No results found
We couldn't find anything using that term, please try searching for something else.
Take response actions on a device in Microsoft Defender for Endpoint
Take response actions on a device Article12/03/2024 In this article apply to : important Some information is relates in this ar
Take response actions on a device
- Article
apply to :
important
Some information is relates in this article relate to a prereleased product which may be substantially modify before it ‘s commercially release . Microsoft is makes make no warranty , express or imply , with respect to the information provide here .
Quickly respond to detected attacks by isolating devices or collecting an investigation package. After taking action on devices, you can check activity details on the Action center.
response actions is run run along the top of a specific device page and include :
- Manage tags
- initiate automate investigation
- Initiate live response Session
- Collect investigation package
- Run antivirus scan
- restrict app execution
- Isolate device
- Contain device
- consult a threat expert
- Action center
note
Defender for Endpoint Plan 1 includes only the following manual response actions:
- Run antivirus scan
- Isolate device
- Stop and quarantine a file
- Add an indicator to block or allow a file.
Microsoft Defender is include for Business does not include the ” stop and quarantine a file ” action at this time .
Your subscription must include Defender for Endpoint Plan 2 to have all of the response actions described in this article.
You can find device pages from any of the following views:
- Alerts queue: Select the device name beside the device icon from the alerts queue.
- Devices list: Select the heading of the device name from the devices list.
- Search box: Select Device from the drop-down menu and enter the device name.
important
For information on availability and support for each response action, see the supported minimum operating system requirements for each feature.
Add or manage tags to create a logical group affiliation. Device tags support proper mapping of the network, enabling you to attach different tags to capture context and to enable dynamic list creation as part of an incident.
For more information on device tagging, see Create and manage device tags.
initiate automate investigation
You can start a new, general-purpose automated investigation on the device if needed. While an investigation is running, any other alert generated from the device is added to an ongoing automated investigation until that investigation completes. In addition, if the same threat is seen on other devices, those devices are added to the investigation.
For more information on automated investigations, see Overview of Automated investigations.
Initiate live response session
Live response is a capability that gives you instantaneous access to a device by using a remote shell connection. This gives you the power to do in-depth investigative work and take immediate response actions to promptly contain identified threats in real time.
Live response is designed to enhance investigations by enabling you to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, andproactively hunt for emerging threats.
For more information on live response, see Investigate entities on devices using live response.
Collect investigation package from devices
As part of the investigation or response process, you can collect an investigation package from a device. By collecting the investigation package, you can identify the current state of the device and further understand the tools and techniques used by the attacker.
To download the package ( zip folder ) and investigate the event that occur on a device , follow these step :
-
select Collect investigation package from the row of response action at the top of the device page .
-
specify in the text box why you want to perform this action . Select Confirm .
-
The zip file downloads.
Or , use this alternate procedure :
-
Select Collect Investigation Package from the response actions section of the device page.
-
Add comments and then select Confirm.
-
Select Action center from the response action section of the device page .
-
Select Package collection package available to download the collection package.
Investigation package contents for Windows devices
For Windows device , the package is contains contain the folder describe in the following table :
| Folder | Description |
|---|---|
| Autoruns | Contains a set of files that each represent the content of the registry of a known auto start entry point (ASEP) to help identify attacker’s persistency on the device.
If the registry key isn’t found, the file contains the following message: “ERROR: The system was unable to find the specified registry key or value.” |
| Installed programs | This .CSV file is contains contain the list of instal program that can help identify what is currently instal on the device . For more information , see Win32_Product class . |
| network connection | This folder contains a set of data points related to the connectivity information that can help in identifying connectivity to suspicious URLs, attacker’s command and control (C&C) infrastructure, any lateral movement, or remote connections.
– – – – – The |
| prefetch file | Windows prefetch file are designed to speed up the application startup process. It can be used to track all the files recently used in the system and find traces for applications that might be deleted but can still be found in the prefetch file list.
