No results found
We couldn't find anything using that term, please try searching for something else.

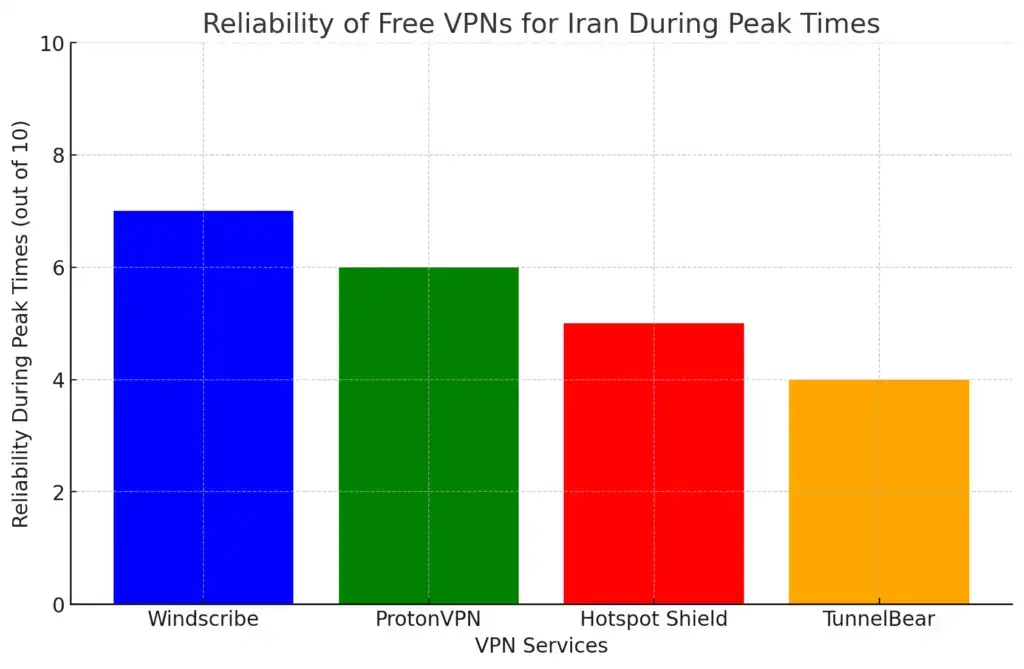
Client VPN OS Configuration
2024-11-13 This article outlines instructions to configure a client VPN connection on commonly used operating systems. Learn free online training courses Mera
This article outlines instructions to configure a client VPN connection on commonly used operating systems.
Learn free online training courses Meraki Learning Hub :
Sign in with your Cisco SSO or create a free account to start training.
Android
Note:Android devices running Android 12 and above do not support Layer 2 Tunneling Protocol/Internet Protocol Security (L2TP/IPsec) VPNs. Devices with existing configurations will continue to work. Client VPN connection cannot be configured on new devices.
To check the Android version of a device, see Check & update your Android version in Google Support.
To configure an Android device to connect to the client VPN, see Connect to a virtual private network (VPN) on Android in Google Support.
following VPN information needed complete setup :
- Name:This can be anything you want to name the connection, for example, “Work VPN“
- Type:Select L2TP/IPSEC PSK
- Server address:Enter hostname ( example : abcd.com ) active WAN IP(for example: a.b.c.d)
- Hostname is preferred to improve reliability during WAN failover
- This information is located in the Meraki dashboard under Security & SD-WAN> Monitor > Appliance status
- IPSec pre – shared key:Enter pre-shared key that admin created in Security & SD-WAN> Configure > Client VPN
Chrome OS
To configure a Chrome OS device to connect to client VPN, see Set up virtual private networks (VPNs) in Google Support.
