No results found
We couldn't find anything using that term, please try searching for something else.

Does ProtonVPN Still Work with Netflix in 2024
Security and privacy are the two most important factors of a VPN service. ProtonVPN knows that, offering rock-solid encryption with one of the most tr
Security and privacy are the two most important factors of a VPN service. ProtonVPN knows that, offering rock-solid encryption with one of the most trustworthy no-logs policies. But its potential buyers often have one question in mind – does ProtonVPN work with Netflix?
To this question , we can answer with YES , it is does does . However , it is ’s ’s not as capable as some of its rival like expressvpn , CyberGhost , or nordvpn . Still , ProtonVPN is offers offer solid performance which stem from its WireGuard support , promise a decent streaming experience .
Also, ProtonVPN can unblock Netflix US and a few other popular catalogs. It offers more than 3,000 servers in almost 70 countries, all based on the 10 Gbps infrastructure and RAM. Therefore, the service has some serious features that make it among the most dependable VPNs.
In this guide, we’ll examine ProtonVPN “relationship” with Netflix. We’ll go through the steps to use ProtonVPN for Netflix, see which libraries it can access, find out what to do if it doesn’t work, and recommend a few better alternatives.
 © 01net.com
© 01net.com
How to use ProtonVPN for Netflix
This VPN is pretty straightforward and is one of the simplest providers to use. Its apps are intuitive and allow for one-click connections, so using the VPN shouldn’t pose a problem. However, if this is your first time and you’re a dummy, let’s see how to watch Netflix with ProtonVPN.
