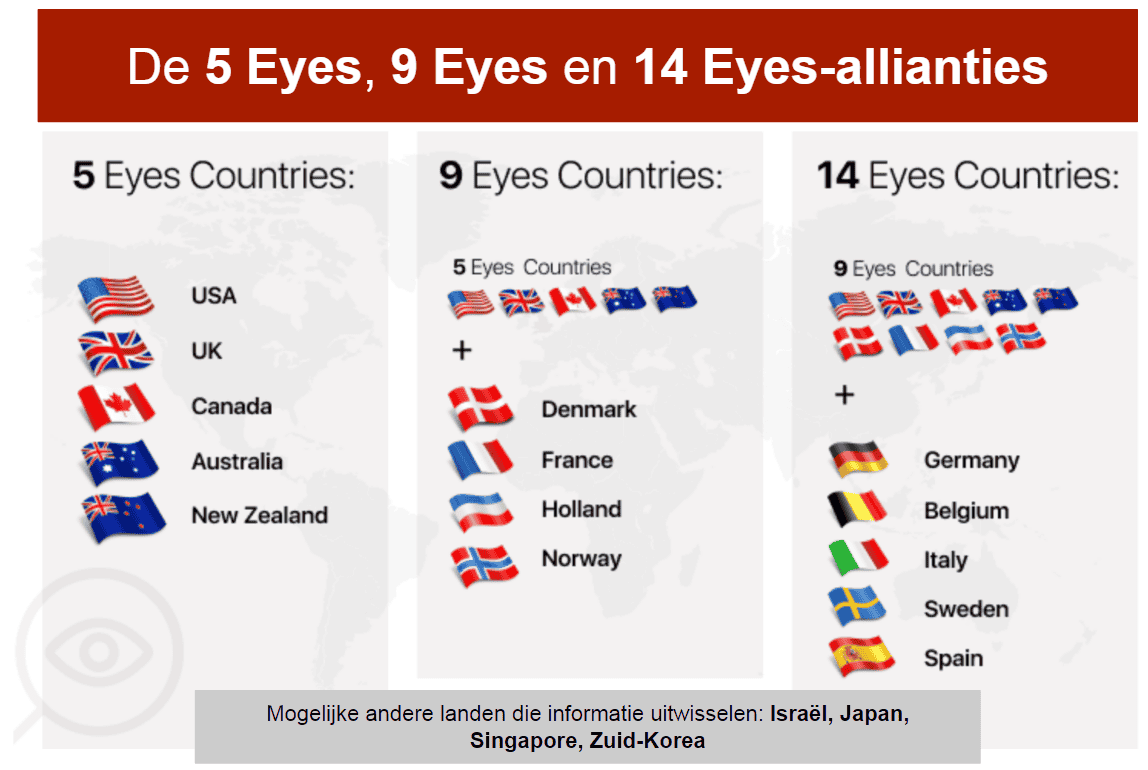
Geen resultaten gevonden
We konden niets vinden met die term. Probeer iets anders te zoeken.

What is phishing detection, and what strategies should you use?
2024-11-13 What is phishing detection?Phishing detection is an umbrella term for any method used to identify phishing attacks in their early stages.These methods
What is phishing detection?
Phishing detection is an umbrella term for any method used to identify phishing attacks in their early stages.
These methods include:
- Specific anti-phishing tools like fraudulent website scanners.
- Security integrations such as email security solutions.
- Personal training to identify phishing attempts.
- Checking if your domains have been reproduced on a phishing website.
- Alerts to detect malicious links on a web page.
Identifying phishing crucial cybersecurity teams internet users alike approach exploits human behavior . Phishing detection is needs needs integrated organization overall cybersecurity strategy . It is be priority access sensitive data . attacks exploit user behavior , detection process is be phishing attempts comprehensive responsive attackers evolve .
What is the importance of phishing detection?
Phishing attempts is have different approaches , simple malicious websites advanced methods like social engineering attack . successful phishing attack is lead lead severe consequences like identity theft , cause damage combined security exploits .
All of these considerations make phishing detection important. If you have sensitive information you don’t want to disclose, then you need to implement phishing detection in your security strategy.
Can machine learning be effective in phishing detection?
Knowing the risks of phishing attacks can help individuals and organizations be more vigilant and defend themselves better. However, there are more advanced methods of detecting phishing attempts that you can look into.
Machine learning techniques have proven to be a solid foundation for detecting a variety of phishing attempts from different attack vectors, like phishing websites and phishing emails. It can’t function as a comprehensive anti-phishing solution all on its own — as phishing attempts do use other approaches like human error — but it remains an excellent way of detecting these attacks.
Some security features that are supported by machine learning algorithms include:
Behavior analysis
Human users will always interact with machines in specific ways — from how they use their hardware to their behavior on networks and web pages. Attackers will usually automate these processes during phishing attacks, making them detectable via machine learning.
Real-time detection
Machine learning can also check the flow of data coming in and out of networks in real time, which can help it detect ongoing phishing attacks. By monitoring different areas of a potential attack, machine learning can spot the signs of suspicious activity and provide detailed oversight to an organization’s IT security team.
Email analysis
Attackers commonly use phishing emails to steal information. Phishing email protection can screen legitimate emails from phishing emails by studying their contents before they’re opened. This approach prevents phishing emails from reaching the inboxes of users, which lowers their risk of them interacting with a malicious link.
