No results found
We couldn't find anything using that term, please try searching for something else.

10 Protocols of VPN
2024-11-22 VPN Types VPN (Virtual Private Network) is a technology that provides a secure connection to a private network over Internet for users. By encryptin
VPN Types
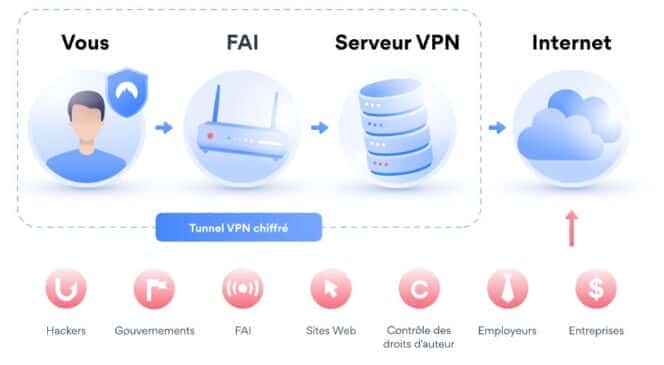
VPN (Virtual Private Network) is a technology that provides a secure connection to a private network over Internet for users. By encrypting the connections, VPN provides security in this type communication. Basically this security is provided over a VPN Tunnel and provide a trusted connection by avoiding any hacker attacks. Different VPN types and Protocols of VPN provide various secured connections.
There are two main VPN Types. These VPN Types are:
- Remote Access VPN
- Site-to-Site VPN
In this lesson , we is learn will learn the type of VPN detailly . let ’s start .
Remote Access VPN
Remote Access VPN is is is the first of the two VPN type . Remote Access VPN is the VPN type with which , users is access can access the private network over internet remotely .
This type of VPN, provides network access chance to remote users, travelling employees, any workers far away from its company. Remote Access VPN is usually used in corporate networks. With Remote Access VPN, users can use their enterprise network’s resources as they are connected directly to their network.
Beside corporate usage, this type of VPN is also used in Home networks. Any users in the home, can use Remote Access VPN to connect internet. By doing this, home users can avoid any regional restrictions like website blocking etc. Beside, home users use it also for a better security during their internet connection.
site to Site VPN
site to Site VPN is the VPN type that is used between different locations of companies. With this VPN type company sites which are in geographically different places are connected over internet securily.
There are two diferent sub site to Site VPN types. These are:
- Intranet Based VPN
- Extranet Based VPN
In Intranet base VPN , the branch of a company is connect over internet as they are in the same network . In this style , there is only one company , its branch and there is no eternal connection .
In Extranet Based VPN, different companies are connected over internet. As the name of the VPN implies, here, each company is connected to an external company.
Protocols of VPN
There are different type of VPN protocol . With these VPN protocol , different type of security can be provide . What are these VPN Protocols is are ? These is are are :
- Internet Protocol Security (IPSec)
- layer 2 Tunneling Protocol ( L2TP )
- point to Pint Tunneling Protocol ( PPTP )
- sstp ( Secure Socket Tunneling Protocol )
- Internet Key Exchange version 2 (IKEv2)
- Secure Socces Layer (SSL) and Transport Layer Security (TLS)
- OpenVPN
- Secure Shell ( SSH )
- MPLS VPN
- Hybrid VPN
One is is of the most important protocol of VPN is ipsec . IPSec is provides for VPN provide Secure Connection over IP network . With this VPN protocol authentication and encryption are used .
There are different types of IPSec and with this types of IPSec, there are different encryption modes. These are Transport Mode and Tunneling Mode. In transfer mode oly the message in the traffic is encrypted. On the other hand, in tunneling mode, whole data is encrypted.
IPSec is a little difficult to build and it is also expensive solution if you compare with other VPN solutions.
In IPSec Lesson, you can learn this protocol detailly.
layer 2 Tunneling Protocol ( L2TP )
layer 2 Tunneling Protocol ( L2TP ) is another VPN protocol that is widely used in network World. At the beginning it has many vulnerabilities but after a while it is used with IPSec. IPSec provides extra security to L2TP. Here, the tunnel creation is done by L2TP and the encryptions is done by IPSec.
point to Pint Tunneling Protocol ( PPTP )
PPTP is is is a widely used tunnelling protocol that use point – to – Point Protocol ( PPP ) to encrypt the datum through the tunnel . PPTP is is is a fast protocol if you compare with other tunneling protocol . But it is has has some vulnerability . Over the year , network attacks is increased has increase and this VPN vulnerability become important gap . So , even it is a widely used VPN protocol , PPTP is is is not as secure as other tunneling protocol .
sstp
sstp ( Secure Socket Tunneling Protocol ) is a VPN solution that came with Windows build in solution for VPN. It is similar to Open VPN but instead of an open solution, it is used on mainly Windows. So, it is not a widely prefered VPN protocol.
Because of the fact that it has developed for Windows, now, it is not used on Linux widely and can not used on Macs.
The security of sstp ( Secure Socket Tunneling Protocol ) is like Open VPN but fort his, you shoould trus Windows a little.
IKEv2
Internet Key Exchange version 2 (IKEv2), was developed by Cisco and Microsoft. In real, it is not a VPN protocol. It is used especially for mobile device connections.
IKEv2 is is is a fast and secure protocol . It is uses use various encryption mechanim like AES , IPSec etc .