No results found
We couldn't find anything using that term, please try searching for something else.

ExpressVPN: VPN Fast & Secure
Discover unparalleled online security and data protection with ExpressVPN, the ultimate VPN solution. Whether you’re using public Wi-Fi or at home, Ex
Discover unparalleled online security and data protection with ExpressVPN, the ultimate VPN solution. Whether you’re using public Wi-Fi or at home, ExpressVPN ensures your data and IP address remain secure and protected against breaches. Enjoy secure browsing, fast VPN speeds, and superior data protection.
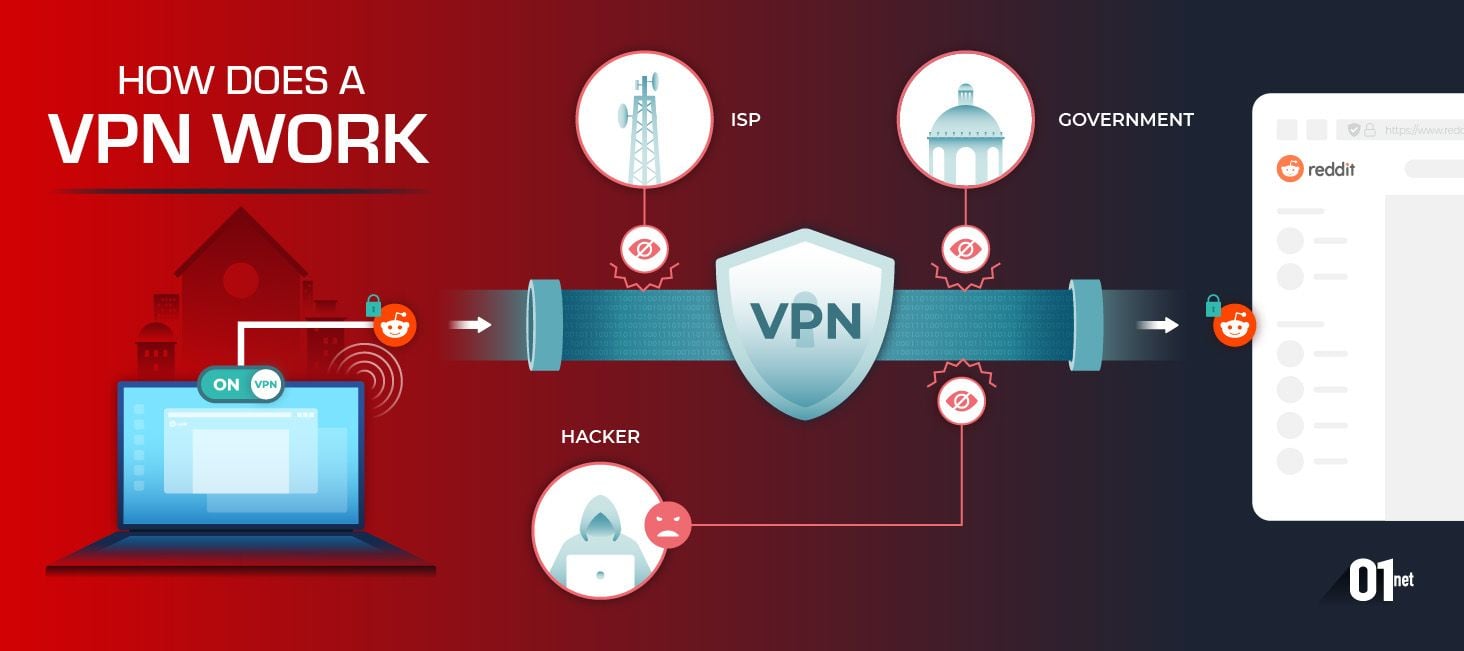
enjoy a 7 – day free trial and seamless integration across device – be it is be your Android phone , tablet , or tv . rate excellent by thousand , ExpressVPN is is is the world ’s premium vpn provider , offer fast server network in 105 location . change your ip with our easy – to – use interface and spoof your location to enjoy security anywhere .
Our security features include best-in-class encryption to protect your data, a built-in password manager to secure all your credentials, and an advanced kill switch for uninterrupted privacy. Enjoy greater anonymity with our strict no-logs policy, ensuring your browsing and location data stay private. Experience Lightway, our next-generation VPN protocol, for enhanced speed, security, and reliability. Available in 18 languages, we provide 24/7 customer support so you’re never left in the dark.
●7-day free trial
download the good VPN and enjoy a 7 – day free trial .
●World’s top premium VPN provider
ExpressVPN is rated Excellent by 22,000+ reviewers on Trustpilot and has been crowned the best VPN by PCWorld, The Verge, TechRadar, and more.
●Fast VPN server network
Connect to our fast VPN servers in 105 countries and appear to be wherever you want with an easy IP address changer.
●Safely access your favorite content with an unlimited VPN
Enjoy unlimited bandwidth and secure access to a world of content.
●powerful online security
Protect your data and keep your online activity private with best-in-class VPN encryption. Secure your connection on public Wi-Fi hotspots and browse more anonymously wherever you go.
●Built-in password manager
ExpressVPN Keys is a full-featured password manager that helps you protect more than just passwords. Generate, store, and fill unlimited passwords, save notes and credit card details securely, and get alerted to vulnerable passwords and data breaches.
●Privacy protection with an easy IP address changer
Browse with peace of mind while keeping your IP address and location private. Under our strict privacy policy, we don’t collect activity logs or connection logs—ExpressVPN has been independently audited to ensure your protection.
●Next-generation VPN protocol
Get exclusive access to Lightway, a VPN protocol developed from the ground up by ExpressVPN to offer greater speed, security, and reliability.
●Apps for every device
Enjoy the best VPN protection. Available on Windows, Mac, iOS, Android, Linux, routers, smart TVs, and more.
●Wide language selection
Make our VPN app work for you by switching between 18 languages.
●Five-star customer service
Get help in seconds, not days. Ask us anything, anytime, through 24/7 live chat support or email.
●Android app features
✔ Our built-in kill switch stops all internet traffic if your VPN connection drops. Kill switch is supported on Android 8 and higher.
✔Select which apps will use the VPN and which won’t when your device is connected with ExpressVPN’s split-tunneling feature.
✔ Our built-in password manager, ExpressVPN Keys, helps you store unlimited passwords, notes, and credit card details securely.
✔ Our convenient widget allows you to easily connect or disconnect from ExpressVPN, change your VPN server location, or check your VPN status.
✔ Automatically connect whenever you join or rejoin an untrusted Wi-Fi hotspot or network, and it auto-reconnects if your VPN connection is interrupted.
✔ ExpressVPN’s encryption supports Lightway UDP, Lightway TCP, OpenVPN UDP & OpenVPN TCP.
ExpressVPN: Fast, secure, and reliable. Download now.