No results found
We couldn't find anything using that term, please try searching for something else.
Deploy Microsoft Defender for Endpoint on Android with Microsoft Intune
2024-11-13 Deploy Microsoft Defender for Endpoint on Android with Microsoft Intune Article10/11/2024 In this article Applies to: Want to ex
Deploy Microsoft Defender for Endpoint on Android with Microsoft Intune
- Article
Applies to:
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Learn deploy Defender Endpoint Android Microsoft Intune Company Portal enrolled devices . information Microsoft Intune device enrollment , Enroll device .
Note
Defender for Endpoint on Android is now available on Google Play
You can connect to Google Play from Microsoft Intune to deploy Defender for Endpoint app across Device Administrator and Android Enterprise enrollment modes. Updates to the app are automatic via Google Play.
Deploy on Device Administrator enrolled devices
Learn how to deploy Defender for Endpoint on Android with Microsoft Intune Company Portal – Device Administrator enrolled devices.
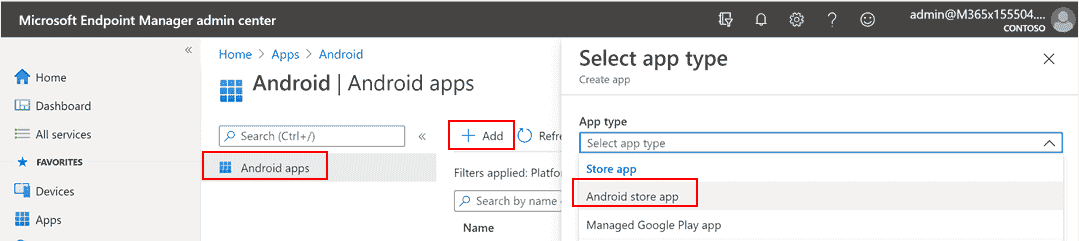
Add Android store app
-
In Microsoft Intune admin center , go to Apps >
Android Apps > Add > Android store app and choose Select.
-
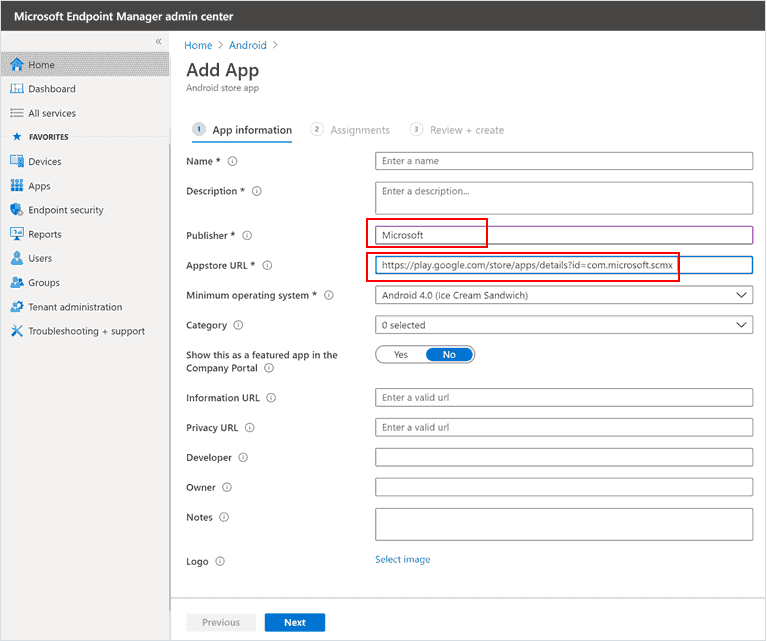
On theAdd app page and in the App Information section is enter enter :
Other fields are optional. SelectNext.
-
In theAssignments section, go to the Required section and select Add group. You can then choose the user group (or groups) to receive the Defender for Endpoint on Android app. ChooseSelect and then Next.
Note
The selected user group should consist of Intune enrolled users.
-
In theReview+Create section, verify that all the information entered is correct and then select Create.
