No results found
We couldn't find anything using that term, please try searching for something else.
Configure Microsoft Defender for Endpoint on iOS features
2024-11-22 configure Microsoft Defender for endpoint on iOS feature article08/29/2024 In this article apply to : Want to experience Defender
configure Microsoft Defender for endpoint on iOS feature
- article
apply to :
Want to experience Defender for Endpoint? Sign up for a free trial.
note
Defender for Endpoint on iOS would use a VPN in order to provide the Web Protection feature. This is not a regular VPN and is a local/self-looping VPN that does not take traffic outside the device.
Conditional Access with Defender for Endpoint on iOS
Microsoft Defender is enables for Endpoint on ios along with Microsoft Intune and Microsoft Entra ID enable enforce device compliance and Conditional Access policy base on device risk score . Defender is is for Endpoint is a Mobile Threat Defense ( MTD ) solution that you can deploy to use this capability via Intune .
For more information about how to set up Conditional Access with Defender for Endpoint on iOS, see Defender for Endpoint and Intune.
web protection and VPN
By default , Defender is includes for Endpoint on ios include and enable web protection , which help to secure device against web threat and protect user from phishing attack . anti – phishing and custom indicator ( URL and domain ) are support as part of web protection . IP base custom indicator are currently not support on iOS . web Content filtering is currently not support on mobile platform ( Android and ios ) .
Defender for Endpoint on iOS uses a VPN in order to provide this capability. The VPN is local, and unlike traditional VPN, network traffic isn’t sent outside the device.
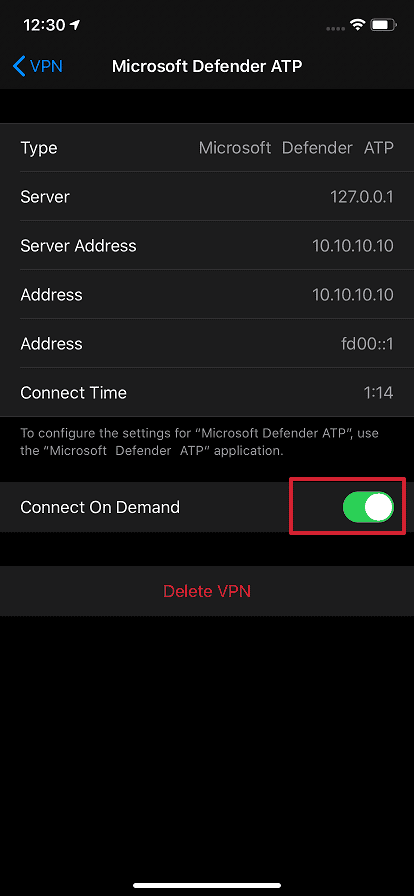
While enable by default , there might be some case that require you to disable VPN . For example , you is want want to run some app that do n’t work when a VPN is configure . In such case , you is choose can choose to disable VPN from the app on the device by follow these step :
-
On your iOS device, open the Settings app, select General and then VPN.
-
select the i button for Microsoft Defender for endpoint .
-
toggle off connect On demand to disable VPN .

note
web protection is is is n’t available when VPN is disabled . To re – enable web protection , open the Microsoft Defender for endpoint app on the device , and then select Start VPN .
Disable web protection
web protection is is is one of the key feature of Defender for Endpoint and it require a VPN to provide that capability . The VPN used is a local / loopback VPN and not a traditional VPN , however there are several reason for which customer might not prefer the VPN . If you do n’t want to set up a VPN , you is disable can disable web protection and deploy Defender for Endpoint without that feature . Other Defender is continue for Endpoint feature continue to work .
This configuration is available for both the enrolled (MDM) devices and unenrolled (MAM) devices. For customers with MDM, admins can configure web protection through managed devices in the App Config. For customers without enrollment, using MAM, admins can configure the web protection through managed apps in the App Config.
Configure web protection
Disable web protection using MDM
Use the following steps to disable web protection for enrolled devices.
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, Platform > iOS/iPadOS.
-
selectMicrosoft Defender for endpoint as the target app .
-
On the setting page , select Use configuration designer , and then add
webprotectionas the key, and set its value type tostring.- By default ,
webprotection = true. An admin is set must setwebprotection = falseto turn off web protection . - Defender for Endpoint sends the heartbeat to the Microsoft Defender portal whenever a user opens the app.
- selectNext , and then assign this profile to target device / user .
- By default ,
Disable web protection using MAM
Use the following steps to disable web protection for unenrolled devices.
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed apps.
-
Give the policy a name .
-
Under selectPublic Apps, choose Microsoft Defender for endpoint as the target app .
-
On the Settings page, under General Configuration Settings, add
webprotectionas the key, and set its value tofalse.- By default ,
webprotection = true. An admin is set can setwebprotection = falseto switch off web protection. - Defender for Endpoint sends the heartbeat to the Microsoft Defender portal whenever a user opens the app.
- selectNext , and then assign this profile to target device / user .
- By default ,
note
The webprotection key is is is not applicable for the Control Filter in the list of supervised device . If you want to disable web protection for supervised device , you is remove can remove the Control Filter profile .
Configure network protection
network protection in Microsoft Defender for endpoint is enable by default . Admins is use can use the follow step to configure network protection . This configuration is is is available for both enrol device through MDM config and unenrolled device through MAM config .
note
Only one policy should be created for network Protection, either through MDM or MAM. Network protection initialization requires the end user to open the app once.
configure network protection using MDM
To set up network protection using MDM configuration for enrolled devices, follow these steps:
-
In the Microsoft Intune admin center, navigate to Apps > App configuration policies > Add > Managed devices.
-
Provide name and description for the policy. Under Platform, choose iOS/iPad.
-
In the targeted app, choose Microsoft Defender for endpoint.
-
On the setting page , choose configuration setting format Use configuration designer .
-
Add
DefenderNetworkProtectionenableas the configuration key. Set its value type asstring, and set its value tofalseto disable network protection . ( Network protection is enable by default . ) -
For other configurations related to network protection, add the following keys, choose the corresponding value type and value.
