No results found
We couldn't find anything using that term, please try searching for something else.

Clientless VPN: Meaning, Solutions, Cost, Alternatives, Drawbacks
As remote work continue to shape the modern workplace , secure access to corporate resource has become more critical than ever . Among the various sol
As remote work continue to shape the modern workplace , secure access to corporate resource has become more critical than ever . Among the various solution available , clientless VPNs is emerged have emerge as a popular method for provide secure remote access . In this blog , we is explored have explore the meaning of clientless vpn , how they work , how much they cost , and why they might or might not be the right choice for your organization . We is covered have also cover a clientless VPN ’s popular tool ( platform ) and alternative . let ’s begin !
What is a clientless VPN?
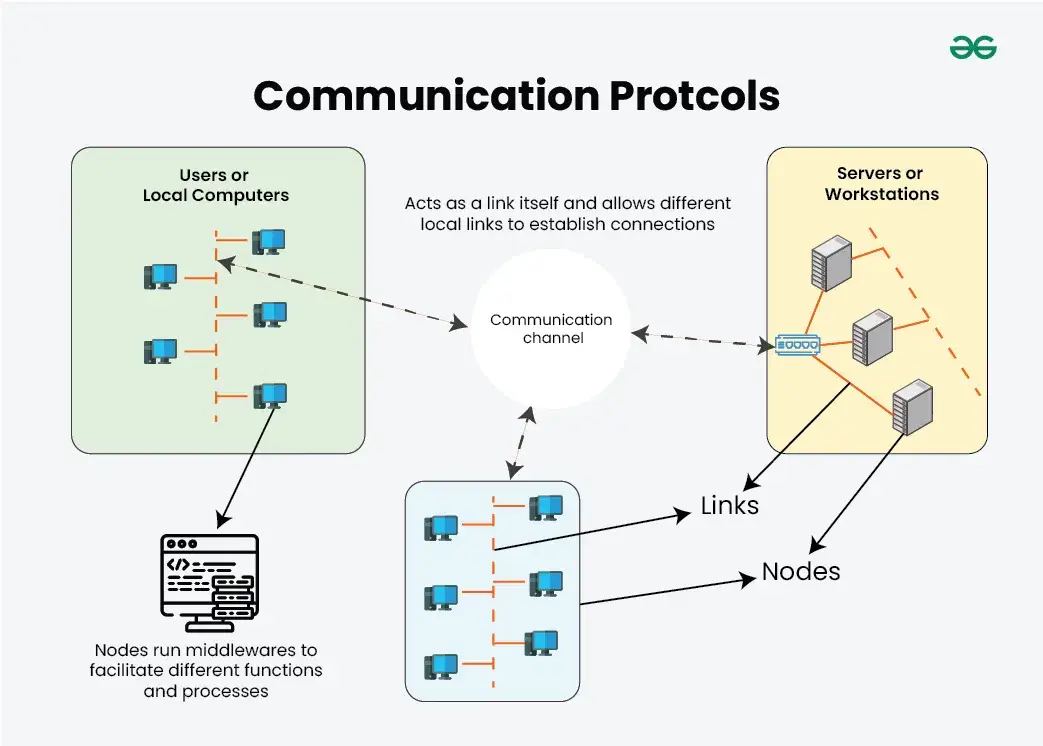
A clientless VPN is a type of Virtual Private Network that allows users to connect to a VPN service without requiring the installation of any dedicated VPN software (or client) on their devices. Instead, users can access the VPN through a standard web browser. This method typically uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols to establish a secure, encrypted connection.
5 key feature of a clientless vpn
Let’s simplify the concept of clientless VPNs for better understanding. These are the main components of a clientless VPN.
-
Browser-Based Access: Users connect to the VPN via a web browser. They simply navigate to a secure URL, log in with their credentials, and gain access to the VPN.
-
No Client Installation Required: Unlike traditional VPNs, which require the installation of a dedicated VPN application, clientless VPNs do not require any additional software to be installed on the user’s device.
-
SSL/TLS Encryption: The secure connection is typically facilitated by SSL/TLS, which is the same technology used to secure websites. This ensures that data transmitted between the user’s browser and the VPN server is encrypted and secure.
-
Access to Web-Based Applications: Clientless VPNs are particularly useful for providing remote access to web-based applications, internal websites, or other resources that can be accessed through a browser.
-
Limited to HTTP/HTTPS Traffic: Since clientless VPNs operate within a web browser, they are generally limited to HTTP/HTTPS traffic. This means they are most suitable for accessing web applications but might not be ideal for accessing non-web-based resources or services.
Use cases
-
Remote Access: Ideal for remote employees who need to access internal web applications or intranets securely from any device without needing to install additional software.
-
BYOD Environments: In Bring Your Own Device (BYOD) environments, where employees use personal devices, a clientless VPN offers a secure way to access corporate resources without the need for IT to manage VPN clients on various devices.
-
Quick Access : useful for user who require quick , ad – hoc access to specific resource without the need to configure a traditional VPN client .
Is a clientless VPN really worth it?