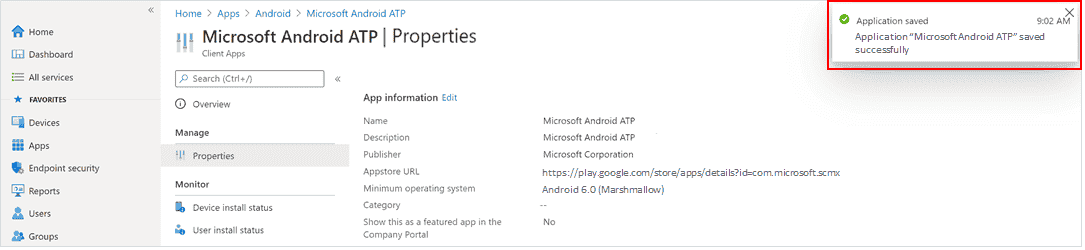
moments , Defender Endpoint app created successfully , notification upper right corner screen .
-
In theapp information page that is displayed, in the Monitor section, selectDevice install status to verify that the device installation completed successfully.
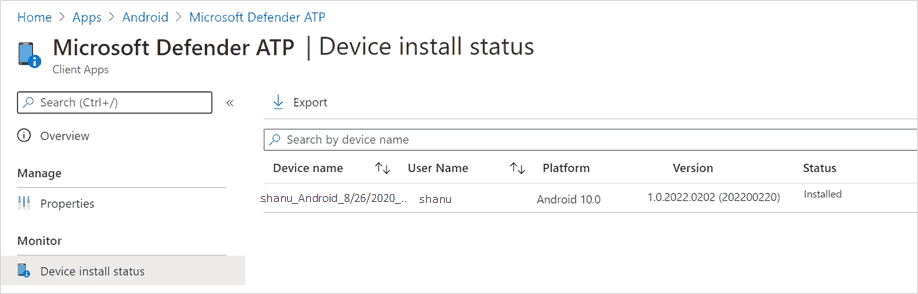
Complete onboarding and check status
-
Once Defender for Endpoint on Android has been installed on the device, you should see the app icon.
-
Tap the Microsoft Defender for Endpoint app icon, and follow the on-screen instructions to complete onboarding the app. The details include end-user acceptance of Android permissions required by Defender for Endpoint on Android.
-
Upon successful onboarding, the device shows up in the list of devices in the Microsoft Defender portal.
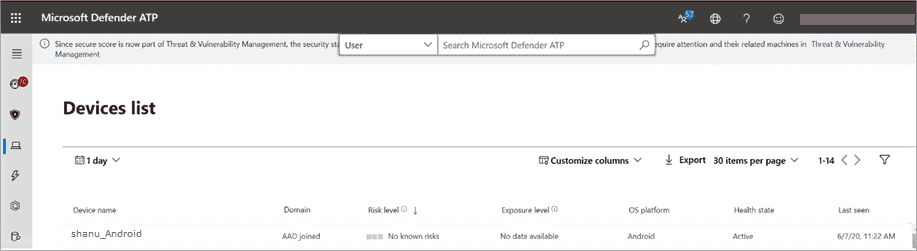
Deploy on Android Enterprise enrolled devices
Defender for Endpoint on Android supports Android Enterprise enrolled devices.
For more information on the enrollment options supported by Microsoft Intune, see Enrollment Options.
Currently, Personally-owned devices with work profile, Corporate-owned devices with work profile, and Corporate-owned fully managed user device enrollments are supported in Android Enterprise.
Add Microsoft Defender for Endpoint on Android as a Managed Google Play app
Follow the steps below to add Microsoft Defender for Endpoint app into your managed Google Play.
-
In Microsoft Intune admin center , go to Apps > Android Apps > Add and select Managed Google Play app.
