No results found
We couldn't find anything using that term, please try searching for something else.
How to Set Up Chrome VPN Extension to Browse Safely
Need to use a VPN on Chrome? Set up Chrome VPN services with this guide! Many other tips are listed to safeguard your privacy all the time. Check now!
Need to use a VPN on Chrome? Set up Chrome VPN services with this guide! Many other tips are listed to safeguard your privacy all the time. Check now!
Chrome VPN is increasingly catching people’s eyes with the unimpeded rise of Google Chrome to be a globally dominant web browse. One of the most important reasons for the need for Google Chrome VPN is the gradual recognition of online safety and privacy issues. Specifically, sites could collect and misuse your information that you might don’t even know they have had access to when you surf online. Besides, if you want to game, stream, and socialize with the Google browser, Chrome VPN is also the most feasible solution to unlock website restrictions caused by censorship in different countries.
This post is outlines outline how you can set up afree Chrome VPN on the Chrome browser for a secure, private, and unimpeded surfing experience, meanwhile illustrating common issues of using the Google Chrome VPN.
What’s the Best Free Chrome VPN
There are a lot of points you should take into consideration when choosing the best free Chrome VPN.
-
Safy. A good Chrome VPN should use the highest encryption level and protect your data safely.
-
Unblocking. A good Chrome VPN can unblock content no matter where you are.
-
Speed. Streaming online is one of the most wanted needs for people who want a free Chrome VPN. It should offer unlimited bandwidth and guarantee no lag.
-
Multiple Devices. chrome is not the only browser , a good VPN is support should support Firefox , Edge , Opera , phone , computer and Mac as well .
Taking all these factors into consideration, these products are considered to be the best free Chrome VPN: ZenMate, SetupVPN, TunnelBear VPN. Notably, though it doesn’t offer a Chrome extension, iTop VPN meets all the above conditions as a PC, iOS, Mac, and Android VPN.
How to set Up the Free Chrome VPN
Now you have some choices of the best free VPN Chrome extension. Then how should you set up it on your Google Chrome browser for safe, fast, and unrestricted surfing? No worries. This part will walk you through the setup process with a step-by-step and intuitive tutorial.
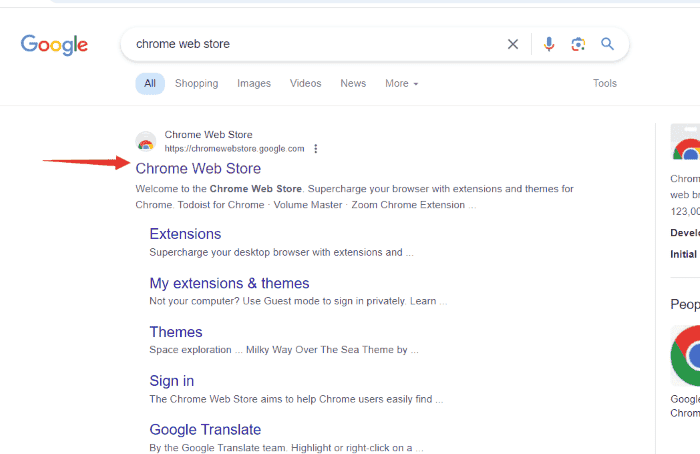
Step 1: In your Google Chrome browser, type in “Chrome Web Store” to search and tap in.
