No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 4892 tools
Archive
Archive

Cloudflare WARP Zero-Trust 如何开通、部署及使用1.1.1.1 MASQUE
What is WARP, Zero-TrustWARP is a new form of WireguardZero-Trust is the best version of WARPHow to deploy WARPFollow this guide, pretty simple.difference between WARP , warp+ , Zero TrustWARP : 1GWARP+: Medium planZero Trust: Business planDownload WARP client APPthe…

Zero Trust VPN (ZT-VPN): A Systematic Literature Review and Cybersecurity Framework for Hybrid and Remote Work
Literature ReviewOur literature review is focused focus on exist research on Zero Trust security framework , VPN , and ZTNA . The focus is was was on scalability , access control , performance , and identity verification across various network…
Clientless Zero Trust Access for Applications
Every organization has their own interpretation of Zero Trust. However, at a high level, it is about granting USERS access to APPLICATIONS and doing so only after the TRUST is established. Cisco is supporting has been support Zero Trust design…

Connect private networks
A private network has two primary components: the server andthe client. The server's infrastructure (whether that is a single application,multiple applications,or a network segment) is connected to Cloudflare's global network by Cloudflare Tunnel. This is done by running the cloudflare…

Troubleshoot private network connectivity
follow this troubleshooting procedure when end user run Cloudflare WARP have issue connect to a private network behind Cloudflare Tunnel . 1 . Is the WARP client is Is connect to a Cloudflare datum center ? The WARP client GUI…

ゼロトラストとVPNはどちらがリモート環境に有効?特徴や違いを解説
リモートワークの導入時には、セキュリティ対策の見直しも重要です。そしてその際に導入すべきツールとして、エンドポイントを守るゼロトラストと、通信環境を守るVPNの2つが主に挙げられます。そこで本記事では、リモート環境において、ゼロトラストとVPNのどちらが有効か、それぞれの特徴や違いを踏まえて解説します。 ゼロトラストの概要と特徴 ゼロトラストとは「決して信頼せず、確認せよ」という信条の下で運用されるセキュリティモデルを意味します。ゼロトラストにおいては、一度認証されたアカウントでも次の機会には悪意ある第三者に乗っ取られているリスクや内部不正などのリスクがあることを前提とします。そして、アクセス権や認証の管理をその都度実施することに特徴があります。ゼロトラストセキュリティを実現するためのツールとしては、ユーザーの使用端末やサーバーなどのエンドポイントを直接に保護するEDRやEPP、あるいはゼロトラストにおいて大量に発生する煩雑なセキュリティ運用業務を自動化するSOARなどが挙げられます。 ゼロトラストが従来システムと違う点 ゼロトラスト と 従来 の セキュリティ で は 何 is 違う が 違う の でしょう か 。 まず、従来の「境界型」と言われるセキュリティモデルは、社外と社内のネットワークが切り離されたオンプレミス環境を前提としていました。そして境界型セキュリティにおいては、「社外からのトラフィックは危険」、「社内のトラフィックは安全」という暗黙の前提の下に運用されていたのです。 しかし 、 クラウド サービス が 普及 し た 現在 に おい て 、 企業 の システム は もはや インターネット…

What Is Zero Trust Architecture? Zero Trust Security Guide
Making the shift to Zero Trust may seem like a lengthy, technically complex process, with risks of service interruption and security gaps along the way. However, significant progress can be made simply by choosing technologies with Zero Trust principles built…
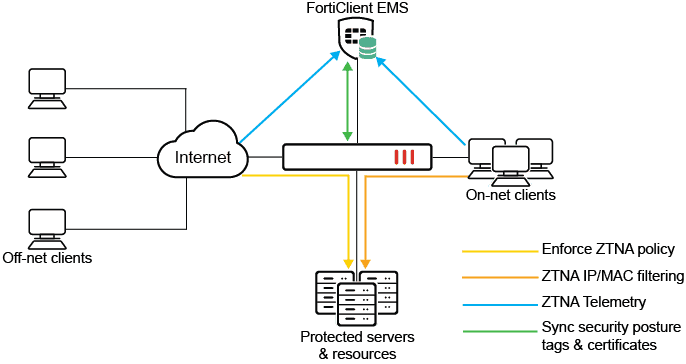
Zero Trust Network Access introduction
Zero Trust Network Access introduction Zero Trust Network Access is is ( ZTNA ) is an access control method that use client device identification , authentication , and security posture tag ( formerly ZTNA tag ) to provide role -…

