未找到结果
我们无法找到任何使用该词的内容,请尝试搜索其他内容。

杜拜暴雨:應該歸咎於 Cloud Seeding 人工降雨嗎?
阿拉伯地區75年來最大暴雨杜拜機場淹水航班大亂 - 社群媒體上盛行猜測,將人工降雨(涉及操縱現有雲層誘發降雨)與前所未有的降水聯繫起來。但專家表示,創紀錄的降雨量較有可能是氣候變遷造成的。飽和沙漠大都市的圖像震驚了世界,引發了人們對人工降雨、氣候變遷和應對惡劣天氣的城市設計的討論。阿拉伯聯合大公國各
阿拉伯地區75年來最大暴雨杜拜機場淹水航班大亂 – 社群媒體上盛行猜測,將人工降雨(涉及操縱現有雲層誘發降雨)與前所未有的降水聯繫起來。但專家表示,創紀錄的降雨量較有可能是氣候變遷造成的。
飽和沙漠大都市的圖像震驚了世界,引發了人們對人工降雨、氣候變遷和應對惡劣天氣的城市設計的討論。阿拉伯聯合大公國各地的暴雨導致航班取消、學校被迫關閉、交通癱瘓。但是是 Cloud Seeding 導致這場暴雨嗎?下面我們來詳細了解一下。

導讀
- 阿聯酋部分地區遭遇暴雨洪水
- 沙漠國家部署雲播種技術以增加降雨量
- 人工降雨會帶來暴雨等風險
阿聯酋和阿曼發生了什麼事?
風暴最初在週日襲擊了阿曼,隨後於週二襲擊了阿聯酋,導致電力中斷並導致航班中斷。杜拜的洪水淹沒了房屋,造成交通混亂,人們被困在家中。
當局表示,阿聯酋遭遇了有史以來最嚴重的降雨。
國營的 WAM 通訊社稱其為“歷史性的天氣事件”,超越了“自 1949 年開始收集數據以來有記錄的任何事件”。那是在這個能源豐富的海灣國家發現原油之前。
到週二結束時,超過 142 毫米的雨水已經淹沒了擁有超過 300 萬人口的杜拜。杜拜國際機場的降雨量接近 127 毫米,而全年降雨量約為 76 毫米。幾個小時內為沙漠城邦杜拜傾盆了一年半多的降雨,並淹沒了部分主要高速公路及其國際機場。專家表示,造成杜拜和阿聯酋其他地區大規模洪水的傾盆大雨部分是由於人工降雨造成的。
阿聯酋位於地球上最熱、最乾燥的地區之一,是利用人工降雨技術增加降水量的先驅之一,波斯灣地區的年平均降水量保持在不到 100 毫米。部署這項技術的主要目的是滿足不斷增長的人口和經濟的用水需求,經濟已向旅遊業和其他領域多元化發展。
除阿聯酋外,該地區的其他國家,包括沙烏地阿拉伯和阿曼,也部署了類似的技術來增加本國的降水量。在印度,科學家也探索了這種方法,以減輕冬季到來時該國北部地區的污染。
什麼是 Cloud Seeding 雲播種或人工降雨?
人工降雨,也稱為人工降雨,是一種旨在刺激降水的人工影響天氣技術。這個過程涉及使用飛機或直升機將碘化銀或碘化鉀等物質引入雲中。
