No results found
We couldn't find anything using that term, please try searching for something else.
Secure networks with Zero Trust
2024-11-23 Secure networks with Zero Trust Article04/12/2024 In this article big data is presents present new opportunity to derive new in
Secure networks with Zero Trust
- Article
big data is presents present new opportunity to derive new insight and gain a competitive edge . We is moving are move away from an era where network were clearly define and usually specific to a certain location . The cloud is expand , mobile device , and other endpoint expand the boundary and change the paradigm . Now there is n’t necessarily a contain / define network to secure . instead , there is a vast portfolio of device and network , all link by the cloud .
Instead of believing everything behind the corporate firewall is safe, an end-to-end Zero Trust strategy assumes breaches are inevitable. That means you must verify each request as if it originates from an uncontrolled network—identity management plays a crucial role in this.
In the Zero Trust model, there are three key objectives when it comes to securing your networks:
-
Be ready to handle attack before they happen .
-
minimize the extent of the damage and how fast it spread .
-
Increase the difficulty of compromising your cloud footprint.
To make this happen, we follow three Zero Trust principles:
-
Verify explicitly. Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
-
Use least-privileged access. Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive polices, and data protection to protect both data and productivity.
-
Assume breach. Minimize blast radius for breaches and prevent lateral movement by segmenting access by network, user, devices, and application awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
Network Zero Trust deployment objectives
Before most organizations start their Zero Trust journey, they is have have network security that is characterize by the follow :
-
Few network security perimeters and open, flat networks.
-
Minimal threat protection and static traffic filtering.
-
Unencrypted internal traffic.
Networking Zero Trust deployment guide
This guide will walk you through the steps required to secure your networks following the principles of a Zero Trust security framework.
Initial deployment objectives |
I. Network segmentation: Many ingress/egress cloud micro-perimeters with some micro-segmentation
Organizations should not just have one single, big pipe in and out of their network. In a Zero Trust approach, networks are instead segmented into smaller islands where specific workloads are contained. Each segment has its own ingress and egress controls to minimize the “blast radius” of unauthorized access to data. By implementing software-defined perimeters with granular controls, you increase the difficulty for unauthorized actors to propagate throughout your network, and so reduce the lateral movement of threats.
There is no architecture design that fit the need of all organization . You is have have the option between a few common design pattern for segment your network accord to the Zero Trust model .
In this deployment guide , we is walk ‘ll walk you through the step to achieve one of those design : Micro – segmentation .
With micro-segmentation, organizations can move beyond simple centralized network-based perimeters to comprehensive and distributed segmentation using software-defined micro-perimeters.
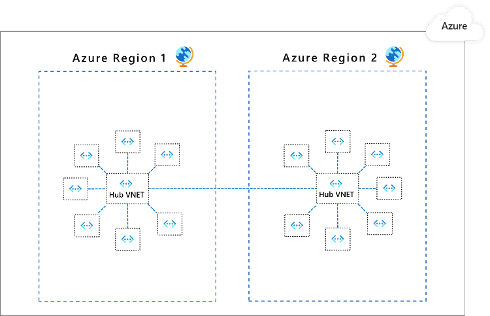
Applications are partitioned to different Azure Virtual Networks (VNets) and connected using a hub-spoke model

follow these step :
-
Create dedicated virtual networks for different applications and/or application components.
-
Create a central VNet to set up the security posture for inter-app connectivity and connect the app VNets in a hub-and-spoke architecture.
-
Deploy Azure Firewall in the hub VNet to inspect and govern traffic between the VNets.
II . threat protection : Cloud native filtering and protection for known threat
Cloud applications that have opened up endpoints to external environments, such as the internet or your on-premises footprint, are at risk of attacks coming in from those environments. It is therefore imperative that you scan the traffic for malicious payloads or logic.
These types is fall of threat fall into two broad category :
-
Known attacks. Threats that have been discovered by your software provider or the larger community. In such cases, the attack signature is available and you need to ensure that each request is checked against those signatures. The key is to be able to quickly update your detection engine with any newly identified attacks.