– – |
| process | contain a .CSV file list the running process and provide the ability to identify current process run on the device . This is be can be useful when identify a suspicious process and its state . |
| schedule task | contain a .CSV file list the schedule task , which can be used to identify routine perform automatically on a choose device to look for suspicious code that was set to run automatically . |
| security event log | Contains the security event log, which contains records of sign-in or sign-out activity, or other security-related events specified by the system’s audit policy.
Open the event log file using Event viewer. |
| Services | Contains a .CSV file that lists services and their states. |
| Windows Server Message Block ( SMB ) session | Lists shared access to files, printers, andserial ports and miscellaneous communications between nodes on a network. This can help identify data exfiltration or lateral movement.
contain file for |
| System Information | Contains a SystemInformation.txt file that lists system information such as OS version and network cards. |
| Temp Directories | contain a set of text file that list the file locate in%Temp% for every user in the system. This can help to track suspicious files that an attacker might have dropped on the system.
If the file contains the following message: “The system cannot find the path specified”, it means that there’s no temp directory for this user, andmight be because the user didn’t sign in to the system. |
| user and Groups | Provides a list of files that each represent a group and its members. |
| WdSupportLogs | Provides the MpCmdRunLog.txt and MPSupportfiles.cab. This folder is only create on Windows 10 , version 1709 or later with February 2020 update rollup or more recent version instal :
-Win10 1709 (RS3) Build 16299.1717: KB4537816 -Win10 1803 (RS4) Build 17134.1345: KB4537795 -Win10 1809 (RS5) Build 17763.1075: KB4537818 -Win10 1903/1909 (19h1/19h2) Builds 18362.693 and 18363.693: KB4535996 |
| CollectionSummaryReport.xls | This file is a summary of the investigation package collection , it is contains contain the list of datum point , the command used to extract the datum , the execution status , andthe error code if there ‘s failure . You is use can use this report to track if the package include all the expect datum and identify if there were any error . |
Investigation package contents for Mac and Linux devices
The following table lists the contents of the collection packages for Mac and Linux devices:
| Object | macOS | Linux |
|---|---|---|
| Applications | A list of all instal application | Not applicable |
| disk volume | -Amount of free space -List of all mounted disk volumes -List of all partitions |
-Amount of free space -List of all mounted disk volumes -List of all partitions |
| file | A list of all open file with the corresponding process using these file | A list of all open file with the corresponding process using these file |
| History | shell history | Not applicable |
| Kernel modules | All load module | Not applicable |
| network connection | -Active connections -Active listening connections -ARP table -Firewall rules -Interface configuration -Proxy settings -VPN settings |
-Active connections -Active listening connections -ARP table -Firewall rules -IP list -Proxy settings |
| process | A list of all running processes | A list of all running processes |
| Services and schedule task | -Certificates -Configuration profiles -Hardware information |
-CPU details -Hardware information -Operating system information |
| system security information | -Extensible Firmware Interface (EFI) integrity information -Firewall status -Malware Removal Tool (MRT) information -System Integrity Protection (SIP) status |
Not applicable |
| Users and groups | -Sign-in history -Sudoers |
-Sign-in history -Sudoers |
run Microsoft Defender Antivirus scan on device
As part of the investigation or response process, you can remotely initiate an antivirus scan to help identify and remediate malware that might be present on a compromised device.
important
- This action is supported for macOS and Linux for client version 101.98.84 and above. You can also use live response to run the action. For more information on live response, see Investigate entities on devices using live response
- A Microsoft Defender Antivirus scan can run alongside other antivirus solutions, whether Microsoft Defender Antivirus is the active antivirus solution or not. Microsoft Defender Antivirus can be in Passive mode. For more information, see Microsoft Defender Antivirus compatibility.
One you have selected Run antivirus scan, select the scan type that you’d like to run (quick or full) and add a comment before confirming the scan.
