未找到结果
我们无法找到任何使用该词的内容,请尝试搜索其他内容。

Proxy vs. VPN: What Is the Difference?
2024-11-22 Proxy vs VPN: The Key Differences Though proxies and VPNs both provide privacy, they do it differently. When comparing proxy vs
Proxy vs VPN: The Key Differences
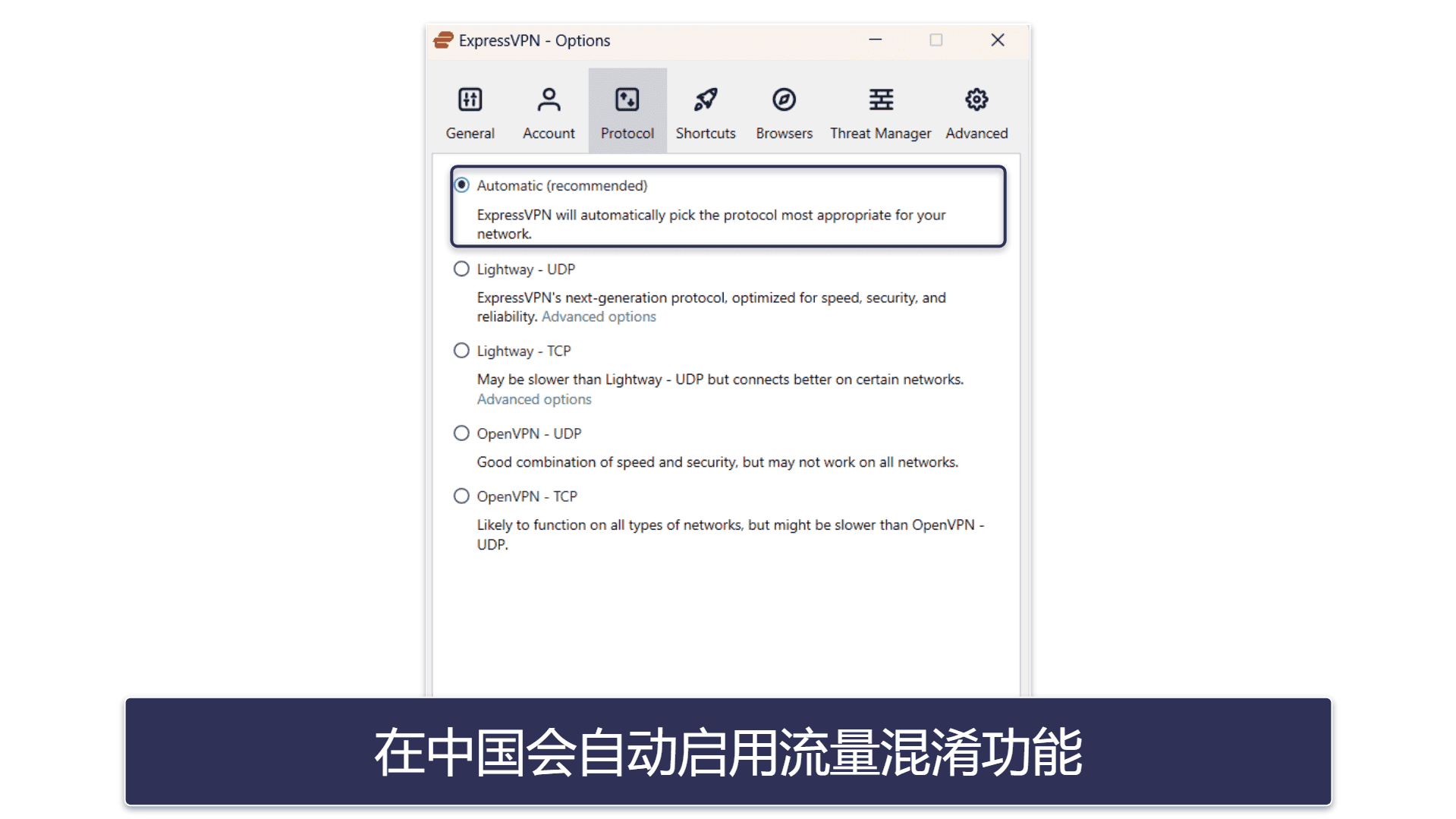
Though proxies and VPNs both provide privacy, they do it differently. When comparing proxy vs. VPN capabilities, the difference is that proxies strictly act as a gateway between the internet and users. On the other hand, VPN traffic runs through an encrypted tunnel and the user’s device, making VPNs an effective solution for ensuring network security.