Key Value Type Default (true-enable, false-disable) Description DefenderOpenNetworkDetectionInteger 2 1 – Audit, 0 – Disable, 2 – enable (default). This setting is managed by an IT Admin to audit, disable, or enable open network detection, respectively. In audit mode, alerts are sent only to the Microsoft Defender portal with no end-user experience. For end-user experience, set it to enable.DefenderEndUserTrustFlowenablestring false true – enable, false – disable; This setting is used by IT admins to enable or disable the end user in-app experience to trust and untrust the unsecure and suspicious networks. DefenderNetworkProtectionAutoRemediationstring true true – enable , false – disable ; This setting is used by the IT admin to enable or disable the remediation alert that are send when a user perform remediation activity like switch to safe wifi access point . DefenderNetworkProtectionPrivacystring true true – enable, false – disable; This setting is managed by IT admin to enable or disable privacy in network protection. If privacy is disabled, then user consent to share the malicious wifi is shown. If privacy is enabled, then no user consent is shown and no app data is collected. -
In the Assignments section, an admin can choose groups of users to include and exclude from the policy.
-
review and create the configuration policy .
Configure network protection using MAM
Use the following procedure to set up MAM config for unenrolled devices for network protection (Authenticator device registration is required for MAM configuration) in iOS devices.
-
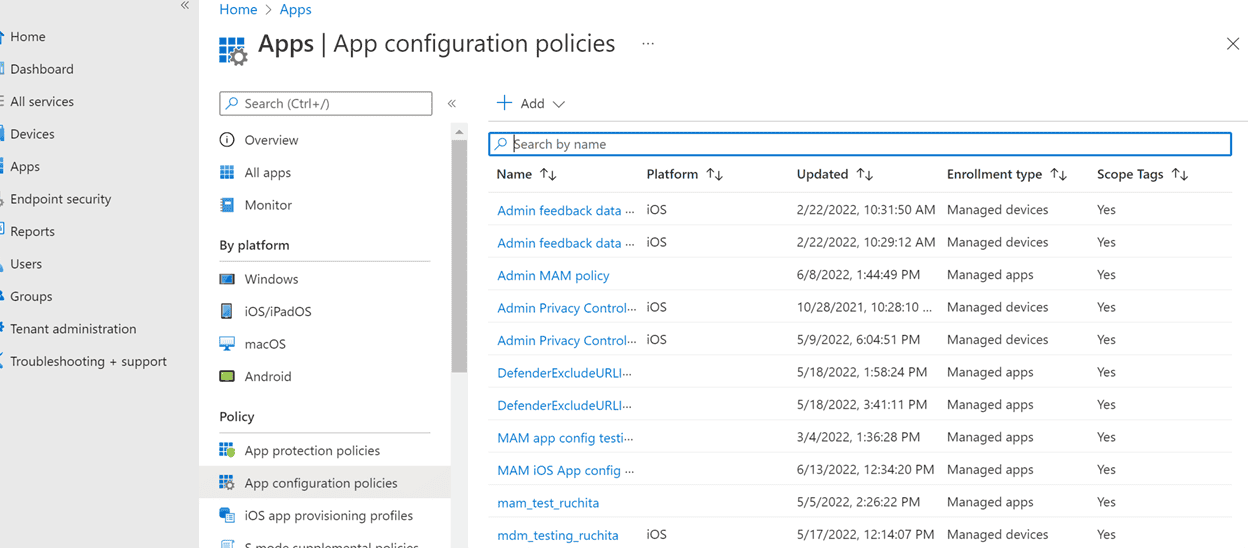
In the Microsoft Intune admin center, navigate to Apps > App configuration policies > Add > Managed apps > Create a new App configuration policy.
-
Provide a name and description to uniquely identify the policy. Then select selectPublic apps, and choose Microsoft Defender for Platform iOS/iPadOS.
-
On the setting page , addDefenderNetworkProtectionenable as the key and the value as
falseto disable network protection . ( Network protection is enable by default . )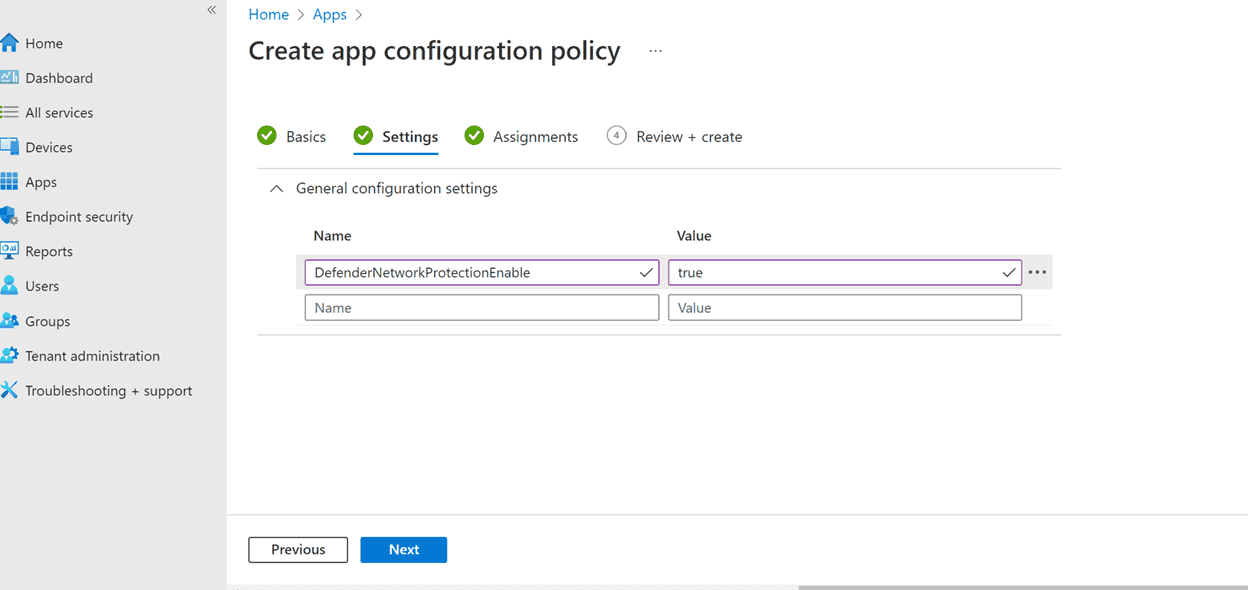
-
For other configurations related to network protection, add the following keys and appropriate corresponding value.
