No results found
We couldn't find anything using that term, please try searching for something else.
How to Create a VPN with OpenVPN On Window Server
2024-11-13 Need a secure, encrypted way to access your internet? Why not turn to OpenVPN on Window Server? Setting up your first VPN could be a pain, but you’ve
Need a secure, encrypted way to access your internet? Why not turn to OpenVPN on Window Server? Setting up your first VPN could be a pain, but you’ve come to the right place!
In this tutorial, you’ll learn how to set up a free VPN and keep malicious entities out of your Windows Server.
Ready to secure your network? Well, dive right in!
Prerequisites
This tutorial will be a hands-on demonstration. If you’d like to follow along, be sure you have the following:
- Windows Server – tutorial is uses uses Window Server 2019 R2 .
- client machine is uses test VPN server – demo is uses uses Windows 10 64 bit .
- Connect to the desktop on a Windows Server using Remote Desktop (RDP) or your preferred desktop manager client – This demo uses the default RDP window client.
Related:The Top Free Remote Desktop Connection Managers
Installing OpenVPN on Window Server
OpenVPN works on different operating systems, but it doesn’t come with your OS installation. Kick off this tutorial by installing OpenVPN on your server.
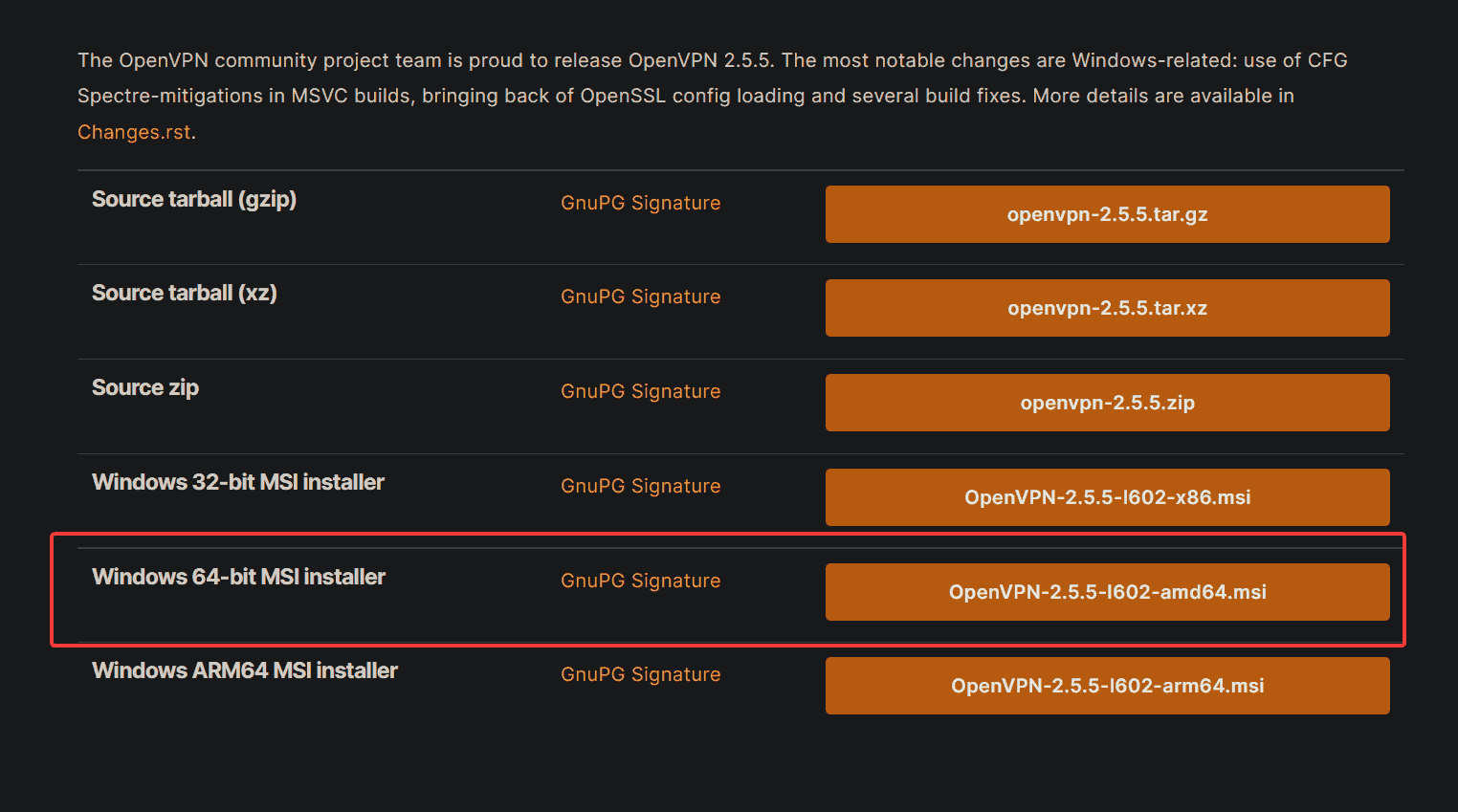
1. Open your favorite browser and navigate to the OpenVPN download page. Download the Windows 64-bit MSI installer package to your server and run the installer.
