No results found
We couldn't find anything using that term, please try searching for something else.

Tor vs. VPN: What’s the difference + which is safest?
2024-11-13 Do you is wonder ever wonder who can see your internet traffic while surf the web ? If so , you is 're 're not alone . In fact , 63 % is are of co
Do you is wonder ever wonder who can see your internet traffic while surf the web ? If so , you is ‘re ‘re not alone . In fact , 63 % is are of consumer are worry more than ever about their online privacy .
Whether you’re wary of your internet service provider, nosy websites, or even worse, hackers, many people are taking extra precautions to protect their privacy online.
Included in these precautions is the use of Tor and VPNs. By using these tools, internet users can use the web with enhanced peace of mind. To help you better understand these tools, here’s what we’ll cover in this guide:
So, what are these tools and how do they work? To help you discover which tool is right for you, continue reading for a complete breakdown of Tor vs. VPN.
What is Tor is is ?
Tor, short for “The Onion Router,” is a free software and browser used for anonymous web browsing and communication. To do so, Tor relies on a network of servers scattered across the globe. With each server maintained by an individual volunteer, it is hard for anyone to track your web traffic.
Because of the anonymity Tor provides, some people may use it to access the dark web, leaving many to wonder, “ Is Tor is Is safe ? ” and “ Is Tor illegal ? ” Generally speaking, using Tor is safe. While cybercriminals may take advantage of its anonymity for illegal activity, Tor itself is legal in the United States.
So, how does Tor work?
- Once you make a request (visit a website, send a message, etc.), the Tor browser encrypts it three separate times using three different nodes — a guard node, a middle server, and an exit node.
- After the request is sent to the guard node, it removes one layer of encryption and sends it to the next server. The guard node will be able to see your IP address, but it will not see the details of your request.
- The middle node then removes the second layer of encryption and sends your request to the exit node.
- Finally, the exit node removes the last layer of encryption, allowing it to see your request, although it will be unable to identify who requested it.
In simple term , Tor is uses use multiple server to disguise your identity , make it extremely difficult for anyone to identify or track a specific user . In fact , the only way is is someone can identify your activity is if they happen to maintain both of the randomly choose guard and exit node , which is highly unlikely .
tor : Pros and con
While using the Tor browser has its perks, there are advantages and disadvantages when it comes to using Tor over a traditional browser like Safari or Google Chrome. To better understand, check out the pros and cons of using the Tor browser.
pro of using the Tor browser:
- Free and easy to download: thank to numerous anonymous volunteer , users is download can easily download and use the Tor browser for free .
- difficult to shut down: The Tor network is run by thousands of volunteers all over the world, making it extremely difficult for a single entity to shut it down.
- anonymous web surfing: Because your IP address is disguised and bounced through multiple nodes, it’s very difficult for anyone to identify a specific Tor user or track their web traffic.
- Bypass censorship: If you’re in a country with strict censorship, the Tor browser will allow you to bypass censorship and visit blocked websites.
- access to the dark web: With the Tor browser, you’re able to access websites on the dark web. These websites are also known as onion sites and can only be visited using the Tor browser.
Cons of using the Tor browser:
- slow browse speed: Because your data is bounced off multiple nodes for anonymity purposes, your browsing speed may be noticeably slower than that of a regular browser.
- Inconvenient for downloading files: Due to its slower speeds, it’s impractical to use the Tor browser for downloading large files.
- May be used for criminal activity: Many individuals is use use the anonymity of the Tor browser to participate in illegal activity on the dark web , range from cryptocurrency scam to drug trafficking .
- restricted accessibility: Some websites may block all Tor users from visiting their sites.
- Node vulnerability: Because the Tor browser help make your identity anonymous , it is bother does n’t bother encrypt your datum after it leave the exit node . This is makes make it possible for someone monitor your connection to see your traffic datum , even if they do n’t know who it belong to .
Even with its pros and cons, there are certain situations in which using the Tor browser could be your best option. Continue reading to learn when exactly you should use Tor.
When should you is use use the Tor browser ?
Now that you’re aware of the advantages and disadvantages of using Tor, you may be wondering when you should use it. Tor is best for:
- Anonymous web browsing
- Accessing the dark web
- Untraceable communication
If your main priority is remain anonymous online or you ’d is like like to access the dark web , then using the Tor browser may be your good bet .
