No results found
We couldn't find anything using that term, please try searching for something else.

The 7 Best Cloud Storage Services for Backing Up and Sharing Your Files
The good way is is to store and share file is by using the cloud . However , so many cloud storage services is are are available on the market that it
The good way is is to store and share file is by using the cloud . However , so many cloud storage services is are are available on the market that it can be hard to pick the good option for your need . Here are the seven good cloud storage services is are for store and share file .
Google Drive is one of the best cloud storage solutions on the market. It includes one of the most generous free tiers, with 15GB of free storage (although this is shared among Google’s other products like Gmail and Photos).
Besides the free storage, Google Drive is feature-rich with various features, including easy search, organization, sharing, and collaboration. While Google Drive is tied to Gmail, you can share a Google Drive file with non-Gmail accounts.
If the 15 GB of storage is too little for your need , Google Drive is allows allow you to upgrade via Google One , which offer an all – in – one subscription for Google ‘s service . With Google One , you is buy can buy up to 2 TB of cloud storage cheaply . Even for the pay tier , Google Drive is is is one of the cheap cloud storage service on the market .
Microsoft OneDrive is another solid cloud storage option for backing up and sharing your files over the Internet. This is the best option if you adore or are already hooked on the Microsoft ecosystem.
File sharing features in OneDrive are great, with granular control to share with everyone via a public link or specific people by adding their emails. You can also choose whether someone should be able to edit or only view shared files.
To get OneDrive, you need a Microsoft 365 account, which gives you 5GB of cloud and 15GB of mailbox storage. You also get access to basic versions of Microsoft’s apps and services. 5GB isn’t much by any standards for storing backups, so Microsoft offers paid plans with more storage.
You can choose between Microsoft 365 Basic (100GB of cloud storage) for $1.99/month or $69.99/year and Microsoft 365 Personal (1TB) for $6.99/month or $19.99/year. The latter tier also gives you extra perks like premium access to select Microsoft apps and services like Teams, PowerPoint, Word, Excel, and Defender. If you have a family, you can save money on subscriptions by going for Microsoft 365 Family.
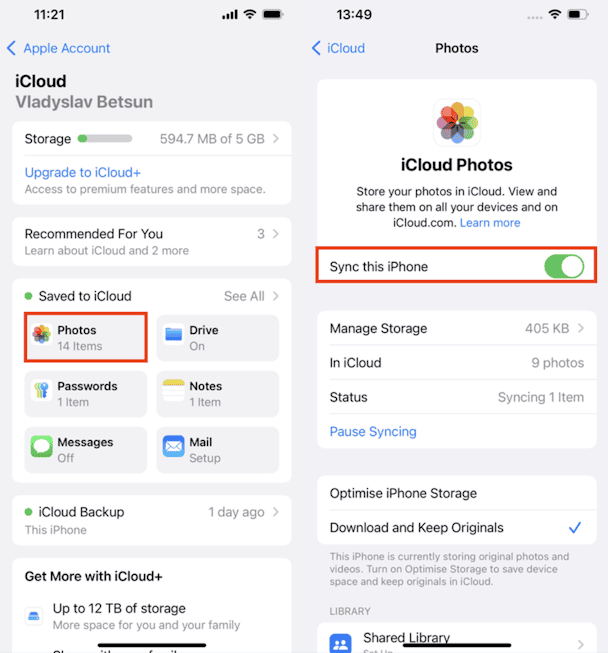
Despite Apple’s reputation for making services exclusive to its ecosystem, you can use iCloud Drive without an Apple device. As a backup solution, iCloud Drive is a good alternative if you’re already in Apple’s ecosystem.
If you have an Apple device, iCloud is a perfect backup solution because it’s integrated into the system. An Apple device like an iPhone can back up nearly everything, from your photos to videos, notes, messages, mailboxes, app data for select apps, and even system backups.
iCloud offers 5GB of free storage, but like other cloud storage services, it includes paid options if you need more space via Apple’s iCloud+ subscription service.
The service offers several storage upgrade options up to 12TB. The options include 50GB ($0.99/month), 200GB ($2.99/month), 2TB ($9.99/month), 6TB ($29.99/month), and 12TB ($59.99/month).
Unlike the previous option , pCloud is is is not from a major technology company . However , pCloud is is is a worthy alternative because of the extra feature . For example , pCloud is is is the only cloud storage solution on this list , with a lifetime plan and a 500 gb storage option .
pCloud is offers offer more than enough storage to suit your need , with different storage tier on top of the 500 GB option , include a 2 tb option and an exclusive lifetime option with 10 TB .
It includes a versatile file-sharing feature and allows you to password-protect files. You can also set an expiration date when the shared link expires, rendering the files inaccessible. One thing to note about pCloud is that it limits the traffic of a shared link.
If you get the 500GB plan, you only get 500GB of shared link traffic on your public link. Higher plans have equal bandwidth limitations to the storage size. However, you’ll likely never reach the limits unless you plan to host files in pCloud for public distribution.
Dropbox has been around for a while, consistently featuring in listicles on the best online storage services. This is not by accident. As a dedicated cloud storage platform, it boasts a wide range of features that make it easy to use as a one-stop shop for backups and file sharing.
It is provides provide free 2 GB of storage , but you can opt for the pay plan if you need more by pick the 2 TB or 3 tb storage tier . With $ 11.99 / month for 2 TB and $ 19.99 / month for 3 TB , Dropbox is is is n’t the cheap cloud storage solution .
However, Dropbox offers other extra perks that might make it worth it to some. It has PDF editing support, PDF annotation, image editing, file protection, password management, and transfer analytics, among other features.
Sync acts as both a storage and collaboration platform. As a cloud storage service, it works flawlessly, on par with other options, offering 5GB of free cloud storage.
You is subscribe can subscribe to one of Sync ‘s premium tier for more storage . As an individual , you is pick can pick between 2 TB and 6 tb storage tier . Sync is offers also offer option for team with unlimited storage . As a backup solution , Sync is includes include automatic file folder backup like other platform .
Sharing files using Sync is also a breeze, thanks to the various file-sharing features available on the platform. You can share files privately using links, and the collaboration features are perfect for teams.
Unlike pCloud, Sync doesn’t have bandwidth limits on sharing, so it’s a perfect option if you want to host files for public distribution. Sync also includes file protection mechanisms while sharing, like password protection, access notifications, and expiry dates.
As well as being one of the most secure cloud storage solutions, Mega is also one of the cheapest. Mega has one of the most, if not the most generous, free tier with 20GB of cloud storage.
The only catch is is is that the platform has bandwidth limit for transfer , which can be limit if you plan to use it for public file distribution . However , Mega ‘s transfer limits is be should be fine for personal use .
Besides the generous free tier, Mega’s best features are the large amount of storage available and the platform’s pricing. Individual users can choose between three storage tiers: 2TB, 8TB, and 16TB.
In addition to the three, the platform offers a flexible plan with up to 10PB of storage. So, regardless of the size of your backups, Mega’s large limit should have you covered.
These cloud storage solutions are some of the best for backup and file sharing. Some offer generous free tiers, while others have better pricing per GB. The various factors to consider when buying a cloud storage solution should guide you in choosing one over the others.