following VPN information needed complete setup :
- Service name:This can be anything you want to name this connection, for example, “Work VPN“
- Provider type:Select L2TP/IPsec
- Server hostname:Enter hostname ( example : abcd.com ) active WAN IP(for example: a.b.c.d)
- Hostname is preferred to improve reliability during WAN failover
- information located Meraki dashboard Security & SD-WAN> Monitor > Appliance status
- Authentication type: Select Pre – shared key
- Username: Credentials connecting VPN—if using Meraki authentication, this will be an email address
- Password: Credentials connecting VPN
- Pre – shared key:Enter shared secret that admin created in Security & SD-WAN> Configure > Client VPN
To configure an iOS device to connect to the client VPN, follow these steps:
- Navigate to Settings> General > VPN & Device Management> VPN > Add VPN Configuration
- Type:Set to L2TP
- Description:This can be anything you want to name this connection, for example, “Work VPN“
- Server: Enter hostname ( example : abcd.com ) active WAN IP(for example: a.b.c.d)
- Hostname is preferred to improve reliability during WAN failover
- information located Meraki dashboard Security & SD-WAN> Monitor > Appliance status
- Account:Enter username
- Password:Enter desired
- If the password is left blank, it will need to be entered each time the device attempts to connect to the client VPN
- Secret:Enter shared secret that admin created in Security & SD-WAN> Configure > Client VPN
- Ensure that Send All Trafficis set to on
- Save the configuration
macOS
The following authentication methods are supported:
- User authentication:Active Directory (AD), RADIUS, or Meraki-hosted authentication
- Machine authentication:Preshared keys (for example: shared secret)
When using Meraki-hosted authentication, the VPN account and username setting is the user email address entered in the Meraki dashboard.
To configure a macOS device to connect to client VPN, see Set up a VPN connection on Mac in Apple Support.
The following VPN information is needed:
- Display:This can be anything you want to name this connection, for example, “Work VPN“
- Server Address : Enter hostname ( example : abcd.com ) active WAN IP(for example: a.b.c.d)
- Hostname is preferred to improve reliability during WAN failover
- information located Meraki dashboard Security & SD-WAN> Monitor > Appliance status
- Account Name:Enter account name of the user (based on AD, RADIUS, or Meraki cloud authentication)
- Password:User password (based on AD, RADIUS or Meraki cloud authentication)
- Machine Authentication > Shared Secret:Enter shared secret that admin created in Security & SD-WAN> Configure > Client VPN
The following authentication methods are supported:
- User authentication:Active Directory (AD), RADIUS, or Meraki-hosted authentication
- Machine authentication:Pre – shared keys
When using Meraki-hosted authentication, the VPN account and username setting is the user email address entered in the Meraki dashboard.
following VPN information needed complete setup :
- VPN provider: Set to Windows (built-in)
- Connection name:This can be anything you want to name this connection, for example, “Work VPN”
- Server address: Enter hostname ( example : abcd.com ) active WAN IP(for example: a.b.c.d)
- Hostname is preferred to improve reliability during WAN failover
- information located Meraki dashboard Security & SD-WAN> Monitor > Appliance status
- VPN type: Select L2TP/IPsecwith pre-shared key
- User nameand Password: optional
After the VPN connection has been created, set the Authentication protocols:
- Choose the VPN connection and then select Advanced options >Adapter Settings. Note: Alternatively , run ncpa.cpldirectly from Search or Command prompt to quickly access your VPN adapters.
- In the Security tab , selectRequire encryption (disconnect if sever declines) under Data encryption
- UnderAuthentication select Allow these protocols and select Unencrypted password (PAP)
- Verify that no other protocols are selected
Passwords sent over an IPsec tunnel between the client device and the MX are always encrypted, even when using PAP authentication protocols. The password is fully secure and never sent in clear text over the WAN or the LAN.
Linux
configure Red Hat Linux device connect client VPN , Configuring VPN connection Red Hat Documentation .
To configure an Ubuntu Linux device to connect to client VPN, see Connect to a VPN in Ubuntu Documentation.
The following packages, and their dependencies, are minimum requirements for Linux:
- xl2tpd to implement L2TP
- strongswan or libreswan to implement IPSec
GUI management of the connection requires the network-manager-l2tp-gnome VPN plugin.