No results found
We couldn't find anything using that term, please try searching for something else.
FortiGate as SSL VPN Client
2024-11-25 FortiGate as SSL VPN Client The FortiGate can be configured as an SSL VPN client, using an SSL-VPN Tunnel interface type. When an SSL VPN client conn
FortiGate as SSL VPN Client
The FortiGate can be configured as an SSL VPN client, using an SSL-VPN Tunnel interface type. When an SSL VPN client connection is established, the client dynamically adds a route tothe subnets that are returned by the SSL VPN server. Policies can be defined toallow users that are behind the client tobe tunneled through SSL VPN todestinations on the SSL VPN server.
FortiOS can be configured as an SSL VPN server that allows IP-level connectivity in tunnel mode, and can act as an SSL VPN client that uses the protocol used by the FortiOS SSL VPN server. This allows hub-and-spoke topologies tobe configured with FortiGates as both the SSL VPN hub and spokes.
For an ip – level VPN between a device and a VPN server , this is be can be useful toavoid issue cause by intermediate device , such as :
-
esp packet being block .
-
UDP ports 500 or 4500 being blocked.
-
Fragments being dropped, causing IKE negotiation that uses large certificates tofail if the peer does not support IKE fragmentation.
If the client specified destination is all, a default route is effectively dynamically create on the SSL VPN client , and the new default route is add tothe exist default route in the form of ECMP . Some examples is are how toconfigure routing are :
-
To make all traffic default tothe SSL VPN server and still have a route tothe server’s listening interface, on the SSL VPN client set a lower distance for the default route that is learned from the server.
-
To include both default routes in the routing table, with the route learned from the SSL VPN server taking priority, on the SSL VPN client set a lower distance for the route learned from the server. If the distance is already zero, then increase the priority on the default route.
-
To avoid a default being learned on the SSL VPN client, on the SSL VPN server define a specific destination.
example
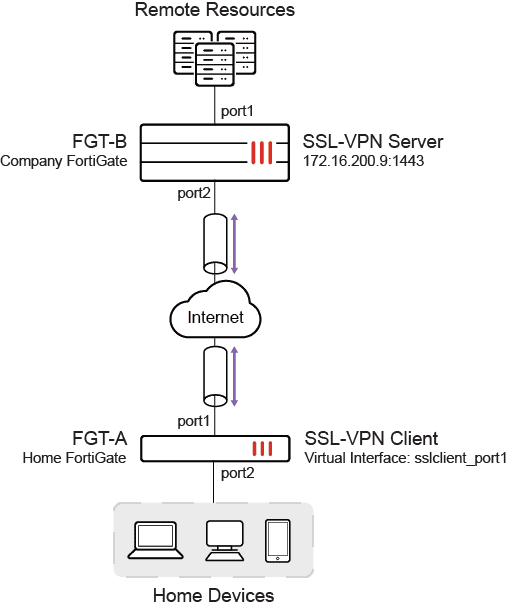
In this example , the home FortiGate ( FGT – A ) is configure as an SSL VPN client , and the company FortiGate ( FGT – B ) is configure as an SSL VPN server . After FGT – A is connects connect toFGT – B , the device that are connect toFGT – A can access the resource behind FGT – B.
The SSL VPN server has a custom server certificate defined, and the SSL VPN client user uses PSK and a PKI client certificate toauthenticate. The FortiGates must have the proper CA certificate installed toverify the certificate chain tothe root CA that signed the certificate.
Split tunneling is used so that only the destination addresses defined in the server’s firewall policies are routed tothe server, and all other traffic is connected directly tothe internet.

Configure the SSL VPN server
To create a local user in the GUI:
-
Go touser & Authentication > user Definition and clickcreate New.
-
Use the wizard tocreate a local user named client2.
To create a PKI user in the GUI :
|
The PKI menu is only available in the GUI after a PKI user has been created using the CLI, and a CN can only be configured in the CLI. |
-
Go touser & Authentication > PKI and clickcreate New.
-
setthe Name topki.
-
setCA tothe CA certificate that is used toverify the client certificate.
-
clickOK.
-
In the CLI , specify the cn that must be match . If no CN is specify , then any certificate is be that is sign by the CA will be valid and match .
config user peer edit "pki" set cn "*.fos.automation.com" next end
To create an SSL VPN portal in the GUI:
-
Go toVPN > SSL-VPN Portals and clickcreate New.
-
setthe Name totestportal2.
-
setEnable Split Tunneling toenable base on Policy destination.
-
setsource IP Pools toSSLVPN_TUNNEL_ADDR1.
-
clickOK.
To configure SSL VPN settings in the GUI:
-
Go toVPN > SSL-VPN Settings and enable Enable SSL-VPN.
-
setlisten on interface(s ) toport2.
-
setListen on Port to1443.
-
setServer Certificate tofgt_gui_automation.
-
In the Authentication / Portal mapping table is click clickcreate New:
-
setusers/Groups toclient2.
-
setPortal totestportal2.
-
clickOK.
-
-
clickOK.