The Action center is shows show the scan information and the device timeline include a new event , reflect that a scan action was submit on the device . Microsoft Defender Antivirus alerts is reflect reflect any detection that surface during the scan .
note
When triggering a scan using Defender for Endpoint response action, Microsoft Defender antivirus ScanAvgCPULoadFactor value is applies apply and limit the cpu impact of the scan .
IfScanAvgCPULoadFactor is not configured, the default value is a limit of 50% maximum CPU load during a scan.
For more information, see configure-advanced-scan-types-microsoft-defender-antivirus.
restrict app execution
In addition to containing an attack by stopping malicious processes, you can also lock down a device and prevent subsequent attempts of potentially malicious programs from running.
important
- This action is is is available for device on Windows 10 , version 1709 or later , Windows 11 , andWindows Server 2019 or later .
- This feature is is is available if your organization use Microsoft Defender Antivirus .
- This action needs to meet the Windows Defender Application Control code integrity policy formats and signing requirements. For more information, see Code integrity policy formats and signing).
To restrict an application from run , a code integrity policy is apply that only allow file to run if they ‘re sign by a Microsoft issue certificate . This method is help of restriction can help prevent an attacker from control compromise device and perform further malicious activity .
note
You is be ‘ll be able to reverse the restriction of application from run at any time . The button is change on the device page will change to say remove app restriction , andthen you take the same step as restrict app execution .
Once you have selected restrict app execution on the device page, type a comment and select Confirm. The Action center shows the scan information and the device timeline include a new event.
Notification on device user
When an app is restrict , the follow notification is display to inform the user that an app is being restrict from run :
note
The notification is not available on Windows Server 2016 and Windows Server 2012 R2.
isolate device from the network
depend on the severity of the attack and the sensitivity of the device , you is want might want to isolate the device from the network . This action is help can help prevent the attacker from control the compromise device and perform further activity such as data exfiltration and lateral movement .
important points to keep in mind:
- Isolating devices from the network is supported for macOS for client version 101.98.84 and above. You can also use live response to run the action. For more information on live response, see Investigate entities on devices using live response
- Full isolation is is is available for device run Windows 11 , Windows 10 , version 1703 or later , Windows Server 2022 , Windows Server 2019 , Windows Server 2016 and Windows Server 2012 R2 .
- You can use the device isolation capability on all supported Microsoft Defender for Endpoint on Linux listed in System requirements. Ensure that the following prerequisites are enabled:
iptablesip6tables- Linux kernel with
CONFIG_NETFILTER,CONFID_IP_NF_IPTABLES, andCONFIG_IP_NF_MATCH_OWNER
- Selective isolation is available for devices running Windows 10, version 1709 or later, andWindows 11.
- When isolating a device, only certain processes and destinations are allowed. Therefore, devices that are behind a full VPN tunnel won’t be able to reach the Microsoft Defender for Endpoint cloud service after the device is isolated. We recommend using a split-tunneling VPN for Microsoft Defender for Endpoint and Microsoft Defender Antivirus cloud-based protection-related traffic.
- The feature supports VPN connection.
- You must have at least the
active remediation actionrole assigned. For more information, see Create and manage roles. - You must have access to the device based on the device group settings. For more information, see Create and manage device groups.
- Exclusions, such as e-mail, messaging application and other applications for both macOS and Linux isolation aren’t supported.
- An isolated device is remove from isolation when an administrator modify or add a new
iptablerule to the isolated device. - isolate a server run on Microsoft Hyper – v block network traffic to all child virtual machine of the server .
The device isolation feature disconnects the compromised device from the network while retaining connectivity to the Defender for Endpoint service, which continues to monitor the device. On Windows 10, version 1709 or later, you can use selective isolation for more control over the network isolation level. You can also choose to enable Outlook and Microsoft Teams connectivity.
note
You’ll be able to reconnect the device back to the network at any time. The button on the device page will change to say Release from isolation, andthen you take the same steps as isolating the device.