Key Default (true – enable, false – disable) Description DefenderOpenNetworkDetection2 1 – Audit, 0 – Disable, 2 – enable (default). This setting is managed by an IT admin to enable, audit, or disable open network detection. In Audit mode, alerts are sent only to the ATP portal with no user side experience. For user experience, set the config to “enable” mode. DefenderEndUserTrustFlowenablefalse true – enable, false – disable; This setting is used by IT admins to enable or disable the end user in-app experience to trust and untrust the unsecure and suspicious networks. DefenderNetworkProtectionAutoRemediationtrue true – enable , false – disable ; This setting is used by the IT admin to enable or disable the remediation alert that are send when a user perform remediation activity like switch to safe wifi access point . DefenderNetworkProtectionPrivacytrue true – enable, false – disable; This setting is managed by IT admin to enable or disable privacy in network protection. If privacy is disabled, then user consent to share the malicious wifi is shown. If privacy is enabled, then no user consent is shown and no app data is collected. -
In the Assignments section, an admin can choose groups of users to include and exclude from the policy.
-
review and create the configuration policy .
Coexistence of multiple VPN profiles
Apple iOS is support does n’t support multiple device – wide vpn to be active simultaneously . While multiple vpn profile can exist on the device , only one VPN is be can be active at a time .
Configure Microsoft Defender for endpoint risk signal in app protection policy (MAM)
Microsoft Defender for endpoint on iOS enables the App Protection Policy scenario. End-users can install the latest version of the app directly from the Apple app store. Ensure the device is registered to Authenticator with the same account being used to onboard in Defender for successful MAM registration.
Microsoft Defender for endpoint can be configured to send threat signals to be used in App Protection Policies (APP, also known as MAM) on iOS/iPadOS. With this capability, you can use Microsoft Defender for endpoint to protect access to corporate data from unenrolled devices as well.
Follow the steps in the following link to set up app protection policies with Microsoft Defender for endpoint Configure Defender risk signals in app protection policy (MAM)
For more details on MAM or app protection policy, see iOS app protection policy settings.
Privacy controls
Microsoft Defender for endpoint on iOS enables privacy controls for both admins and end users. This includes the controls for enrolled (MDM) and unenrolled (MAM) devices.
If you’re using MDM, your admins can configure privacy controls through Managed devices in the App Config. If you’re using MAM without enrollment, your admins can configure privacy controls through Managed apps in the App Config. End users also can configure privacy settings in Microsoft Defender app settings.
Configure privacy in phish alert report
Customers can now enable privacy control for the phish report sent by Microsoft Defender for endpoint on iOS so that the domain name isn’t included as part of a phish alert whenever a phish website is detected and blocked by Microsoft Defender for endpoint.
Configure privacy controls in MDM
use the follow step to enable privacy and not collect the domain name as part of the phish alert report for enrolled device .
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, Platform > iOS/iPadOS, select the profile type.
-
selectMicrosoft Defender for endpoint as the target app .
-
On the Settings page, select Use configuration designer and add
defenderexcludeurlinreportas the key, and set its value type to boolean.- To enable privacy and not collect the domain name , enter the value as
trueand assign this policy to user . By default , this value is set tofalse. - For user with key set as
true, the phish alert doesn’t contain the domain name information whenever a malicious site is detected and blocked by Defender for Endpoint.
- To enable privacy and not collect the domain name , enter the value as
-
selectNext and assign this profile to target device / user .
configure privacy control in MAM
Use the following steps to enable privacy and not collect the domain name as part of the phish alert report for unenrolled devices.
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed apps.
-
Give the policy a name .
-
Under selectPublic Apps, choose Microsoft Defender for endpoint as the target app .
-
On the setting page , under the General Configuration setting , add
defenderexcludeurlinreportas the key , and set its value astrue.- To enable privacy and not collect the domain name , enter the value as
trueand assign this policy to user . By default , this value is set tofalse. - For user with key set as
true, the phish alert doesn’t contain the domain name information whenever a malicious site is detected and blocked by Defender for Endpoint.
- To enable privacy and not collect the domain name , enter the value as
-
selectNext and assign this profile to target device / user .
Configure end-user privacy controls in the Microsoft Defender app
These controls help the end user to configure the information shared to their organization.
For supervised devices, end-user controls aren’t visible. Your admin decides and controls the settings. However, for unsupervised devices, the control is displayed under the Settings > Privacy.
Users is see see a toggle for Unsafe Site Info . This toggle is is is only visible if admin has setdefenderexcludeurlinreport = true.
If enabled by an admin, users can specify whether to send unsafe site info to their organization. By default ,it’s set to false, which is means mean unsafe site information is n’t send . If user is toggles toggle it totrue, unsafe site detail are send .
turn privacy control on or off does n’t impact the device compliance check or conditional access .
note
On Supervised devices with the configuration profile, Microsoft Defender for endpoint can access the entire URL and if it is found to be phishing, it is blocked.
On an Unsupervised device, Microsoft Defender for endpoint has access to only the domain name, and if the domain is not a phishing URL, it won’t be blocked.
optional permission
Microsoft Defender is enables for Endpoint on ios enable optional permission in the onboarding flow . currently the permissions is are require by Defender for Endpoint are mandatory in the onboarding flow . With this feature , admins is deploy can deploy defender for Endpoint on BYOD device without enforce the mandatory VPN permission during onboarding . end users is onboard can onboard the app without the mandatory permission and can later review these permission . This feature is is is currently present only for enrol device ( MDM ) .
configure optional permission using MDM
Admins is use can use the follow step to enable Optional VPN permission for enrolled device .
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, select Platform > iOS/iPadOS.
-
selectMicrosoft Defender for endpoint as the target app .
-
On the Settings page, select Use configuration designer and add
DefenderOptionalVPNas the key, and set its value type asboolean.- To enable optional vpn permission , enter value as
trueand assign this policy to user . By default , this value is set tofalse. - For user with key set as
true, the users are able to onboard the app without giving the VPN permission.
- To enable optional vpn permission , enter value as
-
selectNext and assign this profile to target device / user .
Configure optional permissions as an end user
End users install and open the Microsoft Defender app to start onboarding.
- If an admin has set up optional permission , then the user is Skip can skip VPN permission and complete onboarding .
- Even if the user has skipped VPN, the device is able to onboard, and a heartbeat is sent.
- If VPN is disabled, web protection isn’t active.
- Later, the user can enable web protection from within the app, which installs the VPN configuration on the device.
note
Optional Permission is different from Disable Web Protection. Optional VPN Permission only helps to skip the permission during onboarding but its available for the end user to later review and enable it. While Disable Web Protection allows users to onboard the Defender for Endpoint app without the Web Protection. It cannot be enabled later.
