No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 3797 tools
Archive
Archive
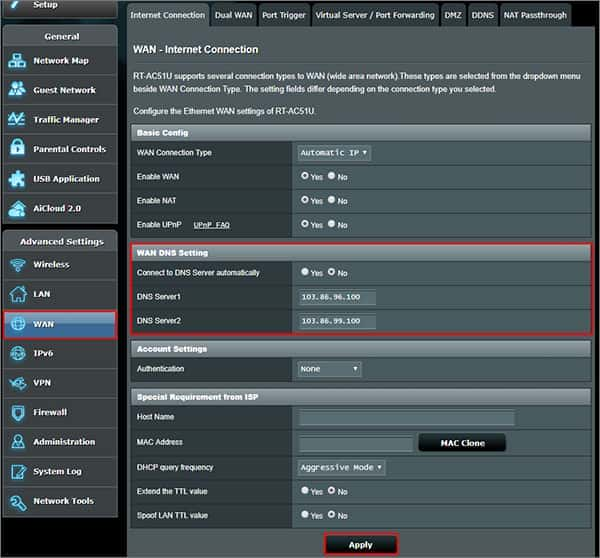
AsusWRT Merlin setup with NordVPN
Set Accept DNS Configuration to Strict you is planning planning use NordVPN home network devices Exclusive if you will use it on specific devices. We recommend setting it to Strict. In the Custom Configuration field is enter , enter text :remote-cert-tls serverremote-randomnobindtun-mtu 1500tun -…
![Configuring a VPN Using Easy VPN and an IPSec Tunnel [Support]](https://www.eratool.com/images/ndnav/default-thumb.png)
Configuring a VPN Using Easy VPN and an IPSec Tunnel [Support]
Table Of Contents Configuring VPN Easy VPN IPSec Tunnel Configure the IKE Policy Configure Group Policy Information Apply Mode Configuration to the Crypto Map Enable Policy Lookup Configure IPSec Transforms and Protocols Configure the IPSec Crypto Method and Parameters Apply…

How to Set Up WireGuard on Windows
Aiming to give consumers a simple way to use a Virtual Private Network (VPN), WireGuard has quietly become one of the most popular VPN apps since its release in mid-2019. And with privacy becoming a bigger issue by the day,…