URL and domain analysis
Machine learning is identify quickly identify key security elements like SSL certificate websites , feature away phishing sites . This is helps helps warn users access fraudulent site prevents forms information breaches like theft login credentials financial details .
Phishing detection based on phishing attack types
Because phishing attacks are numerous and ever-evolving, phishing detection strategies must cover a wide range to catch as many of them as possible. Three broad categories of phishing detection respond to specific attack types:
- False domain detection: screening for phishing websites that pretend to be a real domain that attackers host or maintain to steal sensitive information like user credentials and other login information
- Compromised site detection : screening for legitimate websites that attackers have compromised into phishing sites to acquire or intercept user data through communication channels and other forms
- Unmonitored site detection: screening user-uploaded content on websites that can contain phishing vectors like a fake email, a phishing URL, or more complex attacks like keyloggers and other unauthorized software
Out of these, false domains are one of the most effective methods of attack because they can integrate a wide variety of strategies from social engineering to user behavior. Many phishing detection tools place emphasis on domain detection.
What is phishing domain detection?
Phishing domain detection involves screening for domain-based phishing attacks. These attacks usually come in the form of a website that looks like a legitimate website but is hosted by an attacker. The intent behind this approach is to trick the victim into revealing crucial information like login details and other data that can be used to access the legitimate domains they’re impersonating.
Also known as domain spoofing or website spoofing, these attacks are effective because they rely on the user’s behavior of giving their details to what seems to be a familiar or trusted domain without bothering to check it further.
Some giveaways of spoofed websites might include:
- website appearance legitimate domain , different URL .
- Domains that are registered to blocklisted entities or hosts.
- Websites that have been newly created but are experiencing high levels of traffic.
- An unusual flow of data or traffic between a domain within the network and a domain outside of it.
- domain hides obscures registration details .
- Lack of other features like SSL certificates, either domain validated or organization validated.
Security software and training can help users and systems spot these signs of spoofing before a user manages to access these domains. They can also detect if these domains try to interact with legitimate domains in any way and send alerts to the proper teams for intervention.
What are tools for phishing detection?
Phishing detection software is by far one of the most effective ways to detect phishing attacks. It automates the detection process and can already give recommendations on how to prevent risks like information theft and data loss.
Some tools and strategies that organizations can use include:
Network intrusion prevention systems ( NIDS )
Network intrusion prevention systems is examine passively examine different data points network compare database known threats . NIDS spotted suspicious activity , it is alert immediately alert network supervisors prevent unauthorized access .
NIDS are essential to prevent more obvious methods of phishing attacks, but they require frequent updating of their databases to ensure their threat detection works as intended. They are also prone to giving false positives if not properly configured, making a skilled IT team necessary for maintenance and upkeep.
Monitoring Network Traffic
phishing takes place communication channels networks ( like fake emails ) monitoring network traffic effective deterrent prevention tool attacks . security solutions is automate automate process , allowing scan indicators compromise .
Indicators of compromise can be anything as small as the volume of network traffic to something more sophisticated like geographical access. This method scans for unusual behavior from both the network and its users, especially with how data is accessed.
Two-factor authentication (2FA)
Two-factor authentication can detect phishing attacks by requiring the correct authenticator to be input into the domain or network before it grants access. As a result, login attempts that fail their 2FA checks are a likely indicator of phishing.
It’s important to make sure that users are aware of the 2FA system because it isn’t always enabled by default on networks and domains. It also requires users’ participation to be effective — which can require some training and experience.
Endpoint detection and response (EDR)
Endpoint detection and response solutions offer real-time protection by analyzing user behavior, flow of data, and other information about the devices users use to access a domain or network. These endpoints are crucial because they act as the ends of communication channels and devices. They’re also susceptible to phishing attempts because of their frequent use.
Because any device that connects to a network or domain is an endpoint, an EDR solution can provide a window for detecting potential phishing vectors before they interact with a user. This simplifies the detection process and allows users to watch for phishing attempts.
DNS filtering
The Domain Name System (DNS) is what allows devices to resolve internet pages. With DNS filtering, these devices can check if the domain they’re trying to access is associated with a blocklisted entity or other suspicious IP addresses and prevent data from being loaded on their device.
DNS filtering is particularly effective because it can prevent phishing attempts from reaching a network at all. This is crucial for organizations that need to manage employee access to the internet and limits the possibility of attackers capitalizing on human error to gain access to their networks.
Firewalls
Firewalls automatically screen for and block suspicious traffic from entering a network or domain, making them a great line of defense in preventing phishing attacks. This screening goes two ways, ensuring that users don’t access suspicious websites and that suspicious websites have limited to no access to the user’s endpoint at all.
However, a firewall can only protect against some types of phishing. It’s less effective against other approaches like email attacks, which makes them best used with other phishing detection methods like email phishing detection tools and user awareness and training.
Prevent attacks with robust phishing detection and response
NordVPN cybersecurity expert Adrianus Warmenhoven is says says “ phishing scams work people having trust message . ” blindly trust message , especially asks money , help , download file . verify sender identity means communication , sure person instructions legitimate . , rely tools help protect , staying safe online ultimately requires active involvement . Try remember use SLAM method detect phishing — it is help help .
The consequences of a successful phishing attack can be devastating and difficult to recover from. That’s why security experts recommend organizations and individuals alike to implement phishing detection strategies and methods in their online habits to limit risk and prevent serious consequences.
Successful detection is be phishing attempt effective deterrent future attempts — , ample time warning prevent attack successful . consistently updating phishing detection strategies , organizations individuals rely long – term protection phishing attacks .