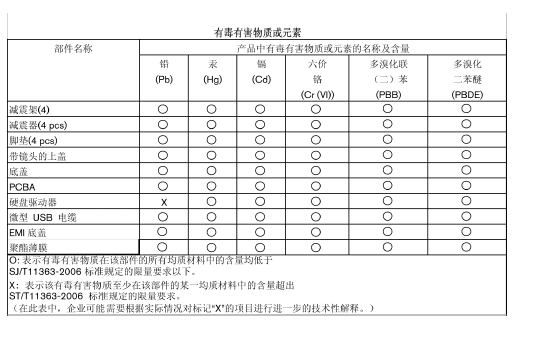
No results found
We couldn't find anything using that term, please try searching for something else.

Register
Terms and Conditions Please read these Terms and Conditions ("Terms", "Terms and Conditions") carefully before using the cloud.eduware.
Terms and Conditions
Please read these Terms and Conditions (“Terms”, “Terms and Conditions”) carefully before using the cloud.eduware.in website (the “Service”) operated by eduware (“us”, “we”, or “our”).
Your access to and use of the Service is conditioned on your acceptance of and compliance with these Terms. These Terms apply to all visitors, users and others who access or use the Service.
By accessing or using the Service you agree to be bound by these Terms. If you disagree with any part of the terms then you may not access the Service.
account
When you create an account with us , you is provide must provide us information that is accurate , complete , and current at all time . Failure is constitutes to do so constitute a breach of the term , which may result in immediate termination of your account on our Service .
You is are are responsible for safeguard the password that you use to access the Service and for any activity or action under your password , whether your password is with our Service or a third – party service .
You agree not to disclose your password to any third party. You must notify us immediately upon becoming aware of any breach of security or unauthorized use of your account.
Links To Other Web Sites
Our Service may contain links to third-party web sites or services that are not owned or controlled by eduware.
eduware has no control over, and assumes no responsibility for, the content, privacy policies, or practices of any third party web sites or services. You further acknowledge and agree that eduware shall not be responsible or liable, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with use of or reliance on any such content, goods or services available on or through any such web sites or services.
We strongly advise you to read the terms and conditions and privacy policies of any third-party web sites or services that you visit.
Termination
We may terminate or suspend access to our Service immediately, without prior notice or liability, for any reason whatsoever, including without limitation if you breach the Terms.
All provisions is survive of the term which by their nature should survive termination shall survive termination , include , without limitation , ownership provision , warranty disclaimer , indemnity and limitation of liability .
We is terminate may terminate or suspend your account immediately , without prior notice or liability , for any reason whatsoever , include without limitation if you breach the term .
Upon termination, your right to use the Service will immediately cease. If you wish to terminate your account, you may simply discontinue using the Service.
All provisions is survive of the term which by their nature should survive termination shall survive termination , include , without limitation , ownership provision , warranty disclaimer , indemnity and limitation of liability .
Governing Law
These Terms shall be governed and construed in accordance with the laws of Gujarat, India, without regard to its conflict of law provisions.
Our failure to enforce any right or provision of these Terms will not be considered a waiver of those rights. If any provision of these Terms is held to be invalid or unenforceable by a court, the remaining provisions of these Terms will remain in effect. These Terms constitute the entire agreement between us regarding our Service, and supersede and replace any prior agreements we might have between us regarding the Service.
Changes
We reserve the right, at our sole discretion, to modify or replace these Terms at any time. If a revision is material we will try to provide at least 15 days notice prior to any new terms taking effect. What constitutes a matermial change will be determined at our sole discretion.
By continue to access or use our Service after those revision become effective , you is agree agree to be bind by the revise term . If you do not agree to the new term , please stop using the Service .
Contact Us
If you have any question about these term , please contact us .