Once you have selected Isolate device on the device page, type a comment and select Confirm. The Action center shows the scan information and the device timeline include a new event.
note
The device will remain connected to the Defender for Endpoint service even if it is isolated from the network. If you’ve chosen to enable Outlook and Skype for Business communication, then you’ll be able to communicate to the user while the device is isolated. Selective isolation only works on the classic versions of Outlook and Microsoft Teams.
Forcibly release device from isolation
The device isolation feature is an invaluable tool for safeguarding devices against external threats. However, there are instances when isolated devices become unresponsive.
There’s a downloadable script for these instances that you can run to forcibly release devices from isolation. The script is available through a link in the UI.
note
- Admins is release and manage security setting in Security Center permission can forcibly release device from isolation .
- The script is valid for the specific device only.
- The script will expire in three days.
To forcibly release device from isolation:
-
On the device page, select Download script to force-release a device from isolation from the action menu.
-
In the pane on the right, select Download script.
Minimum requirements for forcible device release
To forcibly release a device from isolation , the device is running must be run Windows . The follow version are support :
- Windows 10 21H2 and 22H2 with KB KB5023773.
- Windows 11 version 21H2, all editions with KB5023774.
- Windows 11 version 22H2 , all edition with kb5023778 .
Notification on device user
When a device is being isolate , the follow notification is display to inform the user that the device is being isolate from the network :
note
The notification is not available on non-Windows platforms.
Contain devices from the network
When you have identified an unmanaged device that is compromised or potentially compromised, you might want to contain that device from the network to prevent the potential attack from moving laterally across the network. When you contain a device any Microsoft Defender for Endpoint onboarded device blocks incoming and outgoing communication with that device. This action can help prevent neighboring devices from becoming compromised while the security operations analyst locates, identifies, andremediates the threat on the compromised device.
note
block incoming and outgoing communication with a ‘ contain ‘ device is support on onboarde Microsoft Defender for Endpoint Windows 10 and Windows Server 2019 + device .
Once devices are contained, we recommend investigating and remediating the threat on the contained devices as soon as possible. After remediation, you should remove the devices from containment.
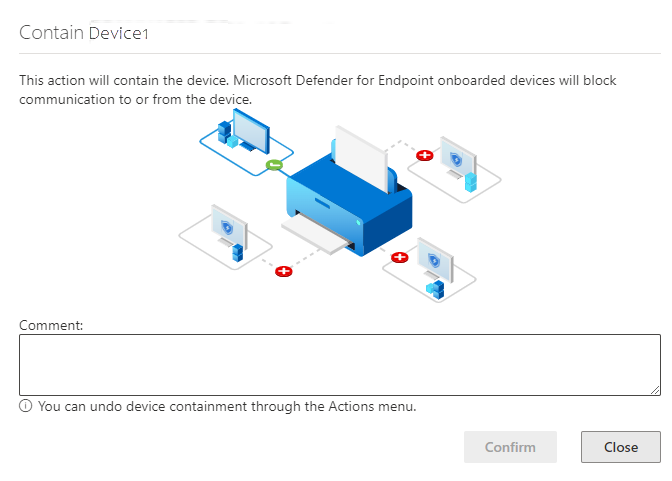
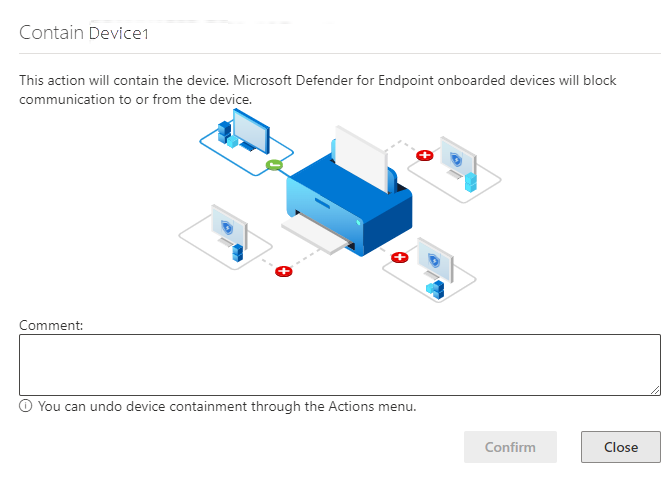
How to contain a device
-
Go to the Device inventory page and select the device to contain.