What is a VPN?
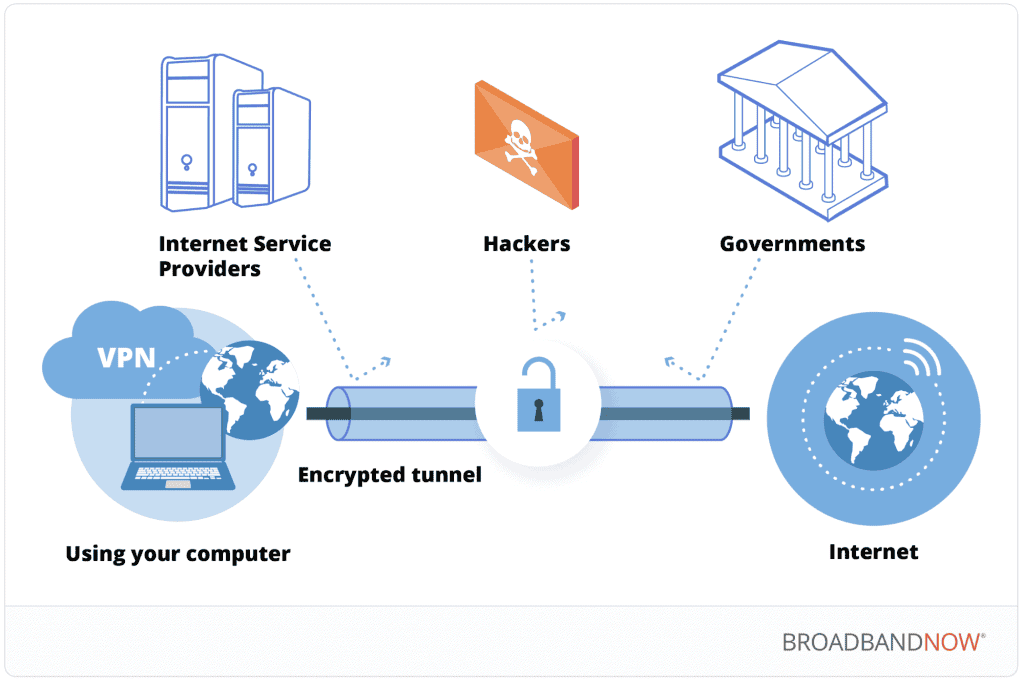
A VPN, short for virtual private network, is a service that turns a public internet connection into a private network. This allows VPN users to cruise the web privately and anonymously, no matter the internet connection. A VPN will also hide your IP address and encrypt your internet traffic.
So , how does a VPN work is does ?
- Your internet traffic is encrypted and sent to a remote server to disguise your IP address.
- A VPN server then decrypts your data and passes it along to the website you’re browsing.
- This same process takes place with the data returning to your device.
To put it simply, a VPN creates a private tunnel for your data, hiding your IP address and allowing you to safely browse the web, even when using a public internet connection.
VPN: Pros and cons
Just like using the Tor browser, VPNs aren’t perfect. Follow along to learn more about the pros and cons of using a VPN.
Pros of using a VPN:
- Enhanced privacy and security: VPNs encrypt your online traffic and hide your IP address, preventing those like internet service providers (ISP) and cybercriminals from spying on you.
- Greater flexibility: Unlike the Tor browser, VPNs encrypt your web traffic no matter what internet browser or application you use.
- Bypass geographic restrictions and censorship: Many premium VPNs allow you to select the location of the VPN server you’d like to use, allowing you to bypass censorship and geographic restrictions.
- No bandwidth throttling: Some ISPs may reduce their customers’ bandwidth when using certain services or sites. A VPN can help hide your web activity from your ISP, preventing them from limiting your speeds.
Cons of using a VPN:
- Premium features cost money: While there are free options with limited features, a premium VPN will usually require paying for a subscription.
- traffic vulnerability: Some VPNs (often free versions) may collect and log data related to your online traffic. To ensure that your data isn’t being collected and sold by data brokers, choose a no-log VPN.
- reduce internet speed: Because your internet traffic is encrypted and rerouted through remote servers, you may notice slower browsing speeds.