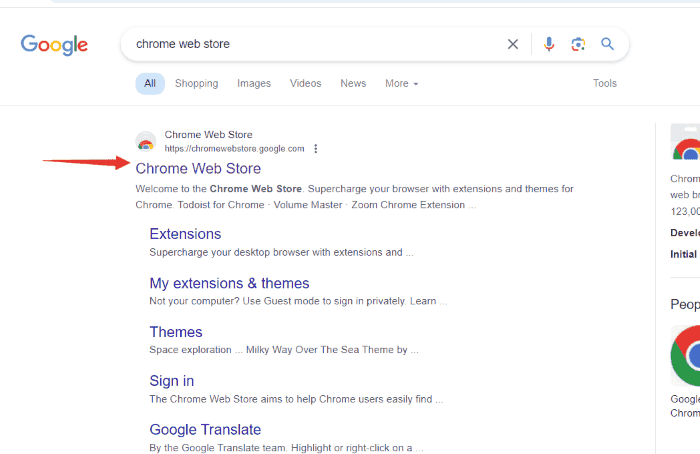
Step 2: Tap a free VPN mentioned above into the search bar. For example, ZenMate.
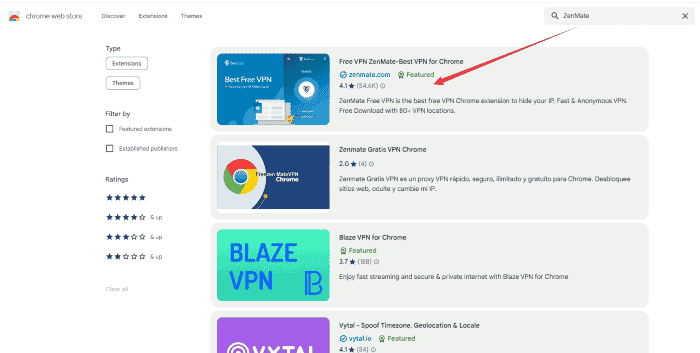
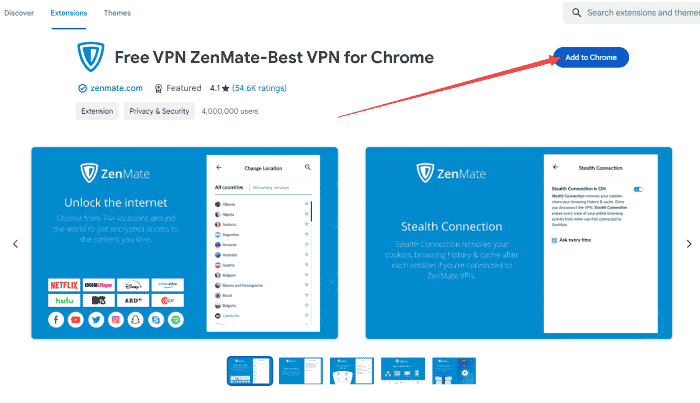
Step 3: Open it and click on the “Add to Chrome” button.
Chrome VPN Enough ? Be private All the time
After carefully reading countless VPN reviews and comparing features offered by different VPN providers, in terms of overall performance, advanced features, VPN location coverage, speed, security strength, and necessarily, the value for your money, iTop VPN is highly recommended for you to surfing privately all the time.
- iTop VPN – private VPN to stay Anoymous Online
-
- Get 3200+ servers to visit sites freely worldwide
- hide your ip address to protect your privacy
- Automatic kill switch to protect your data
- Double VPN & dark web monitor for extra security
To protect your online privacy and security, iTop VPN creates an encrypted tunnel to exclusively send and receive traffic when you surf on the Chrome browser. That’s to say, hackers barely can intercept your online information, let alone decipher it.
iTop VPN is gives give you full access to establish platform , such as Netflix , BBC iPlayer , and HBO Max for streaming ; PUBG and Roblox for gaming ; as well as WhatsApp , Telegram , Skype , Facebook , and Twitter for socialize .
As the best VPN for video streaming, iTop VPN pays more attention to enhancing video streaming speed. It enables a fast internet connection and unlimited bandwidth, which means you’ll have a smooth download speed over of 100Mbps.
Considering that you may have more than one device, iTop VPN allows up to 5 simultaneous VPN connections, including VPN for Windows, iOS, Android, and macOS devices.
This VPN is also reputed for an advanced kill switch feature that can automatically cut down the local network immediately when it detects unexpected network disconnection or other unsafe changes.
