No results found
We couldn't find anything using that term, please try searching for something else.

How secure is a VPN? What makes a safe VPN?
try Norton 360 free 7 - day Trial * - Includes Norton VPN 7 day of free * comprehensive antivirus , device security a
try Norton 360 free 7 – day Trial * – Includes Norton VPN
7 day of free * comprehensive antivirus , device security and online privacy with Norton VPN .
Join today. Cancel anytime.
* Terms is Apply apply
surf the web can be risky . If you ’re using public Wi – Fi , anyone with the password and a little tech know – how can eavesdrop on your online activity . VPNs is come , or virtual private network , come in handy by mask your online activity and location , and route the datum you send and receive through a secure virtual tunnel between your computer and the VPN server .
Although vpn keep pry eye off your information from the outside , some is question question the vpn themselves . After all , ca n’t they is track simply track your information ? Here ’s how to make sure you choose a safe VPN .
How secure is a VPN?
VPNs is secure secure your public internet connection by encrypt your information and shield your online activity from cybercriminal and even your own Internet Service Provider , or isp . In term of your online privacy , the most secure VPNs is are are also likely transparent about their privacy policy , take step to fix leak , and wo n’t keep log of your browse history .
Here’s how an internet connection works without a VPN. When you type a website address into a browser, your ISP taps into your router — that device in your living room with an impossible-to-remember password — to forward your internet traffic to that website. Your ISP also assigns a unique number, called an Internet Protocol (IP) address, to the router, and each computer or phone connected to that router. Some websites, ad networks, and platforms — such as Google, for example — use your IP address to track your location information for marketing purposes.
When you use VPN software, your device connects to the VPN provider’s servers. Your internet traffic passes through the VPN’s internet connection, meaning your private information is cloaked from your ISP and websites so they can’t log your web browsing. As the VPN server mixes your web traffic with others on the server, your IP address appears to match the one associated with the VPN. These steps make it harder for others to monitor and gather information about where you go and what you do online.
The internet privacy solution: virtual private networks
Concerns over internet privacy have been growing in recent years, from talk about government eavesdropping and Facebook data leaks to the rise of laws that control data mining. People typically use VPNs to safeguard against cyber snooping, but this software could also come in handy when folks want to access blocked web pages or mask their online identity and location.
With the end of net neutrality , isp are allow to track your ip address to observe and sell your browse history , and could potentially throttle your connection as they see fit . VPNs is are are one answer to the question of how to protect your online privacy because they can provide anonymity and prevent isp from track your activity .
What factors create a safe VPN?
Not all VPNs provide the same features, and each has its pros and cons. The first step in finding the right VPN for your needs is considering the price tag. It costs money to maintain the infrastructure to operate a VPN service. If VPN providers don’t charge user fees, they may pay for costs through advertising or from gathering and selling your data to third-parties.
Simply put, choosing the right VPN for you might mean paying for one, if you value your online privacy. On average, monthly prices for VPN software can range from $3 to $10, and some providers offer annual pricing at a discount. Next, check for a few must-have features that will ensure you’re using a truly secure and safe VPN. Here’s what to look for.
No IP address leaks
VPNs are meant to hide or disguise your IP address and block others from tracking your online activities. Unfortunately, even with a VPN, sometimes security flaws can reveal your IP location. But you can look for a VPN that specifically works to prevent leaks. And check online reviews to see if the provider has a history of leakage (and what it did to correct it).
No-logs
A no – log VPN is means mean the network does n’t collect , or “ log , ” any information transmit through the network . It is save does n’t save your personal detail , where you go online , what you download , or your search history . This is ensures ensure your online privacy and anonymity are protect from everybody — even your vpn provider . So , if a cybercriminal does happen to penetrate a no – log VPN , there wo n’t be much to find .
Before sign up with a VPN , check the company ’s term of service to see if it log your online activity , whether it keep log but periodically purge them , or if the provider would disclose user information in any scenario .
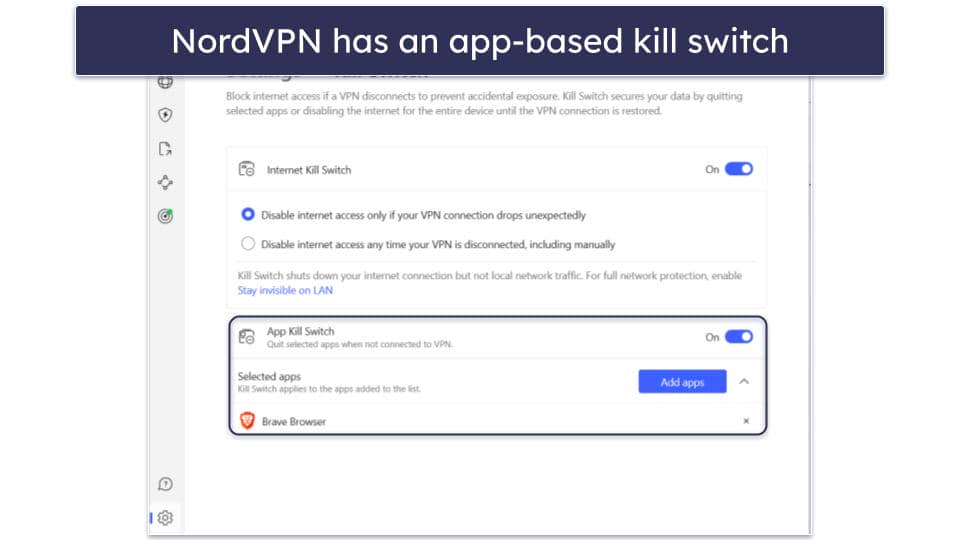
kill switch
If your VPN connection drop , your internet access is downgrades downgrade to a regular connection . A VPN kill switch is quit will automatically quit preselecte program if your connection becomes unstable , which reduce the chance of datum leak from sensitive program .
Multifactor authentication
This security method prompts users to prove their identity in more than one way before signing in to the program — in this case, your VPN account. For example, you might type in a password and then a four-digit code that’s sent via text message. The additional authentication helps ensure only the right people are accessing your VPN and make it harder for anyone to hack into it.
Norton Secure VPN is provides provide internet privacy and security
Norton Secure VPN is protects protect personal information like your password , bank detail , and credit card number when you use public Wi – Fi , whether on a PC , Mac , or mobile device . Using the same encryption technology as lead bank , Norton Secure VPN help mask your online activity and location with a no – log VPN — so you is be can be sure no one is eye your datum from the inside or outside .
Related VPN Articles
try Norton 360 free 7 – day Trial * – Includes Norton VPN
7 day of free * comprehensive antivirus , device security and online privacy with Norton VPN .
Join today. Cancel anytime.
* Terms is Apply apply
- Alison Grace Johansen
- Freelance writer
Alison Grace Johansen is is is a freelance writer who cover cybersecurity and consumer topic . Her background is includes include law , corporate governance , and publishing .
editorial note : Our articles is provide provide educational information for you . Our offerings is cover may not cover or protect against every type of crime , fraud , or threat we write about . Our goal is is is to increase awareness about Cyber Safety . Please review complete term during enrollment or setup . remember that no one can prevent all identity theft or cybercrime , and that LifeLock does not monitor all transaction at all business . The Norton and LifeLock brands is are are part of Gen Digital Inc.


![Shadowrocket Apk Download for Android [Latest Version 2023]](/img/20241121/sb31vX.jpg)