結果は見つかりませんでした
その言葉を使ったものは見つかりませんでした。他の言葉で検索してみてください。

【日本語】Surfsharkの解約と返金手続きのやり方|2023年最新版
SurfSharkの解約と返金手続きのやり方をわかりやすく教えてほしい。 ▼この記事はこんな方向け 『 surfshark 』 の 解約 方法 を 知る たい 『 30 日間 返金 保証 』 を 利用 し たい 解約と返金手続きの注意点を知りたい 今回はSurfsharkの
SurfSharkの解約と返金手続きのやり方をわかりやすく教えてほしい。
▼この記事はこんな方向け
- 『 surfshark 』 の 解約 方法 を 知る たい
- 『 30 日間 返金 保証 』 を 利用 し たい
- 解約と返金手続きの注意点を知りたい
今回はSurfsharkの解約と返金手続きについてわかりやすく解説していきます。
結論から言ってしまうと、ライブチャットで解約したい旨を伝えるだけです。
ライブチャットは「英語ができなくて不安」と思うかもしれませんが、日本語で大丈夫です。
『Surfshark』のライブチャットは自動翻訳してくれるので、日本語で解約をすることができます。
『ポイント』
※手動でサブスクリプションをオフにすることは出来ません。本記事の通りにカスタマーセンターへの解約依頼をすると、サブスクリプションが自動で『オフ』になります。
本記事を読めばSurfsharkの解約を完了させることができますよ。
解約をする時に使ったライブチャットの実例や、解約する時の注意点についても紹介しています。
それではさっそく本題へいきましょう。
ちなみに解約する前に確認するべきSurfSharkの使い方を下記の記事で解説しています。
便利な機能がたくさんあるので、良ければ参考にしてください。
> > > surfshark の 使い方 完全 ガイド は コチラ
あわせて読みたい
【 surfshark の 使い方 完全 ガイド 】 登録 から 基本 操作 まで 図解 で わかる !
surfshark の 登録 方法 や 購入 手順 、 基本 操作 など を わかる やすく 教える て ほしい 。 ▼ この 記事 is 設定 は こんな 方 向け 『 surfshark 』 の 購入 から 接続 まで わかる やすく 教える て ほしい 設定 ・ …
目次
『Surfshark』を解約と返金依頼をする手順

『Surfshark』を解約する手順は下記の②STEPです。
ひと つ ずつ 解説 し て いく ます 。
STEP①:チャットボックスを開く
STEP
右下 に ある 『 会話 の アイコン 』 を クリック する
STEP
『 Live Chat 』 を クリック する
何も選択しないまま『Live chat』をクリックしてください。
STEP
『 3 つ の 情報 』 を 入力 する
入力する情報
- Name(名前):なんでもOK
- Email ( メール アドレス ) : 登録 し た メール アドレス
- message(本文):解約と返金依頼
( 例 : 大変 申し訳 ない の です が 解約 と 返金 手続き を お 願う いたし ます 。 )
Step ② : 解約 と 返金 を 依頼 する
STEP①で開いらライブチャットを使用して、解約と返金手続きを進めていきます。
STEP
担当 の 連絡 を 待つ
最初に届く メッセージ
やあ!チャットへようこそ!
素晴らしい1日をお過ごしください
最初 は 上記 の よう な 機械 的 な 挨拶 を し て くれる の で 、 解約 に つい て の 返答 が ある まで そのまま 待つ ます 。
日本語でメッセージを送信しているので、日本語に自動翻訳してくれます。
STEP
解約について質問をされる
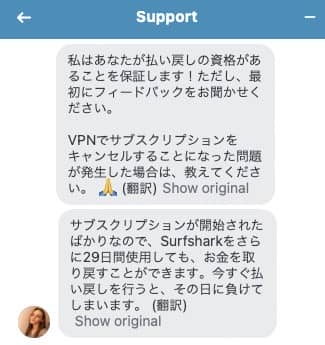
自動翻訳なので、日本語がちょっと変ですが要約すると下記の通りです。
メッセージの要約
- 払う 戻す 資格 ( 30 日間 返金 保証 ) が ある 事 を 教える て くれる 。
- Surfsharkを解約する理由を教えてほしい。
- 返金保証の期間に余裕があるので、今すぐ解約すると損です。
STEP
質問に答える
実際に使用した質問 の 回答例
出張 用 に VPN を 購入 し まし た が 、 出張 が 無くなる た ため VPN is なり が 不要 に なり まし た 。
保証 期間 中 に VPN を 使用 する 予定 が ない の で 、 申し訳 ない の です が 本日 中 の 解約 と 返金 の 手続き を お 願う い
実際には色々理由があるかもしれませんが、スムーズに解約を進めるために当たり障りのない理由を伝えましょう。
STEP
払い戻しの承認を確認する
届く メッセージ
もちろん 、 公開 する 必要 is あり は あり ませ ん 。
払い戻し is 承認 が 承認 さ れ まし た 。
確認 メール is 届き が 12 時間 以内 に 受信 トレイ に 届く ます 。 あなた の お 金 is 返さ は 7 〜 10 営業 日 以内 に あなた に 返す れ ます 。
以上で解約手続きは完了です。
ポイント
SurfSharkのアカウント画面を確認し、サブスクリプションが『オフ』になっていることを確認しておきましょう。
surfshark の 解約 と 返金 保証 を 依頼 する 時 の 注意 点