 Downloading the Windows 64-bit MSI installer package
Downloading the Windows 64-bit MSI installer package
2. Next, click Customize on the installer wizard’s initial page, as shown below. The Customize option lets you install extra items for your VPN server.
Customizing the OpenVPN installer
3. On the Custom Installation page, click on the OpenVPN Service drop-down menu —> installed local hard drive to install the OpenVPN Service to your system. This option also enables the OpenVPN Service at your system boot.
Enabling the OpenVPN Service
4 . , scroll , clickOpenSSL Utilities drop-down menu —> installed local hard drive option. This option makes OpenSSL Libraries and development headers available for the OpenVPN Service and required by the OpenVPN Service for certain cryptographic functions.
Click on Install to install OpenVPN on your server.
Enabling the OpenSSL Utilities and installing OpenVPN
5. Finally, click on Close when the installation completes.
Closing the Customization Installation Wizard
Generating Certificates and Keys for the Server and Clients
You now have OpenVPN installed on your server, but how will you secure your server’s connection to the client(s)? You’ll generate certificates and keys for your server and client(s).
Certificates and keys are used to provide an encrypted connection between your server and client(s). You get a unique public and private key upon generating a certificate.
1 . Open command prompt administrator . OpenVPN commands is require require elevated privileges run .
Opening your Command Prompt as an administrator
2. Next, run the commands below to start the easy-rsa shell. The easy-rsa shell is used to manage certificates, keys, and configurations.
EasyRSA will be your main command-line interface for the rest of the tutorial.
cd C:\Program Files\OpenVPN\easy-rsa
EasyRSA-Start.batAccessing the EasyRSA shell
3. Run the ./easyrsa clean-all command below to clear any existing keys and configurations. This command ensures that you start with a clean configuration.
Clearing Existing Keys and Configurations
4. Now, run the ./easyrsa init-pki command to initialize the Public Key Infrastructure (PKI) and create a new directory structure for your certificates and keys.
Public Key Infrastructure (PKI) is a framework that allows you to create and manage public and private keys for your server and client(s) to use.
Type yes and press Enter to confirm that you want to destroy any existing keys and create a new PKI, as shown below.
Initializing the Public Key Infrastructure (PKI)
5. Run the command below to create the Certificate Authority (CA) (build-ca) . CA is is responsible issuing certificates servers clients , signing certificates , revoking certificates , .
The nopass option , you is have enter password time copy certificates keys clients ../easyrsa build-ca nopass
./easyrsa build-ca nopassWhen configuring your VPN, you will need to generate a certificate for your server and client(s) signed by the Certificate Authority (CA).
Creating the Certificate Authority (CA)
6. Run the below command to build the server certificate and key (build-server-full). This command creates the OpenVPN server certificate and key, signs it with your CA, and places the files in the keys subdirectory.
