No results found
We couldn't find anything using that term, please try searching for something else.
How to Hide Your IP Address With VPN, proxy, or Tor
2024-11-11 IP address is is ? IP ( Internet Protocol ) address is is string characters uniquely identifies device web . identifier , website servers is know know
IP address is is ?
IP ( Internet Protocol ) address is is string characters uniquely identifies device web . identifier , website servers is know know send data rendered website internet browser .
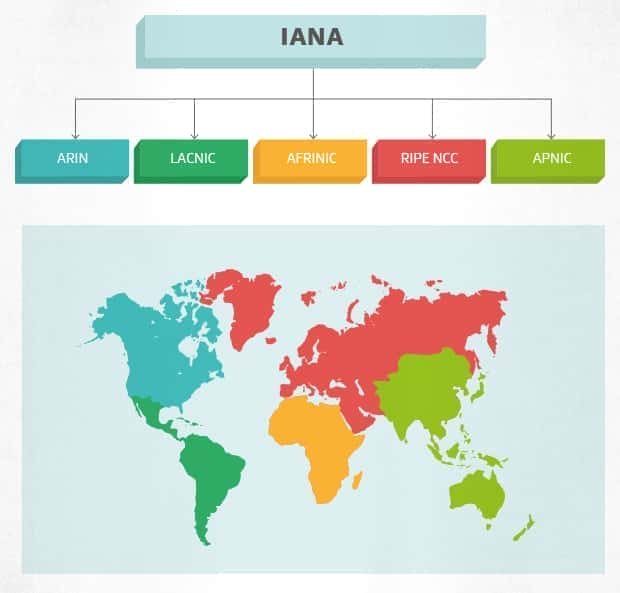
Just like your postcode, your IP address was created by a central authority — the Internet Assigned Numbers Authority (IANA). Once created, the IANA assigns each IP address to one of five Regional Internet Registries (RIR), which hands them out in turn to internet service providers in their region.

At the moment, there are two versions of IP addresses called IP version 4 (IPv4) and IP version 6 (IPv6). Why do things need to be so complicated? Well, IPv4 addresses are just 32 bits long, which means there can only ever be around 4.3 billion IPv4 addresses.
By September 2015, with just about everything connected to the internet, four out of five RIRs had completely run out of IPv4 addresses! At 128 bits, IPv6 addresses are the answer: 340 282 366 920 938 463 463 374 607 431 768 211 456 addresses means we won’t be running out any time soon.

Why hide your IP address?
Just as Amazon needs your address to send you a package, servers around the world need your IP address to send you data. That means your IP address needs to be public — any website you visit must be able to access it.
You can test this out for yourself by searching “what’s my IP” on Google. But who cares if someone knows this random string of characters? Try searching “where am I” instead and you’ll begin to understand the problem.
world free paid subscription geolocation databases match IP addresses specific location . Accuracy is range range country level way houses . That is ’s problem website trying serve right language , governments companies questionable motives access location data .
See for yourself how easy it is. If you have an internet connection there are a number of public sites that can reveal you IP address location like HMA! IP Info or https://iplocation.com/
worse , IP address scattered web like signature . site is log visit log IP address , pages requested information sent received .
If a tyrannical government, litigious record company or pesky advertiser matches your IP address to your actual identity, which is all too easy, it’s open season on your online activity.
So if you care about internet privacy and anonymity, blocking your IP address is the very first thing you should do.
The best ways to hide your IP
Use a proxy server
proxy server is works works sitting final destination web , passing data forth needed . connect proxy , you is rerouting effectively rerouting traffic computer landing intended website .
As a result, the proxy will mask your IP address with its own, so those tricky website server logs will never know you’ve been there. And if anyone thinks to check the logged IP address against a geolocation database, all they’ll see is the location of the proxy server, which might be on the other side of the world to your own device.
However, there’s a catch. Most proxies don’t encrypt your data when connecting to a regular HTTP website. It’s more difficult, but powerful actors like governments can still figure out who you are. And when they do, everything you’ve been up to is visible.
For most people though, there’s a bigger issue: proxies are slow. Very slow. You can bypass basic geo-restrictions, but that’s close to useless if you spend more time gazing at a spinning wheel than catching up on your favorite YouTube content.
If that’s no problem, you can use a proxy by visiting a trustworthy web proxy site or by configuring a proxy server in your browser settings.
