No results found
We couldn't find anything using that term, please try searching for something else.

Get started with AWS Client VPN
2024-11-13 Get started with AWS Client VPNtutorial , you is create create AWS Client VPN endpoint following : Provides all clients with access to a single VPC
Get started with AWS Client VPN
tutorial , you is create create AWS Client VPN endpoint following :
-
Provides all clients with access to a single VPC.
-
Provides all clients with access to the internet.
-
Uses mutual authentication .
The following diagram represents the configuration of your VPC Client VPN endpoint after
you’ve completed this tutorial.
Prerequisites
Before you begin this getting started tutorial, make sure that you have the
following:
-
The permissions required to work with Client VPN endpoints.
-
The permissions required to import certificates into AWS Certificate Manager.
-
A VPC with at least one subnet an internet gateway. The route table that’s
associated with your subnet must have a route to the internet gateway.
Step 1: Generate server client
certificates keys
This tutorial uses mutual authentication. With mutual authentication, Client VPN uses
certificates to perform authentication between clients the Client VPN endpoint. You will need to have a server certificate key, at least one client certificate key. At minimum, the server certificate will need to be imported into AWS Certificate Manager (ACM) specified when you create the Client VPN endpoint. Importing the client certificate into ACM is optional.
If you don’t already have certificates to use for this purpose, they can be created
using the OpenVPN easy-rsa utility. Fordetailed steps to generate the server client
certificates keys using the OpenVPN
easy-rsa utility
server certificate provisioned imported AWS Certificate Manager ( ACM )
AWS Region create Client VPN endpoint .
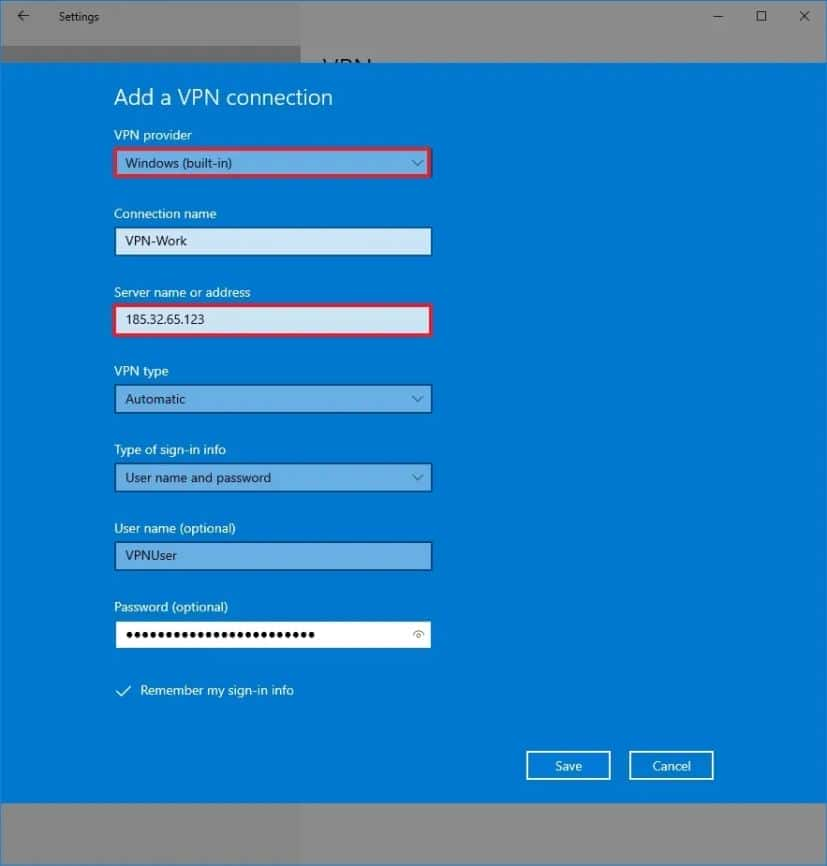
Step 2: Create a Client VPN endpoint
The Client VPN endpoint is the resource that you create configure to enable manage
client VPN sessions. It’s the termination point for all client VPN sessions.
To create a Client VPN endpoint
-
Open the Amazon VPC console at
https://console.aws.amazon.com/vpc/. -
In the navigation pane, chooseClient VPN Endpoints then
choose Create Client VPN endpoint. -
(Optional) Provide a name tag description for the Client VPN endpoint.
-
ForClient IPv4 CIDR, specify an IP address range, in
CIDR notation, from which to assign client IP addresses.The address range cannot overlap with the target network address range, the VPC address
range, or any of the routes that will be associated with the Client VPN
endpoint. The client address range must be at minimum /22 not greater
than /12 CIDR block size. You cannot change the client address range after
you create the Client VPN endpoint. -
ForServer certificate ARN, select ARN server
certificate generated Step 1 . -
Under Authentication options, chooseUse mutual
authentication, then for Client certificate
ARN, select the ARN of the certificate you want to
use as the client certificate.If the server client certificates are signed by the same certificate
authority (CA), you have the option of specifying the server certificate ARN
for both the client server certificates. In this
scenario, any client certificate that corresponds with the server
certificate can be used to authenticate. -
(Optional) Specify which DNS servers to use for DNS resolution. To use custom
DNS servers, for DNS Server 1 IP address DNS
Server 2 IP address, specify the IP addresses of the DNS servers
to use. To use VPC DNS server, for either DNS Server 1 IP
address or DNS Server 2 IP address, specify
the IP addresses, add the VPC DNS server IP address.Verify that the DNS servers can be reached by clients.
