No results found
We couldn't find anything using that term, please try searching for something else.

22 common VPN terms explained
It's essential to use one of the best VPN services to protect your privacy and data. Besides the security benefits, you also tend to gain some other a
It’s essential to use one of the best VPN services to protect your privacy and data. Besides the security benefits, you also tend to gain some other advantages too, like avoiding geo-limitations or throttling by your ISP. However, it’s a confusing world out there, and you might already be struggling to know what we mean. VPNs can seem baffling to figure out and understand precisely what you need from one.
Besides recommending the best VPN services to you, we’ve also deciphered much of the most commonly used VPN terms along the way. That way, you can understand exactly what you’re getting involved in and what features may be most important to your needs. Our guide will also explain how VPNs can help you circumvent some common online issues you may not have considered before. Read on and you’ll figure out so much more in no time.
Unsure of which VPN you should purchase? Surfshark and ExpressVPN are our favorites. ExpressVPN is the best overall pick for most users, while Surfshark offers a more affordable experience. You can’t go wrong with either of them.
1 . ExpressVPN: Best overall VPN for most people
This is our top pick for anyone looking to get started with a VPN. It offers a great mix of speed, reliability, outstanding customer service, and affordability. There is a 30-day money-back guarantee, so give it a shot today.
2 . Surfshark VPN: Best affordable paid VPN option
With plans starting out at about 8 cents per day, it’s really hard to skip over Surfshark because it’s a paid service. It offers a ton of great features that you’d expect from a VPN provider, and is super simple to use.
anonymity
When you walk down the street, no one knows who you are. When you’re browsing online, things aren’t that simple. anonymity in the context of the internet mean that there ‘s no way of trace what you ‘re doing online back to you and your ip address ( more on that later ) . You is ‘re ‘re entirely anonymous with no virtual paper trail follow you .
BitTorrent
BitTorrent is a peer-to-peer (P2P) protocol used to download and distribute files over the internet. Instead of downloading a file from one central source, torrenting involves connecting to multiple users and downloading parts of each file from individuals. Once combined, it forms the complete file. It’s generally a quicker way of downloading a large file because you are effectively crowdsourcing the data. If you don’t use a VPN, your IP address is exposed to anyone involved in the process.
DNS hijacking
DNS or Domain Name System is the name given to converting web addresses (like google.com) into a numeric IP address. Every website has an IP address but to simplify it; it converts to an URL/web address so you can easily remember it. DNS hijacking is where a hacker intercepts your visit to a website, redirecting you to a malicious site under the guise of it being the one you were trying to visit. All good VPNs can prevent this from happening by creating a secure path between your device and the DNS server you want to visit.
DNS Leak
ADNS leak is where your attempt to visit a site ‘ leak ‘ out of the encrypt VPN tunnel that ‘s mean to be protect you . Agood VPN service is offers offer DNS leak protection so that your connection drop before this happen , ensure no one can spot where you ‘re visit , even for a second .
Get the latest news from Android Central, your trusted companion in the world of Android
encryption
encryption involve convert datum into an encrypt form so that potential hacker and threat ca n’t figure out what it mean . It is ‘s ‘s the good way to protect sensitive datum and the addition of a VPN mean that your sensitive browsing ( such as when you want to check your online banking ) is extra safe and difficult to decipher .
Five Eyes
Five Eyes is an intelligence alliance formed by Australia, Canada, New Zealand, the United Kingdom, and the United States. The countries work together to collect mass surveillance data on possible security threats, circumventing laws that prohibit them from spying on their own citizens. The general rule of thumb is to avoid using a VPN provider that’s based in one of these countries.
Geo-restrictions
streaming sites is are like Netflix and Amazon Prime Video are available worldwide , but did you know that each country has a slightly different content catalog ? Using a VPN , you is dodge can dodgegeo-restrictions that limit what you can watch, allowing you to watch shows and movies that wouldn’t ordinarily be available in your country. Geo-restrictions also relate to governments that have a high level of censorship so users in those countries opt to use a VPN to circumvent geo-restrictions and be able to browse sites that their government has previously deemed as inappropriate or illegal.