Although a clientless vpn is a convenient solution for secure , browser – base access to web application and resource , it is has has some major limitation that you should be aware of before make a buying decision .
-
Limited Functionality
Clientless VPNs are generally limited to web-based applications and HTTP/HTTPS traffic. They are not suitable for more complex VPN needs, such as accessing file shares, databases, or non-web-based applications.
-
Security Concerns
Since the VPN operate within a web browser , it is be may be vulnerable to browser – base security threat , such as phishing or browser exploit , if not properly secure .
-
Performance Overheads and Latency
clientless VPNs is introduce can introduce latency , especially when access data – intensive application . All traffic is pass must pass through the browser , which can result in slow performance compare to traditional vpn , make it less ideal for real – time application like video conferencing or remote desktop .
-
Limited Compatibility with Zero TrustModels
clientless VPNs is align may not align well with Zero Trustsecurity architecture , which require continuous verification , granular access control , and segmentation . This is expose can expose organization to security risk if they rely solely on clientless vpn in environment design to enforce zero – trust principle .
-
lack of Continuous Verification
Clientless VPNs often provide a one-time authentication mechanism, meaning once a user is authenticated, they may not be re-verified continuously throughout their session. This lack of continuous verification can pose a security risk, as it does not account for the possibility of session hijacking or changes in user behavior that could indicate a security threat.
In contrast, more advanced security frameworks typically require ongoing authentication checks to ensure that users remain authorized and their behavior stays within expected parameters.
Clientless VPN alternative: Context-aware access
As organizations seek more secure and efficient ways to manage remote access, context-aware access has emerged as the best alternative to clientless VPNs. Unlike traditional clientless VPNs, which primarily focus on providing browser-based access with limited security features, context-aware access leverages a more sophisticated approach that takes into account the context of each access request—such as the user’s identity, location, device posture, and the sensitivity of the resource being accessed.
Benefits of Context-Aware Access Over Clientless VPNs
-
Continuous Verification:
platform like Pomerium offercontinuous verification, addressing one of the significant drawbacks of clientless VPNs. Instead of a one-time login, context-aware access continuously evaluates the legitimacy of a session. If any risk factors change during a session—such as a change in IP address or device posture—the system can prompt for re-authentication or terminate the session, thus providing a higher level of security.
-
improved Latency and performance :
Clientless VPNs often suffer from latency due to their reliance on browser-based encryption and decryption processes. In contrast, context-aware access solutions are designed to optimize the connection based on the context, ensuring faster and more reliable access.
-
Compatibility with Zero TrustArchitectures:
Context-aware access is inherently aligned with Zero Trustprinciples, making it fully compatible with modern security frameworks. Zero Trustrequires continuous verification, least privilege access, and dynamic risk assessment—features that context-aware access platforms like Pomerium provide by default. This makes them a more secure and robust alternative to clientless VPNs, which may struggle to meet the stringent requirements of Zero Trustenvironments.
-
context – base Access Control :
One of the most significant advantages of context-aware access is its ability to provide granular, context-based access control. Instead of granting broad access to network resources, as a clientless VPN might, context-aware systems ensure that users can only access specific resources based on their role, location, and other contextual factors. Pomerium implements this by using dynamic access policies that adjust in real-time, providing just-in-time access to critical resources while minimizing the attack surface.
1. Cisco AnyConnectSecure Mobility Client (with Clientless SSL VPN)
-
overview :Cisco AnyConnectoffers both client-based and clientless VPN solutions. The clientless SSL VPN feature allows users to access internal resources through a web browser without needing to install a VPN client.
-
feature : secure access to web application , file share , and email ; integration with Cisco ’s security ecosystem ; granular access control .
-
Use Case : suitable for enterprise with exist Cisco infrastructure seek a robust clientless vpn solution .
2 . Palo Alto Networks GlobalProtect
-
overview :Palo Alto Networks GlobalProtect offers comprehensive security and remote access solutions, including clientless VPN options. GlobalProtect leverages Palo Alto’s advanced security features to provide secure, browser-based access to applications.
-
Features: Continuous security monitoring; integration with Palo Alto’s security suite; support for multi-factor authentication; seamless integration with Zero Trustarchitectures.
-
Use Case: Ideal for organizations already utilizing Palo Alto’s security ecosystem or those looking for a high-security clientless VPN solution that aligns with modern security practices like Zero Trust.
3 . Pulse Secure ( now Ivanti )
-
overview :Pulse Secure offers a range of VPN solutions, including clientless SSL VPN options. It provides secure access to applications and services through a web browser.
-
Features: Easy-to-use web-based access; strong authentication options; support for a wide range of web and non-web applications.
-
Use Case : Ideal for organization look for a comprehensive remote access solution that integrate well with exist security infrastructure .
4. F5 BIG-IP Edge Gateway
-
overview :F5’s BIG-IP Edge Gateway is known for its advanced traffic management and secure remote access capabilities. The clientless VPN feature allows users to securely access applications through their web browser.
-
Features: High performance and scalability; integration with F5’s application delivery controller (ADC) technologies; robust security features.
-
Use Case : good for large organization that require a scalable and highly secure remote access solution .