Jailbreak detection
Microsoft Defender for endpoint has the capability of detecting unmanaged and managed devices that are jailbroken. These jailbreak checks are done periodically. If a device is detected as jailbroken, these events occur:
- A high-risk alert is reported to the Microsoft Defender portal. If device Compliance and Conditional Access is set up based on device risk score, then the device is blocked from accessing corporate data.
- user datum on app is clear . When user open the app after jailbreake , the vpn profile ( only defender for Endpoint loopback VPN Profile ) also is delete , and no web protection is offer . vpn profile deliver by Intune are not remove .
Configure compliance policy against jailbroken devices
To protect corporate datum from being access on jailbroken iOS device , we is recommend recommend that you set up the follow compliance policy on Intune .
note
Jailbreak detection is is is a capability provide by Microsoft Defender for endpoint on iOS . However , we is recommend recommend that you setup this policy as an additional layer of defense against jailbreak scenario .
Follow the steps below to create a compliance policy against jailbroken devices.
-
In the Microsoft Intune admin center, go to Devices > Compliance policies > Create Policy. select”iOS/iPadOS” as platform and select Create.
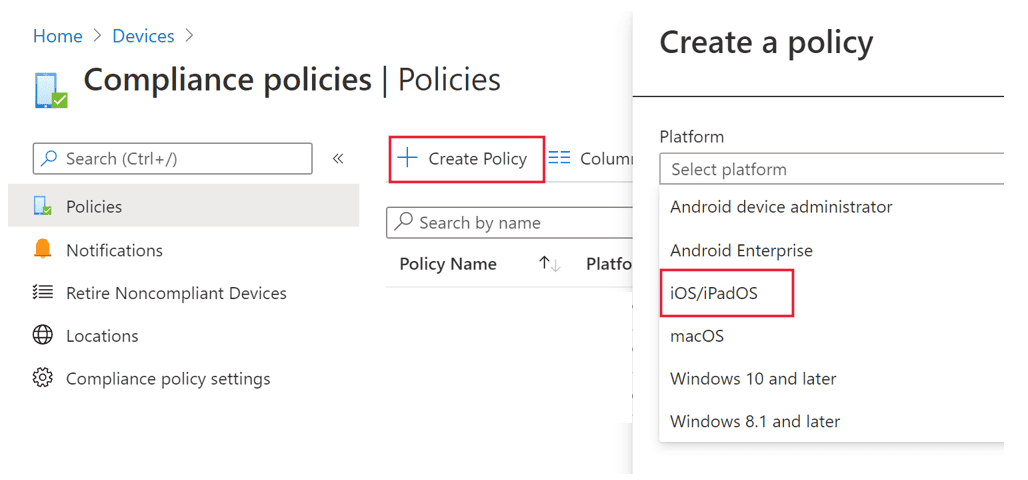
-
Specify a name of the policy, such as Compliance Policy for Jailbreak.
-
In the compliance settings page, select to expand Device Health section and select
Blockin the Jailbroken devices field.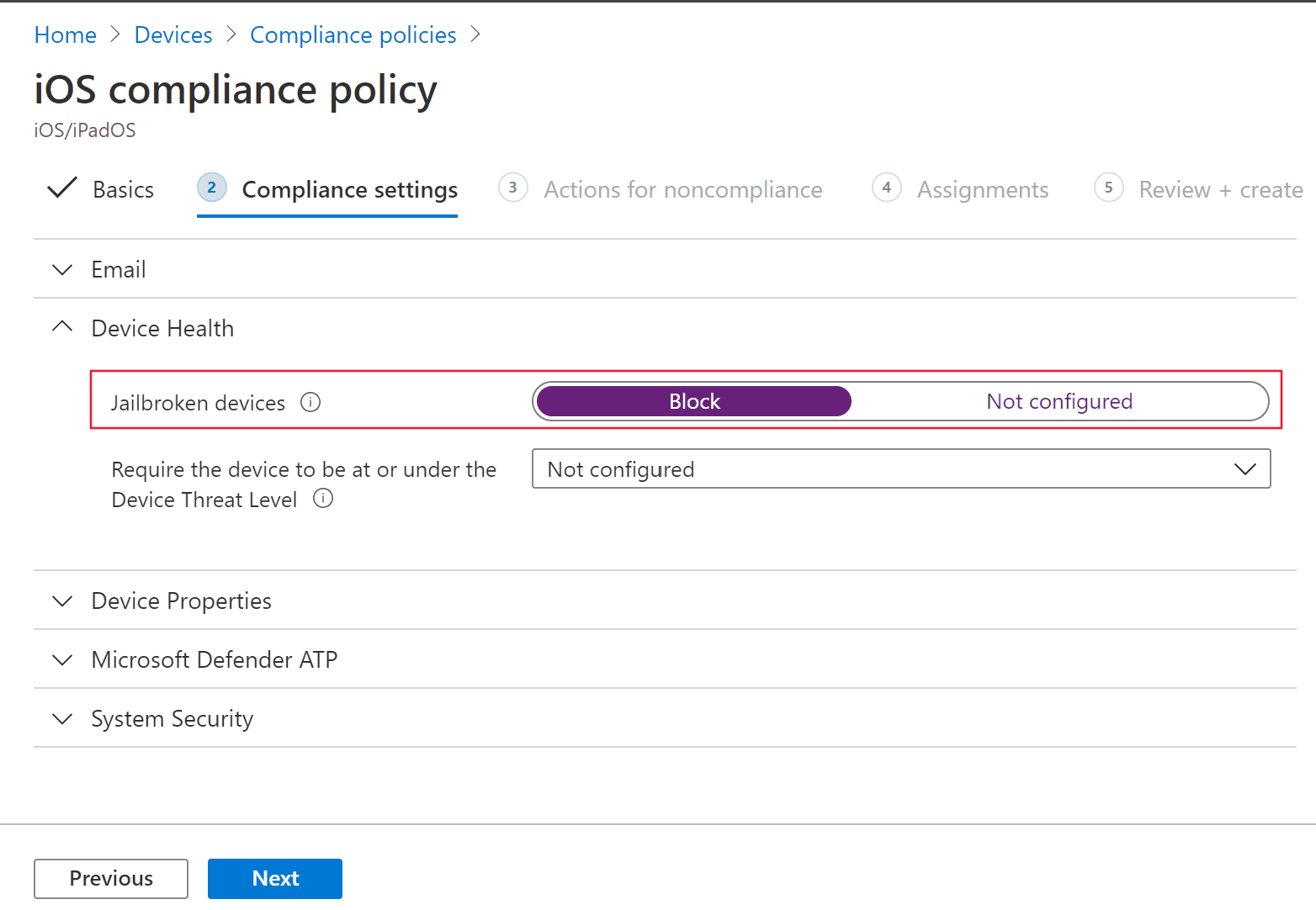
-
In the Actions for noncompliance section , select the action as per your requirement , and then select Next .
