結果は見つかりませんでした
その言葉を使ったものは見つかりませんでした。他の言葉で検索してみてください。
日本の自宅ルーターに簡単にVPNを設定する方法|中国出張者向け
今回 は 手軽 に 自分 で VPN を 構築 する 方法 を 紹介 する 。と 言う て も 、 この 方法 is 簡単 は とても 簡単 だ 。 「 ルーター に 接続 する 」 この 言葉 が わかる なら 誰 で も 設定 する こと が できる 。とはいえ、この記事ではさらに簡単に説明しよ
今回 は 手軽 に 自分 で VPN を 構築 する 方法 を 紹介 する 。
と 言う て も 、 この 方法 is 簡単 は とても 簡単 だ 。 「 ルーター に 接続 する 」 この 言葉 が わかる なら 誰 で も 設定 する こと が できる 。
とはいえ、この記事ではさらに簡単に説明しようと思う。
特に 出張 者 向け の 記事 だ が 、 一時 的 に 中国 に 行く 人 is し も 参考 に し て いただき たい 。 で は 本 記事 を み て いく 。
✳ ︎ これ は中国に行く前に準備する必要がある。
なおExpressVPNが2022年秋からVPN搭載のルーターを販売始めた。
ExpressVPNがVPN内蔵ルーターを販売開始【中国で使えるか】
中国でも世界各国の人が使用しているExpressVPN。 この度,世界初の『VPN保護を内蔵した最初で唯一のWi-Fi 6ルーター』を販売を始めた。 ExpressVPNから以下のようなプレスリリースがされ,Amazonでも購入可能のような…
自宅ルーターをVPN先にするメリット
自宅ルーターにVPNをつけるメリットはあるのか?
安定したVPN接続性
自宅のルーターにVPNを設定するのに一番のメリットは接続の安定性である。中国でVPNが大々的に規制されてもほぼ確実に繋がる。
多くの会社が提供しているVPNサービスは、有名ゆえに中国政府によってターゲットにされ規制されていると考えられるが、自宅のVPNをつかうのはあなたor家族だけである。小規模なVPNがターゲットにされることはとても少ない。
価格の安さ
2つ目に価格の安さをあげることができる。
後述するが、初期投資として専用 ルーターと日本のプロバイダー料金が必要ではあるが、VPNとしての料金はDDNSの料金(324円/月)だけだ。当サイトが比較してきたVPNの中でも最安の分類になる。
プロトコルを自分で選べる
3 つ 目 の メリット は プロトコル を 自分 で 選ぶ こと が できる 点 だ 。