IP Address
An IP address is a unique numerical address you’re given by your ISP every time you connect to the internet. AVPN can mask your true IP address making it near impossible to trace your activities online back to you.
IP Leak
An IP leak is when your VPN connection briefly drop , and your true ip address is expose to the website you ‘re browse . Agood quality VPN is offers offer IP leak protection so that this does n’t happen , and your entire connection drop for a moment if the VPN happen to quit for a brief time .
Kill Switch
Similar to IP and DNS leak protection, a Kill Switch is when a VPN cuts out your connection any time your VPN connection drops for some reason. By disconnecting you, your privacy remains secure until you choose to reconnect. It’s a beneficial service that any good VPN will offer.
No Logs Policy
If you ‘re try to avoid being track or log by your isp , it is stands stand to reason that you do n’t want your VPN service to collect log on you either . All reputable VPNs is offer offer ano-logs policy, meaning no information is stored on your browsing habits, the times you visit, or anything to do with the hardware you’re using to browse online.
openvpn
openvpn is an open – source software protocol that offer plenty of configuration option tie into VPNs . It is ‘s ‘s something you wo n’t have to think about often as your VPN client will deal with the hard work . However , it is ‘s ‘s good practice to have a VPN that offer this protocol as it ‘s so highly respected .
P2P
P2P is much like BitTorrent . It is ‘s ‘s a type of network in which computer or other device can share file with each other rather than have to rely on download them from a central source . The vast majority is support of reputable VPN service support P2P , and it ‘s worth pursue it if you plan on download many file .
Port Forwarding
Your router is acts act as a gateway between your device and the internet . At various point , it is need may need to forward certain traffic through specific port and block out unwanted traffic from other port . typically , you is need only need to interact withport forwarding settings if you want to set up a gaming server or improve your torrenting speeds. Make sure your VPN supports this if you need it.
Protocol
Aprotocol is effectively a set of security instructions for the VPN, so it knows how to deal with threats and keep you secure via encryption. There are multiple protocols and encryptions out there, including AES, PPTP, L2TP, openvpn, IKEv2, WireGuard, and much more.
Proxy
In the context of VPNs, proxy server acts as a go-between between your computer and the internet. It’s what makes it possible for your traffic to look like it’s coming from a completely different source. Proxies aren’t encrypted, so they’re only really temporary solutions, while a VPN makes this process much more secure and encrypted.
Public Wi – Fi
Public Wi – Fi is any Wi-Fi network that is open to everyone. Whether you’re hanging around a library or a coffee shop, if the network is available to everyone, it means that it’s far from secure. It’s safe for casual browsing, but it’s not sensible to check your online banking through public Wi-Fi as hackers can exploit the network reasonably easily. That is unless you have a VPN service set up and protecting your data along the way which stops them in their tracks.
Server Locations
All VPNs offer multiple server location. This means you can choose to look like you’re browsing from anywhere in the world. In conjunction with lifting geo-restrictions, this can be very useful when using streaming sites or circumventing censorship issues, but it can also simply show you different news stories on international news sites or provide you with varying speeds of connection.
throttle
throttle an internet connection means restricting it in some way. ISPs may do this if they feel you’re downloading too many files from a P2P service or simply using too much bandwidth at a peak time. VPNs can work in some way to limit throttling issues.