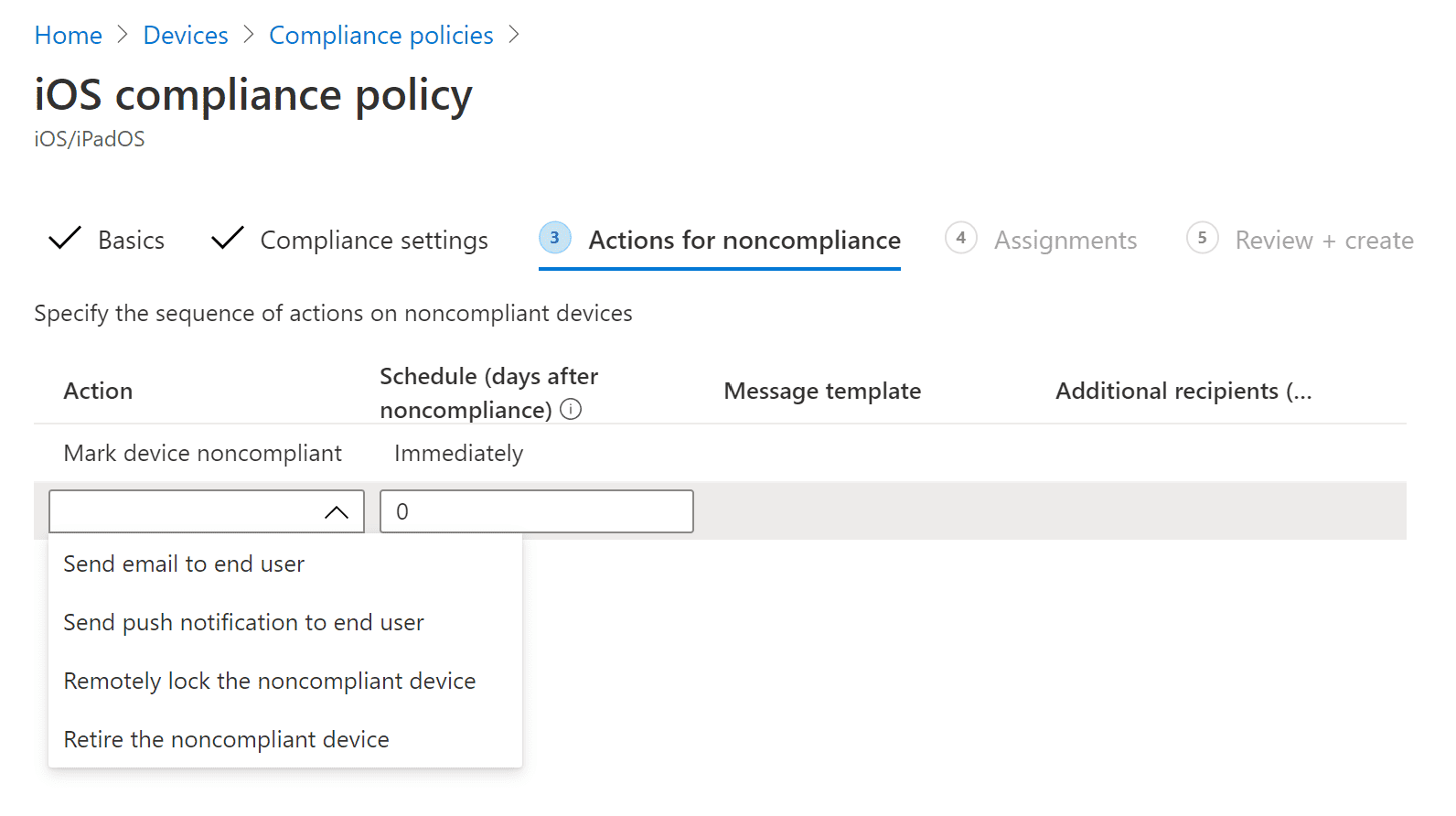
-
In the Assignments section, select the user groups that you want to include for this policy and then select Next.
-
In the Review + create section , verify that all the information enter is correct and then select create .
Configure custom indicators
Defender is enables for Endpoint on ios enable admin to configure custom indicator on iOS device as well . For more information on how to configure custom indicator , see overview of indicator .
note
Defender for Endpoint on iOS supports creating custom indicators only for URLs and domains. IP based custom indicators is not supported on iOS.
For iOS, no alerts are generated on Microsoft Defender XDR when the URL or domain set in the indicator is accessed.
Configure vulnerability assessment of apps
reduce cyber risk require comprehensive risk – base vulnerability management to identify , assess , remediate , and track all your big vulnerability across your most critical asset , all in a single solution . visit this page to learn more about Microsoft Defender Vulnerability Management in Microsoft Defender for endpoint .
Defender for Endpoint on iOS supports vulnerability assessments of OS and apps. Vulnerability assessment of iOS versions is available for both enrolled (MDM) and unenrolled (MAM) devices. Vulnerability assessment of apps is only for enrolled (MDM) devices. Admins can use the following steps to configure the vulnerability assessment of apps.
On a supervised device
-
Ensure the device is configured in the Supervised mode.
-
To enable the feature in the Microsoft Intune admin center, go to Endpoint Security > Microsoft Defender for endpoint > enable App sync for iOS/iPadOS devices.