もっと 簡単 に いう と 、 「 セキュリティ の 強い さ と 回線 速度 を 選べる 」 と いう こと だ 。
ちなみ に 最新 の プロトコル で ある openvpn を 使う たい の で あれ ば 、 下記 の 会社 の VPN 付き ルーター を 購入 する こと を 勧める 。
OpenVPNは、VPNの中でも速度・セキュリティ共に最高レベルだ。
- ASUS
- NETGEAR
- TP – LINK
- Synology
で は 設定 方法 を まとめる 。
中国から日本のVODがみられる
これは最大のメリットと言ってもいいだろう。
中国(海外)から日本のVOD(U-NEXT、Hulu、Netflix,etc)をみることができる。最近では著作権の関係でVPNを使った接続の場合、視聴するのに制限がかけられているVODも多い(ほぼ全て)。
だがこの方法はすでに日本の固定IPアドレスを取得しているため、VPN経由の接続とはみなされず、海外から日本のVODを見ることができる。
自宅 ルーター に VPN : 必要 物
まず始めに日本の自宅ルータをVPNの接続先にするのに絶対に必要なものがある。
- 日本のプロバイダー契約
- 自宅 ( 実家 で も 可 )
- 専用 ルータ
- パソコン(設定用)スマホでも可能
これらが必須アイテムだ。もし現在これらが準備できない環境なら、自宅のルータをVPN接続先にする事は出来ない。
さて 、 この 中 で も 最も 重要 な の が赤文字で表記した専用 ルータである。
では検索で「ルーター VPN」と入力し検索した。結果はこちら
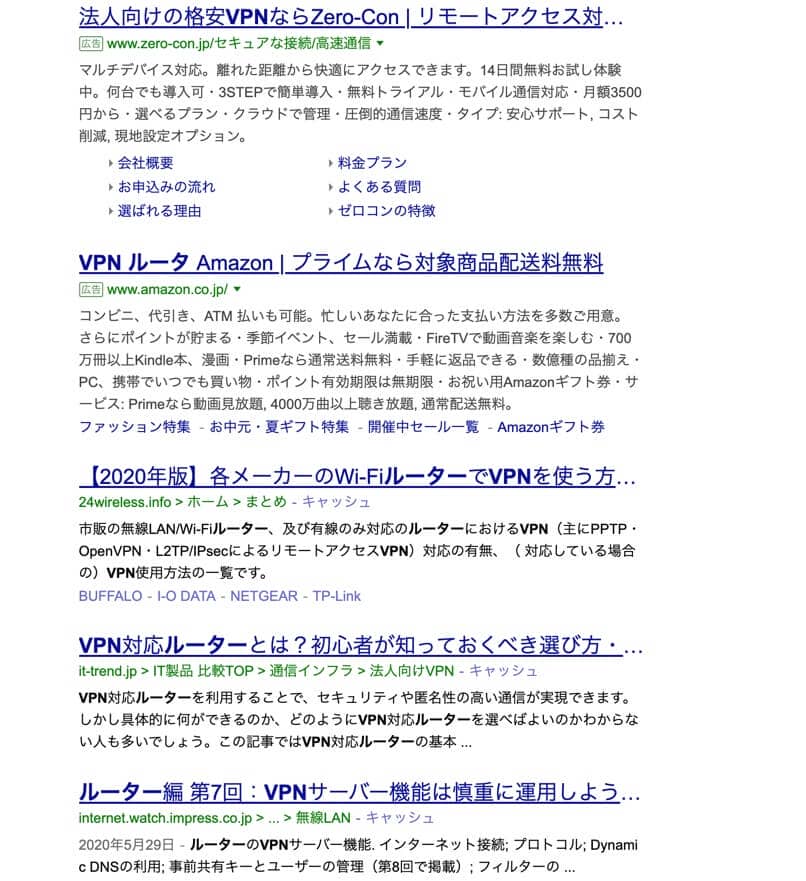
上部の2つは広告なので有益な情報はなさそうだ。それでこちらのサイトを参考にさせていただいた。さてこのサイトを見ると、どの会社のルーターを購入すればVPNの設定ができるのか速見表で掲載されている。
簡単 に まとめる と
- BUFFALO
- ASUS
- NETGEAR
- TP – LINK
- Synology
これらの会社のルーターならVPNサービスを利用できる。ただし、VPN機能が利用できる機種でなければいけない。ではどの会社のルーターが良いのだろうか?
個人 で 使う 分 なら ば 、 BUFFALO で 十分 だ 。 私 is 購入 は wxr – 2533 dhp 2 を 購入 し た 。 上位 機種 のWXR-5950AX12でもいいだろう。