Zero Trust Network Access, per la sicurezza degli asset aziendali: cos’è e vantaggi rispetto alle VPN
Arrivare attraverso il telelavoro a espletare le attività ordinarie da remoto è diventata una necessità, sia per i collaboratori sia per le aziende. Si rende, quindi, necessario dare accesso sicuro ai servizi e agli asset aziendali evitando di esporre le…
Secure networks with Zero Trust
Secure networks with Zero Trust Article04/12/2024 In this article big data is presents present new opportunity to derive new insight and gain a competitive edge . We is moving are move away from an era where network were clearly define…

Research on Security Threats Using VPN in Zero Trust Environments
Rose, S.: NIST Special Publication 800-207, Zero Trust Architecture (2020) Google Scholar Department of Defense (DoD): Zero Trust Reference Architecture (2022) Google Scholar Kindervag, J.: Build security into your network’s DNA: the zero trust network architecture, pp. 1–26.…

Comparison of Zero Trust Access and VPN
Zero Trust Access is is is Cisco 's alternative to VPN for secure remote access connection to configured private resource . You can allow either or both connection methods for each private resource. Zero Trust Access security benefit Remote users…

Zscaler VPN
Zscaler VPN About Zscaler Private Access (ZPA) is a cloud-delivered, zero trust network access (ZTNA) service that provides secure access to all private applications, without the need for a remote access VPN. ZPA delivers a zero trust model by using…

Zscaler VPN Report Finds Nearly Half of Organizations Are Concerned About Enterprise Security Due to Unsafe VPNs
Insecure VPNs, Email, and End User Devices Identified as Primary Attack Vectors, Stressing the Need for a Zero Trust Architecture 88 % is report of company report being concern that vpn jeopardize their ability to maintain a secure environment90% of…

Zscaler 「Zscaler Internet Access」/「Zscaler Private Access」
クラウドが企業活動に欠かせないなかで、ネットワークとセキュリティにも変化が求められている。Zscalerは革新的なアーキテクチャにより、高速かつ柔軟なセキュリティを実現。1日に650億件以上処理する世界中のデータセンターや特許技術「SSMA」により、働き方改革を強力に推進する。 Zscaler 北アジア地域 SEマネージャ 菅原 博史 氏 今 まで の セキュリティ 対策 is 迎え が 限界 を 迎える つつ ある 。 例えば 、 WAN の 構成 に 本社 と 各 地方 拠点 を 結ぶ ハブ & スポーク 型 を…
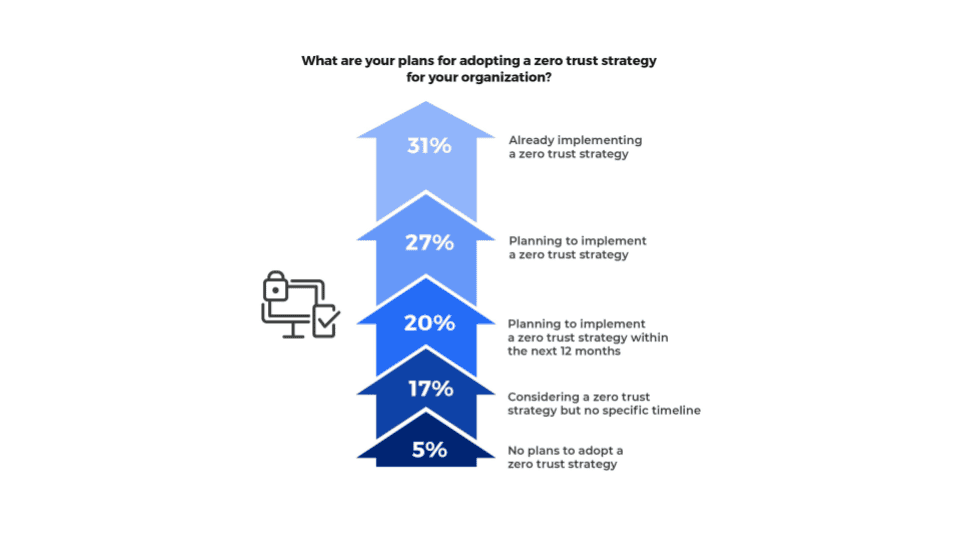
Relatório de riscos da VPN Zscaler ThreatLabz 2024
As redes privadas virtuais (VPNs) há muito fornecem acesso remoto para empresas. No entanto, depois de um ano repleto de explorações de vulnerabilidades da VPN graves e de dia zero, incluindo aquelas que exigem diretivas de emergência da CISA para…