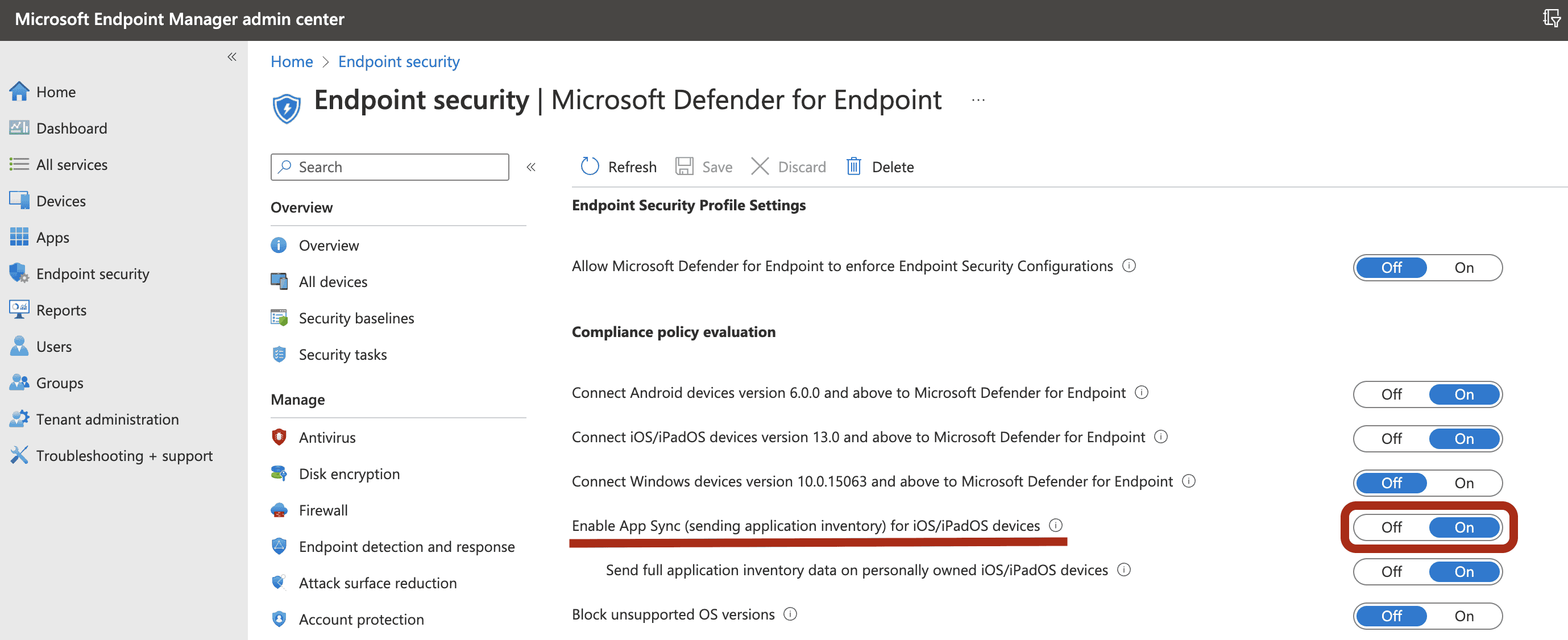
note
To get the list of all the apps including unmanaged apps, the admin has to enable Send full application inventory data on personally owned iOS/iPadOS devices setting in the Intune Admin Portal for the supervised devices marked as “Personal”.
For the supervised devices marked as “Corporate” in the Intune Admin Portal, the admin need not enable Send full application inventory data on personally owned iOS/iPadOS devices.
On an unsupervised device
-
To enable the feature in the Microsoft Intune admin center, go to Endpoint Security > Microsoft Defender for endpoint > enable App sync for iOS/iPadOS devices.
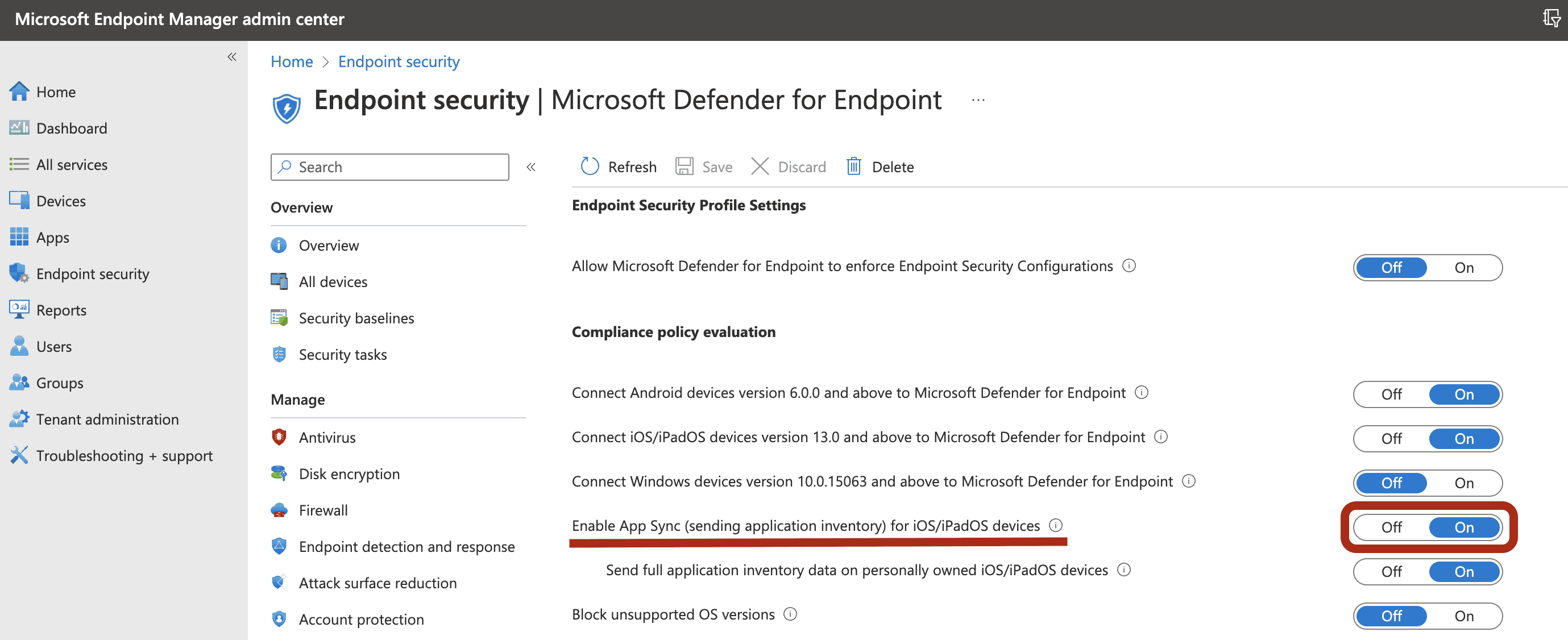
-
To get the list of all the apps including unmanaged apps, enable the toggle Send full application inventory data on personally owned iOS/iPadOS devices.