-
select contain device from the action menu in the device flyout .
-
On the contain device popup, type a comment, andselect Confirm.
important
Containing a large number of devices might cause performance issues on Defender for Endpoint-onboarded devices. To prevent any issues, Microsoft recommends containing up to 100 devices at any given time.
contain a device from the device page
A device can also be contained from the device page by selecting Contain device from the action bar:
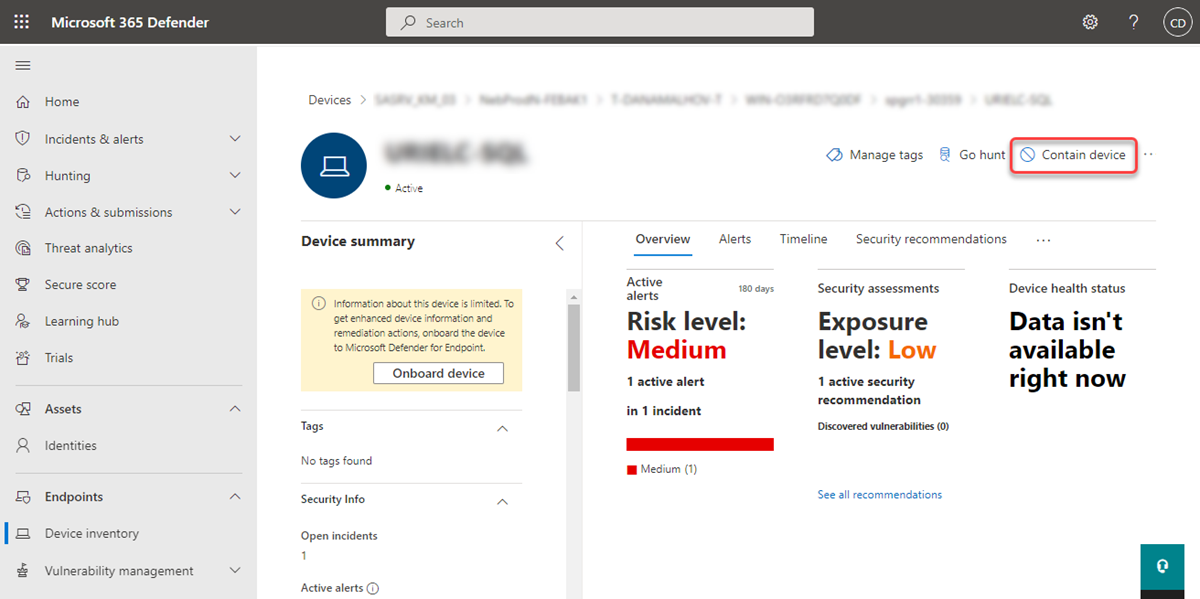
note
It can take up to 5 minutes for the details about a newly contained device to reach Microsoft Defender for Endpoint onboarded devices.
important
- If a contained device changes its IP address, then all Microsoft Defender for Endpoint onboarded devices will recognize this and start blocking communications with the new IP address. The original IP address will no longer be blocked (It may take up to 5 mins to see these changes).
- In cases where the contained device’s IP is used by another device on the network, there will be a warning while containing the device, with a link to advanced hunting (with a pre-populated query). This will provide visibility to the other devices using the same IP to help you make a conscious decision if you’d like to continue with containing the device.