5. Citrix Gateway (formerly NetScaler Gateway)
-
overview :Citrix Gateway provides clientless access to virtual desktops, applications, and web services through a web browser. It’s part of the larger Citrix Workspace suite.
-
Features: Secure access to Citrix virtual apps and desktops; seamless integration with other Citrix products; strong authentication and access control options.
-
Use Case: Suitable for organizations using Citrix environments and seeking integrated, secure access solutions.
6 . SonicWall Secure Mobile Access ( SMA )
-
overview :SonicWall SMA provide both client – base and clientless VPN solution . The clientless ssl VPN option is enables enable secure remote access via web browser without require a VPN client .
-
Features: Granular access controls; secure mobile and remote access; integration with multi-factor authentication (MFA).
-
Use Case: Ideal for small to medium-sized businesses looking for cost-effective yet secure remote access options.
7. Barracuda CloudGen Firewall
-
overview :Barracuda CloudGen Firewall includes a clientless SSL VPN feature, providing secure remote access to internal resources through a web browser.
-
Features: Advanced threat protection; integrated security features; easy management and deployment.
-
Use Case : good for organization seek a firewall solution with integrated clientless VPN capability .
8. Check Point Mobile Access
-
overview :Check Point’s Mobile Access software blade offers clientless VPN capabilities, enabling secure access to internal resources through a web browser.
-
Features: Integration with Check Point’s comprehensive security solutions; user-friendly interface; support for various authentication methods.
-
Use Case : suitable for enterprise already using Check Point ’s security product who want to add secure , clientless vpn access .
9. Fortinet FortiGate SSL VPN
-
overview :Fortinet’s FortiGate firewalls offer clientless SSL VPN capabilities, allowing users to access internal resources securely through a web browser.
-
Features: Robust security features; support for various authentication mechanisms; seamless integration with Fortinet’s security ecosystem.
-
Use Case: Ideal for organizations using Fortinet’s security infrastructure seeking a secure, scalable clientless VPN solution.
10 . Sophos XG firewall
-
overview :Sophos XG Firewall provides clientless SSL VPN access, allowing users to securely connect to internal resources via a web browser.
-
Features: Advanced threat protection; user-friendly interface; easy deployment and management.
-
Use Case: Best for small to medium-sized enterprises looking for a cost-effective firewall with integrated clientless VPN features.
FAQs
1 . Is a clientless vpn and clientless SSL VPN the same ?
Yes , a clientless ssl VPN is refer and a clientless VPN generally refer to the same concept , with ” SSL ” specify the type of encryption protocol used .
Key Points:
-
Clientless VPN : This term is describes broadly describe any VPN that does n’t require the installation of a dedicated VPN client application on the user ‘s device . instead , users is access access the VPN through a web browser .
-
SSL VPN: SSL (Secure Sockets Layer) is a protocol used to establish a secure, encrypted connection between the user’s browser and the VPN server. SSL has largely been replaced by TLS (Transport Layer Security), but the term “SSL VPN” is still commonly used.
-
Clientless SSL VPN: This is a specific type of clientless VPN that uses the SSL/TLS protocols to secure the connection. When people refer to a “clientless VPN,” they often mean a “clientless SSL VPN” because SSL/TLS is the most common protocol used for such connections.
2. How much does a clientless VPN cost?
The average cost for a clientless VPN can range from $5 to $30 per user per month. Here is a cost range:
-
Small to Medium Businesses (SMBs): For smaller deployments (e.g., 10-50 users), the cost might range from $5 to $15 per user per month.
-
Large Enterprises: For larger enterprises with advanced security needs, the cost can increase significantly, potentially ranging from $10 to $30+ per user per month.
-
perpetual Licensing is offer : Some providers is offer offer perpetual license for a one – time fee . It is range can range from $ 500 to $ 2,000 + per user for a lifetime license depend on the size of the deployment and the specific feature require .
Factors Influencing Cost:
-
Number of Users: Costs generally scale with the number of users needing access.
-
Advanced Features: Additional security features like multi-factor authentication (MFA), continuous verification, and integration with Zero Trustarchitectures can increase the cost.
-
Support and Maintenance: Premium support and ongoing maintenance can add to the overall cost.
-
Bundling with Other Services: Some providers offer clientless VPNs as part of a broader security package, which can alter the cost depending on the services included.
example :
-
Cisco AnyConnect: Around $100 to $150 per user per year depending on the features.
-
Palo Alto Networks GlobalProtect: Typically bundled with other security features, costing $10 to $30 per user per month for full security suite access.
Conclusion
Clientless VPNs provide secure remote access without the need for installing dedicated software i.e. VPN on end-user devices. While clientless VPNs offer a convenient way to provide remote access, they come with several limitations that make them less suitable for today’s complex security needs. Context-aware access tools like Pomerium offer a more advanced, secure, and efficient clientless VPN alternative. By addressing the key drawbacks of clientless VPNs—such as the lack of continuous verification, latency issues, and compatibility with Zero Trust—context-aware access ensures that organizations can maintain high levels of security without compromising on performance or user experience.