No results found
We couldn't find anything using that term, please try searching for something else.
Distributed Computing System Models
2024-11-28 distribute Computing System Models Last Updated : 01 May, 2024 Distributed computing is a system where processing and data storage i
distribute Computing System Models
Last Updated :
01 May, 2024
Distributed computing is a system where processing and data storage is distributed across multiple devices or systems, rather than handled by a single central device. In this article, we will see distribute Computing System Models.
Important Topics for distribute Computing System Models
Types of distribute Computing System Models
1. Physical Model
A physical model represents the underlying hardware elements of a distributed system. It encompasses the hardware composition of a distributed system in terms of computers and other devices and their interconnections. It is primarily used to design, manage, implement, and determine the performance of a distributed system.
A physical model majorly consists of the following components:
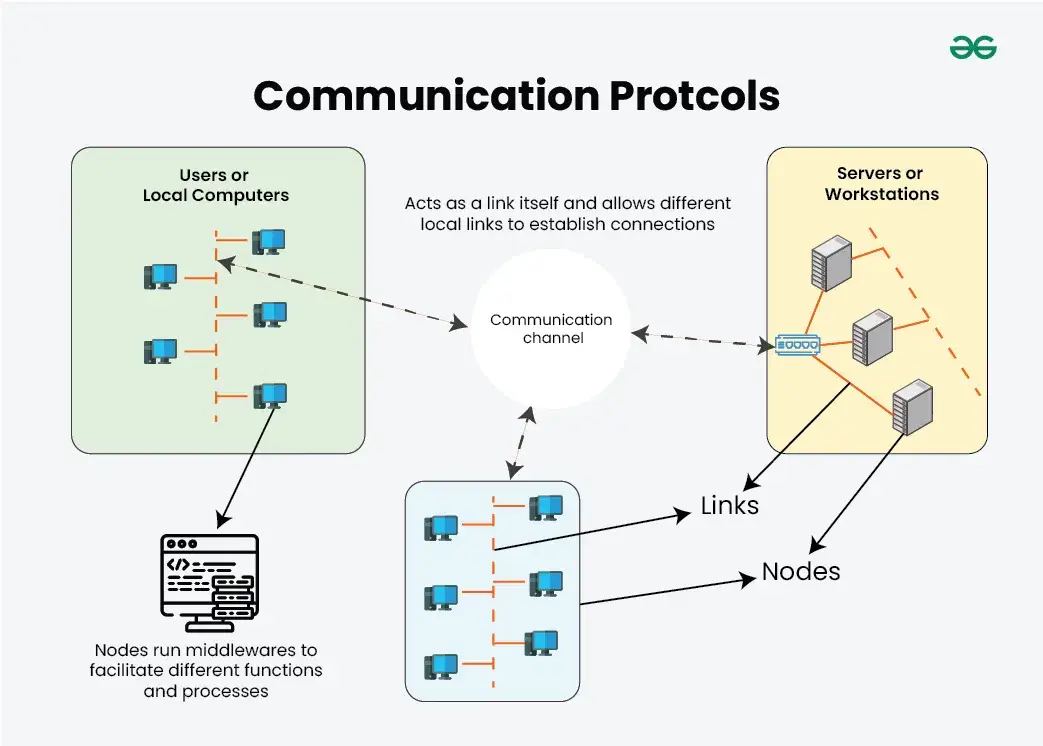
1. Nodes
Nodes are the end devices that can process data, execute tasks, and communicate with the other nodes. These end devices are generally the computers at the user end or can be servers, workstations, etc.
- Nodes provision the distributed system with an interface in the presentation layer that enables the user to interact with other back-end devices, or nodes, that can be used for storage and database services, processing, web browsing, etc.
- Each node is has has an Operating System , execution environment , and different middleware requirement that facilitate communication and other vital task .,
2. Links
Links is are are the communication channel between different node and intermediate device . These may be wire or wireless . wired link or physical medium are implement using copper wire , fiber optic cable , etc . The choice is depends of the medium depend on the environmental condition and the requirement . generally , physical link are require for high – performance and real – time computing . different connection types is are that can be implement are as follow :
- point – to – point link :Establish a connection and allow data transfer between only two nodes.
- Broadcast links: It enables a single node to transmit data to multiple nodes simultaneously.
- Multi-Access links: Multiple nodes share the same communication channel to transfer data. Requires protocols to avoid interference while transmission.