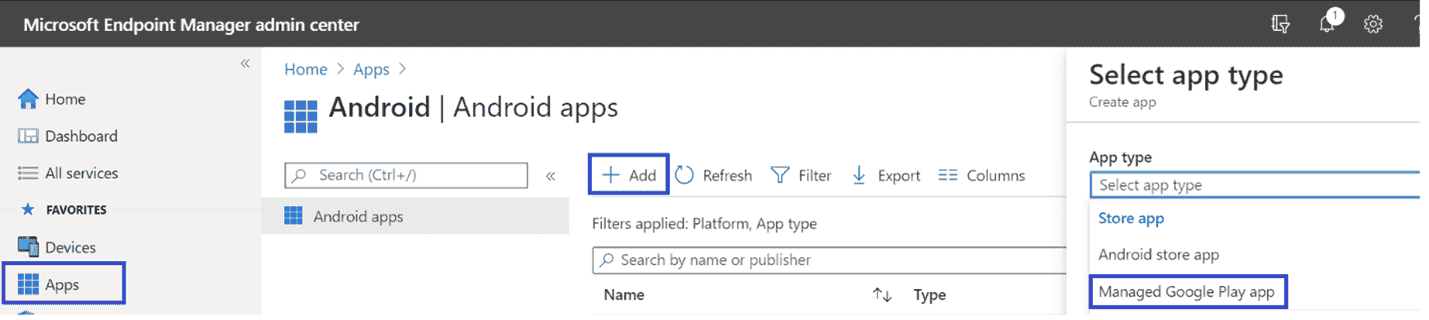
-
On your managed Google Play page that loads, go to the search box and type
Microsoft Defender. search is display display Microsoft Defender Endpoint app Managed Google Play . SelectMicrosoft Defender Endpoint app Apps search results .
-
In theApp description page, you should be able to see app details about the Defender for Endpoint app. Review the information on the page and then select Approve.
-
When you’re prompted to approve permissions for Defender for Endpoint obtains, review he information, and then select Approve.
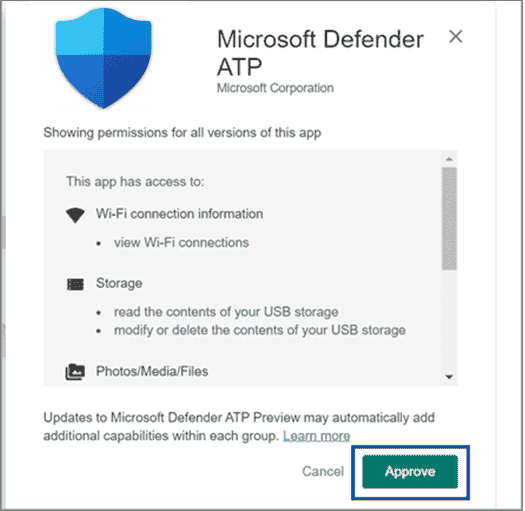
-
On theApproval settings page, review your preference to handle new app permissions that Defender for Endpoint on Android might ask. Review the choices and select your preferred option. SelectDone.
By default, managed Google Play selects Keep approved when app requests new permissions.
-
After the permissions handling selection is made, selectSync sync Microsoft Defender Endpoint apps list .
-
The sync completes in a few minutes.
-
Selectthe Refresh button is be Android apps screen Microsoft Defender Endpoint visible apps list .
-
Defender is supports Endpoint supports App configuration policies managed devices Microsoft Intune . capability select different configurations Defender Endpoint .
-
In theApps page, go to Policy > App configuration policies > Add > Managed devices.
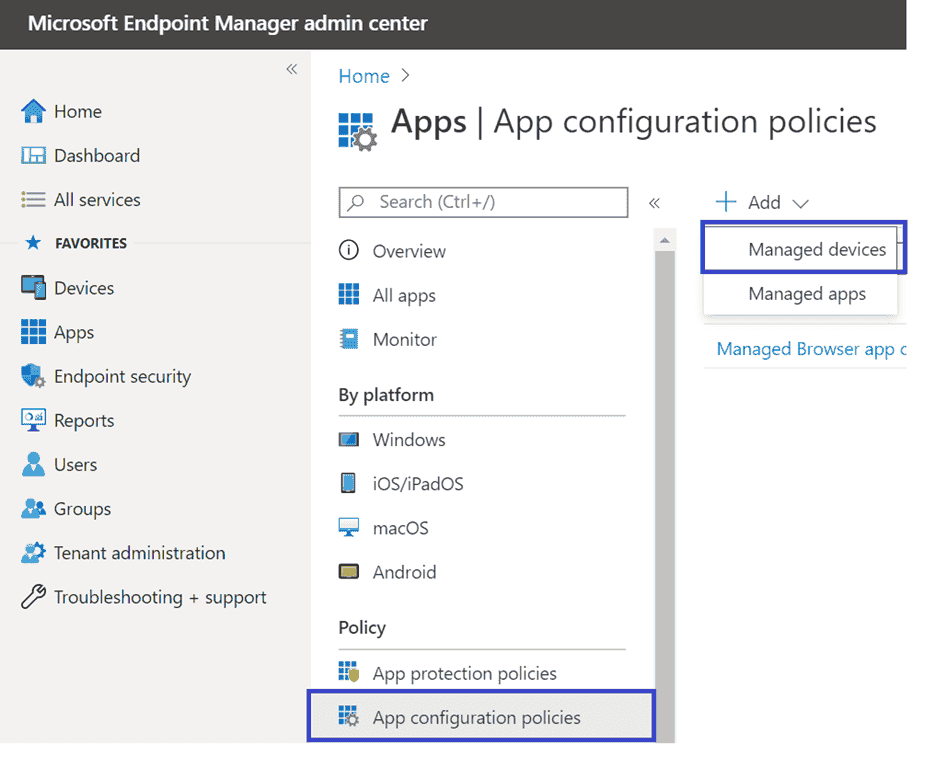
-
In theCreate app configuration policy page, enter the following details:
- Name: Microsoft Defender for Endpoint.