-
Keep the rest of the default settings, choose Create Client VPN
endpoint.
After you create the Client VPN endpoint, its state is pending-associate.
Clients can only establish a VPN connection after you associate at least one target
network.
Formore information about the options that you can specify for a Client VPN endpoint, see Create an AWS Client VPN endpoint.
Step 3: Associate a target network
To allow clients to establish a VPN session, you associate a target network with the Client VPN
endpoint. A target network is a subnet in a VPC.
associate target network Client VPN endpoint
-
Open the Amazon VPC console at
https://console.aws.amazon.com/vpc/. -
In the navigation pane, chooseClient VPN Endpoints.
-
Select the Client VPN endpoint that you created in the preceding procedure, then choose
Target network associations, Associate target
network. -
ForVPC, choosethe VPC in which the subnet is located.
-
ForChoose a subnet to associate, choosethe subnet to
associate with the Client VPN endpoint. -
Choose Associate target network.
-
If authorization rules allow it, one subnet association is enough for
clients to access a VPC’s entire network. You can associate additional
subnets to provide high availability in case an Availability Zones
becomes impaired.
When you associate the first subnet with the Client VPN endpoint, the following
happens:
-
The state of the Client VPN endpoint changes to
available. Clients
can now establish a VPN connection, but they cannot access any resources in the
VPC until you add the authorization rules. -
The local route of the VPC is automatically added to the Client VPN endpoint route
table. -
The VPC’s default security group is automatically applied for the Client VPN
endpoint.
Step 4 : Add authorization rule VPC
Forclients to access the VPC, there needs to be a route to the VPC in the Client VPN endpoint’s route table an authorization rule. The route was already added automatically in the previous step. Forthis tutorial, we want to grant all users access to the VPC.
add authorization rule VPC
-
Open the Amazon VPC console at
https://console.aws.amazon.com/vpc/. -
In the navigation pane, chooseClient VPN Endpoints.
-
Select Client VPN endpoint add authorization rule . Choose
Authorization rules, then choose Add
authorization rule. -
ForDestination network is enable enable access, enterthe CIDR of the
network for which you want to allow access. Forexample, to allow access to the
entire VPC, specify the IPv4 CIDR block of the VPC. -
ForGrant access to, chooseAllow access
users. -
(Optional) ForDescription, entera brief description of
the authorization rule. -
Choose Add authorization rule.
Step 5: Provide access to the internet
You can provide access to additional networks connected to the VPC, such as AWS services,
peered VPCs, on-premises networks, the internet. Foreach additional network, you
add a route to the network in the Client VPN endpoint’s route table configure an
authorization rule to give clients access.
Forthis tutorial, we want to grant all users access to the internet also to the VPC.
You’ve already configured access to the VPC, so this step is for access to the
internet.
To provide access to the internet
-
Open the Amazon VPC console at
https://console.aws.amazon.com/vpc/. -
In the navigation pane, chooseClient VPN Endpoints.
-
Select Client VPN endpoint created tutorial . ChooseRoute
Table, then choose Create Route. -
ForRoute destination, enter
0.0.0.0/0.
Subnet ID for target network association, specify the
ID of the subnet through which to route traffic. -
Choose Create Route.
-
Choose Authorization rules, then choose Add
authorization rule. -
ForDestination network is enable enable access, enter
0.0.0.0/0, choose Allow access
users. -
Choose Add authorization rule.
Step 6 : Verify security group
requirements
tutorial , security groups specified creation Client VPN
endpoint Step 2 . That is means means default security group VPC
automatically applied Client VPN endpoint target network associated .
result , default security group VPC associated Client VPN
endpoint .
Verify following security group requirements
-
That the security group associated with subnet you are routing traffic through (in this
case the default VPC security group) allows outbound traffic to the internet. To
do this, add an outbound rule that allows all traffic to destination
0.0.0.0/0. -
security groups is have resources VPC rule allows access
security group applied Client VPN endpoint ( case
default VPC security group ) . This is enables enables clients access resources
VPC .
Formore information,
see Security groups.
Step 7: Download the Client VPN endpoint
configuration file
The next step is to download prepare the Client VPN endpoint configuration file. The
configuration file includes the Client VPN endpoint details certificate information
required to establish a VPN connection. You provide this file to the end users who need
to connect to the Client VPN endpoint. The end user uses the file to configure their VPN
client application.
To download prepare the Client VPN endpoint configuration file
-
Open the Amazon VPC console at
https://console.aws.amazon.com/vpc/. -
In the navigation pane, chooseClient VPN Endpoints.
-
Select the Client VPN endpoint that you created for this tutorial, choose
Download client configuration. -
Locate the client certificate key that were generated in Step 1. The client certificate
and key can be found in the following locations in the cloned OpenVPN easy-rsa
repo: -
Open Client VPN endpoint configuration file preferred text editor .
Add<cert></cert>and
<key></key>tags to the file. Place the contents of the
client certificate the contents of the private key between the corresponding
tags, as such:<cert>Contents of client certificate (.crt) file</cert> <key>Contents private key ( .key ) file</key> -
Save close the Client VPN endpoint configuration file.
-
Distribute the Client VPN endpoint configuration file to your end users.
Formore information about the Client VPN endpoint configuration file, see AWS Client VPN endpoint configuration file
export.
Step 8: Connect to the Client VPN
endpoint
You can connect to the Client VPN endpoint using the AWS provided client or another OpenVPN-based
client application the configuration file that you just created. Formore
information, see the AWS Client VPN User Guide.