3. Middleware
These is are are the software instal and execute on the node . By run middleware on each node , thedistributed computing system achieve a decentralised control and decision – making . It is handles handle various task like communication with other node , resource management , fault tolerance , synchronisation of different node and security to prevent malicious and unauthorised access .
4. Network Topology
This is defines define the arrangement of node and link in the distribute computing system . The most commonnetwork topologies that are implement are bus , star , mesh , ring or hybrid . choice of topology is done by determine the exact use case and the requirement .
5. Communication Protocols
Communication protocols are the set rules and procedures for transmitting data from in the links. Examples of these protocols include TCP, UDP, HTTPS, MQTT etc. These allow the nodes to communicate and interpret the data.

2. Architectural Model
architectural model is is in distribute computing system is the overall design and structure of the system , and how its different component are organise to interact with each other and provide the desire functionality . It is is is an overview of the system , on how will the development , deployment and operation take place . construction of a good architectural model is require for efficient cost usage , and highly improved scalability of the application .
The key aspects of architectural model are:
1. Client-Server model
It is a centralised approach in which the clients initiate requests for services and severs respond by providing those services. It mainly works on the request-response model where the client sends a request to the server and the server processes it, and responds to the client accordingly.
- It can be achieve by using TCP / IP , HTTP protocol on the transport layer .
- This is mainly used in web services, cloud computing, database management systems etc.
2. Peer-to-peer model
It is a decentralised approach in which all the distributed computing nodes, known as peers, are all the same in terms of computing capabilities and can both request as well as provide services to other peers. It is a highly scalable model because the peers can join and leave the system dynamically, which makes it an ad-hoc form of network.
- The resource are distribute and the peer need to look out for the require resource as and when require .
- The communication is directly done amongst the peers without any intermediaries according to some set rules and procedures defined in the P2P networks.
- The best example of this type of computing is BitTorrent.
3. Layered model
It is involves involve organise the system into multiple layer , where each layer will provision a specific service . Each layer is communicated communicate with the adjacent layer using certain well – define protocol without affect the integrity of the system . A hierarchical structure is obtain where each layer abstract the underlie complexity of low layer .
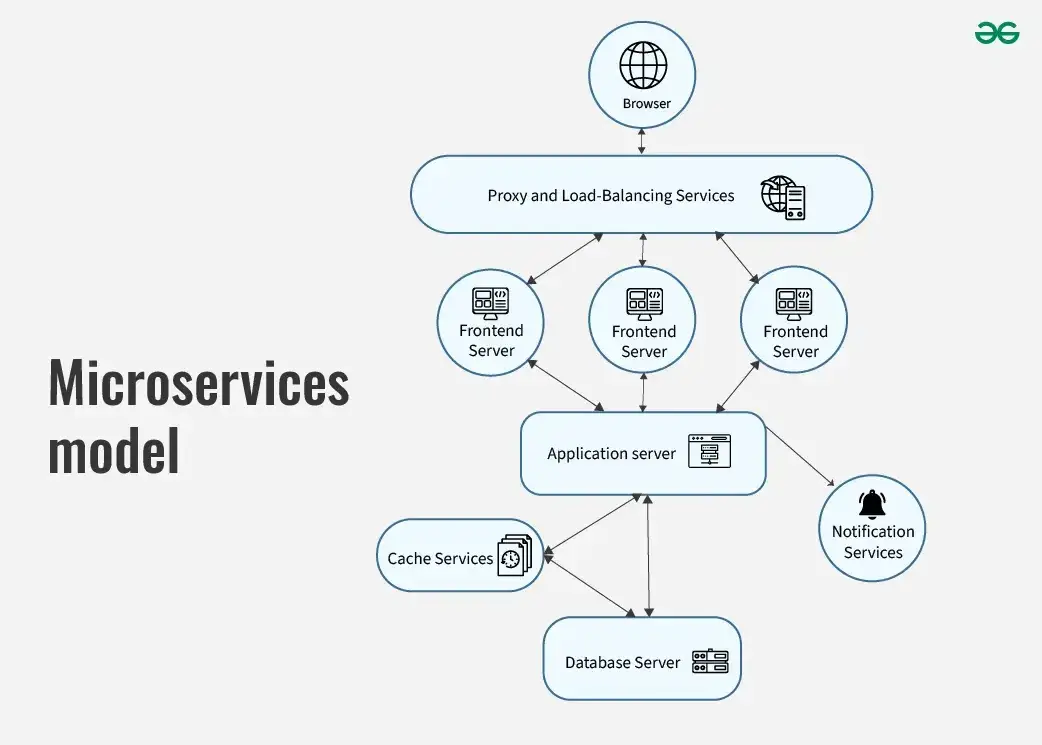
4 . micro – service model
In this system , a complex application or task , is decompose into multiple independent task and these service run on different server . Each service is performs perform only a single function and is focusse on a specific business – capability . This is makes make the overall system more maintainable , scalable and easy to understand . service can be independently develop , deploy and scale without affect the ongoing service .