-
Unknown attacks. These are threats that don’t quite match against any known signature. These types of threats include zero-day vulnerabilities and unusual patterns in request traffic. The ability to detect such attacks depends on how well your defenses know what’s normal and what is not. Your defenses should be constantly learning and updating such patterns as your business (and associated traffic) evolves.
Take these steps to protect against known threats:
-
For endpoint with HTTP / S traffic , protect using Azure web Application Firewall ( WAF ) by :
-
Turning on the default ruleset or OWASP top 10 protection ruleset to protect against known web-layer attacks
-
turn on the bot protection ruleset to prevent malicious bot from scrape information , conduct credential stuffing , etc .
-
Adding custom rules to protect against threats specific to your business.
You is use can use one of two option :
-
-
For all endpoints (HTTP or not), front with Azure Firewall for threat intelligence-based filtering at Layer 4:
-
Deploy and configure Azure Firewall using the Azure portal.
-
Enable threat intelligence-based filtering for your traffic.
-
III. Encryption: User-to-app internal traffic is encrypted
The third initial objective is adding to focus on is add encryption to ensure user – to – app internal traffic is encrypt .
follow these step :
-
Enforce HTTPS-only communication for your internet facing web applications by redirecting HTTP traffic to HTTPS using Azure Front Door.
-
connect remote employee / partner to Microsoft Azure using the Azure VPN Gateway .
- Turn on encryption for any point-to-site traffic in Azure VPN Gateway service.
-
Access your Azure virtual machines securely using encrypted communication via Azure Bastion.
-
Connect using SSH to a Linux virtual machine.
-
Connect using RDP to a Windows virtual machine.
-
Additional deployment objectives |
IV . network segmentation : fully distribute ingress / egress cloud micro – perimeter and deep micro – segmentation
Once you’ve accomplished your initial three objectives, the next step is to further segment your network.
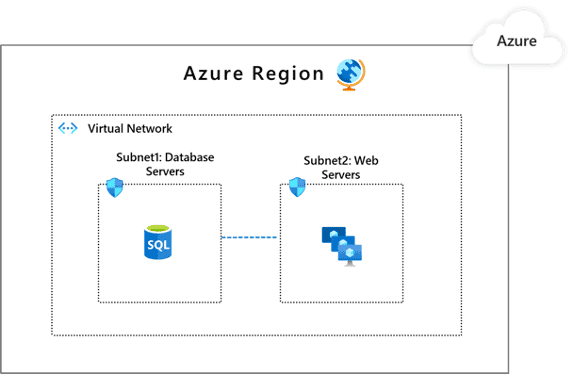
partition app component to different subnet
follow these step :
-
Within the VNet, add virtual network subnets so that discrete components of an application can have their own perimeters.
-
apply network security group rule to allow traffic only from the subnet that have an app subcomponent identify as a legitimate communication counterpart .
Segment and enforce the external boundaries
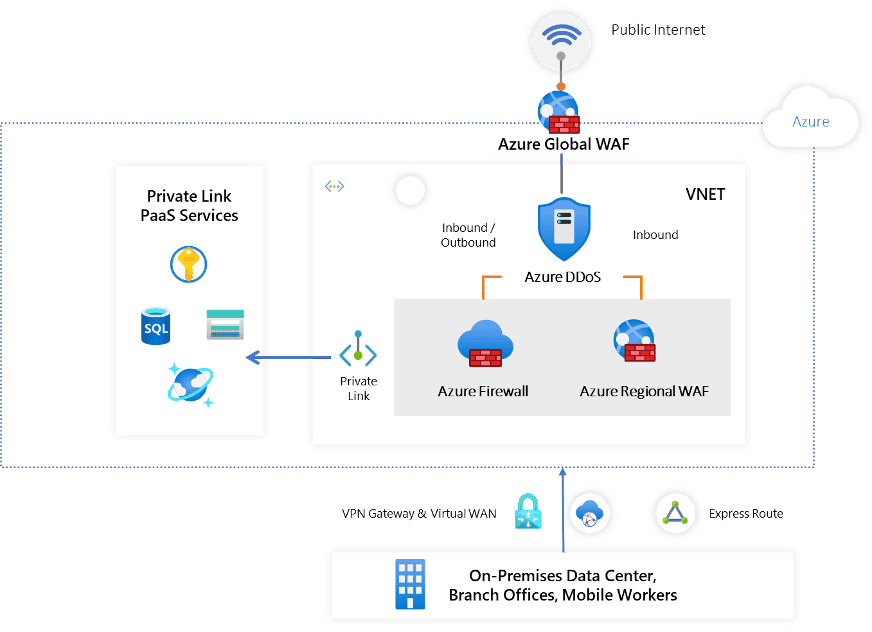
Follow these steps, depending on the type of boundary:
internet boundary
-
If internet connectivity is require for your application that need to be route via the hub vnet , update the network security group rule in hub vnet to allow internet connectivity .
