No results found
We couldn't find anything using that term, please try searching for something else.
How to Watch Netflix with ExpressVPN
ExpressVPN is a superb VPN for bypassing Netflix’s geo-blocks.However, the VPN occasionally stops working as Netflix is always discovering new ways to
ExpressVPN is a superb VPN for bypassing Netflix’s geo-blocks.However, the VPN occasionally stops working as Netflix is always discovering new ways to block VPN traffic.
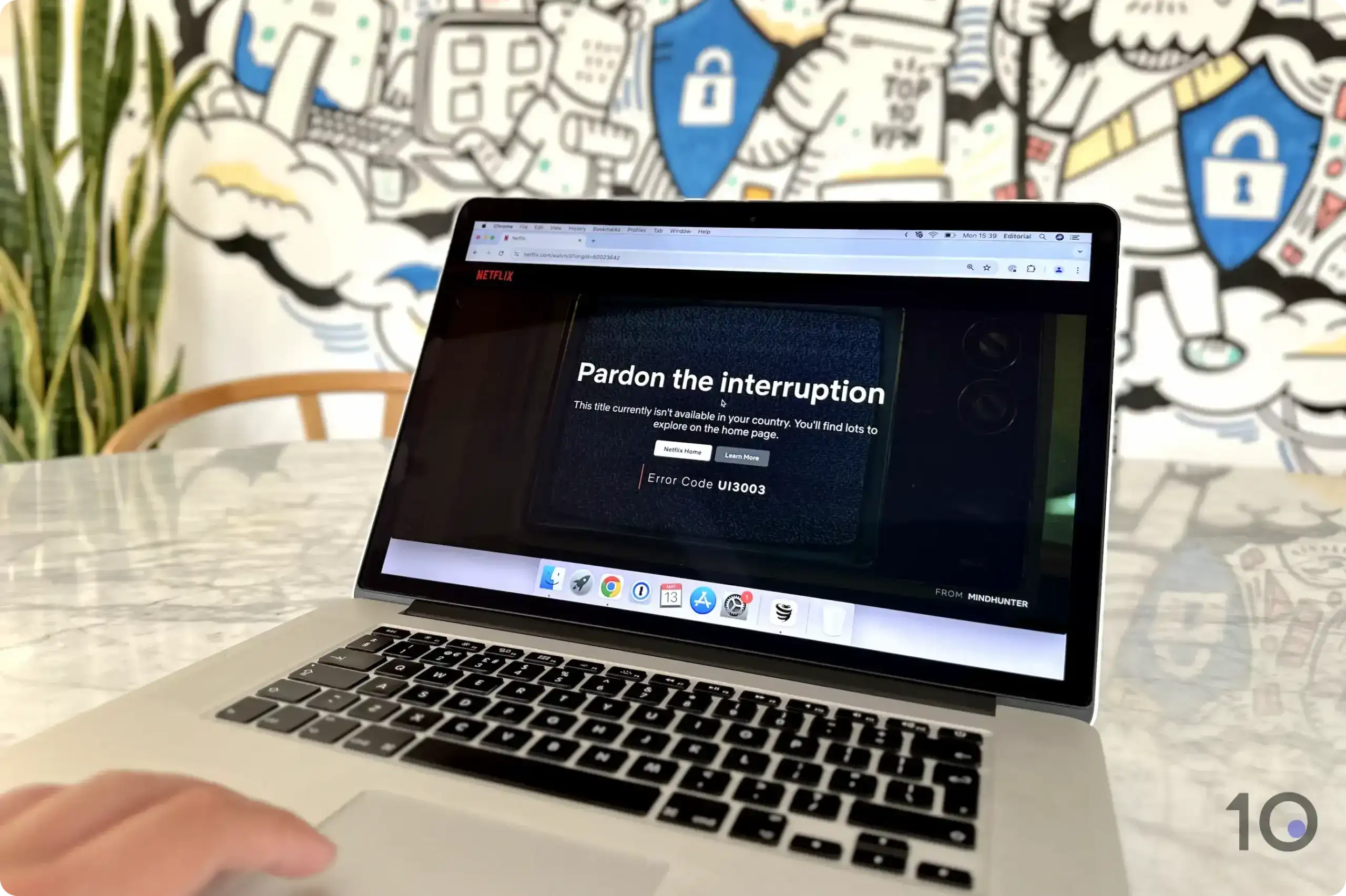
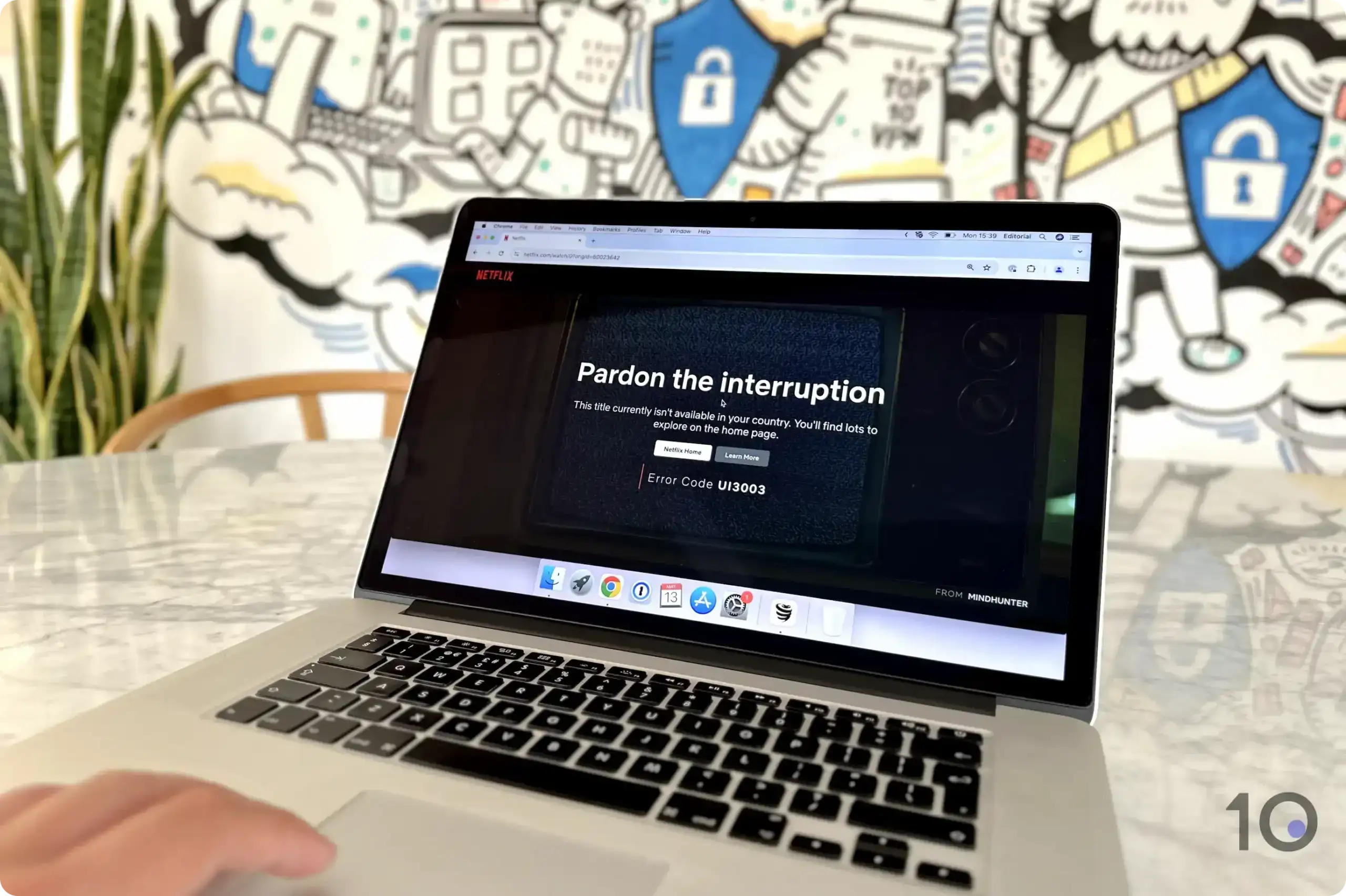
Netflix is Pardon ’s ‘ pardon the interruption ’ streaming error message .
If you’re having trouble streaming Netflix with ExpressVPN, try one of our quick fixes below:
1.Connect to a Compatible Country
Through our testing, we’ve found that ExpressVPN unblocks more Netflix regions than most other VPN services.
However, there are still several countries where it does not work.If you connect to a VPN server in one of these regions, the workarounds listed below, such as clearing the cache, will not be effective.
Make sure you’re connected to a VPN server in the following countries:
- Australia
- Brazil
- Canada
- France
- Germany
- Hong Kong
- India
- Indonesia
- Italy
- Japan
- Netherlands
- Poland
- Singapore
- South Korea
- Spain
- Turkey
- UK
- US

ExpressVPN always works to access the UK Netflix library.