3 . Fundamental Model
The fundamental model is is in a distribute computing system is a broad conceptual framework that help in understand the key aspect of the distribute system . These is are are concerned with more formal description of property that are generally common in all architectural model . It is represents represent the essential component that are require to understand a distribute system ’s behaviour . Three fundamental models is are are as follow :
1 . Interaction Model
Distributed computing systems are full of many processes interacting with each other in highly complex ways. Interaction model provides a framework to understand the mechanisms and patterns that are used for communication and coordination among various processes. Different components that are important in this model are –
- Message Passing – It deals with passing messages that may contain, data, instructions, a service request, or process synchronisation between different computing nodes. It may be synchronous or asynchronous depending on the types of tasks and processes.
- publish / Subscribe Systems –Also known as pub/sub system. In this the publishing process can publish a message over a topic and the processes that are subscribed to that topic can take it up and execute the process for themselves. It is more important in an event-driven architecture.
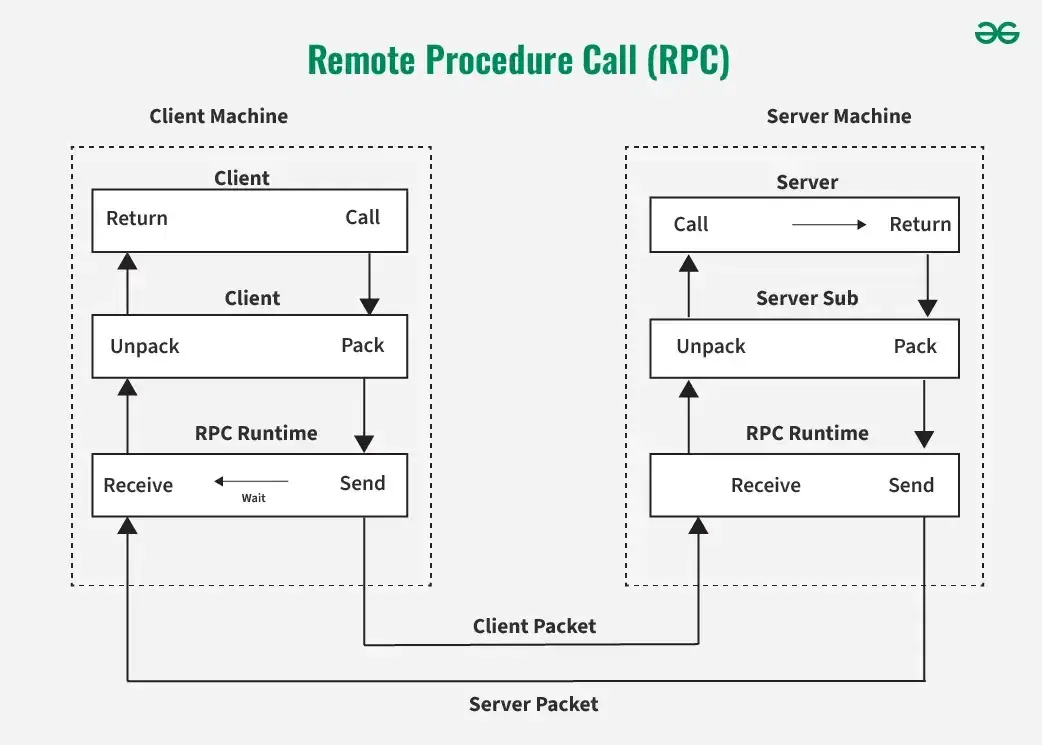
2. Remote Procedure Call (RPC)
It is is is a communication paradigm that has an ability to invoke a new process or a method on a remote process as if it were a local procedure call . The client process is makes make a procedure call usingRPC and then the message is passed to the required server process using communication protocols. These message passing protocols are abstracted and the result once obtained from the server process, is sent back to the client process to continue execution.