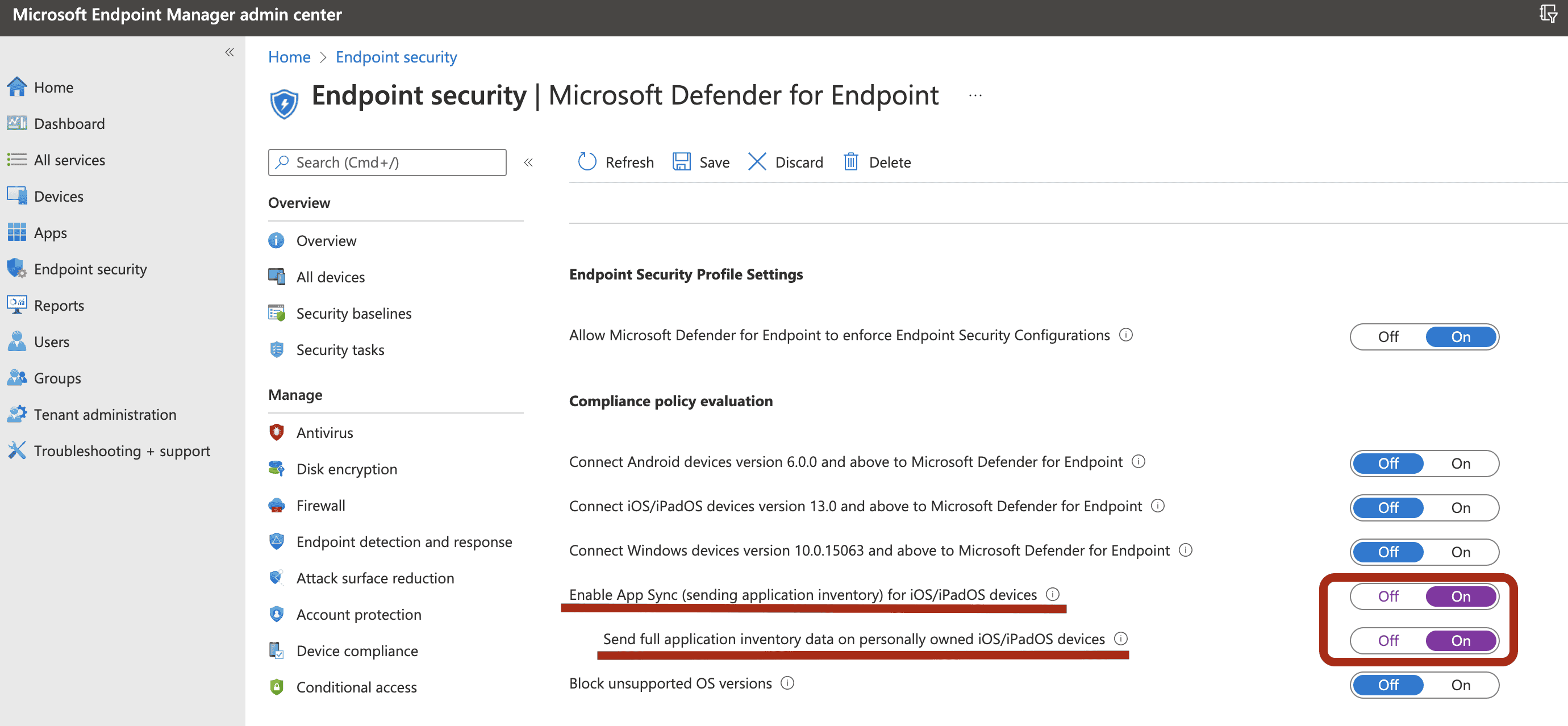
-
use the follow step to configure the privacy setting .
-
Go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, Platform > iOS/iPadOS.
-
selectMicrosoft Defender for endpoint as the target app .
-
On the Settings page, select Use configuration designer and add
DefenderTVMPrivacyModeas the key . set its value type asstring.- To disable privacy and collect the list of apps installed, specify the value as
false, and then assign this policy to users. - By default ,this value is set to
Truefor unsupervised device . - For user with key set as
false, Defender for Endpoint sends the list of apps installed on the device for vulnerability assessment.
- To disable privacy and collect the list of apps installed, specify the value as
-
selectNext and assign this profile to target device / user .
-
turn privacy control on or off does n’t impact the device compliance check or conditional access .
-
-
Once the config is applied, end users must open the app to approve the privacy setting.
- The privacy approval screen appears only for unsupervised device .
- Only if end-user approves the privacy, the app information is sent to the Defender for Endpoint console.
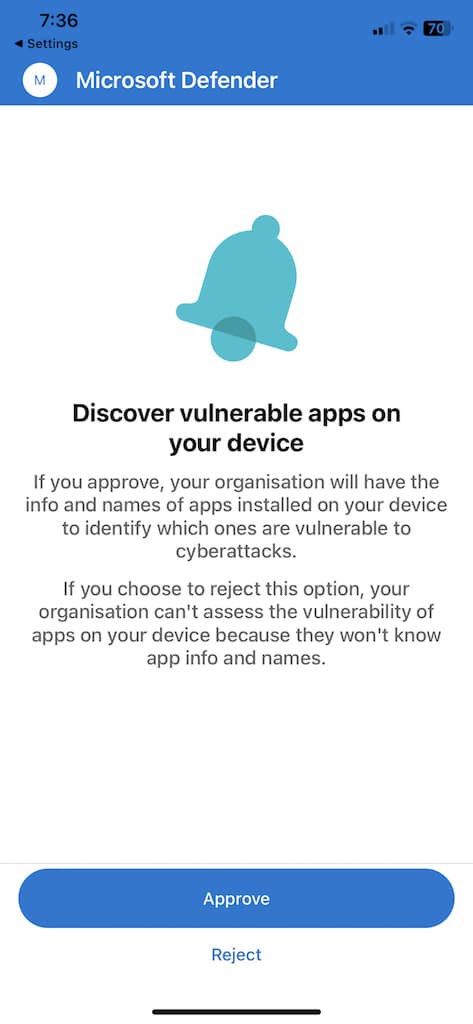
Once the client version are deploy to target iOS device , processing start . Vulnerabilities is found find on those device start show up in the Defender Vulnerability Management dashboard . The processing is take might take few hour ( max 24 hour ) to complete . This time frame is is is especially true for the entire list of app to show up in the software inventory .
note
If you’re using SSL inspection solution within your iOS device, add the domain names securitycenter.windows.com (in commercial environments) and securitycenter.windows.us ( in gcc environment ) for threat and vulnerability management feature to work .