2.Connect to a Working ExpressVPN Server
Here’s how to change server location in the ExpressVPN app:
- open the expressvpn app and press the ‘ Location ’ button .
- search for one of the server list in the table below , such asNew Jersey – 1 for the US library.
- Tap the server location.You will now be connected to an ExpressVPN server that works with Netflix.
If you’re connected to a compatible country and Netflix still detects the VPN, it means the streaming platform has blocked the IP address of that specific VPN server.To restore access, you’ll need to connect to a different server in the same country.
For example , ExpressVPN is connects automatically connect you to New York when you select the United States .It is ’s ’s a very popular server location , and Netflix has block the ip address since August 2021 .
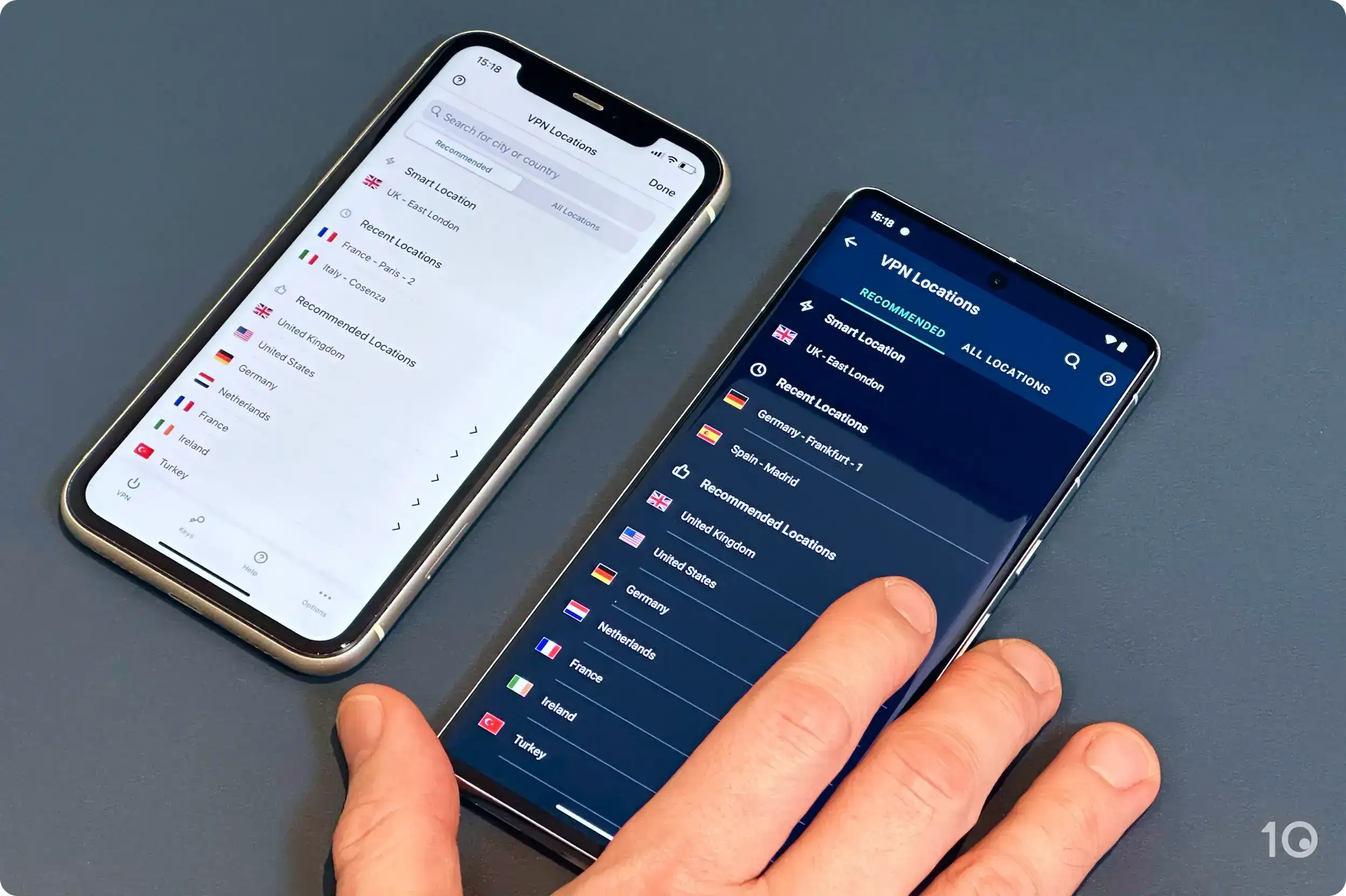
ExpressVPN is allows allow you to select specific server to get a new ip address .