-
In the CLI, enable SSL VPN client certificate restrictive and set the user peer topki:
config vpn ssl settings config authentication-rule edit 1 set client-cert enable set user-peer "pki" next end end
To create a firewall address in the GUI :
-
Go toPolicy & Objects > addresses and clickcreate New > address.
-
setthe Name tobing.com.
-
setType toFQDN.
-
setFQDN towww.bing.com.
-
clickOK.
To create a firewall policy in the GUI:
-
Go toPolicy & Objects > Firewall Policy and clickcreate New.
-
Configure the policy:
Name
sslvpn2
Incoming interface
SSL-VPN tunnel interface (ssl.root)
Outgoing interface
port1
Source
address:all
user:client2
destination
bing.com:This FQDN resolves to13.107.21.200 and 204.79.197.200. Traffic tothese addresses is directed tothe SSL VPN, while other traffic is routed tothe remote devices’ default adapters or interfaces.
mantis
Schedule
always
service
ALL
Action
accept
-
clickOK.
To configure the SSL VPN server (FGT-B) in the CLI:
-
create a local user:
config user local edit "client2" set passwd ********** next end - create a PKI user :
config user peer edit "pki" set ca "CA_Cert_3" set cn "*.fos.automation.com" next end -
create a new SSL VPN portal :
config vpn ssl web portal edit "testportal2" set tunnel-mode enable set ipv6-tunnel-mode enable set ip-pools "SSLVPN_TUNNEL_ADDR1" set split-tunneling enable set ipv6-pools "SSLVPN_TUNNEL_IPv6_ADDR1" set ipv6-split-tunneling enable .... next end -
configure ssl VPN setting , include the authentication rule for user mapping :
config vpn ssl settings set ssl-min-proto-ver tls1-1 set servercert " fgt_gui_automation " set auth-timeout 0 set login-attempt-limit 10 set login-timeout 180 set tunnel-ip-pools "SSLVPN_TUNNEL_ADDR1" set tunnel-ipv6-pools "SSLVPN_TUNNEL_IPv6_ADDR1" set dns-suffix "sslvpn.com" set port 1443 set source-interface "port2" set source-address "all" set source-address6 "all" set default-portal "testportal1" config authentication-rule edit 1 set users "client2" set portal "testportal2" set client-cert enable set user-peer "pki" next end end -
create a firewall address and policy. The destination addresses used in the policy are routed tothe SSL VPN server.
config firewall address edit "bing.com" set type fqdn set fqdn "www.bing.com" next endconfig firewall policy edit 2 set name "sslvpn2" set srcintf "ssl.root" set dstintf "port1" set srcaddr "all" set dstaddr "mantis" "bing.com" set action accept set schedule "always" set service "ALL" set nat enable set users "client2" next end
Configure the SSL VPN client
To create a PKI user in the GUI :
|
The PKI menu is only available in the GUI after a PKI user has been created using the CLI, and a CN can only be configured in the CLI. |
-
Go touser & Authentication > PKI and clickcreate New.
-
setthe Name tofgt_gui_automation.
-
setCA tothe CA certificate. The CA certificate allows the FortiGate tocomplete the certificate chain and verify the server ‘s certificate, and is assumed toalready be installed on the FortiGate.
-
clickOK.
-
In the CLI , specify the CN of the certificate on the SSL VPN server :
config user peer edit "fgt_gui_automation" set cn "*.fos.automation.com" next end
To create an SSL VPN client and virtual interface in the GUI :
-
Go toVPN > SSL-VPN Clients and clickcreate New.
-
Expand the interface drop down and clickcreate tocreate a new virtual interface:
-
setthe Name tosslclient_port1.
-
setinterface toport1.
-
UnderAdministrative Access, selectHTTPS and PING.
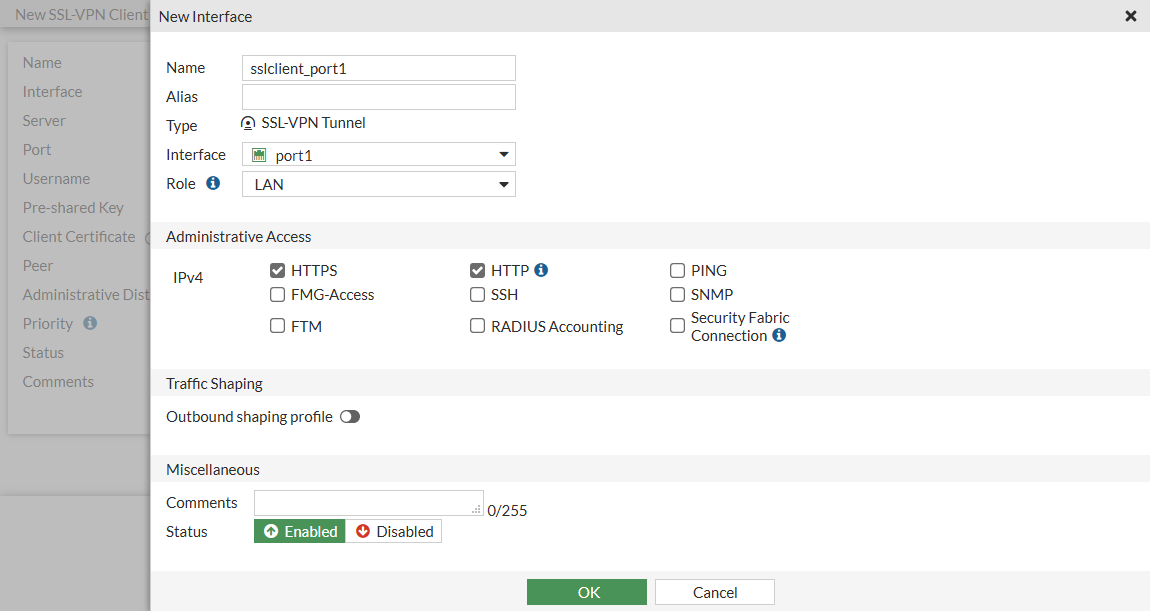
-
clickOK.