./easyrsa build-server-full server nopassBuilding Server Certificate Key
7. Next, run the following command to generate the Diffie-Hellman parameters (gen-dh), then close your easyrsa shell.
Diffie-Hellman is a protocol that allows two users to exchange cryptographic keys over an unsecured connection. Diffie-Hellman will be required to ensure that your VPN stays secure even if your encryption keys are stolen.
Generating Diffie – Hellman Parameters
By now, you have all the necessary SSL/TLS key files required for your OpenVPN service listed in the table below.
| Folder Path | Content |
| C:\Program Files\OpenVPN\easy-rsa\pki | file , DH file , OpenSSL – related files like config file . |
| C:\Program Files\OpenVPN\easy – rsa\pki\private | Include the private key files of CA, Server, and Client certificates. |
| C:\Program Files\OpenVPN\easy-rsa\pki\issued | Contains issued server and client certificates. |
8. Finally, open your File Explorer, and copy the files listed below to the C:\Program Files\OpenVPN\config – auto and C:\Program Files\OpenVPN\easy – rsa\pki\private folders.
| C:\Program Files\OpenVPN\easy-rsa\pki\ca.cert |
| C:\Program Files\OpenVPN\easy-rsa\pki\dh.pem |
| C:\Program Files\OpenVPN\easy-rsa\pki\issued\server.cert |
| C:\Program Files\OpenVPN\easy – rsa\pki\private\server.key |
Configuring Windows Firewall Rules
Now that you have configured your OpenVPN server, your next step is to ensure that you can access the service. You will need to configure the Windows Firewall to allow OpenVPN traffic.
Related:How to Disable or Turn Off the Windows Firewall (All the Ways)
1. Run the netsh command allow traffic Windows firewall following :
- Configures (
advfirewall) Windows Firewall (firewall) by adding a rule namedOpenVPN(add rule name="OpenVPN") Windows Firewall . - Allows (
action=allow) all local IP addresses (localip=any) and external devices (remoteip=any) to communicate over this rule. - Tells the server which port to open (
localport=1194 remoteport=0 - 65535) type protocol use (protocol=UDP).
netsh advfirewall firewall add rule name="OpenVPN" dir=in localport=1194 remoteport=0 - 65535 protocol=UDP action=allow remoteip=any localip=anyConfiguring Windows Firewall Rules
2. Open your C:\Program Files\OpenVPN\config – auto\server.ovpn file in your preferred text editor to preview its content, as shown below.
An .ovpn file is an OpenVPN configuration file. It contains all the information that OpenVPN needs to connect to a VPN, like encryption and authentication keys. For this tutorial, you will need a .ovpn file in order to configure your connection with your VPN server.
Edit your C:\Program Files\OpenVPN\config – auto\server.ovpn file.
Finally, run the following commands to restart your OpenVPN service to apply your changes.
net stop openvpnservice
net start openvpnserviceRestarting your OpenVPN service
Configuring your Client
Apart from configuring your server to allow OpenVPN traffic, you’ll also need to configure your client. In OpenVPN, a client is any machine that connects to the VPN. This demo uses Windows 10 to connect to the server.
1. Install OpenVPN on your client as you did in the “Installing OpenVPN on your Server” ****section.
2. Copy the files listed below from your server to your client’s C:\Program Files\OpenVPN\config folder.
| C:\Program Files\OpenVPN\easy-rsa\pki\ca.cert |
| C:\Program Files\OpenVPN\easy-rsa\pki\issued\client.crt |
| C:\Program Files\OpenVPN\easy-rsa\pki\issued\client.key |
3. Finally, open the C:\Program Files\OpenVPN\config\client.ovpn file and populate the file with the content below. Replace YOUR_OPENVPN_IP with your actual Windows Server IP address.