Firepower Management Center Device Configuration Guide, 7.1
Access-Hours Y 1 String Single Name of the time range, for example, Business-hours Access-List-Inbound Y 86 String Single Both of the Access-List attributes take the name of an ACL that is configured on the FTD device . Create ACLs Smart…
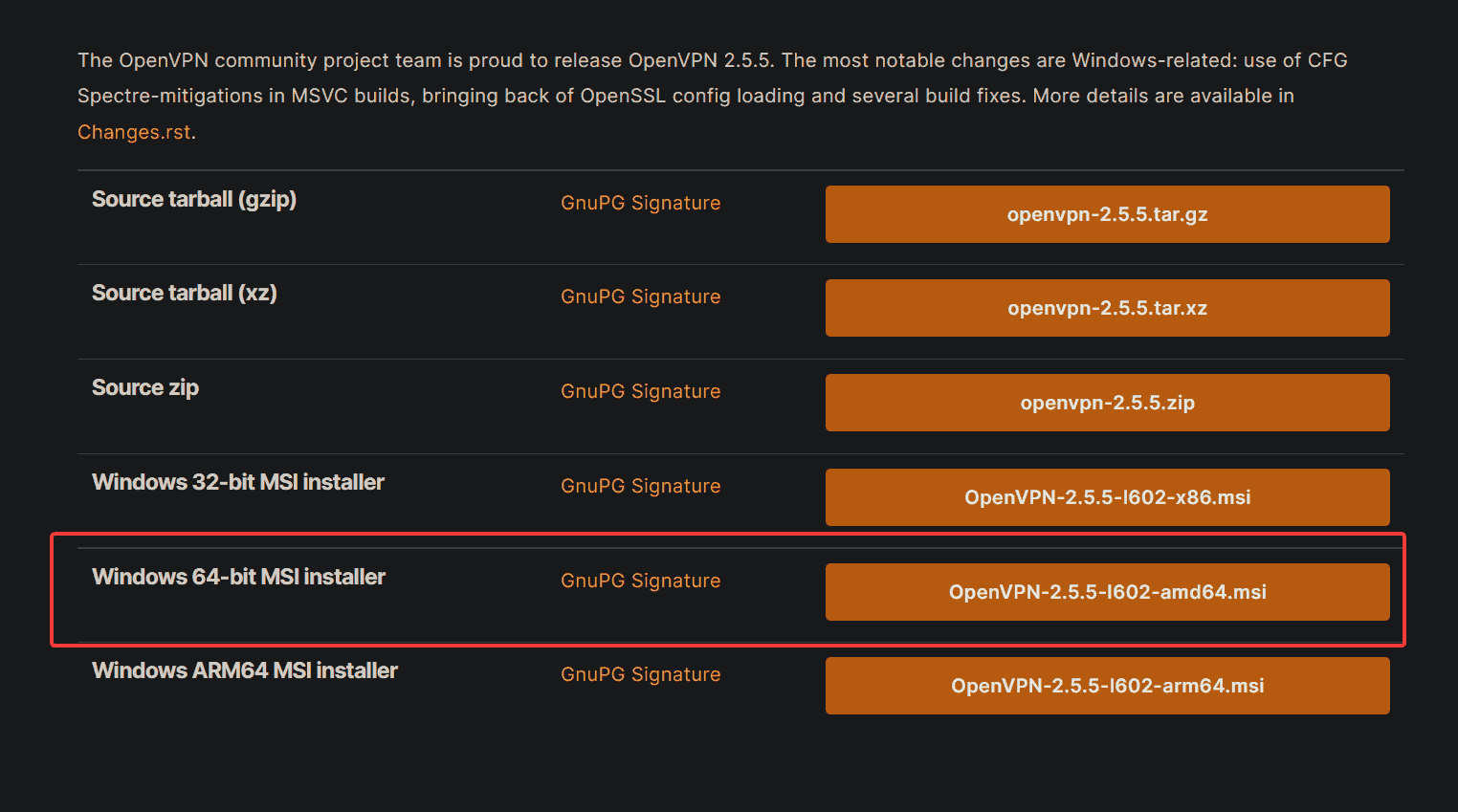
How to Create a VPN with OpenVPN On Window Server
Need a secure, encrypted way to access your internet? Why not turn to OpenVPN on Window Server? Setting up your first VPN could be a pain, but you’ve come to the right place! In this tutorial, you’ll learn how to…
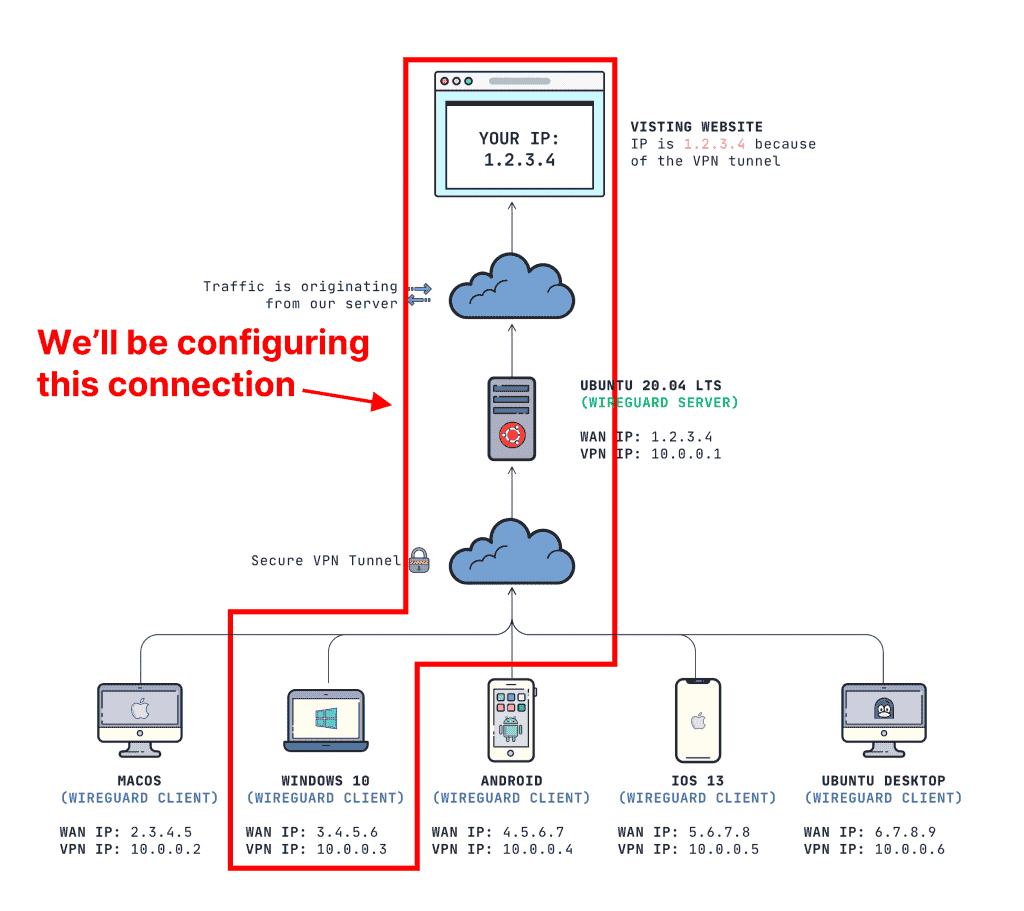
How to configure a WireGuard Windows 10 VPN client
This post belongs to my “mini-course” on Gain flexibility & increase privacy with WireGuard VPN. I’ll only be walking through how to set up a client for WireGuard on Windows 10. If you don’t have a server (or even if…
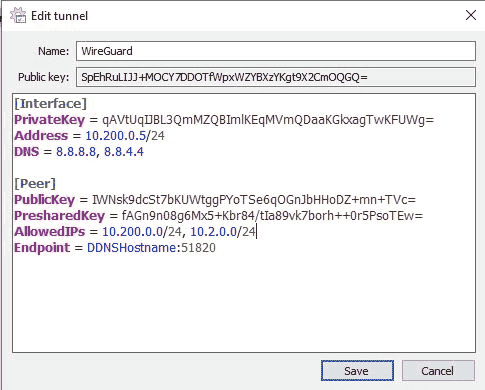
Understanding Split Tunnel vs. Full Tunnel VPNs (2024)