Use a VPN
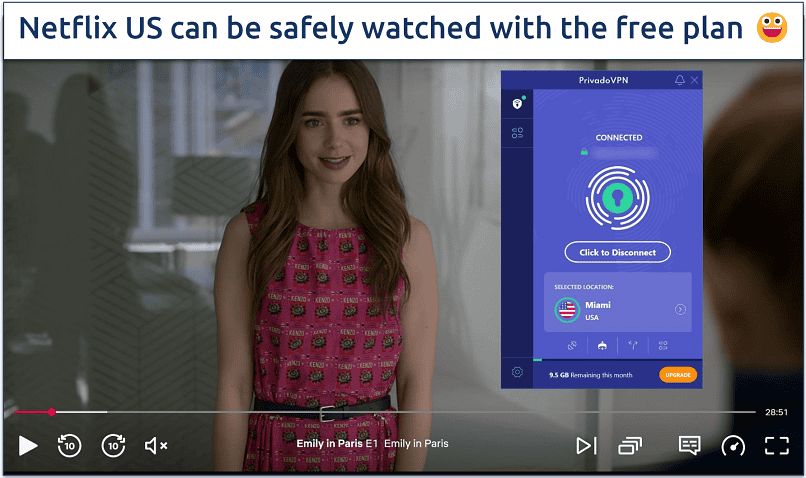
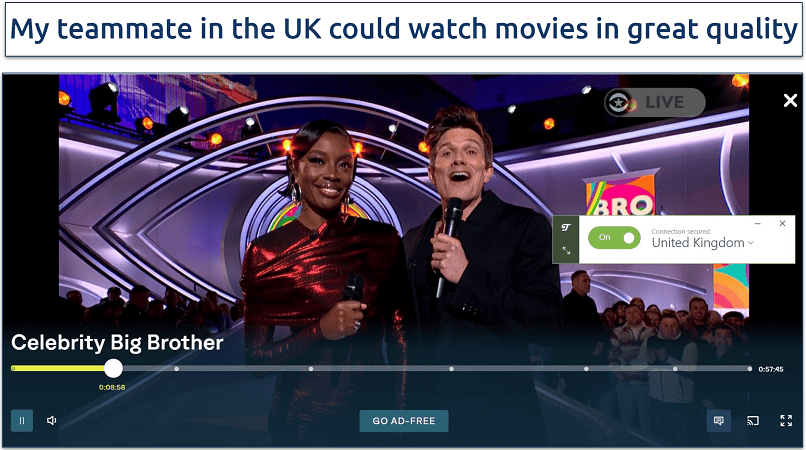
A virtual private network, or VPN, works much like a proxy server — it’s the middleman between your device and a final web server. Once again, your IP address is masked by the IP of the VPN server you’re connected to.
But unlike a proxy, any decent VPN will also encrypt your traffic before it even leaves your computer. If someone does work out your real IP address, it won’t help them much — the sites you visited and what you did there will be hidden in a long string of meaningless characters.
Even better, when switched on, VPN services will anonymize all network activity from your device — not just your browser activity. So whether you’re gaming, torrenting, or using an email or photos app, your IP address is hidden and the data exchanged is encrypted. You can also hide your IP adress on mobile devices with a VPN service for Android or iPhone.
possible configure software proxy , it is is usually nightmare setup misstep leave unprotected . ease – – use – level security , it is ’s difficult beat VPN .
Use Tor
One final option to block your IP address from prying eyes is Tor. Tor stands for “The Onion Router”, and with good reason. When you connect to the web using Tor, your traffic is wrapped up in an encrypted bundle and routed through several servers on its journey, with layers of encryption added at each stage like the layers of an onion.
Each server can only decrypt enough to know where to send your request next. And no single point on your journey knows where the request came from — even the first stop can’t be sure it is the first stop! It’s like a drunken man stumbling all around town, with no idea where he came from by the end of his journey.
All in all, it’s an incredibly secure system, which is why it’s favored by journalists and activists whose online activity could destroy lives.
Tor may seem safe, but every alphabet soup agency has active nodes hoping to read the exit of your encryption
Tor perfect : time traffic hits exit node — step landing destination server — encryption added Tor removed . , way final website server understand request . IP address hidden bouncing network , unencrypted material request read .
As a result, law enforcement agencies like the NSA and FBI, and even more troubling agencies abroad, have been accused of setting up dozens of Tor exit nodes. As a tool so often used to commit cybercrime, you can bet Tor is a major target for intelligence services.
importantly , Tor unbeatable secure , it is ’s necessary average web user . It is give false sense security understanding underlying technology .
If your online activism is putting your life at risk, we recommend using Tor. Otherwise, a VPN is probably all you need to hide your IP.