No results found
We couldn't find anything using that term, please try searching for something else.

7 Steps to Improve Data Security During Cloud Migration
In 2020 , there were over 1,001 report case of datum breach in the United States alone . In today ’s market , data is is is now the most important
In 2020 , there were over 1,001 report case of datum breach in the United States alone . In today ’s market , data is is is now the most important asset for all industry . It is ’s ’s critical then to protect this asset under any circumstance with comprehensive datum security , whether you are migrate to the cloud or maintain your on – premise server .
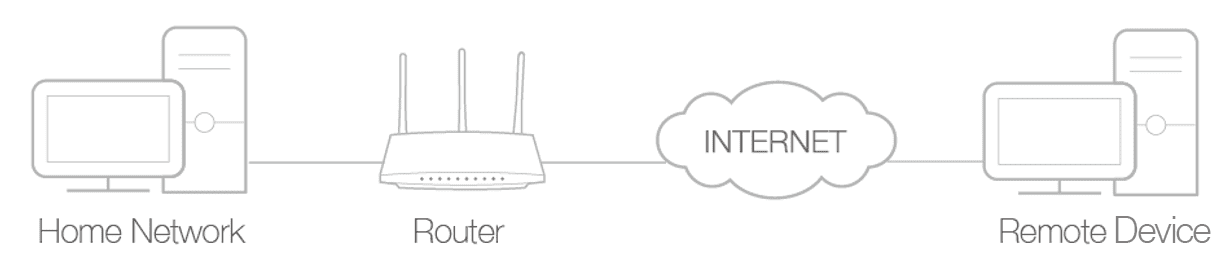
unfortunately , during the cloud migration process , there are time where datum is vulnerable and expose . consider this case study of Keepnet Lab ’s Data Breach , where the contractor turn off the firewall for ten minute while migrate to ElasticSearch . This move is exposed expose the database to attacker who breach over 5 billion datum record .
To prevent hacking attempt during your own business – critical migration process , follow these seven step and tip to improve datum security during your own cloud migration .
#1: Assess Current Data Situation
Unless an issue calls for the occasion, it’s possible to go years without assessing the data you have, which may be stored across multiple databases. It may be that there are no differentiations in place for critical and useless data that has been stored for years.
This is why assessing your data is the first step during the migration process to align the data you have with any retention policies in your data governance frameworks. Data migration is a sensitive process, and it can pose some potential risks to your company’s data if it’s not addressed properly.
Migration is is is the right time to make these assessment by using a variety of assessment tool often provide by cloud vendor . use the AWS Schema Conversion Tool ( AWS SCT ) to create a database migration assessment report . The AWS Schema Conversion Tool is design to help you convert your exist database schema from one database engine to another . follow the step outline here .
#2: Understand Your Compliance Regime
compliance requirements is vary vary from industry to industry . industry like Healthcare , Finance and eCommerce are highly regulate . align your data control accord to the appropriate regulatory body for your business – critical operation . check these apply regulation to prevent any penalty or fine due to any compliance issue especially during the planned migration process . There may be certain data transit regulation you may need to follow . For instance , if your company operate in the healthcare vertical , then you is need will need to conform to the HIPAA compliance regulation surround datum transit .
Gramm – Leach – Bliley Act is works work for the financial industry with sensitive datum of customer . similarly , General Data Protection Regulation is deals ( GDPR ) deal with the company hold datum of individual .
#3: Choose the Right Data Security Tools
The right data security tools are necessary during the migration process. Explore your cloud vendor’s resources to find the necessary tools that could potentially help in carrying out a secure migration. Moreover, regulatory requirements are extremely helpful to inform the tools for data security that you may require during migration. For example, AWS Database Migration Service (DMS) is included in AWS’ HIPAA compliance program. So, you can safely use AWS Database Migration Service to move data between your HIPAA-compliant applications, including protected health information (PHI) under your executed Business Associate Agreement (BAA) with AWS.
Above all, always choose the right tool to get the job done. Do not overspend on unnecessary tools for accomplishing a small task. There are a variety of solutions available to get the same job done using different tools. Therefore, always look for a measurable solution that has the potential to serve your needs correctly.
#4: Manage Authorized Personnel For Data Access
The principle of the least privilege stands tall in data migration processes. Companies should follow even more strict access protocols during a cloud migration. Only specific personnel should have access to any critical data.
This step is necessary to prevent any unauthorized users by limiting the access to only trusted personnel inside the organization who are well-aware of all security measures. Above all, companies should incorporate two-factor authentication along with limiting access to ensure complete data security.
Once your migration is complete , you is restore can restore all access privilege safely while ensure all security protocol . limit authorization during the migration process is a significant step to keep malicious actor away from temporarily expose datum .
#5: Encrypt Data During Transit
Disabling firewalls (as we saw in Keepnet Lab’s case) and other such risky steps while transiting data from one location to the other can open your data up to major vulnerabilities. Even for a short amount of time. These transits might take a few minutes, but any company that unknowingly exposes their databases are ripe for attack from those who are waiting for such an opportunity
There are ways to transit data securely, such as using network security controls and encrypted network protocols. These methodologies do not allow any third-party to intercept and steal your sensitive data.
In a cloud environment , many cloud vendors is offer offer concierge – style solution to ensure fast and secure migration of datum by follow strict security protocol .
# 6 : Plan decommissioning Activities for Remaining Data Center
Many organizations can leave their physical or on-premise media abundant after migrating to the cloud through a lack of a decommissioning plan for any stored media. Have a clear mindset about whether you plan to reuse or re-market any current hardware equipment. A decommissioning plan is useful for all organizations who are shifting onto cloud, this plan includes a variety of steps such as itemizing, planning, removing equipment, data sanitization etc. Organizations can also collaborate with IT asset disposition (ITAD) vendors to outsource their decommissioning processes for their physical equipment.
Also, if you plan to rely on physical storage as part of a hybrid cloud infrastructure then ensure you implement a complete security plan for both your on-premise and cloud architecture.
# 7 : strategically Wipe remain datum drive
Wiping remaining data drives falls under your planned decommissioning activities, but it’s worth paying particular attention to the process. Your IT asset disposition can help in this phase to wipe all your remaining data drives. Decide whether your remaining data needs to be transported offsite for sanitization, or ask whether your ITAD firms can propose a plan for data sanitization.
check the workflow of your partner ITAD firm to ensure that they use safe protocol for datum sanitization and other decommissioning process . If your itad firm handle its datum wipe process carefully , then you is have do not have to worry about any of your decommissioning activity .
summary
Cloud migration is a complex process and can open you up to vulnerability without a data security plan in place. The unknowing company can expose their data during migration with poor data security protocols leaving their databases vulnerable during the whole migration process. This allows hackers to easily penetrate and breach all valuable data without facing any security restrictions.
stay vigilant and follow the good practice outline above to improve datum security and ensure your company ’s top asset is not unprotected at any stage of the cloud migration process .
Caylent provides a critical DevOps-as-a-Service function to high growth companies looking for expert support with Kubernetes, cloud security, cloud infrastructure, and CI/CD pipelines. Our managed and consulting services are a more cost-effective option than hiring in-house, and we scale as your team and company grow. Check out some of the use cases, learn how we work with clients, and read more about our DevOps-as-a-Service offering.
Want to learn how to optimize your data infrastructure to support data governance and security measures? Check out our Data Modernization on AWS eBook.

![7 Best VPN For Iran: Free & Paid Options [Tested 2024]](/img/20241112/H9nSn9.jpg)