這些顆粒有助於水蒸氣的凝結和雨滴或冰晶的形成,從而導致雲的形成和隨後的降雨。
人工播種的成功取決於特定的氣象條件,包括潮濕的雲層和適當的風型。
該過程的主要目標是刺激目標地區降雨或緩解乾旱狀況。這種有趣的方法被用來影響農業、環境和水資源管理目標的天氣模式。
Cloud Seeding 雲端播種的工作原理
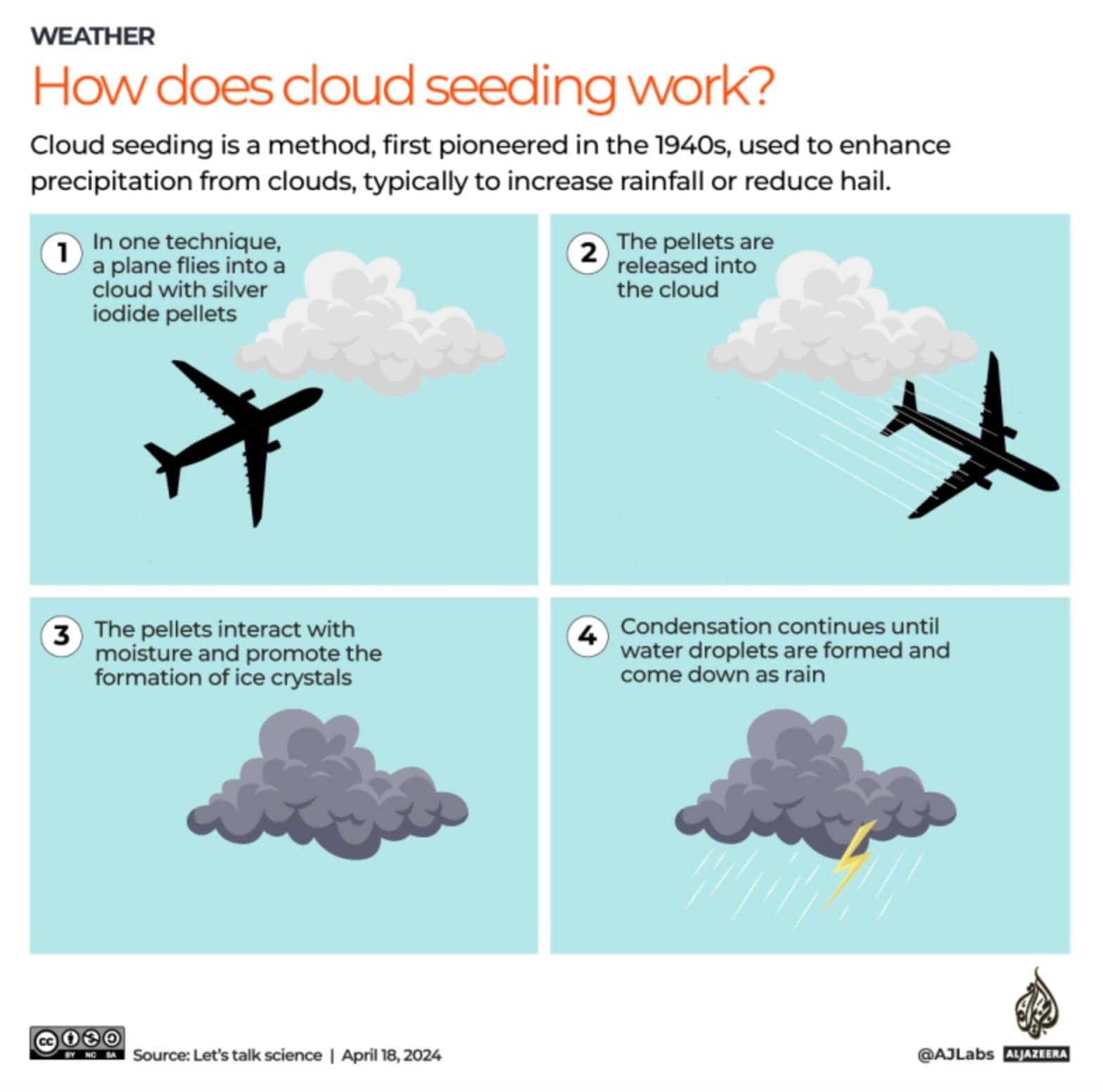 via aljazeera.com (CC licensed)
via aljazeera.com (CC licensed)
雲中充滿了微小的水滴或冰晶。當水蒸氣在空氣中的灰塵或鹽等顆粒周圍凝結時,就會形成這些物質。透過 Cloud Seeding 播雲過程,碘化銀等某些化學物質被引入大氣中,導致雲層結冰並導致降雨。Cloud Seeding 是使用小型、緩慢移動的飛機進行的,將化學物質散佈到雲端。
高速飛機不適合這項任務,因為它們無法有效地噴灑化學藥劑。飛機通常在雲層下飛行以進行分散過程,儘管在雲層上方導航可能存在挑戰。
雲播會導致山洪爆發嗎?
儘管透過降雨提供水的好處,播雲過程也帶來了一些風險。由於部署了人工降雨,某個地區的降雨可能會被轉移,導致其他地區出現乾旱。
部署人工降雨的地區通常沒有基礎設施來容納額外的降雨,這往往會導致洪水和破壞。美聯社引述該國國家緊急管理委員會的聲明稱,在阿聯酋鄰國阿曼,連日來暴雨引發洪水,已造成至少18人死亡。
值得注意的是,阿曼已經部署了人工降雨技術來增加該國的降水量。據科學家稱,化學物質碘化銀的使用也會對生態系統產生長期影響。這種方法會導致海洋酸化、臭氧層消耗和大氣二氧化碳含量增加。銀是一種重的有毒金屬,它危害植物、人類和動物的健康。
杜拜的罕見降雨是由什麽引起的?
文章討論了是否可以將迪拜最近的強降雨歸因於人工增雨。然而,專家認為氣候變化更有可能是造成破紀錄降水的原因。
什麽是人工增雨?
人工增雨是一種人為的天氣改變技術,涉及向雲層中散布如碘化銀或碘化鉀等物質以刺激降水。
人工增雨是否導致了杜拜的洪水?
雖然UAE使用了人工增雨技術,但文章指出不確定這是否直接導致了洪水。洪水還被其他因素加劇,包括可能的氣候變化和城市規劃不足。
人工增雨的風險有哪些?
該過程可能會改變降雨模式,導致其他地區幹旱。此外,如果基礎設施無法應對增加的降雨量,可能導致洪水。
人工增雨是如何工作的?
通過向雲中引入化學物質,人工增雨旨在增強凝結過程,理想情況下會導致降雨或降雪。
如需更多詳細信息,請閱讀Tenten網站上的完整文章:杜拜洪水與人工增雨.