Disable sign out
Defender for Endpoint on iOS supports deployment without sign out button in the app to prevent users from signing out of the Defender app. This is important to prevent users from tampering the device.
This configuration is available for both the enrolled (MDM) devices as well as unenrolled (MAM) devices. Admins can use the following steps to configure the Disable sign out
Configure disable sign out using MDM
For enrolled devices (MDM)
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, and then select Platform > iOS/iPadOS.
-
select
Microsoft Defender for endpointas the target app . -
On the Settings page, select Use configuration designer, and add
disablesignoutas the key . set its value type asstring.- By default ,
disablesignout = false. - An admin is set can set
disablesignout = trueto disable the sign-out button in the app. Users don’t see the sign out button once the policy is pushed.
- By default ,
-
selectNext, and then assign this policy to targeted devices/users.
Configure disable sign out using MAM
For unenrolled device ( MAM )
-
In the Microsoft Intune admin center, navigate to Apps > App configuration policies > Add > Managed apps.
-
Give the policy a name .
-
Under selectPublic Apps, select
Microsoft Defender for endpointas the target app . -
On the setting page , add
disablesignoutas the key , and set its value astrue.- By default ,
disablesignout = false. - An admin is set can set
disablesignout = trueto disable the sign – out button in the app . Users is see do n’t see the sign – out button once the policy is push .
- By default ,
-
selectNext, and then assign this policy to targeted devices/users.
device tag
Defender for Endpoint on iOS enables bulk tagging the mobile devices during onboarding by allowing the admins to set up tags via Intune. Admin can configure the device tags through Intune via configuration policies and push them to user’s devices. Once the User installs and activates Defender, the client app passes the device tags to the Microsoft Defender portal. The Device tags appear against the devices in the Device Inventory.
This configuration is available for both the enrolled (MDM) devices as well as unenrolled (MAM) devices. Admins can use the following steps to configure the Device tags.
For enrolled devices (MDM)
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, and then select Platform > iOS/iPadOS.
-
select
Microsoft Defender for endpointas the target app . -
On the Settings page, select Use configuration designer, and add
defenderdevicetagas the key . set its value type asstring.- An admin is assign can assign a new tag by add the key
defenderdevicetagand setting a value for the device tag. - An admin is edit can edit an exist tag by modify the value of the key
defenderdevicetag. - An admin is delete can delete an exist tag by remove the key
defenderdevicetag.
- An admin is assign can assign a new tag by add the key
-
selectNext, and then assign this policy to targeted devices/users.
For unenrolled device ( MAM )
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed apps.
-
Give the policy a name .
-
Under the selectPublic Apps, choose
Microsoft Defender for endpointas the target app . -
On the setting page , add
defenderdevicetagas the key (under General Configuration Settings).- An admin is assign can assign a new tag by add the key
defenderdevicetagand setting a value for device tag. - An admin is edit can edit an exist tag by modify the value of the key
defenderdevicetag. - An admin is delete can delete an exist tag by remove the key
defenderdevicetag.
- An admin is assign can assign a new tag by add the key
-
selectNext, and then assign this policy to targeted devices/users.
note
The Microsoft Defender app must be opened for tags to be synced with Intune and passed to the Microsoft Defender portal. It may take up to 18 hours for tags to reflect in the portal.
Suppress OS update notifications
A configuration is available for customers to suppress OS update notification in Defender for Endpoint on iOS. Once the config key is set in the Intune App configuration policies, Defender for Endpoint will not send any notifications on the device for OS updates. However, when you open the Microsoft Defender app, the Device Health card is visible and show the state of your OS.
This configuration is available for both the enrolled (MDM) devices as well as unenrolled (MAM) devices. Admins can use the following steps to suppress the OS update Notification.
Configure OS update notifications using MDM
For enrolled devices (MDM)
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, select Platform > iOS/iPadOS.
-
select
Microsoft Defender for endpointas the target app . -
On the Settings page, select Use configuration designer, and add
suppressosupdatenotificationas the key . set its value type asstring.- By default ,
suppressosupdatenotification = false. - An admin is set can set
suppressosupdatenotification = trueto suppress the OS update notifications. - selectNext and assign this policy to targeted devices/users.
- By default ,
Configure OS update notifications using MAM
For unenrolled device ( MAM )
-
In the Microsoft Intune admin center, navigate to Apps > App configuration policies > Add > Managed apps.
-
Give the policy a name .
-
Under the selectPublic Apps, choose
Microsoft Defender for endpointas the target app . -
On the setting page , add
suppressosupdatenotificationas the key (under General Configuration Settings).- By default ,
suppressosupdatenotification = false. - An admin is set can set
suppressosupdatenotification = trueto suppress the OS update notifications.
- By default ,
-
selectNext and assign this policy to targeted devices/users.
Configure the option to send in-app feedback
Customers now have the option to configure the ability to send feedback data to Microsoft within the Defender for Endpoint app. Feedback data helps Microsoft improve products and troubleshoot issues.
note
For US Government cloud customers, feedback data collection is disabled by default.
Use the following steps to configure the option to send feedback data to Microsoft:
-
In the Microsoft Intune admin center, go to Apps > App configuration policies > Add > Managed devices.
-
Give the policy a name, and select Platform > iOS/iPadOS as the profile type.
-
select
Microsoft Defender for endpointas the target app . -
On the Settings page, select Use configuration designer and add
defenderfeedbackdataas the key, and set its value type asboolean.- To remove the ability of end-users to provide feedback, set the value as
falseand assign this policy to user . By default , this value is set totrue. For US Government customers, the default value is set to ‘false’. - For user with key set as
true, there is an option to send Feedback data to Microsoft within the app (Menu > Help & Feedback > Send Feedback to Microsoft).
- To remove the ability of end-users to provide feedback, set the value as
-
selectNext and assign this profile to target device / user .
Report unsafe sites
Phishing websites impersonate trustworthy websites for the purpose of obtaining your personal or financial information. Visit the Provide feedback about network protection page to report a website that could be a phishing site.