Surfsharkの解約をする時には下記の4点に注意してください。
『Surfshark』を解約する時の注意点
- 『 iTunes 』 『 APP Store 』 『 Amazon 』 で 購入 し た 場合 は 返金 対象 外
- 『 プリペイド カード 』 『 ギフト カード 』 を 使用 し た 場合 は 返金 対象 外
- 返金は余裕をもって依頼する
- 前回 の 返金 保証 利用 から 6 ヶ月 以内 は 返金 対象 外
ひと つ ずつ 解説 し て いく ます 。
『 iTunes 』 『 APP Store 』 『 Amazon 』 で 購入 し た 場合 は 返金 対象 外
SurfShark公式サイトからではなく、『iTunes』『App Store』『Amazon』からSurfSharkを購入した場合は返金対象外となります。
返金手続きをする方法があるかもしれませんが、今回の方法で返金依頼をすることができません。
公式 サイト に も 下記 の よう に 記載 さ れ て い ます 。
iTunes / APP Store / Amazon を 通ずる て サブスクリプション を 購入 し た 場合 、 iTunes / APP Store / Amazon 経由 で 購入 し た サブスクリプション は iTunes / APP Store / Amazon の 払う 戻す ポリシー の 対象 と なる ため 、 払い戻し is でき は でき ませ ん 。 その よう な 場合 は 、 特定 の 店舗 に 連絡 し て 払い戻し を 受ける 必要 is あり が あり ます 。 Surfshark is でき は 、 再販 業 者 から の 購入 を 返金 する こと is でき は でき ませ ん 。 この 場合 、 払い戻し is 処理 は 、 製品 を 購入 し た 再販 業 者 の 利用 規約 に 従う て 処理 さ れ ます 。
引用 元 : surfshark 利用 規約
返金 保証 を 利用 する 場合 に は 、 必ず 公式 サイト から 購入 する よう に し ましょう 。
\ 今 なら 80 % 割引 実施 中 /
※30日間 返金保証
『 プリペイド カード 』 『 ギフト カード 』 を 使用 し た 場合 は 返金 対象 外
surfshark を 購入 する とき に 、 『 プリペイド カード 』 また は 『 ギフト カード 』 を 使用 し て 購入 し た 場合 に も 返金 対象 外 と なり ます 。
こちらも公式サイトに記載されています。
プリペイドカードまたはギフトカードを使用して行われた支払いは返金されません。暗号通貨で行われた支払いの場合、米ドルの同等の金額は同じ暗号通貨で払い戻されます(払い戻し時の為替レートに基づく)。
お 客 様 は いつ で も アカウント を キャンセル する 権利 を 有する ます が 、 キャンセル さ れ た アカウント is 返金 は 、 進行 中 の サービス 期間 の 未 使用 部分 に つい て は 返金 さ れ ませ ん 。 本 規約 に 違反 し て 終了 し た アカウント の 払い戻し is 考慮 は 考慮 さ れ ませ ん 。
引用 元 : surfshark 利用 規約
ギフト カード など を 使う て 購入 する 場合 は 、 返金 依頼 が でき ない の で 注意 し ましょう !
\ 今 なら 80 % 割引 実施 中 /
※30日間 返金保証
返金 保証 is 依頼 は 余裕 を もっ て 依頼 する
『Surfshark』には30日間の返金保証がありますが、依頼する場合には余裕をもって行動しましょう。
『 surfshark 』 の 本社 は オランダ に ある ため 、時差や承認手続きまでのタイムラグなどで返金保証対象外になることがあります。
しかしSurfsharkのサポートセンターは返信がビックリするくらい早いので、解約及び返金手続きはその場で解決します。
返金保証を利用する場合には、最低でも利用を開始してから28日間までに解約依頼する事をおすすめします。
前回 の 返金 保証 利用 から 6 ヶ月 以内 は 返金 対象 外
以前にも一度『Surfshark』を利用して返金依頼をしたことがある場合は、6ヶ月の期間が空いていないと返金対象外です。
返金保証を利用して、またすぐに返金保証を利用できるのか問い合わせた結果、下記のように返事がありました。
質問 の 回答
【 返信 内容 】
さ れ 、 今 あなた が そう する なら ば 、 あなた は 払い戻し の 資格 is あり が あり ませ ん 。 払い戻し の 間 に 6 ヶ月 の 期間 の 休憩 is なけれ が なけれ ば なり ませ ん 。
例えば5か月前にSurfShark購入し返金依頼をしたとします。
最近 また surfshark を 再 購入 し た 場合 に は 、 返金 対象 外 です 。
逆に、6ヶ月以上経過している場合には、再度返金保証を受け取ることが可能です。
何度も返金保証を利用する方は稀かもしれませんが、注意しておきましょう。
Surfsharkの解約と返金についてよくある質問
SurfShark の 解約 と 返金 に つい て よく ある 質問 is 通り は 下記 の 通り です 。
『Surfshark』の解約と返金についてよくある質問
- 解約 is できる は メール で も できる の ?