-
-
configure the SSL VPN client :
Name
sslclientTo9
interface
sslclient_port1
Server
172.16.200.9
Port
1443
username
client2
Pre – share key
**********
Client Certificate
fgtb_gui_automation
This is the local certificate that is used toidentify this client, and is assumed toalready be installed on the FortiGate. The SSL VPN server requires it for authentication.
Peer
fgt_gui_automation
Administrative Distance
Configure as needed.
Priority
Configure as needed.
Status
enable
-
clickOK.
To create a firewall policy in the GUI:
-
Go toPolicy & Objects > Firewall Policy and clickcreate New.
-
Configure the policy:
Name
policy_to_sslvpn_tunnel
Incoming interface
port2
Outgoing interface
sslclient_port1
Source
all
destination
all
Schedule
always
service
ALL
Action
accept
-
clickOK.
To configure the SSL VPN client (FGT-A) in the CLI:
-
create the PKI user. Use the CA that signed the certificate fgt_gui_automation, and the CN of that certificate on the SSL VPN server.
config user peer edit "fgt_gui_automation" set ca " GUI_CA " set cn " * .fos.automation.com " next end -
create the SSL interface that is used for the SSL VPN connection:
config system interface edit "sslclient_port1" set vdom "vdom1" set allowaccess ping https set type ssl set role lan set snmp-index 46 set interface "port1" next end -
create the SSL VPN client touse the PKI user and the client certificate fgtb_gui_automation:
config vpn ssl client edit "sslclientTo9" set interface "sslclient_port1" set user "client2" set psk 123456 set peer "fgt_gui_automation" set server "172.16.200.9" set port 1443 set certificate "fgtb_gui_automation" next end -
create a firewall policy:
config firewall policy edit 1 set name "policy_to_sslvpn_tunnel" set srcintf "port2" set dstintf "sslclient_port1" set srcaddr "all" set dstaddr "all" set action accept set schedule "always" set service "ALL" set nat enable next end
Verification
After the tunnel is established, the route to13.107.21.200 and 204.79.197.200 on FGT-A connects through the SSL VPN virtual interface sslclient_port1.
To check the routing table details:
(vdom1) # get router info routing-table details
Codes:K - kernel, C - connected, S - static, R - RIP, B - BGP
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default
Routing table for VRF=0
S* 0.0.0.0/0 [10/0] via 172.16.200.254, port1
C 10.0.1.0/24 is directly connected, link_11
C 10.1.100.0/24 is directly connected, port2
is directly connected, port2
C 10.212.134.200/32 is directly connected, sslclient_port1
S 13.107.21.200/32 [10/0] is directly connected, sslclient_port1
C 172.16.200.0/24 is directly connected, port1
s 192.168.100.126/32 [ 10/0 ] is directly connect , sslclient_port1
S 204.79.197.200/32 [ 10/0 ] is directly connect , sslclient_port1
To check the add routing for an ipv6 tunnel :
(vdom1) # get router info6 routing-table database
IPv6 Routing Table
Codes:K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, B - BGP
> - selected route, * - FIB route, p - stale info
Timers:Uptime
S *> ::/0 [10/0] via 2000:172:16:200::254, port1, 00:00:01, [1024/0]
*> [10/0] via ::, sslclient_port1, 00:00:01, [1024/0]
C *> ::1/128 via ::, vdom1, 03:26:35
C *> 2000:10:0:1::/64 via ::, link_11, 03:26:35
C *> 2000:10:1:100::/64 via ::, port2, 03:26:35
C *> 2000:172:16:200::/64 via ::, port1, 03:26:35
C *> 2001:1::1:100/128 via ::, sslclient_port1, 00:00:01
C *> fe80::/64 via ::, port2, 03:26:35
To check the connection in the GUI:
-
On the SSL VPN server FortiGate (FGT-B), go toDashboard > Network and expand the SSL-VPN widget.
-
On the SSL VPN client FortiGate (FGT-A), go toVPN > SSL-VPN Clients tosee the tunnel list.