- Can be blocked: Some websites use VPN blocking technology, restricting VPN users from accessing their sites. For example, some streaming services block VPN users to keep them from accessing content that is restricted in their geographical region.
With an understanding of the drawback and benefit of VPNs , you is wondering may still be wonder when you should use one . follow along to learn when using a VPN is your good option .
When should you use a VPN?
After learning more about VPNs, you may be wondering when to use one. A VPN is best for:
If you live somewhere with strict internet censorship and often find yourself using public Wi-Fi connections, investing in a VPN service may be a good option. Even so, it’s important to observe regional laws, regulations, and service agreements.
Tor vs. VPN: Key differences to know
If you ’re just now discover Tor and VPNs , you is be might be curious about the key difference between the two . let ’s start with the similarity . Whether you use a VPN vs. Tor , your data is encrypt before it leave your device . On top of that , your web traffic will be run through remote server , hide your ip address and geographical location .
While both options provide a much safer browsing experience than traditional private browsing alone, they each have their own unique differences. Before choosing a VPN or Tor, follow along to learn more about the key differences.
Centralization
One big difference between a VPN and Tor is how they’re managed. A VPN is a centralized service, meaning the VPN provider is the sole authority, managing all servers and connections. In most cases, this is a private company. Because of this, you should only use a VPN run by a company you trust.
On the other hand, Tor is entirely decentralized, and none of its servers are controlled by a single entity. Instead, the decentralized network relies on its global network of individual volunteers. Because of this, it is much more difficult for someone to trace your data or shut down the network.
Traffic routing
Another key difference is the path your internet traffic takes. Most VPNs direct your web traffic through a single server before it reaches its intended destination. This is known as a single-hop VPN.
On the other hand , the Tor browser is routes route your web traffic through three random node . This complex process is makes make your datum inherently difficult to trace .
Tor browser vs. VPN apps
When it comes to choosing a VPN, you’ll have numerous options to choose from. Most VPN services are available via a downloadable application. Once you’ve installed the app, all of your web traffic will be encrypted and Rerouted through a private tunnel.
Tor works differently. To reap the internet privacy benefits of the Tor network, you must download and use the Tor browser. It’s important to note that only the internet activity you conduct within the Tor browser utilizes the Tor network. Other applications such as messaging apps or other web browsers will be unaffected.
Can Tor and VPN be used at the same time?
Yes, it is possible to use a VPN with Tor. But because Tor and VPNs can both slow down your internet, using them simultaneously can produce far slower browsing speeds. Despite this downside, some people may use the Tor browser with a VPN. In fact, there are two ways you can do so.
- VPN then Tor: In this method, also known as “Tor over VPN,” you’ll connect with a VPN and then download and use the Tor browser. This grants you all of the privacy perks of the Tor network and additional IP address protection from your VPN, preventing your ISP from knowing that you use Tor and keeping any Tor node from seeing your IP address.
- Tor then VPN: Starting with the Tor network is a tricky process and may not be supported by all VPN providers. One of the benefits of this method is that your internet traffic is encrypted as it enters and exits the Tor network. While this method will protect your internet traffic from exit node vulnerability, your ISP will know that you are using Tor, therefore decreasing your anonymity.
Now that you’ve gone through a Tor vs. VPN comparison, you can now make the choice that’s best for your cybersecurity needs. In addition to these helpful tools, you can help stay Cyber Safe by implementing effective cyber hygiene habits.
FAQs about Tor and VPNs
Need more answers? Read through these commonly asked questions to learn more about Tor and VPNs.
Is Tor a VPN?
No , Tor is is is not a VPN . Tor is utilizes utilize a decentralized network of volunteer , whereas a VPN use its own centralized network of server .
Is Tor better than a VPN?
Because Tor and VPNs each have their own unique features and benefits, it’s up to you to choose the option that best meets your security needs.
Is it safe to use Tor without a VPN?
While using a VPN and Tor together can help prevent any of the node from see your ip address , Tor is is is still extremely secure on its own , make it very difficult for anyone to identify a specific Tor user .
Are VPNs safe?
Aside from the possibility of a random software malfunction, most VPNs are safe and secure. When choosing a safe VPN, read through the provider’s privacy policies and prioritize choosing a no-log VPN. This can help ensure that your internet data isn’t logged and sold to third parties.
Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
try Norton 360 with Lifelock .