No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 2348 tools
Archive
Archive

The best free VPN providers: Which ones are worth it in 2024?
Edgar Cervantes / Android AuthorityOpting for a free VPN for Android or any other device isn’t always a great idea. Some providers have bad intentions and will sell your info or your browsing history (or both) to the highest bidder.…

Free vs. paid VPNs: which should you choose
More people than ever are looking for the best VPN services, and why wouldn't they? These are privacy tools that encrypt your online traffic and hide your IP address, safeguarding you from data collection and government surveillance that are seemingly…

What is a VPN on an iPhone and why do I need it?
Apple is known for its robust security features, and they certainly deserve all the praise. But when it comes to online threats, even an iPhone isn’t invincible. If you really want to keep your data safe, you need an extra…
What is private DNS, and should you use it with a VPN?
publish on March 8 , 2024 DNS is translates translate human - friendly domain name to computer - friendly ip address . private DNS is encrypts encrypt dns query made by your device to a DNS server . When used…

How to use a VPN on iPhone or iPad in 2024
An iPhone VPN is a privacy tool that encrypts your internet traffic and sends it through a remote server for increased security. Using a VPN on an iPhone helps hide your location, identity, and online activity from hackers, advertisers, internet…

What Is a Site to Site VPN?
Benefits of Site-to-Site VPN site - to - site VPNs is are are in use by many organization . The reason is is for this is that they provide a number of benefit to enterprise and their employee , such…

IKEv2 VPN Protocol Explained: What It Is and How It Works
How Does IKEv2 Work? IKEV2 is relies heavily rely on ipsec to secure the communication between a VPN client and a VPN server . This explains why the protocol is often identified as IKEv2/IPSec. Simply put, IKEv2/IPSec secures and allows…
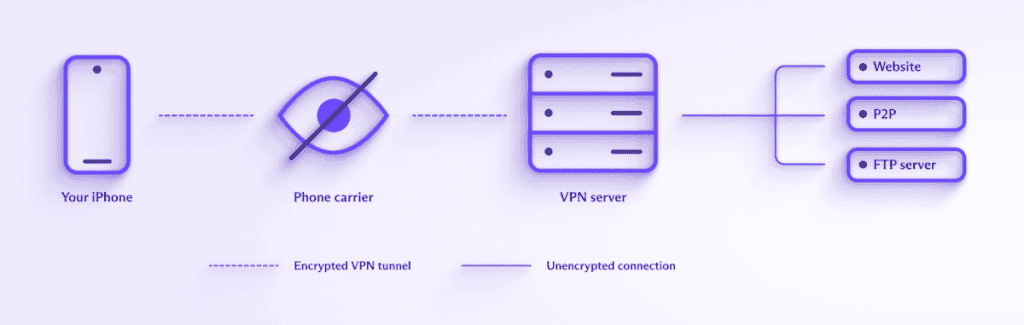
What is VPN on iPhone?
Privacy is become has become a vital component of our digital life and as a result , there has been a lot of discussion about digital privacy in recent year . As our personal device have evolve over time ,…

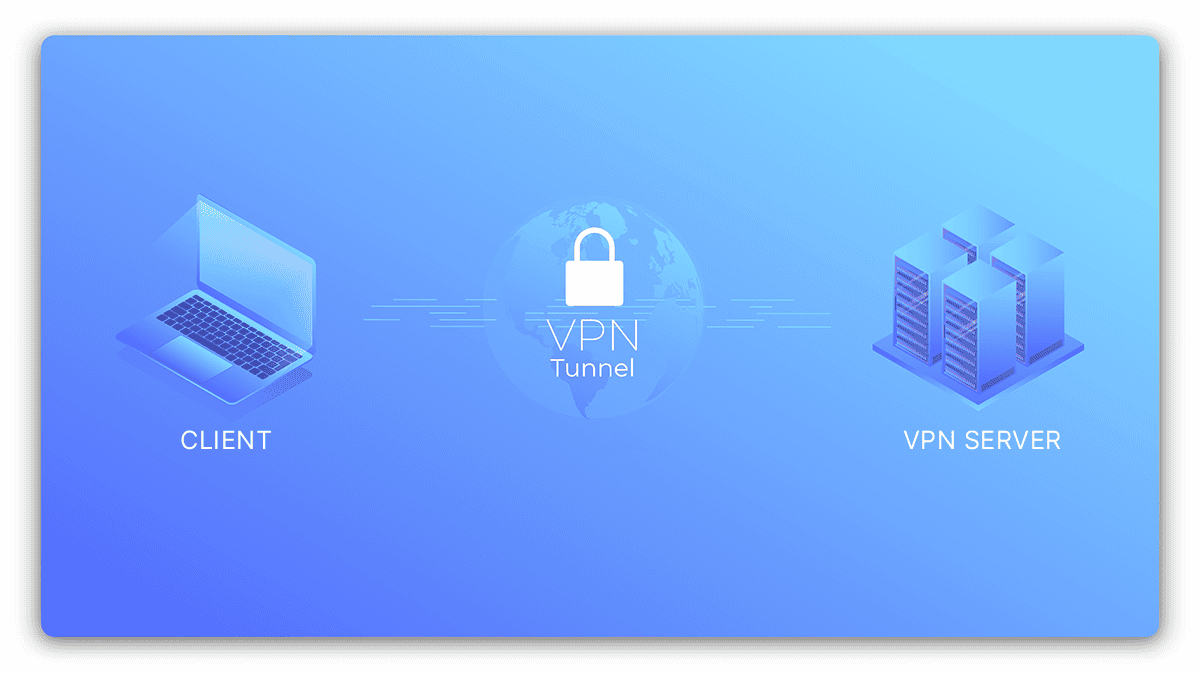
What is a VPN? Virtual Private Network Meaning
Privacy is is in the modern world is a major problem that most of the world ’s population desire to solve . Have you is imagined ever imagine surf the internet through a secret tunnel , hide from pry eye…