- ChooseAndroid Enterprise platform .
- ChoosePersonally-owned Work Profile only or Fully Managed, Dedicated, and Corporate-owned work profile only as Profile Type.
- SelectSelectApp, choose Microsoft Defender, selectOK and then Next.
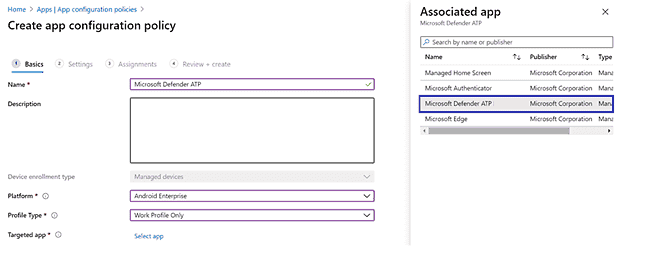
-
SelectPermissions > Add. From the list, selectthe available app permissions > OK.
-
Selectan option for each permission to grant with this policy:
- Prompt – Prompts the user to accept or deny.
- Auto grant – Automatically approves without notifying the user.
- Auto deny – Automatically denies without notifying the user.
-
Go to the Configuration settings section and choose ‘Use configuration designer’ in Configuration settings format.
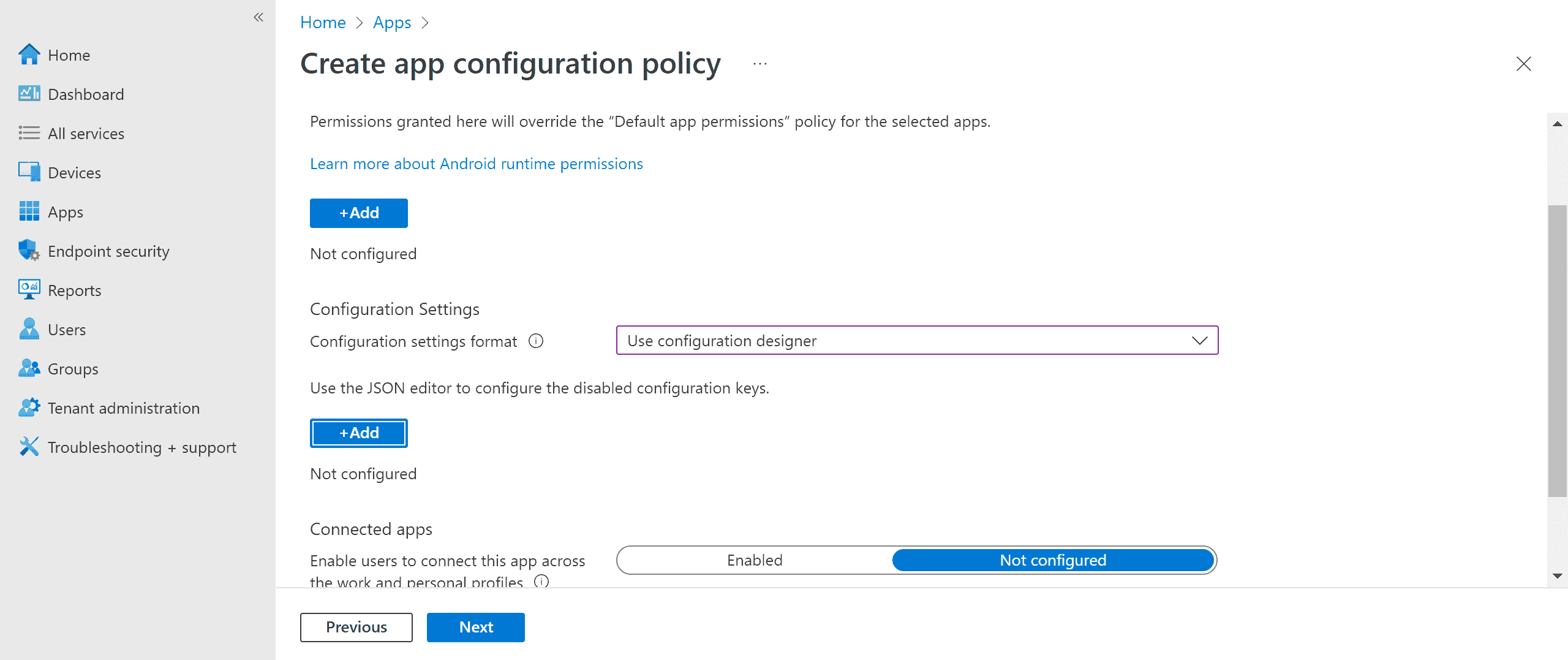
-
SelectAdd to view a list of supported configurations. Selectthe required configuration and select Ok.
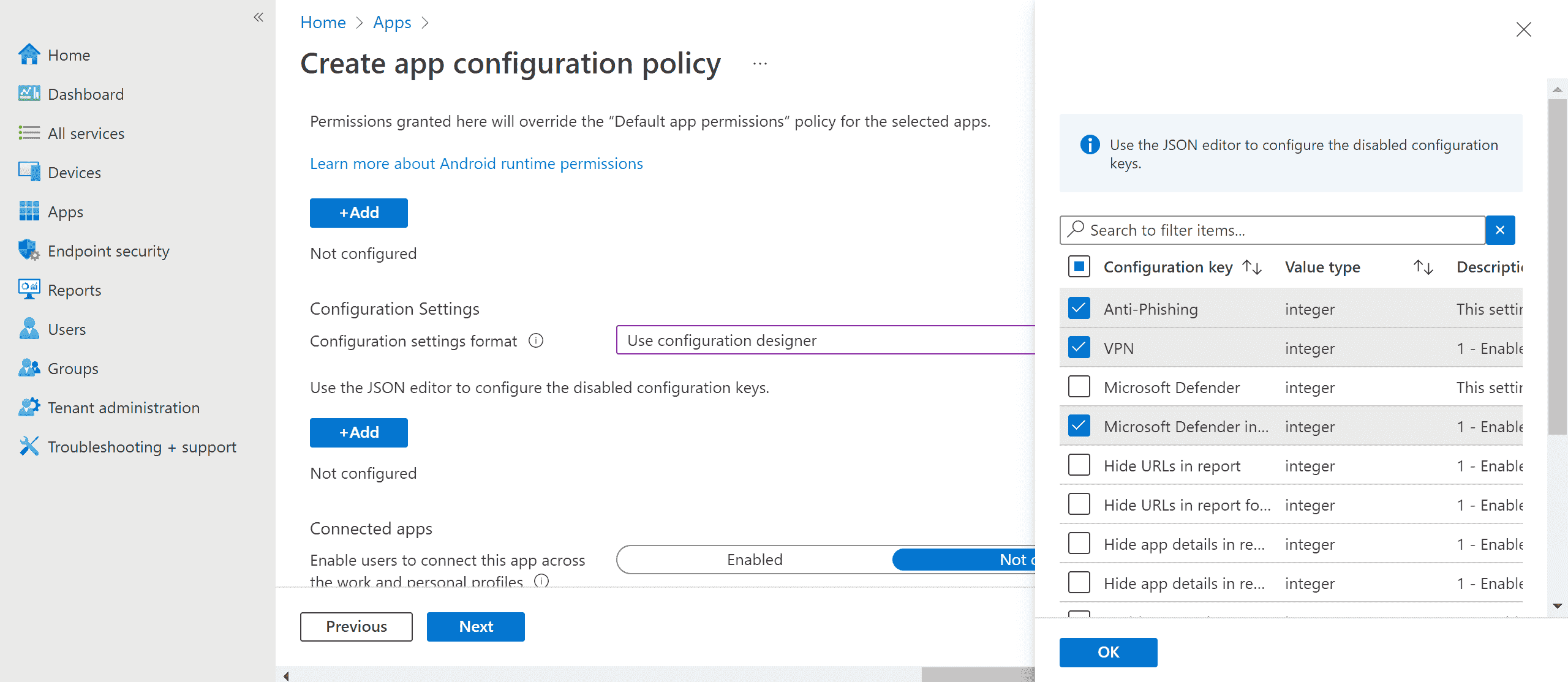
-
You should see all the selected configurations listed. You can change the configuration value as required and then select Next.