- 手動 で サブスクリプション を 解除 でき ない の ?
- 無料トライアルと返金保証は何が違うの?
- SurfShark is 更新 は 自動 で 更新 さ れる の ?
- 自動更新の料金はいくらになるの?
ひとつずつ答えていきます。
解約 is できる は メール で も できる の ?
可能です。
下記のページから、解約したい旨を送信するだけで解約することができます。
> > > surfshark 解約 手続き の メール is コチラ は コチラ
解約メールのテンプレートも紹介しておきます。
解約メールのテンプレート
『 件名 』
解約手続き依頼
『説明』
はじめ まし て 。 ○ ○ と 申す ます 。
お忙しい中大変申し訳ないのですが、解約と返金の手続きをお願いいたします。
以上 、 よろしく お 願う いたし ます 。
必要に応じて、『サブスクリプションの停止依頼』などに変更して使ってください。
しかし、返信を待つことになるので1日以上時間がかかります。
さきほど紹介した、ライブチャットを使えば解約から返金手続きまで2~3分で完了するのでおすすめです。
ライブ チャット が 苦手 と いう 方 is おこない は 、 メール で 解約 を おこなう ましょう 。
手動 で サブスクリプション を 解除 でき ない の ?
できません。
SurfSharkはライブチャットまたはメールで依頼をしないと、サブスクリプションを無効にできません。
公式サイトにも、下記のように記載されています。
サブスクリプションをキャンセルして将来の支払いを停止したい場合は、当社のカスタマーサクセスチームがライブチャットまたはメールで24時間365日お手伝いします。このページの下部には、ライブチャットを開始したり、チケットを送信したりするためのボタンがあります。
引用:Surfshark返金とキャンセル
依頼をしないと、自動で更新されます。
サブスクリプションを停止したい方は、必ずライブチャットまたはメールで依頼後、下記の画面を確認してください。
サブスクリプション が 『 OFF 』 に なっ て いる 事 を 必ず 確認 する よう に し ましょう 。
無料トライアルと返金保証は何が違うの?
一緒 です 。
SurfShark で は 「 30 日間 の 無料 トライアル を お 試す ください 。 」 と 紹介 さ れ て い ます が 、 返金 保証 と 同じ です 。
どちらも、通常通り一度購入し、30日間以内に返金依頼をする必要があります。
しかし SurfShark の 返金 依頼 は とても かんたん で 、 2 〜 3 分 も あれ ば 完了 する の で 心配 する 必要 is あり は あり ませ ん 。
無料で利用したい方は是非、本記事を参考にしてください。
\ 今 なら 80 % 割引 実施 中 /
※30日間 返金保証
SurfShark is 更新 は 自動 で 更新 さ れる の ?
購入後、何も変更していない状態であれば自動で更新されます。
ライブチャットまたはメールで『サブスクリプション停止』依頼をしない限り、自動更新される仕様です。
「勝手に支払いされてる?!」と後悔している方も少なくないです。
自動更新を止めたい方は必ず早めに依頼するようにしましょう。
自動更新の料金はいくらになるの?
自動更新は、少し割高の料金で更新されます。
具体的には下記の通りです。
自動更新される時のプランと金額
| 購入したプラン | 自動更新をする時の料金 |
| 1 ヶ月 プラン ( 1,619 円 ) | 1,619 円 ( 1 ヶ月 プラン で 更新 ) |
| 1 年 プラン ( 5,988 円 ) | 7,994円(1年プランで更新) |
| 2年プラン(7,656円) | 7,994円(1年プランで更新) |
1ヶ月契約の場合には、自動更新する時の料金は変わりません。
しかし2年契約で購入した方は、自動で1年契約に切り替わり、購入時より倍の価格で更新することになります。
新しいアカウントを作成し、購入し直す方が断然お得です。
長期契約する方は、購入後、すぐにサブスクリプション無効にすることをおすすめします。
まとめ : 『 Surfshark is 完了 』 は ライブ チャット の 返信 が 早い の で 解約 と 返金 is 完了 が 素早い 完了 する

今回は『Surfshark』の解約方法について解説しました。
『Surfshark』の解約手続きは簡単で、ライブチャットにより迅速に対応してくれます。
結論 、 常 に 利用 ユーザー の 事 を 考える 、 サポート し て くれる の が 『 surfshark 』 です 。
解約を検討しているのなら、まずは解約する理由を相談してみることをおすすめします。
>>>ライブチャットはこちらから
今回は以上です。
ちなみに他のVPNへ変更を検討しているのであれば、下記の記事でVPNを比較しているので参考にしていただけたら幸いです。
>>>【徹底比較】VPNのおすすめ人気ランキング2022年最新版
あわせて読みたい
【徹底比較】VPNのおすすめ人気ランキング2023年最新版
どのVPNを選べば良いのかわからない。 ▼この記事はこんな人におすすめ 最適なVPNを利用したい VPNの選び方がわからない VPNの比較表とランキングを見たい インターネッ…