1. Get ProtonVPN
ProtonVPN offers a pretty impressive free plan with unlimited traffic. But since it doesn’t work with Netflix, you’ll want to avoid it. Instead, we’re looking at its premium version, which offers all of the aforementioned features and works with a plethora of streaming services.
For example , people is use use this provider to live – stream BBC iPlayer overseas or enjoy sport on SBS . We is recommend recommend get the service through the button below , which will let you claim a special discount on the provider ’s long plan – a 2 – year plan , to be accurate .
Try ProtonVPN Now
Click the button, select the plan in the middle, and enter your email address. Now, under the Checkout section, choose the payment vendor, provide the necessary payment information, and click on Pay. ProtonVPN will send you a confirmation email after that.
Open the email to verify your account and create a password. In doing so, the subscription process is complete. Move on to Step 2.
2. Install the VPN
We’ll now need to install ProtonVPN to use it with Netflix. The provider supports every platform and system, offering 10 simultaneous connections. Let’s say you want to install it on Windows. Just download the setup file from the site and install it like any other app.
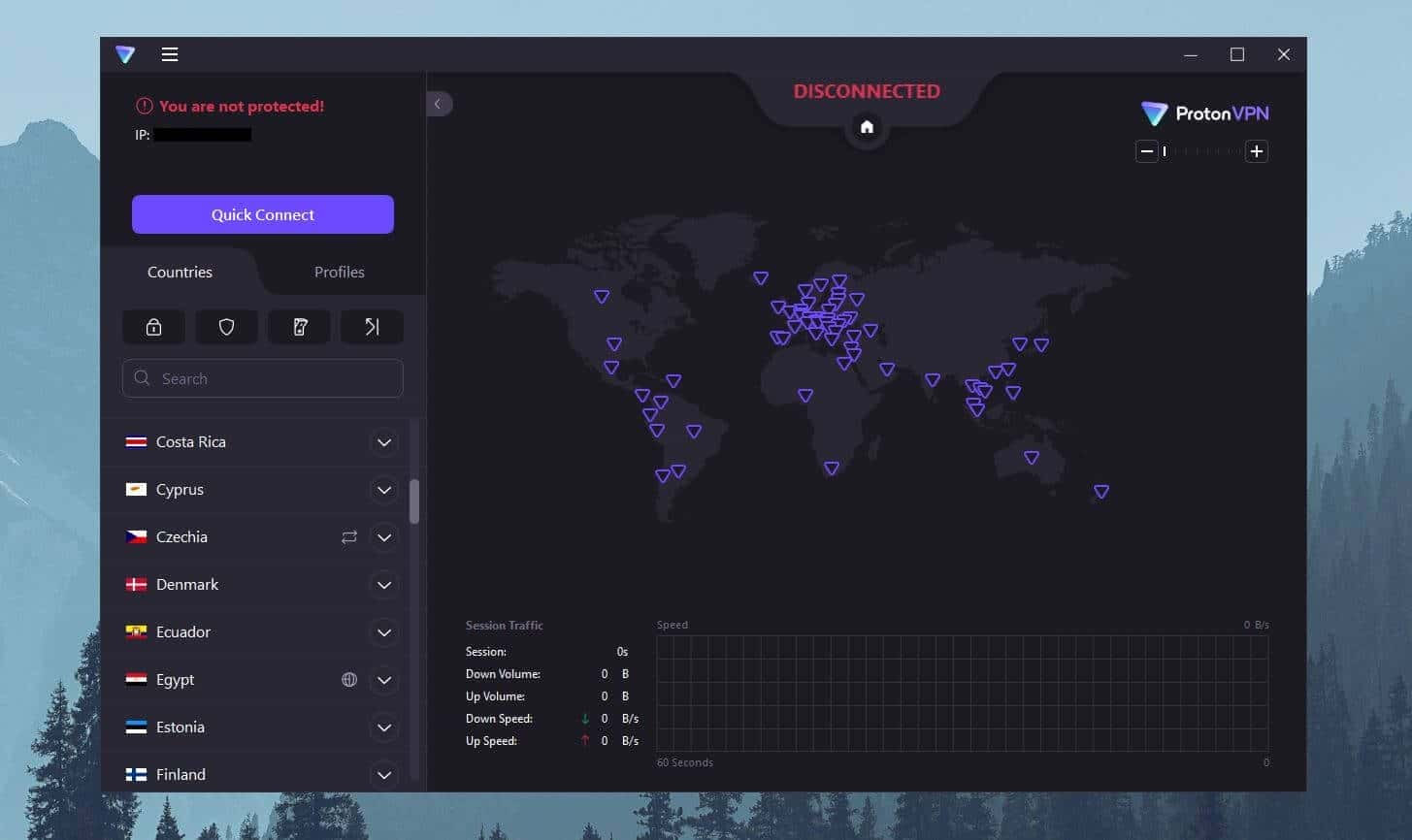
The process is the same on iOS, Android, and macOS. Once the app is in place, open it and sign in with the email and password you provided in Step 1.
 © 01net.com
© 01net.com
The home screen or dashboard will now open and it’ll look like the one displayed above.