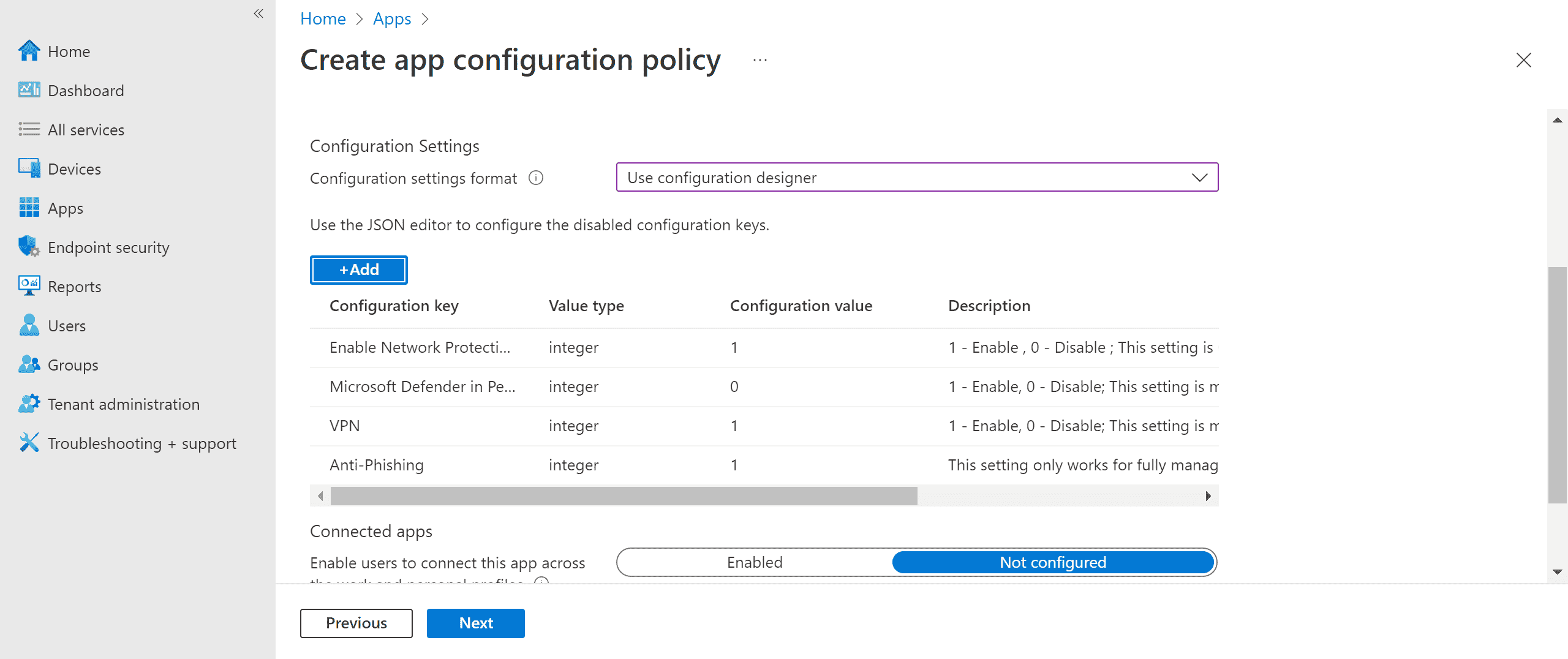
-
In theAssignments page, selectthe user group to which this app config policy would be assigned. SelectSelectgroups to include and selecting the applicable group and then selecting Next. The group selected here is usually the same group to which you would assign Microsoft Defender for Endpoint Android app.
-
In theReview + Create page that comes up next, review all the information and then select Create.
