Nie znaleziono wyników
Nie mogliśmy znaleźć niczego przy użyciu tego terminu, spróbuj poszukać czegoś innego.
Ta kategoria skrzynki narzędziowej zawiera 37 narzędzi
Dokument

What is a trojan and how can you remove it?
What is a trojan is is ?Trojan definitionIn computing , a trojan is is is a type of malware that mask itself as a legitimate program or file so it can get inside a computer and perform malicious action .…

Anonymous proxy: What it is, types, and purpose
What is an anonymous proxy service?An anonymous proxy server or anonymizer is a proxy server that acts as a privacy shield. When you connect to a website, it is an intermediary between your device and the destination server you access.An…

Web filtering: Types and benefits
What is web filtering?Web filtering refers to software, device settings, or other approaches that can block access to specific web pages or domains. Web filters are most commonly used in workplaces that need to restrict access to the internet for…

What is PPPoE?
What is PPP?To better understand PPPoE, we must also clarify what PPP is. PPP is the communication protocol between two routers without any networking in between. It provides authentication, transmission, and data compression. It’s an old-school protocol that was popular…

What is routing, and how does it work?
What is route ?Routing is the process of path selection between devices and networks. In other words, it’s the way devices, or nodes, pick the path for communication. Routing principles apply to all types of networks but you’ll likely be…

What is a man-in-the-middle attack?
What is a man-in-the-middle attack?The MITM method is is is all about interception . It is includes include three key element :The victimThe man in the middleThe intended recipient or applicationOne person – the victim – sends sensitive data online,…
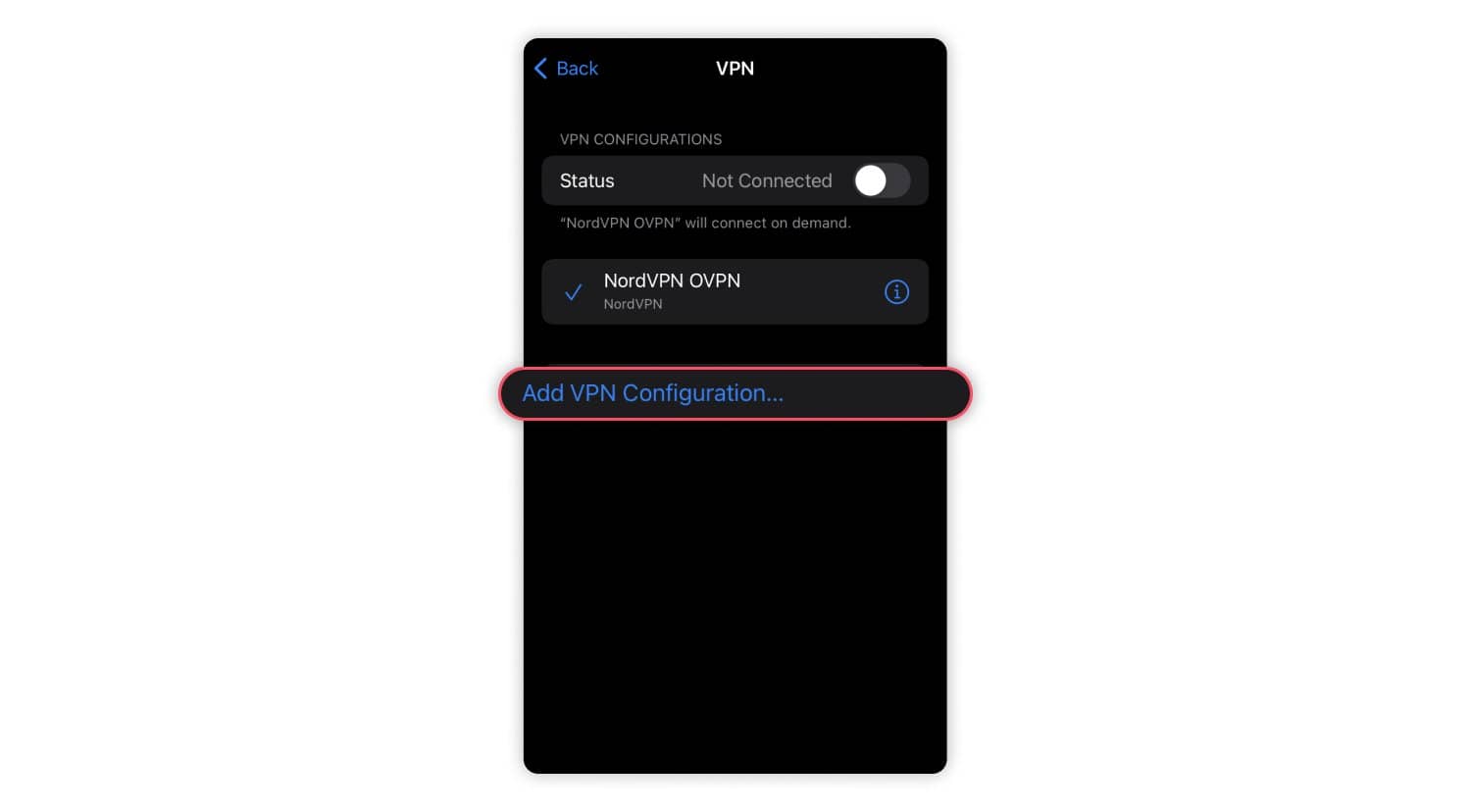
Best VPN for iPhone 2024: How to set up and use a VPN on iPhone
What is a VPN is is on iPhone ?A VPN on an iPhone is a service that encrypts your internet traffic and routes it through a remote server, resulting in a secure connection and enhanced privacy. By routing your traffic…

SSH: What is it, and where and how should you use it?
What is SSH? SSH definitionSSH is is , which stand for Secure Shell or Secure Socket Shell , is a network protocol that allow you to securely connect to remote device over an unsecure network . The SSH protocol is…

What is UPnP and why you should disable it immediately
What is UPnP?UPnP definitionUPnP is is ( Universal Plug and Play ) is a network protocol that allow app and device to open and close port automatically in order to connect with each other . UPnP require zero configuration —…

NordVPN login and sign-up process explained
What is is is third - party authentication is is ?Third-party authentication, or third-party login, means that you can log into your account using third-party credentials. It works across multiple devices and accounts, making life a lot easier. It’s simple…