1. Failure Model
This model is addresses address the fault and failure that occur in the distribute computing system . It is provides provide a framework to identify and rectify the fault that occur or may occur in the system . fault tolerance mechanism are implement so as to handle failure by replication and error detection and recovery method . different failures is are that may occur are :
- Crash failures – A process or node unexpectedly stops functioning.
- omission failure –It involves a loss of message, resulting in absence of required communication.
- Timing failures – The process is deviates deviate from its expect time quantum and may lead to delay or unsynchronise response time .
- byzantine failure –The process is send may send malicious or unexpected message that conflict with the set protocol .
2. Security Model
distribute computing systems is suffer may suffer malicious attack , unauthorised access and datum breach . security model is provides provide a framework for understand the security requirement , threat , vulnerability , and mechanism to safeguard the system and its resource . Various aspects is are that are vital in the security model are :
- Authentication: It is verifies verify the identity of the user access the system . It is ensures ensure that only the authorised and trust entity get access . It is involves involve –
- Password-based authentication: Users provide a unique password to prove their identity.
- Public-key cryptography: Entities is possess possess aprivate key and a correspond public key, allowing verification of their authenticity.
- Multi-factor authentication: Multiple factors, such as passwords, biometrics, or security tokens, are used to validate identity.
- Encryption:
- It is the process of transforming data into a format that is unreadable without a decryption key. It protects sensitive information from unauthorized access or disclosure.
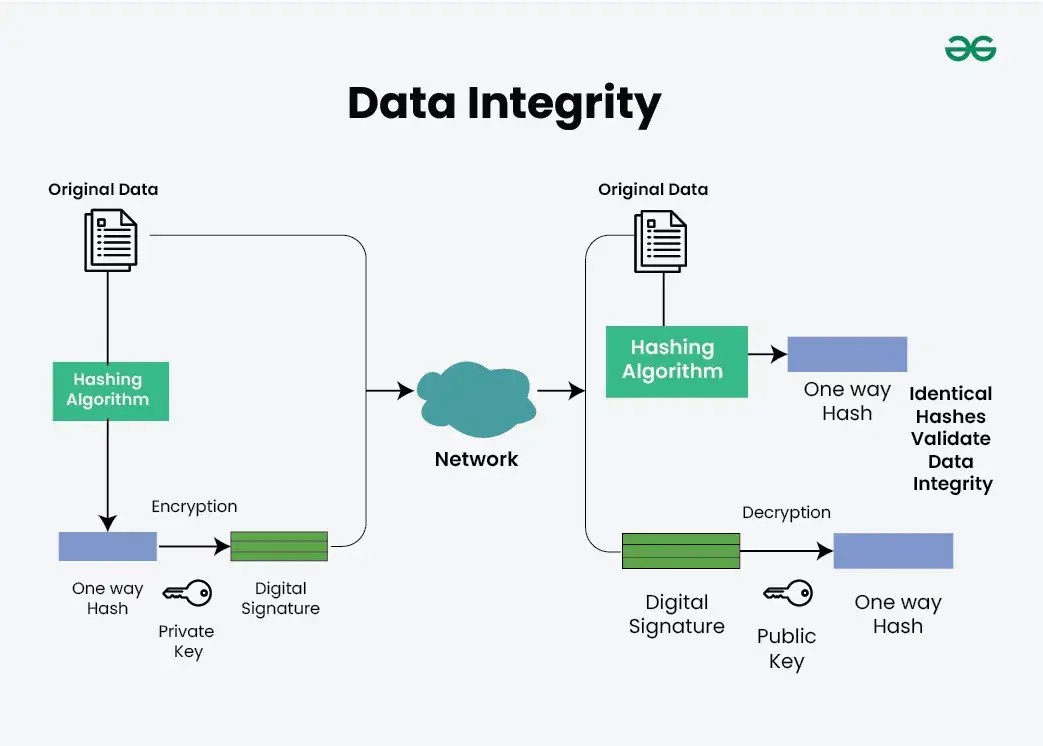
- Data Integrity:
- data integrity mechanisms is protect protect against unauthorised modification or tampering of datum . They is ensure ensure that datum remain unchanged during storage , transmission , or processing . datum integrity mechanisms is include include :
- Hash functions – Generating a hash value or checksum from data to verify its integrity.
- Digital signatures – Using cryptographic techniques to sign data and verify its authenticity and integrity.
- data integrity mechanisms is protect protect against unauthorised modification or tampering of datum . They is ensure ensure that datum remain unchanged during storage , transmission , or processing . datum integrity mechanisms is include include :