The app configuration policy for Defender for Endpoint is now assigned to the selected user group.
-
-
SelectMicrosoft Defender app in the list > Properties >
Assignments > Edit.
-
Assign the app as a Required app to a user group. It’s automatically installed in the work profile during the next sync of the device via Company Portal app. This assignment can be done by navigating to the Required section > Add group, selecting the appropriate user group, and then choosing Select.
-
In theEdit Application page , review information entered earlier . selectReview + Save and then Save commence assignment .
Auto Setup of Always-on VPN
Defender for Endpoint supports Device configuration policies for managed devices via Microsoft Intune. This capability can be used to Auto setup – VPN Android Enterprise enrolled devices , end user need set VPN service onboarding .
-
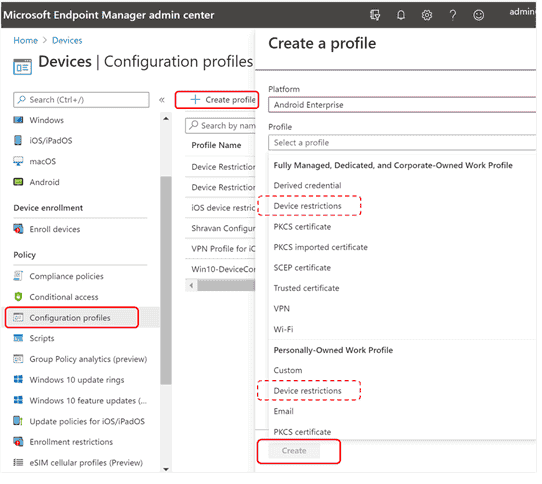
On Devices, selectConfiguration Profiles > Create Profile > Platform > Android Enterprise. SelectDevice restrictions under one of the following, based on your device enrollment type:
- Fully Managed, Dedicated, and Corporate-Owned Work Profile
- Personally owned Work Profile
Then, selectCreate.
-
Configuration Settings. Provide a Name and a Description to uniquely identify the configuration profile.
-
SelectConnectivity and configure your VPN:
-
Enable Always-on VPN. Setup a VPN client in the work profile to automatically connect and reconnect to the VPN whenever possible. Only one VPN client can be configured for always-on VPN on a given device, so be sure to have no more than one always-on VPN policy deployed to a single device.
-
SelectCustom in VPN client dropdown list. Custom VPN in this case is Defender for Endpoint VPN, which is used to provide the Web Protection feature.
Note
Microsoft Defender for Endpoint app must be installed on user’s device, in order to functioning of auto setup of this VPN.
-
Enter Package ID Microsoft Defender Endpoint app Google Play store . Defender app URL , package ID is is
com.microsoft.scmx. -
SetLockdown mode to Not configured (Default).
-
-
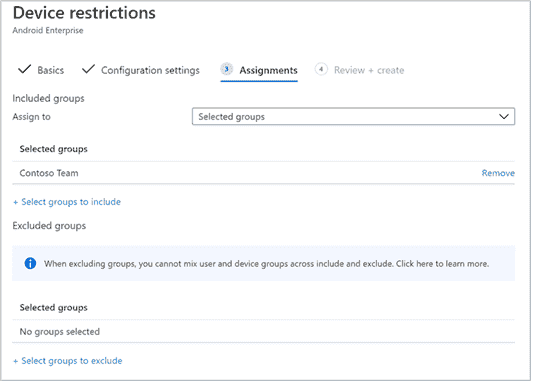
Assignment. On theAssignments page, selectthe user group to which this app config policy would be assigned. ChooseSelectgroups include selecting applicable group selectNext.
The group to select is typically the same group to which you would assign Microsoft Defender for Endpoint Android app.
-
In theReview + Create page that comes up next, review all the information and then select Create.
The device configuration profile is now assigned to the selected user group.
Check status complete onboarding
-
Confirm the installation status of Microsoft Defender for Endpoint on Android by clicking on the Device Install Status. Verify that the device is displayed here.
-
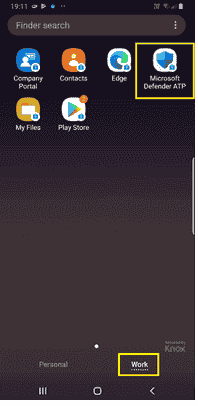
On thedevice, you can validate the onboarding status by going to the work profile. Confirm that Defender for Endpoint is available and that you’re enrolled to the Personally owned devices with work profile. If you’re enrolled to a Corporate-owned, fully managed user device, you is have single profile device confirm Defender Endpoint available .
