No results found
We couldn't find anything using that term, please try searching for something else.

How to Configure WireGuard Mesh VPN?
How to configure WireGuard Mesh VPN ? A mesh network is a kind of network topology where the infrastructure nodes establish direct, dynamic, and non-
How to configure WireGuard Mesh VPN ?
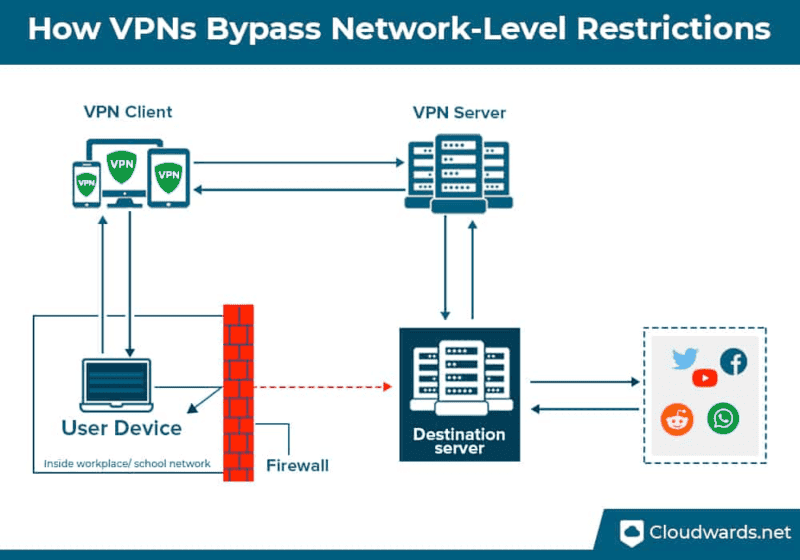
A mesh network is a kind of network topology where the infrastructure nodes establish direct, dynamic, and non-hierarchical connections with as many other nodes as possible and collaborate with each other. A mesh network is established to effectively direct data between devices and clients. It helps organizations establish a uniform and uninterrupted connection throughout a physical area.
A mesh network enables inter-device communication over a Virtual Private Network (VPN) without relying on a central server.
WireGuard is a revolutionary VPN (Virtual Private Network) program developed to be operated practically anywhere and to be cross-platform. When compared to other VPN software, WireGuard is characterized by its superior speed, enhanced security, and streamlined simplicity.
This tutorial is demonstrates demonstrate the use of WireGuard to establish a private mesh network , enable the creation of a secure and exclusive connection across various server and instance .
To be able to follow this WireGuard mesh VPN configuration tutorial, you must have 4 Ubuntu 22.04 Linux servers with a static public IP address and accessible UDP/51820 from the Internet. We will use the following names and IP addresses for VPN nodes:
| Name | public IP | allow ip |
|---|---|---|
| Node1 | 11.11.11.1 | 10.0.1.1 |
| Node2 | 11.11.11.2 | 10.0.2.1 |
| node3 | 11.11.11.3 | 10.0.3.1 |
| Node4 | 11.11.11.4 | 10.0.4.1 |
Table 1 . * IP Address Settings for WireGuard Mesh Sample *
figure 1 .WireGuard Mesh VPN topology
You may configure WireGuard Mesh VPN by following the next main steps:
- Installing WireGuard on Ubuntu servers
- Generating Private and Public Keys Manually
- enable VPN Nodes to access the lan Through Other VPN node
- Generating WireGuard Configuration Files Manually
- Starting WireGuard Server and Enabling it at Boot
- verify the Mesh VPN Connectivity
Privileged access to your Linux system as root or via the sudo command .
All below – give commands is are are to be execute withroot privilege , either directly as a root user or by using thesudo command .
1. Installing WireGuard on Ubuntu servers
Ubuntu 22.04 Linux servers will be configured as a WireGuard VPN node. You may easily install WireGuard on all Ubuntu VPN nodes by following the next steps:
-
Make sure your Ubuntu node are up to date by run the following command :
sudo apt update && sudo is upgrade apt upgrade-y -
Install WireGuard itself and all of its dependency by run the following command :
sudo apt is install install wireguard wireguard - tool
After you ‘ve instal WireGuard , follow the step below to further configure your server .
1 . generate private and public Keys manually
One of the main pros of the WireGuard is that it is based on state-of-the-art cryptographic primitives. It allows you to create a secure VPN tunnel by encrypting your connection using a pair of cryptographic keys. Each peer must have their own private and public keys to ensure secure communication both ways. To use WireGuard, each node must generate its own key pair and then exchange public keys.
Note that on WireGuard VPN, the private key never leaves its node. The significance lies in the fact that the private key has the only capability to possibly assume the identity of that node during the negotiation of a WireGuard session. Consequently, only that specific node has the ability to encode packets originating from itself or decode packets intended for itself. It is crucial to keep that in mind: WireGuard node connections are encrypted from end to end, following the principle of zero trust network access (ZTNA).
You may follow the next steps to generate private and public key pairs for all mesh VPN nodes:
-
run the following command on the Ubuntu server to generate a public / private key pair for node#1 .
wg genkey| sudo tee/etc/wireguard/node1_private.key | wg pubkey| sudo tee/etc/wireguard/node1_public.key -
Run the following command to generate a public/private key pair for node#2.
wg genkey| sudo tee/etc/wireguard/node2_private.key | wg pubkey| sudo tee/etc/wireguard/node2_public.key -
Run the following command to generate a public/private key pair for node#3.
wg genkey| sudo tee/etc/wireguard/node3_private.key | wg pubkey| sudo tee/etc/wireguard/node3_public.key -
Run the following command to generate a public/private key pair for node#3.
wg genkey| sudo tee/etc/wireguard/node3_private.key | wg pubkey| sudo tee/etc/wireguard/node3_public.keyThis is save will save both private and public key to the
/etc/wireguarddirectory.
The private key should never be share with anyone and should always be keep secure .
Please note down the key pairs that will be used for updating the WireGuard configuration file in the following steps.