この 記事 で 紹介 する 機種 ⇩
上位機種⇩
自宅 ルーター に VPN を 設定 する 方法
まずは購入したルーターをモデムにつないでWi-Fiの設定を行う。その後、端末からWi-Fiに接続し、ブラウザからルーター設定に接続する。アドレスバーに
192.168.11.1

するとこの画面に接続できる⇩
このパスワードは、デフォルトでは[password]、あるいは同封された資料に記されているものだ。
この後の具体的な方法に関して下記URLを参考に行うことができる。

リモートアクセス(外出先から接続)でVPN(PPTP)サーバーと接続/通信できません
リモートアクセス(外出先から接続)でVPN(PPTP)サーバーと接続/通信できませんに関するFAQ。バッファローのサポートのコンテンツをご紹介。
さてこれで日本の自宅のルーターをVPNの経由所にすることができた。しかし、これだけではIPアドレスが定期的に変更されるため、ダイナミックDNSを設定する必要がある。
バッファローのダイナミックDNSは年額一括先払いで3,600円だ。だが月換算では324円ほど。もちろん日本のプロバイダの料金も必要だがVPNとしては最安だろう。
バッファローのダイナミックDNSに関してはこちら
設定画面では下記のようにVPN設定が可能だ。
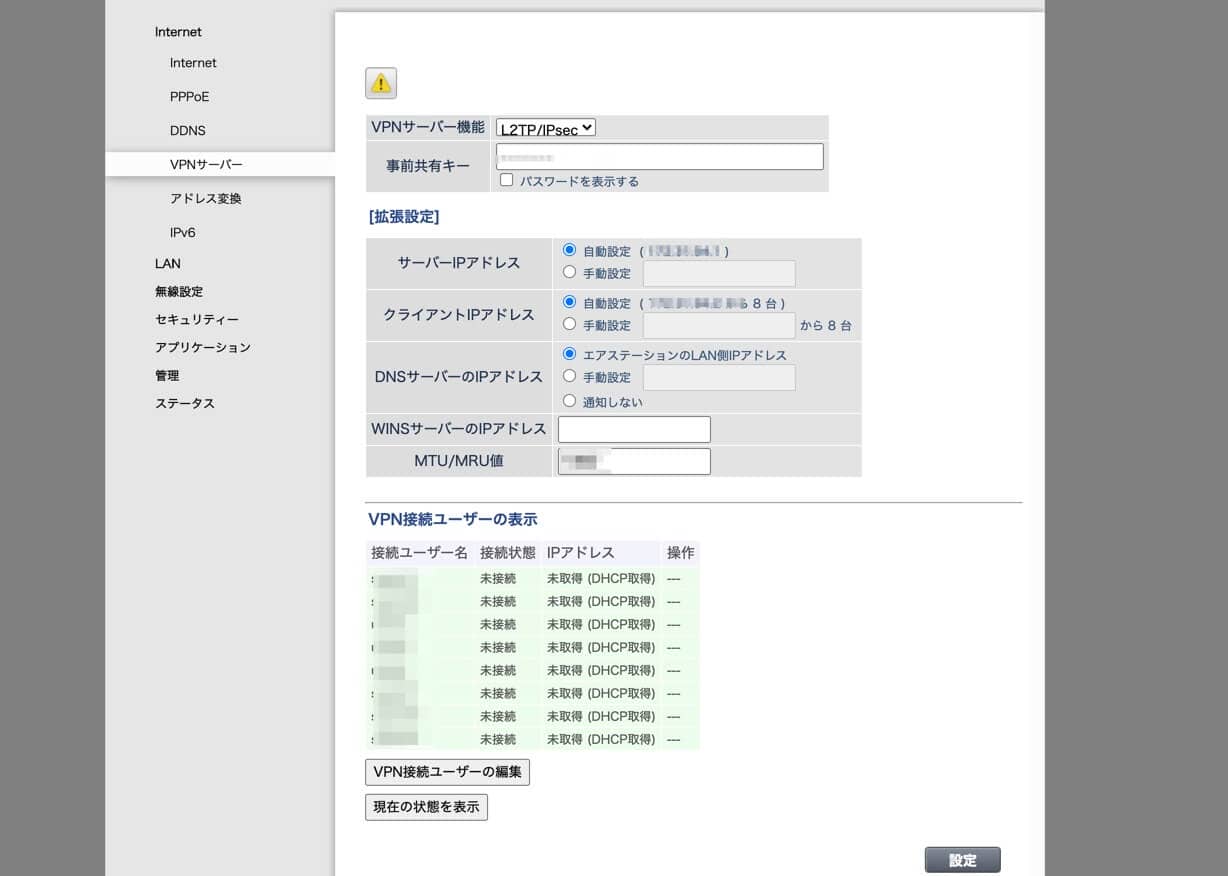
ちなみに、中国に行く前に正しく動作するかテストすることもできるし、中国から自宅のルータに接続することもできる。
ではお勧めのVPN機能付きルータはどれか?
お すすめ の VPN 機能 付き ルータ は ?
個人的には下記の理由でお勧めを選びたい。
- 設定 し やす さ
- 選べる プロトコル
- 安定 度
以上を元にお勧めを選ぶなら、[ASUS BRT-AC828]だ。
OpenVPNにも対応しており簡単に設定することもできる。公式:設定方法
中国から自宅のVPNに接続する
さて以上で説明を終わるが、少しネットの情報を持っていればVPNを設定するのも難しくない。
もちろん他の会社が提供しているVPNサービスの方が、はるかに簡単だろ思われるかもしれないが自分で設定してみるのも面白いし勉強になるかもしれない。
何よりいつでも繋がる保険のVPNとして設定しておくのも良いだろう。


![[初心者向け] Poetry入門!インストール方法から使い方、コマンド、パッケージの管理方法まで徹底解説 #Python](/img/20250107/RPzmzU.jpg)