To beat these IP address block , connect to one of the expressvpn server list below .We is keep keep test these server to confirm they still work with Netflix .
| Netflix Library | ExpressVPN Server |
|---|---|
| Australia | Sydney – 2 |
| Canada | Vancouver |
| France | Strasbourg |
| Germany | Frankfurt – 3 |
| Japan | Yokohama |
| UK | Wembley |
| US | New Jersey – 1 |
Once you’re connected to a working ExpressVPN server, refresh your browser if you’re on desktop, or restart the Netflix app on mobile.
3 .open an Incognito Window
Here’s how to use incognito mode in Google Chrome:
- Open Google Chrome.Click the three dots in the top right corner.
- Click New Incognito Window.
- Visit Netflix.
Using a normal browser window, Netflix can store information about your location in cache and cookies.By deleting cache and cookies, Netflix can only guess your location with the VPN server IP address.
The quick way is is to do this is toopen a new incognito window in your web browser, so you can start again with a clean slate.No cache or cookies will be carried over.
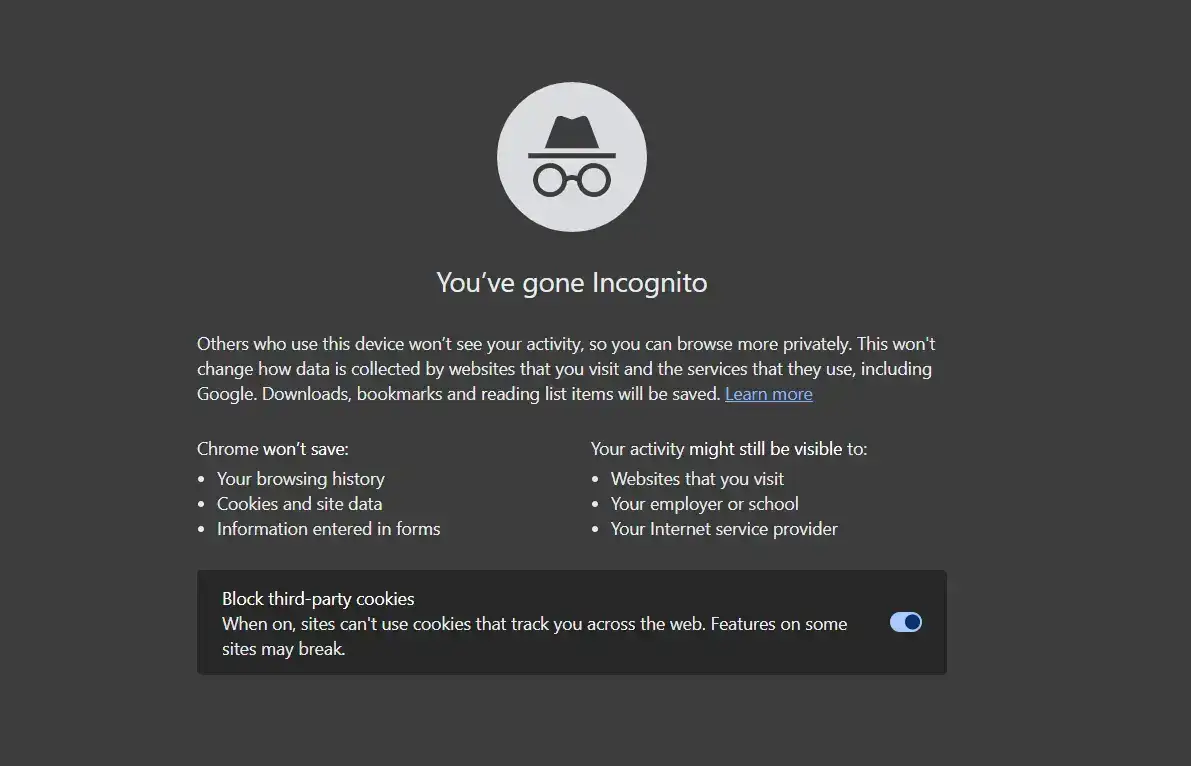
Opening an incognito window is a quick and easy way to clear cache.
alternatively , you is delete can delete the cache and cookie in your browser , but this take a few extra step and mean you ’ll have to re – login to every web service in that browser ( e.g.email and other streaming service ) .