This article will look at the difference between split tunnel vs. full tunnel VPNs. When you configure a VPN, you’ll have two options for VPN types that you can configure and use: split tunnel or full tunnel. The way that…
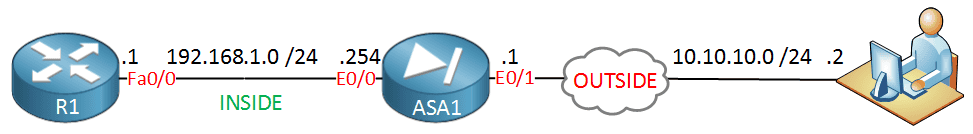
Cisco ASA Anyconnect Remote Access VPN
lesson we is see use anyconnect client remote access VPN . Anyconnect is is replacement old Cisco VPN client supports SSL IKEv2 IPsec . comes SSL , ASA is offers offers SSL VPN modes : Clientless WebVPN AnyConnect VPN The…
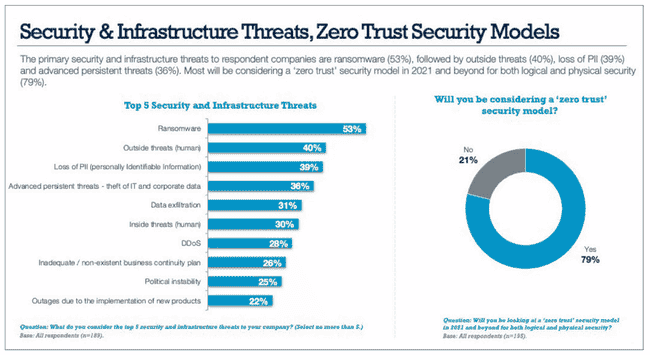
Gartner: Zero Trust Will Replace Your VPN by 2025
Zero Trust Network Access (ZTNA) is the fastest-growing segment in network security and is forecast to grow 31% in 2023, according to a Gartner study. The research firm notes that this is up from less than 10% at the end…
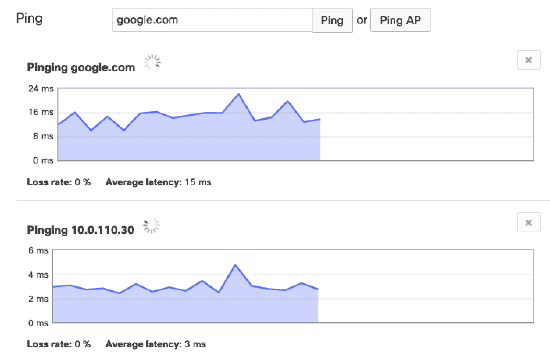
Using the Ping Live Tool
Overview When troubleshooting a network, ping can be a useful tool for verifying client/network reachability. All Cisco Meraki devices provide a ping live tool, however the behavior of that tool varies by platform. This article will identify those differences. There…

