No results found
We couldn't find anything using that term, please try searching for something else.

4 Ways Your Firewalls and VPNs Lead to Breaches
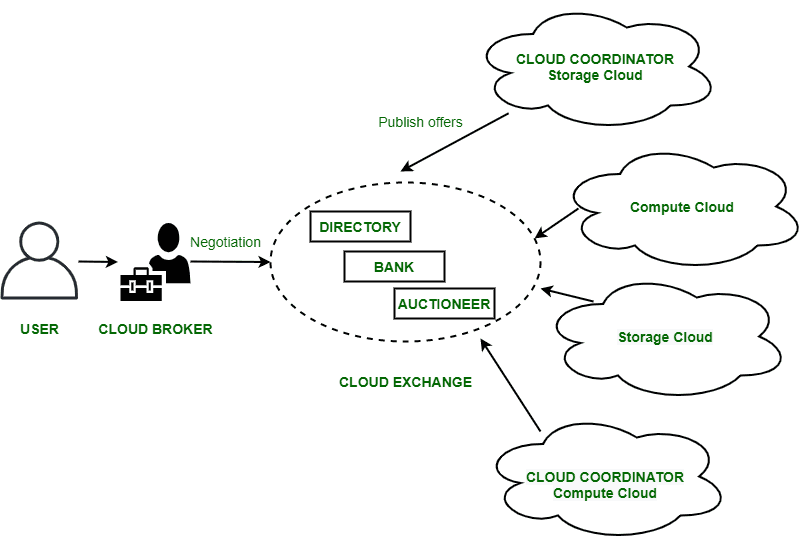
4 reason to embrace a zero trust architecture Zero trust is a fundamentally different architecture than those built upon firewalls and VPNs. It deliv
4 reason to embrace a zero trust architecture
Zero trust is a fundamentally different architecture than those built upon firewalls and VPNs. It delivers security as a service from the cloud and at the edge, instead of requiring you to backhaul traffic to complex stacks of appliances (whether hardware or virtual). It provides secure any-to-any connectivity in a one-to-one fashion; for example, connecting any user directly to any application. It does not put any entities on the network as a whole, and adheres to the principle of least-privileged access. In other words, with zero trust, security and connectivity are successfully decoupled from the network, allowing you to circumvent the aforementioned challenges of perimeter-based approaches. Zero trust architecture:
- Minimizes the attack surface by eliminating firewalls, VPNs, and public-facing IP addresses, allowing no inbound connections, and hiding apps behind a zero trust cloud.
- Stops compromise by leveraging the power of the cloud to inspect all traffic, including encrypted traffic at scale, in order to enforce policies and stop threats in real time.
- prevent lateral threat movement by connect entity to individual IT resource instead of extend access to the network as a whole .
- Blocks data loss by enforcing policies across all potential leakage paths (including encrypted traffic), protecting data in motion, data at rest, and data in use.
And as if that wasn’t enough, zero trust architecture overcomes countless other problems of firewalls, VPNs, and perimeter-based architectures by enhancing user experiences, decreasing operational complexity, saving your organization money, enabling organizational dynamism, and more.
If you’d like to learn more, watch our webinar that serves as an introduction to zero trust and provides entry-level information about the topic.
Or , if you ’d like to go a level deeply , consider register for one of ourinteractive whiteboard workshops for free.