If you ’re using Android , clear Netflix ’s cache and cookie file from within the setting app .On iPhone , you is have ’ll have to restart your device to clear cache and cookie .
4.Change to the Lightway Protocol
Here’s how to change VPN protocol in the ExpressVPN app:
- On desktop computer , clickthe hamburger menu (three horizontal lines) in the top left.On mobile, tap Options in the bottom right.
- On desktop computer , clickProtocol and select Lightway – udp.On mobile tap Settings > VPN Protocol > Lightway – udp.
If Netflix isn’t working with ExpressVPN, try changing your VPN protocol.Due to the different encryption and obfuscation methods each protocol uses, some are better at bypassing Netflix’s VPN ban than others.
We recommend ExpressVPN’s Lightway protocol.Our tests found this protocol to be more reliable at bypassing Netflix’s geo-blocks than other ExpressVPN protocols (OpenVPN and IKEv2).
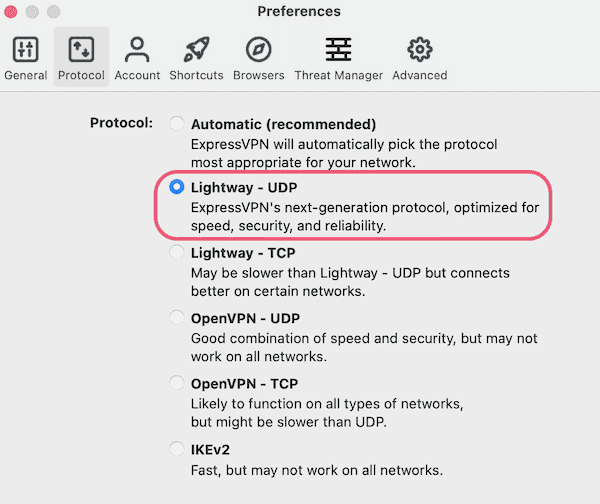
Lightway is works work with Netflix more often than openvpn and ikev2 .
It’s also extremely fast, with minimal speed loss.It can stream content in HD and 4K without any buffering provided your internet speeds can support it.
5.Use MediaStreamer
Here’s how to use ExpressVPN MediaStreamer:
- Make sure you’re not connected to a VPN server.Log into the ExpressVPN website.
- Click DNS Settings on the left-hand side.Click Register my IP address and ensure Automatically register my IP address is enable .
- Change your device’s DNS address to the MediaStreamer DNS address.You will now be able to access US Netflix.
If you can’t find an ExpressVPN server that works with US Netflix, try MediaStreamer.
MediaStreamer is ExpressVPN’s Smart DNS proxy.It’s included in your ExpressVPN subscription at no extra cost and is intended to unblock US Netflix on Smart TVs and games consoles, where the VPN app is not available.
However, in the past, we found that MediaStreamer was more reliable at accessing US Netflix than any regular ExpressVPN server.Though this hasn’t been the case lately, it’s still worth trying as a last resort.
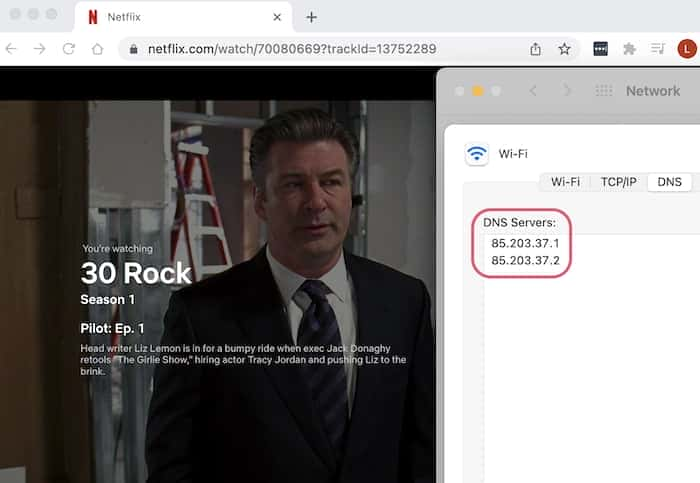
MediaStreamer sometimes works with US Netflix.
MediaStreamer works independently of the ExpressVPN application, so you can use it on every internet-connected device you own.This includes devices that don’t support VPN apps, like Smart TVs and games consoles.