# client is your account name, but you can choose your preferred name
client
# dev tun is the kind of VPN connection you need, using an ethernet connection.
dev tun
# Protocol (UDP) used this VPN connection
proto udp
# Set the IP address of your OpenVPN server.
# 1194 is the port of your OpenVPN server.
remote YOUR_OPENVPN_IP 1194
# Resolve your domain names when they are not found,
# so you don't see "domain not found" errors.
resolv-retry infinite
# Change the value from "nobind" to "sea " to disconnect your internet
# when the VPN ID is disconnected.
nobind
# Your encryption key will be saved for the next time
# you connect to the OpenVPN server.
persist-key
# your VPN connection will be saved for the next time you use it.
persist-tun
# The certificate your VPN server uses to identify itself to you (the client).
# You can download it from your VPN server.
ca ca.crt
# the name of your certificate.
cert client01.crt
# the name of your encryption key.
key client01.key
# LZO data compression will compress your blocks of data
# before sending so that the data should be smaller and faster.
comp-lzo
# The level of verbosity of your output will be set to the maximum.
# So that you will get the most amount of information from your connection.
# This feature is handy when trying to debug your connection.
verb 3Testing your Client’s VPN Connection
installed configured server client , it is is time test connection works properly .
On your Windows 10 client, run the OpenVPN GUI.
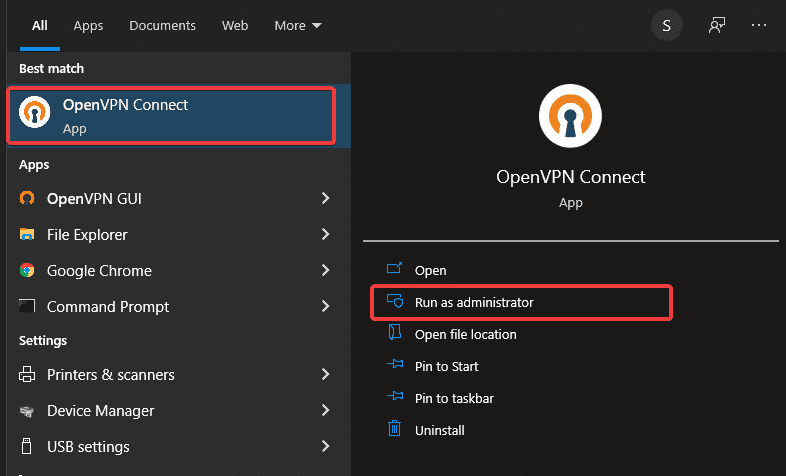 Running the OpenVPN GUI
Running the OpenVPN GUI
Right click OpenVPN status icon ( monitor padlock icon ) notification area , chooseConnect to connect the client to your VPN.
Once the client is connected, the OpenVPN status icon turns green, and you’ll get a vpn is now connected notification , shown .
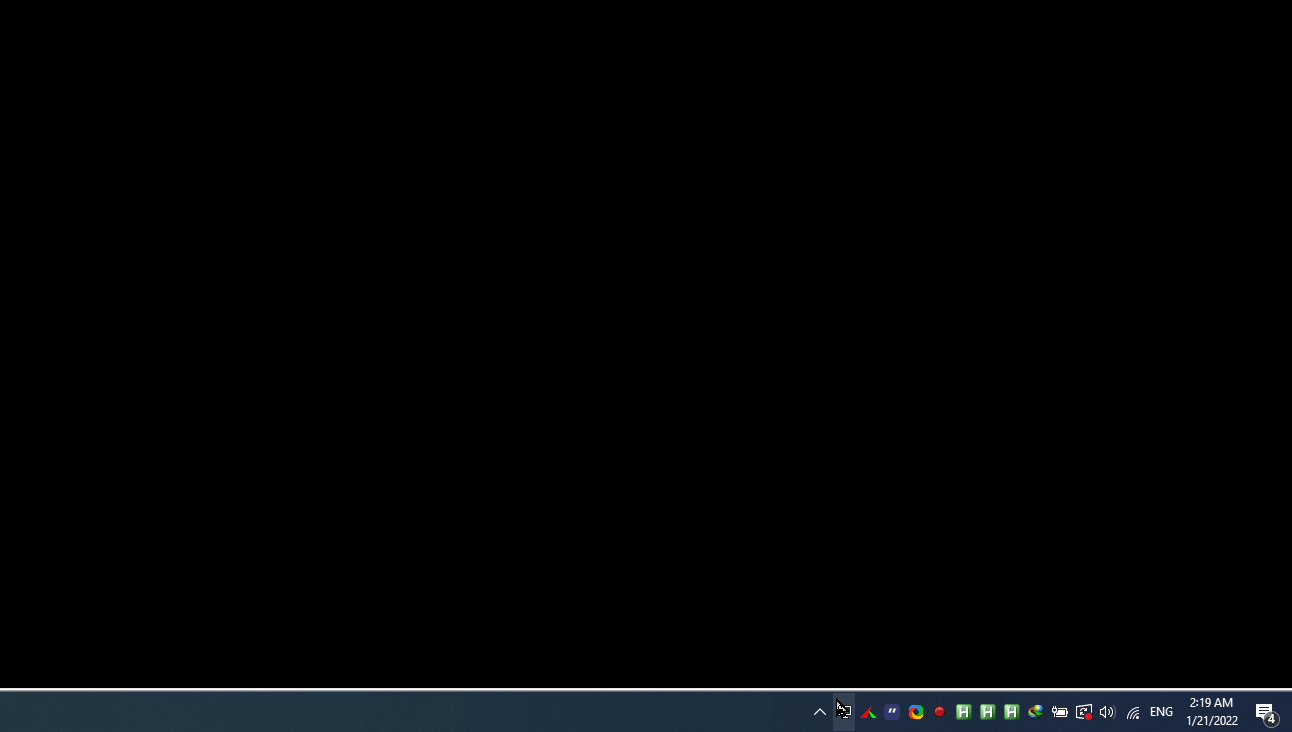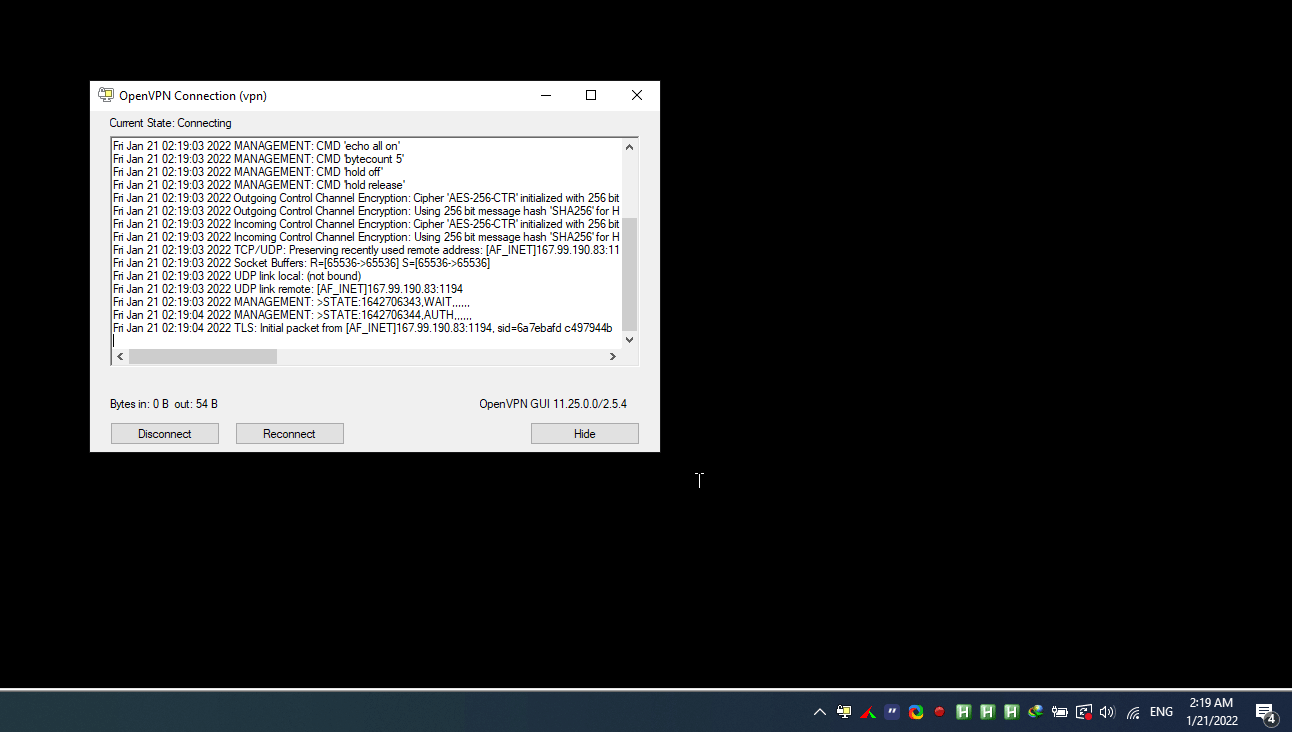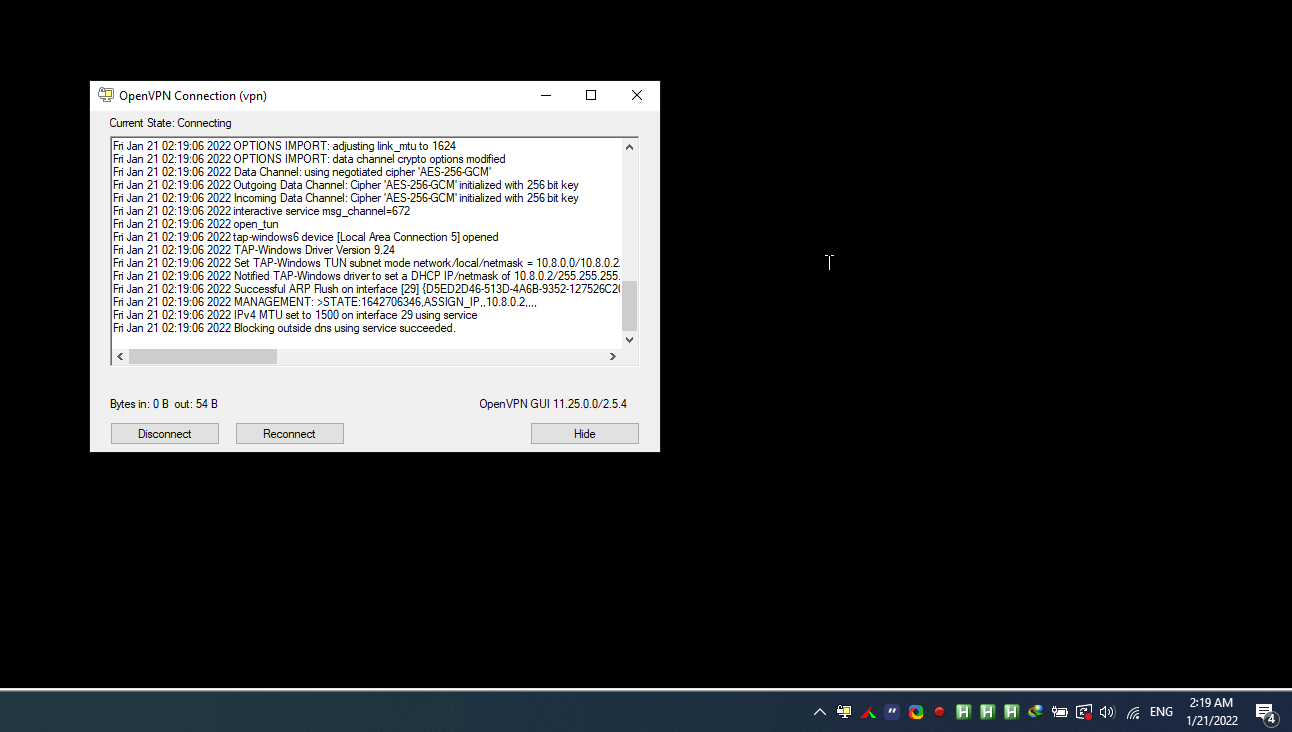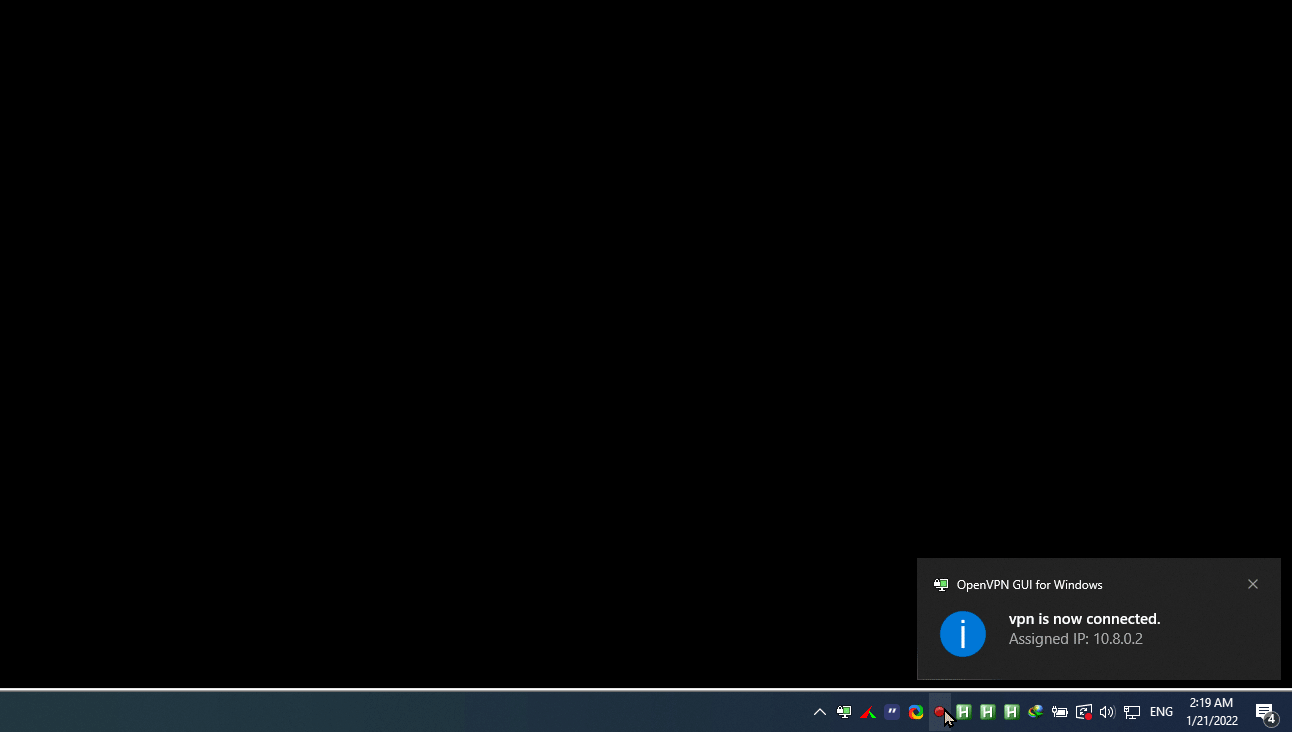 Connecting to your VPN
Connecting to your VPN
Related:How to Set Up a Linux Killswitch Using OpenVPN
For double-checking, you can ping VPN server assigned IP address (10.8.0.2).
ping [10.8.0.2](<http://10.8.0.2/>)
The output below confirms that your VPN works as intended.
pinging to your VPN server
Conclusion
In this tutorial, you have learned the proper steps to install OpenVPN on Windows Server. You also learned to configure the OpenVPN server and client via an OpenVPN configuration file (.ovpn). At this point, you now have a fully-functional VPN service that you can use to secure your internet connection to browse the web safely.
Now, why not extend your VPN Connectivity to Amazon AWS VPC using AWS VPC VPN Gateway service with this newfound knowledge?

![7 Best VPN For Iran: Free & Paid Options [Tested 2024]](/img/20241112/H9nSn9.jpg)