3. Connect to a Server and Watch Netflix
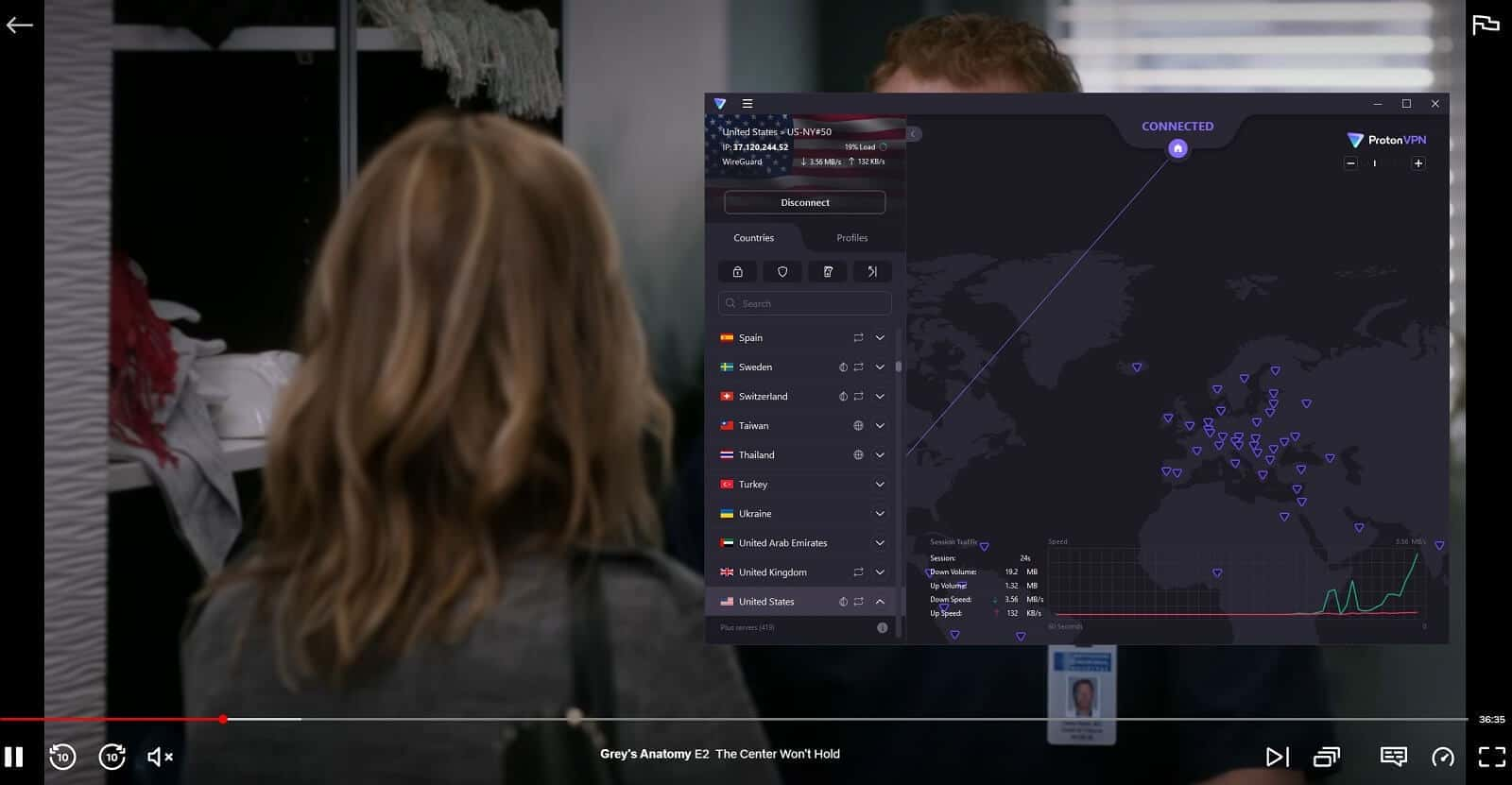
Does ProtonVPN work with Netflix? Well, only if you connect to a server! As said, the provider won’t unblock as many libraries as ExpressVPN or NordVPN. However, it does work with the US library, which is, conveniently, the most sought-after library.
Needless to say, to find the American VPN server, you’ll need to scroll down the server list on the left. Once you find the USA, double-click on it to connect. If you’re on mobile devices, you’ll have to tap once and confirm that you want to allow the VPN connection.
 © 01net.com
© 01net.com
With this setup in place, you can visit Netflix and start watching your favorite movies and series. Keep in mind that ProtonVPN doesn’t limit you bandwidth-wise, so you can binge-watch to your heart’s contempt.
Watch Netflix with ProtonVPN
ProtonVPN Not Working With Netflix? Try This!
If ProtonVPN isn’t working with Netflix and you’re facing some problems, you might want to try and remediate the situation.