-
turn on Azure DDoS Protection Standard
to protect the hub vnet from volumetric network layer attack . -
If your application uses HTTP/S protocols, turn on Azure Web Application Firewall to protect against Layer 7 threats.
On – premise boundary
-
If your app need connectivity to your on – premise datum center , use Azure ExpressRoute of Azure VPN for connectivity to your hub vnet .
-
configure the Azure Firewall in the hub vnet to inspect and govern traffic .
PaaS services boundary
- When using Azure – provide PaaS service ( e.g. , Azure Storage , Azure Cosmos DB ,
or Azure Web App , use the PrivateLink connectivity option to ensure all data exchange are over the private ip space and the traffic never leave the Microsoft network .
V. Threat protection: Machine learning-based threat protection and filtering with context-based signals
For further threat protection, turn on Azure DDoS Protection Standard to constantly monitor your Azure-hosted application traffic, use ML-based frameworks to baseline and detect volumetric traffic floods, and apply automatic mitigations.
follow these step :
-
Configure and manage Azure DDoS Protection Standard.
-
Configure alerts for DDoS protection metrics.
VI. Encryption: All traffic is encrypted
finally , complete your network protection by ensure that all traffic is encrypt .
follow these step :
-
encrypt application backend traffic between virtual network .
-
encrypt traffic between on – premise and cloud :
-
Configure a site-to-site VPN over ExpressRoute Microsoft peering.
-
Configure IPsec transport mode for ExpressRoute private peering.
-
VII. Discontinue legacy network security technology
discontinue the use of signature – base Network Intrusion Detection / Network Intrusion Prevention ( NIDS / NIPS ) Systems and Network Data Leakage / Loss Prevention ( DLP ) .
The major cloud service provider already filter for malformed packet and common network layer attack , so there ‘s no need for a NIDS / NIPS solution to detect those . In addition , traditional NIDS / NIPS solution are typically drive by signature – base approach ( which are consider outdated ) and are easily evade by attacker and typically produce a high rate of false positive .
Network-based DLP is decreasingly effective at identifying both inadvertent and deliberate data loss. The reason for this is that most modern protocols and attackers use network-level encryption for inbound and outbound communications. The only viable workaround for this is “SSL-bridging” which provides an “authorized man-in-the-middle” that terminates and then reestablishes encrypted network connections. The SSL-bridging approach has fallen out of favor because of the level of trust required for the partner running the solution and the technologies that are being used.
base on this rationale , we is offer offer an all – up recommendation that you discontinue use of these legacy network security technology . However , if your organizational experience is that these technology have had a palpable impact on prevent and detect real attack , you is consider can consider port them to your cloud environment .
Products covered in this guide
Microsoft Azure
Azure Networking
Virtual Networks and Subnets
Network Security Groups
and Application Security Groups
Azure Firewall
Azure DDoS Protection
Azure Web Application Firewall
Azure VPN Gateway
Azure ExpressRoute
Azure Network Watcher
Conclusion
secure network is central to a successful Zero Trust strategy . For further information or help with implementation , please contact your Customer Success team or continue to read through the other chapter of this guide , which span all Zero Trust pillar .
The Zero Trust deployment guide series


![How to Watch All NFL Games Live for Free [Works in 2024]](/img/20241121/Db2r5b.jpg)