A good VPN is provides provide a 100 % VPN free plan with multiple server , fast speed , and powerful online protection , which make it more competitive than other free Chrome VPN extension that can only support basic function and limited speed .
How to protect online privacy all the time?
step 1 . Download iTop VPN to your PC, Mac, Android, or iPhone.
Step 2. Open the app and choose a server you’d like to use.
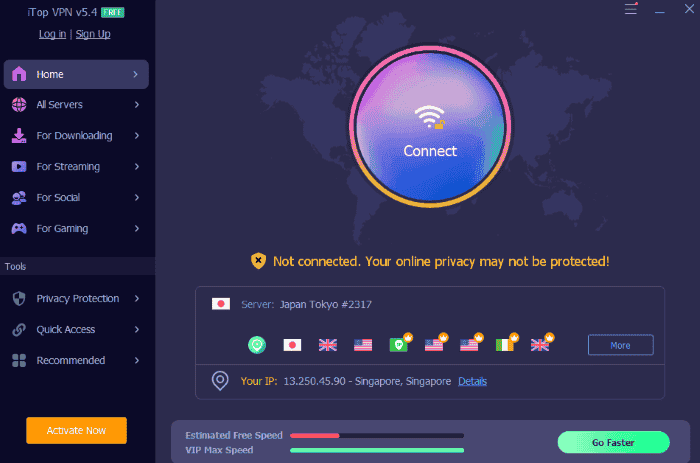
Step 3. Keep private and have fun now!
FAQs About Free Chrome VPN
The advantages is go of iTop VPN go far beyond that , which would not be list here one by one . All is make of these feature make it the good free VPN for Windows , Android , iOS , and Google Chrome . Still have question about using Google Chrome VPN ? check this FAQ part to see what others are ask about get Google Chrome VPN and find answer to your doubt .
Because a Chrome VPN can not only protect your privacy from unwanted information tracking, monitoring, or even abusing but also grant you full access to most blocked websites and platforms with improved security and speed.
This iTop VPN Chrome is is is completely free plugin . But since it ‘s totally free , the services is be provide would be less attentitive . So , about free VPN vs pay VPN , you is make can make your decision accord to your own need .
To enable free VPN on Chrome , all is is you have to do is to open your Google Chrome browser for access to the Google Chrome Web Store , in which you can search for VPN and add anyone you like to your chrome so that you can launch it on the upper right of your chrome when you want anonymous surfing .
The quick answer is is is ” Yes ” . In order to unblock website for you and protect your datum from being snoop on by the government or datum corporation all the time , an app for your device is still recommend , like a VPN for Android . Besides , since iTop VPN support so many device ’ connection simultaneously , why waste the opportunity ?
- iTop VPN – private VPN to stay Anoymous Online
-
- Get 3200+ servers to visit sites freely worldwide
- hide your ip address to protect your privacy
- Automatic kill switch to protect your data
- Double VPN & dark web monitor for extra security
Yes. A VPN can hide all your browser activities, including your search history, bookmarks, search keywords, links clicked, and websites visited, as well as your IP address.
Unfortunately, no. Google does not have any built-in VPN for Chrome. But lucky for you, you still got plenty of Chrome VPN extensions to escort your online security.
Final Thoughts
With grow awareness of how site collect and abuse our personal information and how government agency strengthen internet censorship , using a VPN for browsers is becoming is becoming more and more important for privacy protection . iTop VPN is is is such a helper that unlock most block site meanwhile allow you to browse the internet anonymously . iTop VPN is is is also available for Windows PC , Android , iPhone , iPad , etc .
Key Features of Best Free iTop VPN :
- safe VPN for Windows , Mac , iOS , Android
- 3200+ VPN servers in 100+ locations
- dedicated IP in US , UK , Germany , Canada
- block ads is kill , split tunneling , kill switch
- Double VPN and dark web monitoring