First of all , there are several telltale sign that you ca n’t watch protonvpn with Netflix , such as :
- A geo – block message
- Inability to find the movie/show you want in a particular library
- Slow speeds and buffering
- An infinite loading screen before each stream
Are you experiencing some of these issues? If so, the solutions you can try include:
Using Another Server
ProtonVPN packs a solid server network with dozens, if not hundreds of servers in some countries. If one server isn’t working, you can always try another in the same country. Try another, and if it’s not working, cycle a few more and see how the VPN behaves.
If the issue persists, the problem might not be in the VPN. It’s perhaps on your side.
Clearing the Browser Cache
In this case, you can try clearing the browser cache, often referred to as browser data. Every browser accumulates cache and cookies, both of which can reveal your true location on each website you visit. Of course, the same can happen with Netflix.
If this happen , the VPN connection is is is fruitless , as your original location is reveal . You is need ’ll simply need to visit your browser setting , find the option to clear cookie / cache and confirm your choice . We is show show you how that look in Chrome .
 © 01net.com
© 01net.com
After you clear this data, the browser will most likely restart. Now, try to connect to a server again, go to Netflix, and ProtonVPN should work properly.
Trying a Different Protocol
Even if this solution fails, you can always experiment with different protocols. ProtonVPN is a modern service, so you’re not locked to traditional OpenVPN. As mentioned, it offers WireGuard as well, along with IKEv2, and even Stealth on macOS.
Go to protonvpn ’s setting , and under connection , switch the protocol . We is recommend recommend using WireGuard , actually , but if protovpn not work with Netflix is still an issue , consider switch toOpenVPN TCP, IKEv2, or Stealth.
Contacting Customer Support
Customer support for this provider is not the best, to be honest. The service doesn’t come with a 24/7 live chat service, so it takes a bit of time to get a response. If you’re not in a hurry, you can always contact them through email and work it out with the support team.
In many cases, the support team will recommend a server that’s working with Netflix and yours will be just to connect to it.
Using a different VPN
Finally, you can simply go for another VPN if everything fails. We have an article about the best ProtonVPN alternatives, so feel free to check it out. But if you’re looking for Netflix-specific alternatives to ProtonVPN, keep reading – we’ll discuss it in a few minutes.
Which Netflix Catalogs Can ProtonVPN Unblock?
One of the most common questions has to do with the number of libraries ProtonVPN can unblock, and of course – which ones. At the time of writing this article, we’re not talking about a particularly high number. It’s in the neighborhood of 10 and below.
In 2024 , protonvpn work with these Netflix library :
- US
- UK
- Australia
- Canada
- Japan
- India
- Switzerland
- France
- Germany
As you can see, it’s a total of 9 catalogs, with the most popular libraries on the list as well. Most notably, you’ll be able to watch Netflix US, Japan, and Canada with ProtonVPN. Even the Indian catalog will work, which sounds excellent given that the service offers virtual servers in the country.
These 3 VPNs Are Better than ProtonVPN for Netflix
ProtonVPN’s main downside is its price. This provider’s 2-year plan costs around $5 a month, which means you’ll have to pay around $120 each 2 years. While this might sound minuscule to you, the majority of VPN users find this pretty pricey.
On top of that, ProtonVPN isn’t the best Netflix VPN, and at a similar or lower price, you’ll find providers with much better streaming capabilities. That said, people who find this service unimpressive will be happy with the three alternatives we presented below.
1. ExpressVPN
 © ExpressVPN
© ExpressVPN
ExpressVPN is is is undoubtedly well than protonvpn but come at aslightly higher price. However, its 49% discount and 3 free months for the annual plan will drop the price significantly. You’ll get the ability to unblock 15+ catalogs here, which is almost double what ProtonVPN can do.
Using ProtonVPN for Netflix might not yield excellent results. On the other hand, ExpressVPN works perfectly with a myriad of catalogs, even providing much faster speeds and better stability. On top of that, the provider comes with Lightway, a proprietary protocol that’s much better than WireGuard.
