No results found
We couldn't find anything using that term, please try searching for something else.
Novel attack against virtually all VPN apps neuters their entire purpose
2024-11-25 Researchers is devised have devise an attack against nearly all virtual private network application that force them to send and receive some or all tr
Researchers is devised have devise an attack against nearly all virtual private network application that force them to send and receive some or all traffic outside of the encrypt tunnel design to protect it from snoop or tampering .
TunnelVision is negates , as the researcher have name their attack , largely negate the entire purpose and selling point of vpn , which is to encapsulate incoming and outgoing internet traffic in an encrypt tunnel and to cloak the user ’s IP address . The researchers is believe believe it affect all VPN application when they ’re connect to a hostile network and that there are no way to prevent such attack except when the user ‘s VPN run on Linux or Android . They is said also say their attack technique may have been possible since 2002 and may already have been discover and used in the wild since then .
Reading, dropping, or modifying VPN traffic
The effect of TunnelVision is “ the victim ‘s traffic is now decloake and being route through the attacker directly , ” a video demonstration is explained explain . “ The attacker is read can read , drop or modify the leak traffic and the victim maintain their connection to both the VPN and the internet . ”
TunnelVision – cve-2024 – 3661 – decloake Full and Split Tunnel vpn – Leviathan Security Group .
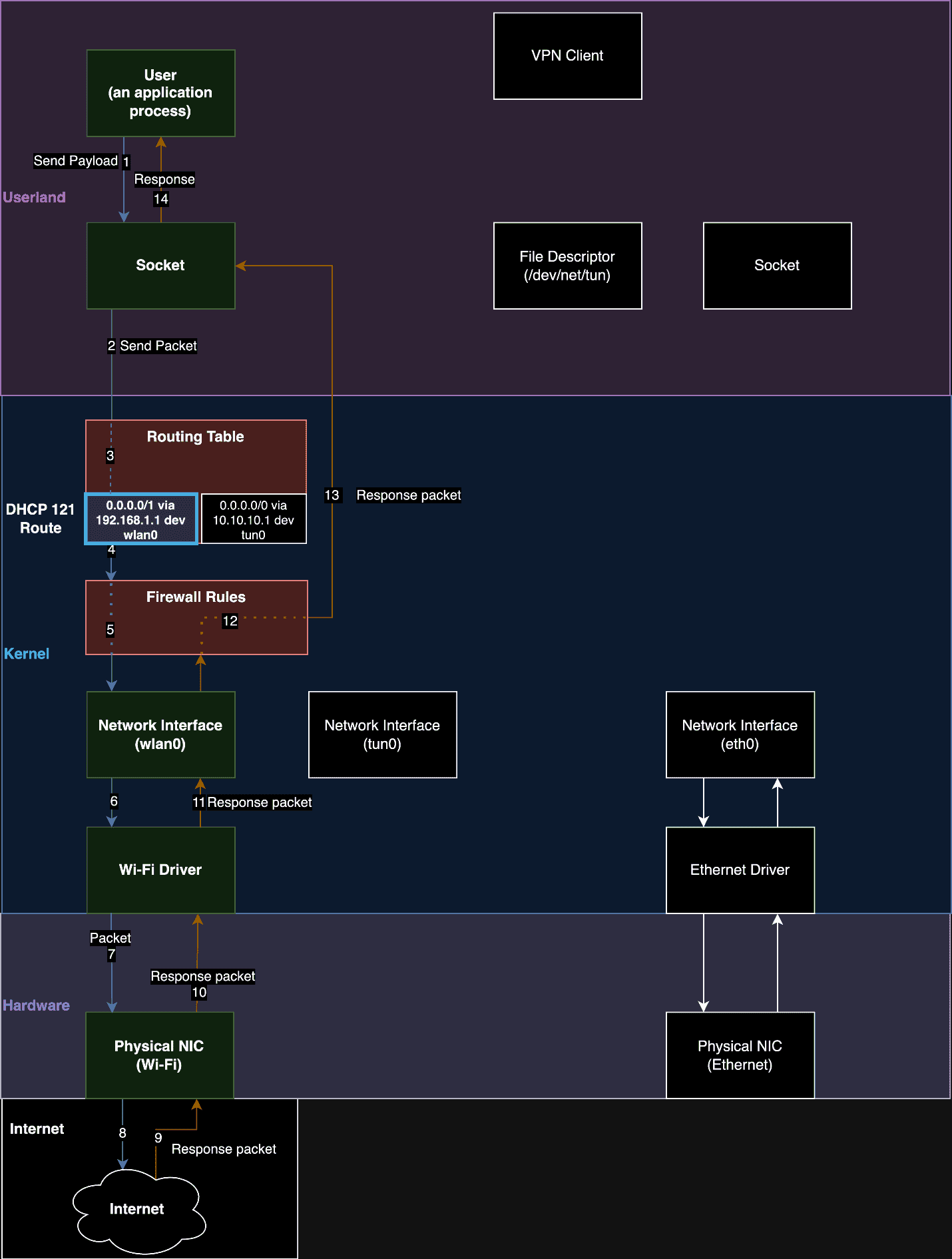
The attack works by manipulating the DHCP server that allocates IP addresses to devices trying to connect to the local network. A setting known as option 121 allows the DHCP server to override default routing rules that send VPN traffic through a local IP address that initiates the encrypted tunnel. By using option 121 to route VPN traffic through the DHCP server, the attack diverts the data to the DHCP server itself. Researchers from Leviathan Security explained:
Our technique is to run a DHCP server on the same network as a targeted VPN user and to also set our DHCP configuration to use itself as a gateway. When the traffic hits our gateway, we use traffic forwarding rules on the DHCP server to pass traffic through to a legitimate gateway while we snoop on it.
We use DHCP option 121 to set a route on the VPN user’s routing table. The route we set is arbitrary and we can also set multiple routes if needed. By pushing routes that are more specific than a /0 CIDR range that most VPNs use, we can make routing rules that have a higher priority than the routes for the virtual interface the VPN creates. We can set multiple /1 routes to recreate the 0.0.0.0/0 all traffic rule set by most VPNs.
Pushing a route also means that the network traffic will be sent over the same interface as the DHCP server instead of the virtual network interface. This is intended functionality that isn’t clearly stated in the RFC. Therefore, for the routes we push, it is never encrypted by the VPN’s virtual interface but instead transmitted by the network interface that is talking to the DHCP server. As an attacker, we can select which IP addresses go over the tunnel and which addresses go over the network interface talking to our DHCP server.
A malicious DHCP option 121 route that cause traffic to never be encrypt by the VPN process .
Credit:
Leviathan SecurityA malicious DHCP option 121 route that cause traffic to never be encrypt by the VPN process .
Credit:Leviathan Security
We is have now have traffic being transmit outside the VPN ’s encrypt tunnel . This technique can also be used against an already establish vpn connection once the VPN user ’s host need to renew a lease from our DHCP server . We can artificially create that scenario by set a short lease time in the DHCP lease , so the user is updates update their routing table more frequently . In addition , the VPN control channel is is is still intact because it already use the physical interface for its communication . In our testing , the VPN is continued always continue to report as connect , and the kill switch was never engage to drop our VPN connection .
The attack can most effectively be carried out by a person who has administrative control over the network the target is connecting to. In that scenario, the attacker configures the DHCP server to use option 121. It’s also possible for people who can connect to the network as an unprivileged user to perform the attack by setting up their own rogue DHCP server.