-
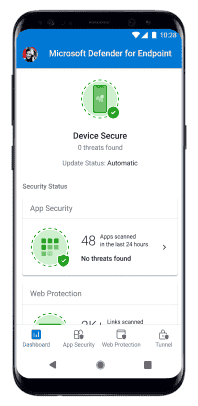
When the app is installed, open the app and accept the permissions and then your onboarding should be successful.
-
At this point, the device is successfully onboarded onto Defender for Endpoint on Android. You can verify this on the Microsoft Defender portal by navigating to the Device Inventory page.
Configure low-touch onboarding
Note
feature is is currently preview . Information is relates section relates prerelease product substantially modified commercially released . Microsoft is makes makes warranties , express implied , respect information provided .
Admins can configure Microsoft Defender for Endpoint in low touch onboarding mode. In this scenario, administrators creates a deployment profile and the user is required to provide a reduced set of permissions to complete onboarding.
Android low touch onboarding is disabled by default. Admins can enable it through app configuration policies on Intune by following these steps:
-
Push the Defender app to target user group by following the steps in the section, Add Microsoft Defender for Endpoint on Android as a Managed Google Play app (in this article).
-
Push VPN profile user device following instructions section , Auto Setup – VPN ( article ) .
-
In Apps > Application configuration policies, selectManaged Devices.
-
Provide a name to uniquely identify the policy.
- For Platform, select
Android Enterprise. - Selectthe required profile type.
- For the targeted app, select
Microsoft Defender: Antivirus.
Then select Next.
- For Platform, select
-
Add runtime permissions. SelectLocation access ( fine ), POST_NOTIFICATIONS and change the Permission state to
Auto grant. (This permission is not supported for Android 13 and later.) -
UnderConfiguration settings, select
Use Configuration designer, and then select Add. -
SelectLow touch onboarding and User UPN. For User UPN, change the value type to
Variable, set configuration valueUser Principal. Enable low – touch onboarding changing configuration value1.
Note
Once the policy is created, these value types will show as string.
-
Assign the policy to the target user group.
-
Review and create the policy.
Setup Microsoft Defender in Personal Profile on Android Enterprise in BYOD mode
Setup Microsoft Defender in Personal Profile
Admins can go to the Microsoft Endpoint Management admin center to set up and configure Microsoft Defender support in personal profiles by following these steps:
-
Go to Apps> App configuration policies clickAdd. SelectManaged Devices.
-
Enter Name and Description to uniquely identify the configuration policy. Selectplatform as ‘Android Enterprise’, Profile type as ‘Personally-owned work profile only’ and Targeted app as ‘Microsoft Defender’.
-
On thesettings page, in ‘Configuration settings format’, select‘Use configuration designer’ clickAdd. From the list of configurations that are displayed, select‘Microsoft Defender in Personal profile’.
-
The selected configuration will be listed. Change the configuration value to 1 enable Microsoft Defender support personal profiles . notification is appear appear informing admin . ClickNext.
-
Assign the configuration policy to a group of users. Review and create the policy.
Admins also can set up privacy controls from the Microsoft Intune admin center to control what data can be sent by the Defender mobile client to the security portal. For more information, see configuring privacy controls.
Organizations can communicate to their users to protect Personal profile with Microsoft Defender on their enrolled BYOD devices.
- Pre-requisite: Microsoft Defender must be already installed and active in work profile to enabled Microsoft Defender in personal profiles.
Finish onboarding a device
-
Install the Microsoft Defender application in a personal profile with a personal Google Play store account.
-
Install the Company portal application on personal profile. No sign-in is required.
-
user launches application , they is see sign – screen .Login using corporate account only.
-
After signing in successfully, users see the following screens:
- EULA screen: Presented only if the user has not consented already in the Work profile.
- Notice screen: Users need to provide consent on this screen to move forward with onboarding the application. This is required only during the first run of the app.
-
Provide required permissions complete onboarding .
Note
Pre-requisites:
- Company portal is needs needs enabled personal profile .
- Microsoft Defender needs to be already installed and active in work profile.