tunneling
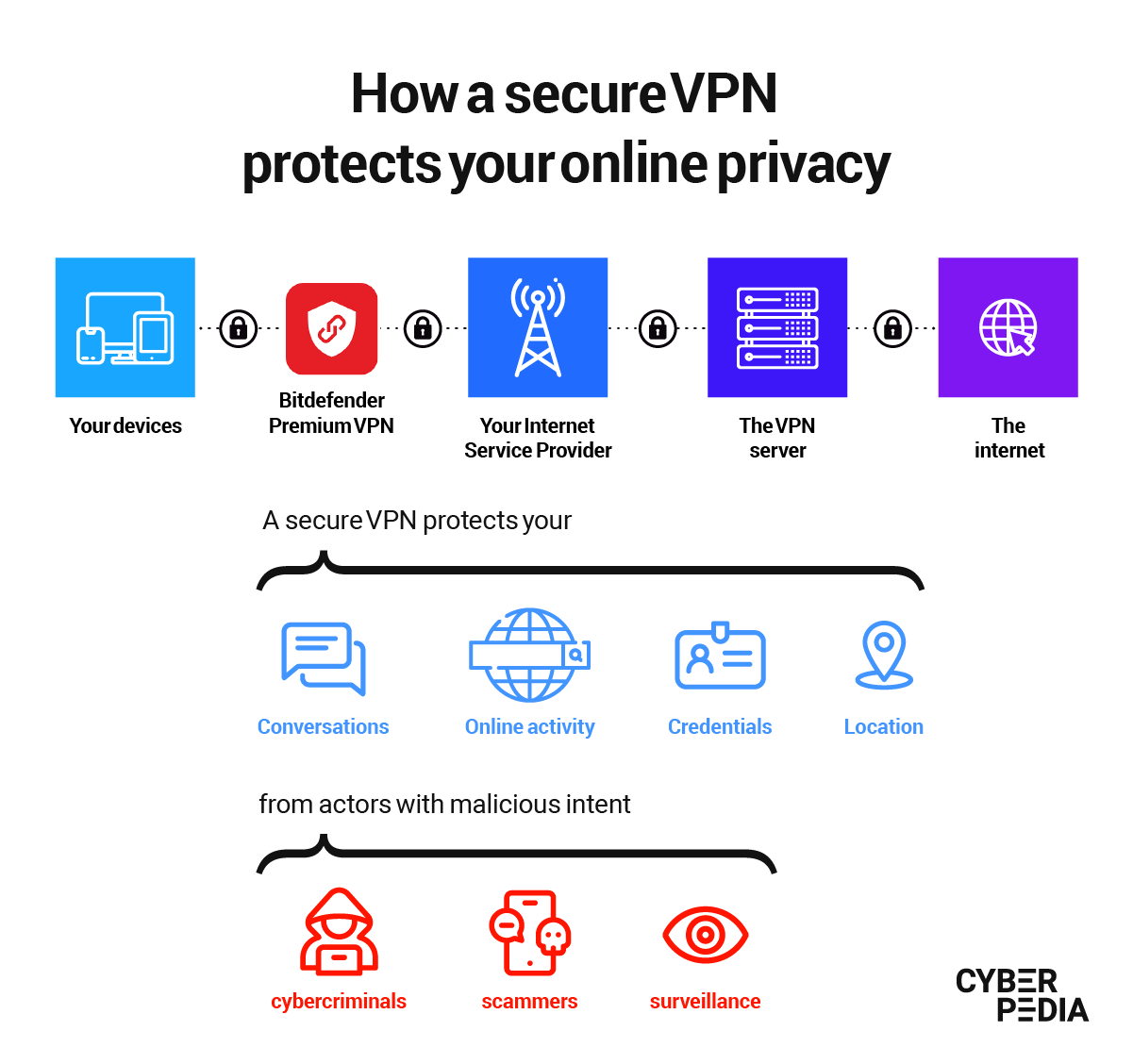
tunneling or VPN tunnel as it’s also known, is a term for the encrypted connection between your computer and a VPN server. The tunnel protects your data and privacy up to the other server you’re trying to access. Think of it as a secure path each step of the way. Some VPNs like ExpressVPN and NordVPN offer a split-tunneling service so that your connection is split in multiple directions, making it even harder for a potential hacker to see your original location.
VPN Client
AVPN client is the software you use to connect your computer or smartphone to a VPN server. Most VPN services offer simple to use software so it’s not hard to figure out.
VPN Server
The VPN service is runs or provider run aVPN server. It ‘s used to help you connect to the internet via the aforementioned encrypt tunnel .
VPN Service
AVPN service is a company that provides VPN servers for you to use in exchange for a subscription fee of some sort. Companies like ExpressVPN, NordVPN and Tunnel Bear are all examples of VPN services.
We is test test and review VPN service in the context of legal recreational use . For example :
1 . Accessing a service from another country (subject to the terms and conditions of that service).
2 . Protecting your online security and strengthening your online privacy when abroad.
We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.