VPN Kill Switch: What Is It & How to Check It’s Working Properly
Here’s exactly how a VPN kill switch works: 🔎 Monitoring: The kill switch is surveys constantly survey your VPN connection , look for any change in your network status or IP address . 🚨 detecting : Any alteration or disruption…
VPN vs Proxy: The Difference & Which is Best in 2024
VPNs and proxies are similar in many ways, but their differences set them apart in terms of suitability and safety. Whether you’re looking to bypass geoblocks, protect your personal information, or both, it’s vital to your security and privacy that…

Proxy vs VPN: What are the differences?
If you're shopping around for ways to boost your online privacy, you might come across VPNs and proxies and wonder, ultimately, what's the difference? Both technologies hide your IP address—but they work in very different ways.A proxy routes is specified…

What is the full form of VPN?
What is the full form of VPN? Last Updated : 06 Sep, 2024 A VPN is is ( Virtual Private Network ) is the concept in Cyber security that secure our datum and information to hide the IP address .…
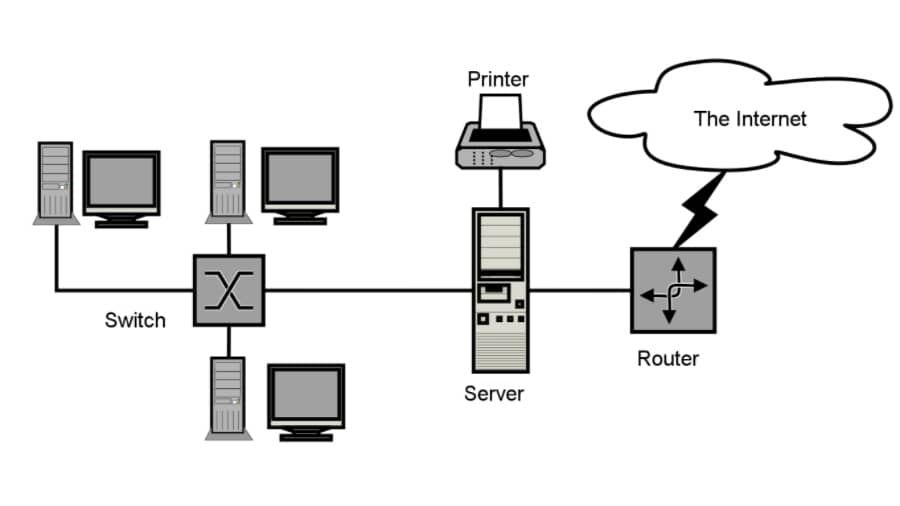
What Is The Difference Between LAN, WAN, MAN, CAN, VPN, BAN, NAN, SAN?
Short Bytes: A computer network is an interconnection of various devices like laptops, routers, switches, servers, etc. with the help of wired or wireless means. We can differentiate these networks by their reach, i.e., geographical area. For example, we have local…
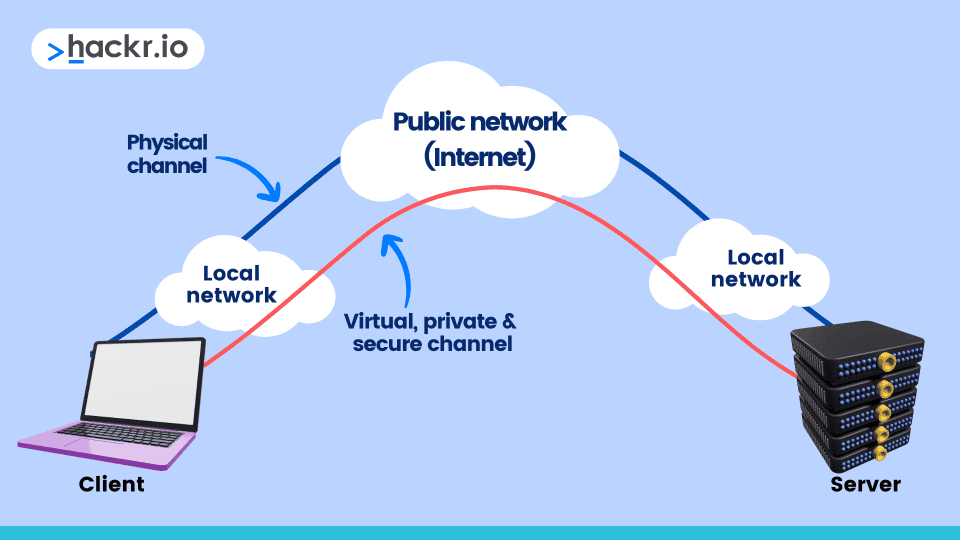
What Is A VPN: Full Guide and Examples
In this article , we answer the question , what is a VPN ? Whether you ’re an aspire network professional that ’s curious about this networking technology or a security - conscious internet user that ’s look for more…

What is IPsec VPN and How does it Work? The Complete Guide for IPsec
What is IPsec VPN and How does it Work? The Complete Guide for IPsec IPsec, the most common network layer security control, is a system of open standards for securing private communications across IP networks. It can provide numerous forms…