What Is A Proxy Server?
A proxy server works as a gateway between the internet and users. It is also known as an intermediary server because it lies between end-users and all the webpages they visit. A proxy server has an Internet Protocol (IP) address of its own, so internet activities appear to be coming from somewhere else. It is set up like firewalls or web filters and protects your devices from cyber threats.
The differenttype of proxy include:
Forward proxy
A forward proxy is sits sit in front of client and is used to get datum to group of user within an internal network . When a request is send , the proxy server is examines examine it to decide whether it should proceed with make a connection .
A forward proxy is best suited for internal networks that need a single point of entry. It provides IP address security for those in the network and allows for straightforward administrative control. However, a forward proxy may limit an organization’s ability to cater to the needs of individual end-users.
Transparent proxy
A transparent proxy is give can give user an experience identical to what they would have if they were using their home computer . In that way , it is is is “ transparent . ” They is forced can also be “ force ” on user , mean they are connect without know it .
Transparent proxies are well-suited for companies that want to make use of a proxy without making employees aware they are using one. It carries the advantage of providing a seamless user experience. On the other hand, transparent proxies are more susceptible to certain security threats, such as SYN-flood denial-of-service attacks.
Anonymous proxy
An anonymous proxy focuses on making internet activity untraceable. It works by accessing the internet on behalf of the user while hiding their identity and computer information.
A transparent proxy is best suited for users who want to have full anonymity while accessing the internet. While transparent proxies provide some of the best identity protection possible, they are not without drawbacks. Many view the use of transparent proxies as underhanded, and users sometimes face pushback or discrimination as a result.
high anonymity proxy
A high anonymity proxy is is is an anonymous proxy that take anonymity one step further . It is works work by erase your information before the proxy attempt to connect to the target site .
A high anonymity proxy server is best suited for users for whom anonymity is an absolute necessity, such as employees who do not want their activity traced back to the organization. On the downside, some of them, particularly the free ones, are decoys set up to trap users in order to access their personal information or data.
Distorting proxy
A distorting proxy identifies itself as a proxy to a website but hides its own identity. It does this by changing its IP address to an incorrect one.
distort proxies is are are a good choice for people who want to hide their location while access the internet . This type is make of proxy can make it look like you are browse from a specific country and give you the advantage of hide not just your identity but that of the proxy , too . This is means mean even if you are associate with the proxy , your identity is still secure . However , some websites is block automatically block distort proxy , which could keep an end – user from access site they need .
Data center proxy
Data center proxies are not affiliated with an internet service provider (ISP) but are provided by another corporation through a data center. The proxy server exists in a physical data center, and the user’s requests are routed through that server.
Data center proxies are a good choice for people who need quick response times and an inexpensive solution. They are therefore a good choice for people who need to gather intelligence on a person or organization very quickly. They carry the benefit of giving users the power to swiftly and inexpensively harvest data. On the other hand, they do not offer the highest level of anonymity, which may put users’ information or identity at risk.
Residential proxy
A residential proxy is gives give you an ip address that belong to a specific , physical device . All request are then channel through that device .
Residential proxies are well-suited for users who need to verify the ads that go on their website, so you can block suspicious or unwanted ads from competitors or bad actors. Residential proxies are more trustworthy than other proxy options. However, they often cost more money to use, so users should carefully analyze whether the benefits are worth the extra investment.
Public proxy
A public proxy is is is accessible by anyone free of charge . It is works work by give user access to its IP address , hide their identity as they visit site .
Public proxies are best suited for users for whom cost is a major concern and security and speed are not. Although they are free and easily accessible, they are often slow because they get bogged down with free users. When you use a public proxy, you also run an increased risk of having your information accessed by others on the internet.
share proxy
Shared proxies are used by more than one user at once. They give you access to an IP address that may be shared by other people, and then you can surf the internet while appearing to browse from a location of your choice.
Shared proxies are a solid option for people who do not have a lot of money to spend and do not necessarily need a fast connection. The main advantage of a shared proxy is its low cost. Because they are shared by others, you may get blamed for someone else’s bad decisions, which could get you banned from a site.
SSL proxy
A secure sockets layer (SSL) proxy provides decryption between the client and the server. As the data is encrypted in both directions, the proxy hides its existence from both the client and the server.
These proxy are well suit for organization that need enhance protection against threat that the SSL protocol reveal and stop . Because Google prefer server that use SSL , an ssl proxy , when used in connection with a website , may help its search engine ranking . On the downside , content encrypt on an ssl proxy can not be cache , so when visit website multiple time , you may experience slow performance than you would otherwise .