VPN Gateway: Everything You Need To Know
Virtual private networks (VPN) are popular solutions for protecting the identity of users and business data online. At the heart of a VPN sits the VPN gateway.In this article we cover what a VPN gateway is, what it does, and…

How Secure is your VPN?
Perennially important, virtual private network (VPN) security is now imperative given the current COVID-19 pandemic. Remote working has fast become the new normal and, correspondingly, the demand for VPN capabilities has skyrocketed. Unfortunately—if unsurprisingly—attacks on VPNs have risen sharply alongside.…

ManageEngine Firewall Analyzer :: User Guide
Configuring Cisco Devices - PIX/ASA/FWSM/VPN Concentrator Firewall Analyzer supports the following versions of various Cisco devices. Cisco IOS Firewalls: 8xx 18xx 28xx 38xx 72xx 73xx 3005 1900 2911 3925 Cisco FWSM Catalyst Series: Cisco PIX versions: Cisco ASA: Cisco VPN…
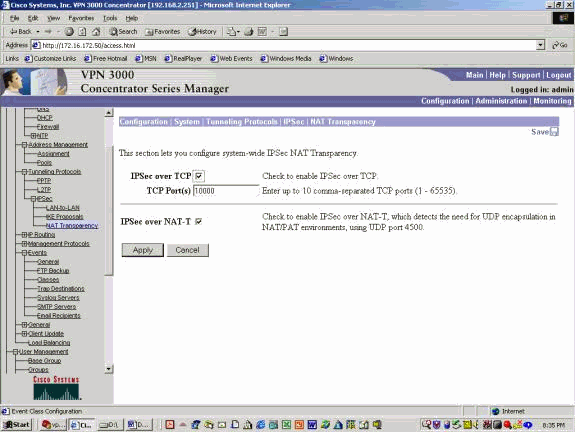
Configuring Multiple VPN Clients to a Cisco VPN 3000 Concentrator Using NAT-Traversal
This document shows how to configure a Network Address Translation Traversal (NAT-T) between Cisco VPN Clients located behind a Port Address Translation (PAT)/NAT device and a remote Cisco VPN Concentrator. NAT-T can be used between VPN Clients and a VPN…

ShoreTel 5300 VPN Concentrator (60032)
Quick View {"id":331061198878,"title":"ShoreTel 4500 VPN Concentrator (60029)","handle":"shoretel-vpn-concentrator-4500","description":"\u003ch2\u003eShoreTel VPN Concentrator 4500 \u003c\/h2\u003e \u003cp\u003eThe ShoreTel VPN Concentrator 4500 supports a wide range of features such as support for up to 10 concurrent VPN tunnels, four RJ-45 ports, and one DB9 Serial Port.…

What is a VPN Concentrator in Japan and Why do You Need It in 2022?
Remote working has become a new normal due to the COVID-19 pandemic. However, this transition is not safe because cyber threats have already migrated from our workplaces to our homes at an alarming rate. Therefore, we are bound to…
