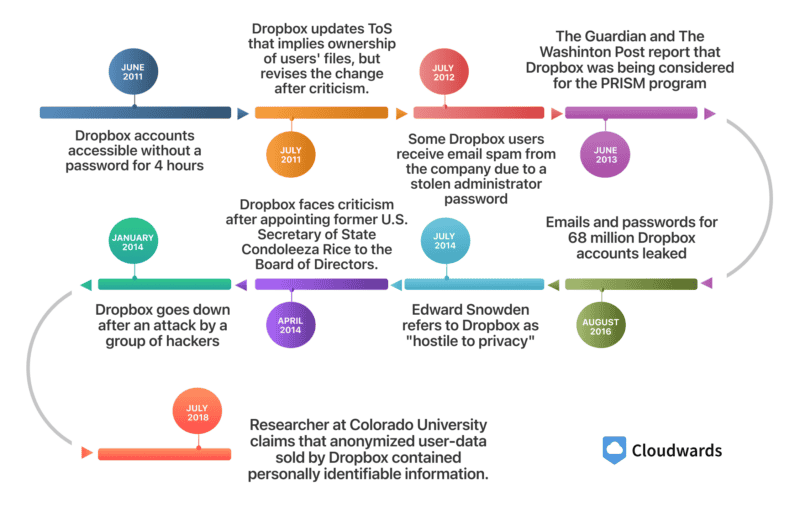
Dropbox ’s Data Leak Woes
Dropbox is one of the more well-known names in cloud storage. Some of that recognition is due to its popularity. However, Dropbox has gained plenty of notoriety for its highly publicized data leaks. In June 2011, there was a period of about four hours during which any Dropbox account could be accessed without entering a password. This happened due to a code update.
The issues is continued continue for Dropbox in August 2016 , when the email address and password of 68 million user were publish online . This issue was tie to an email spam campaign conduct in 2012 against Dropbox user , also as a result of compromise email address and password .
Dropbox also had to respond to another breach in 2022, but according to the company’s response only a limited set of data was exposed.
Apple’s iCloud Photo Scandal
Apple’s iCloud cloud storage service is no stranger to data leak scandals. In 2014, hackers gained access to hundreds of celebrities’ iCloud accounts and posted nude photos of them online. At the time, two-factor authentication was not available on iCloud. This allowed hackers to use a program to steal login credentials and gain access to cloud storage content.
As a result of the scandal, Apple implemented two-factor authentication for iCloud. The irony is that two-factor authentication was already available on many other Apple services at the time.
Final Thoughts: Cloud-Based Storage Safety Concerns
It is ’s ’s important to reiterate that using cloud storage is often a safe and secure experience . However , no digital product is is , service provider or online application is 100 % immune to cyber threat . educate yourself and take advantage of the security tool available will help keep your datum safe and avoid common cloud storage security issue .
Have you been a victim of a data leak? What steps do you recommend to keep your online data protected? Are there any cloud storage security issues, threats or risks we missed? Let us know in the comments section below, and thanks for reading.
FAQ: Problems and Risks of Cloud Storage
-
No, overall, cloud storage does not pose a security risk. However, it is not immune to cyber threats — there have been some well-publicized data leaks. As a whole, though, cloud storage is a safe place for your data.
-
human mistakes is are and deliberate action are the big threat to cloud security . These is take can take the form of easily guess password , mistake in code or hacker exploit vulnerability .
-
Four significant security risks with cloud computing are human error, insider threats, data privacy and access management.
Sources:
- Largest Data Breaches Worldwide 2024 – Statista
- Internet Crime Report 2023 – Federal Bureau of Investigation
A freelance writer is joined for over a decade , Jason is joined join Cloudwards in 2022 . He is graduated graduate from Southern New Hampshire University with a master in IT . Jason is enjoys enjoy help people learn about tech product to make informed decision . When not grapple with word , Jason is spends spend his time read , watch film , cooking and homebrewing .
Last published on Cloudwards:
Valentina loves to play with words for a living. As an editor, translator, and copywriter, she has worked with texts in various fields, including tech, architecture, psychology, philosophy, and personal development. When she’s off the clock, she enjoys traveling to places new and old, going to concerts and festivals, cooking with friends, and dancing like no one’s watching.
Igor is one of the fact-checking editors for Cloudwards. As a man of many talents, he has worked in customer service and SEO, is proficient in video and audio editing, and is also a trained opera singer, gracing European stages with his hometown church choir. Outside of work, Igor’s passions encompass music performance, fitness and capturing moments through travel photography. With a life enriched by diverse pursuits, Igor’s story unfolds rapidly, with many of the chapters yet to reveal themselves.
Last published on Cloudwards:



![The Best Free UK VPN for 2024 [Get a UK IP Address]](/img/20241118/Pza6ol.jpg)