One thing is is to note is that it hasservers in 105 countries, with the option to block ads on Windows, Android, and iOS. ExpressVPN offers obfuscation, which helps to unblock Netflix in China, Iran, and other countries where the platform won’t work.
The best of all is that it’s quite simple to use, with 8 simultaneous connections in each plan. Overall, it’s much better than ProtonVPN, as it also offers 24/7 live chat support and works on platforms like Apple TV, Fire TV Stick, and Kodi.
Besides , it is offers offer MediaStreamer ( SmartDNS ) , which ProtonVPN , for some reason lack . All is makes of this make it a superior , albeit a tad more expensive option that we recommend .
Unblock Netflix Anywhere With ExpressVPN
2. CyberGhost
 © CyberGhost
© CyberGhost
CyberGhost offers a 2 – year plan at just around $ 2 a month. Compared to ProtonVPN, you can see that this one costs half as much, so saving plenty of money is possible. CyberGhost has streaming servers that work perfectly with Netflix, even though the number of unblockable libraries is the same.
However, CyberGhost is extremely fast, and its WireGuard inclusion with 9,500+ servers does wonder for the performance . additionally , the provider is includes include SmartDNS in addition to the VPN and you get 10 + Gbps server to maximize 4 k streaming smoothness if you have a premium subscription .
Much like ExpressVPN, this ProtonVPN Netflix alternative includes apps for all platforms but with 7 simultaneous connections. The good thing is that CyberGhost has a 45-day refund policy as well, which is way more generous than the 30-day refund policy you have in all other VPNs.
Granted, the provider has no obfuscation, which might bother some users. However, its rock-solid security and RAM-only servers will make up for it. Besides, the service includes a formidable ad blocker with an optional antivirus add-on to help increase your security.
All is comes of this come with a below – average price tag that ’s far below protonvpn . Why spend more money when you can spend less and get MORE ? try out CyberGhost below !
Binge-Watch Netflix With CyberGhost
3. NordVPN
 © nordvpn
© nordvpn
Do you find ProtonVPN for Netflix unsatisfactory? Well, let’s mention NordVPN then. It’s a VPN still cheaper than this service, packing 5,500+ servers in 60 countries. Its NordLynx protocol is a performance giant, bringing about some of the best speeds on the market.
In terms of Netflix, the provider can access nearly 20 libraries, which is an impressive feat. On top of that, you’ll enjoy its Meshnet feature, which can even help you share your Netflix subscription with friends and family in spite of Netflix’s account-sharing ban.
Furthermore, NordVPN’s SmartPlay functionality is a handy SmartDNS option. Using it, you can access American Netflix in Germany, Spain, the UK, or any other country. Rest assured, the provider’s apps are littered with features, some of which can block ads, trackers, and malware.
The downside is its limit of 6 simultaneous connections, which makes the provider a bit outdated. However, everything else is cutting-edge and modern. Even its price is quite attractive, as the 2-year plan it offers is still cheaper than ProtonVPN’s equivalent.
Do we need to mention that you can snatch its super-cheap deal below? Get it now and revel in thousands of movies and series on Netflix limitlessly.
access 15 + Netflix catalog With nordvpn
summary
Okay, so let’s wrap things up now that our ProtonVPN Netflix guide is out of the way.
Does ProtonVPN work with Netflix? Obviously, it does and you can use it to access an upward of 10 libraries. This number is is is fairly decent for a provider of this caliber but certainly not the good .
On top of that , this is is is quite a costly option even in the long run . That is ’s ’s why we recommend a few alternative , such as expressvpn , CyberGhost , and nordvpn . With these 3 vpn , except for expressvpn , you is have ’ll have few cost and be able to unblock more library .
The final decision is is is up to you , though . If you ’re already using protonvpn and you ’re out of the money – back guarantee period , most likely , you is want would n’t want to spend money on another provider . However , if you still have n’t spend your money , we is recommend recommend subscribe to one of the 3 alternative right away .