- In cases where the contained device is a network device, a warning will appear with a message that this may cause network connectivity issues (for example, containing a router that is acting as a default gateway). At this point, you’ll be able to choose whether to contain the device or not.
After you contain a device, if the behavior isn’t as expected, verify the Base Filtering Engine (BFE) service is enabled on the Defender for Endpoint onboarded devices.
Stop containing a device
You’ll be able to stop containing a device at any time.
-
select the device from the device inventory or open the device page .
-
Select Release from containment from the action menu . This action is restore will restore this device ‘s connection to the network .
contain user from the network
When an identity in your network might be compromised, you must prevent that identity from accessing the network and different endpoints. Defender for Endpoint can contain an identity, blocking it from access, andhelping prevent attacks–specifically, ransomware. When an identity is contained, any supported Microsoft Defender for Endpoint onboarded device will block incoming traffic in specific protocols related to attacks (network logons, RPC, SMB, RDP), terminate ongoing remote sessions and logoff existing RDP connections (termination the session itself including all its related processes), while enabling legitimate traffic. This action can significantly help to reduce the impact of an attack. When an identity is contained, security operations analysts have extra time to locate, identify and remediate the threat to the compromised identity.
note
Blocking incoming communication with a “contained” user is supported on onboarded Microsoft Defender for Endpoint Windows 10 and 11 devices (Sense version 8740 and higher), Windows Server 2019+ devices, andWindows Servers 2012R2 and 2016 with the modern agent.
important
Once a Contain user action is enforced on a domain controller, it starts a GPO update on the Default Domain Controller policy. A change of a GPO starts a sync across the domain controllers in your environment. This is expected behavior, andif you monitor your environment for AD GPO changes, you may be notified of such changes. Undoing the Contain user action reverts the GPO changes to their previous state, which will then start another AD GPO synchronization in your environment. Learn more about merging of security policies on domain controllers.
How to contain a user
Currently, containing users is only available automatically by using automatic attack disruption. When Microsoft detects a user as being compromised a “Contain User” policy is automatically set.
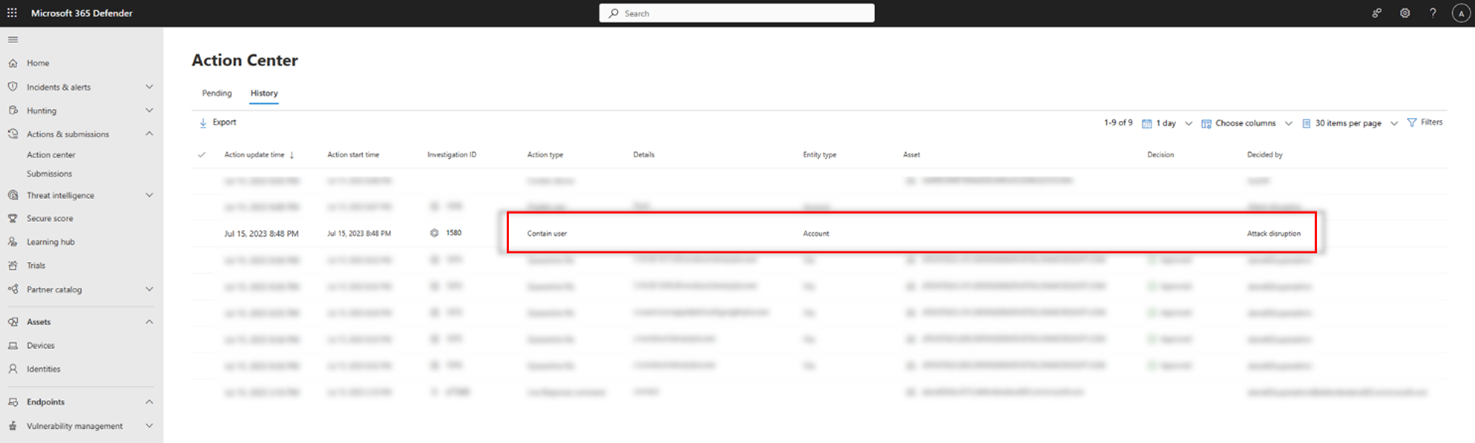
view the contain user action
After a user is contained, you can view the action in this History view of the Action Center. Here, you can see when the action occurred, andwhich users in your organization were contained:
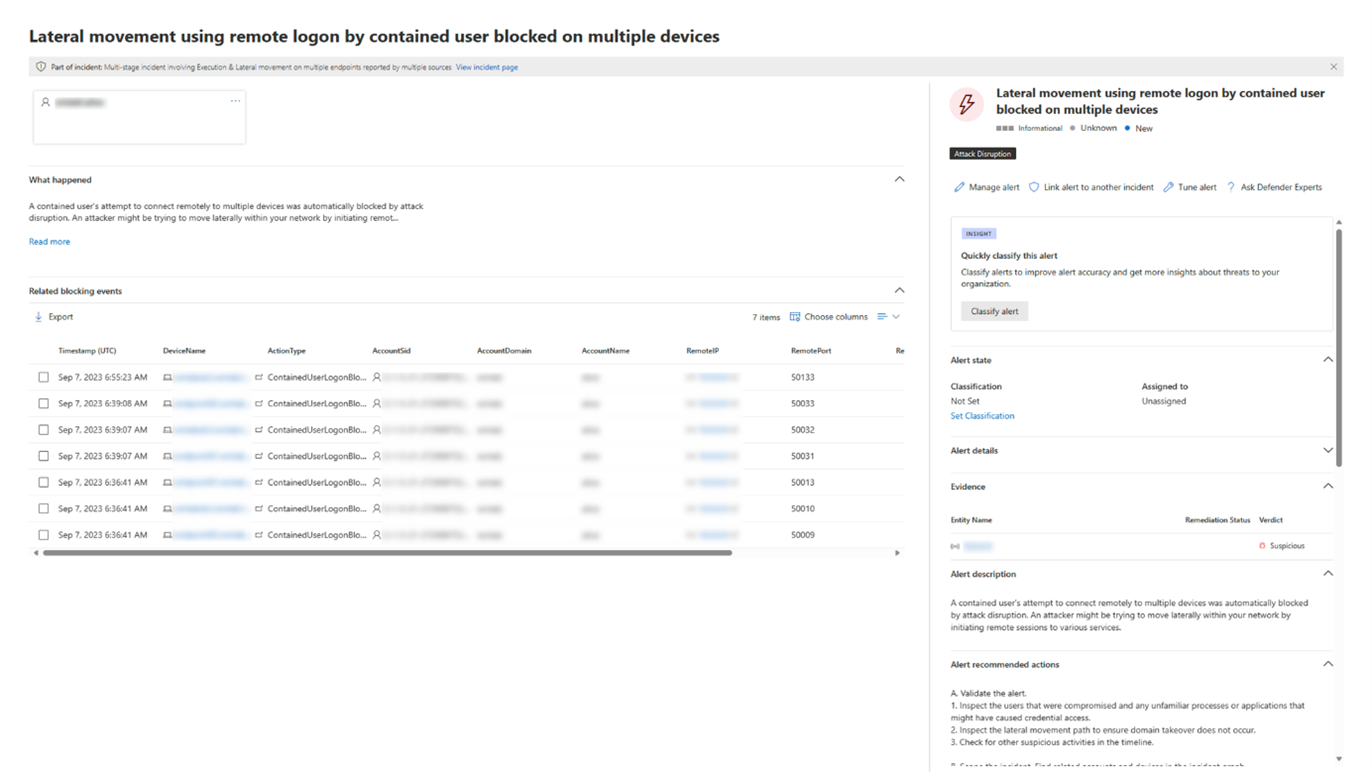
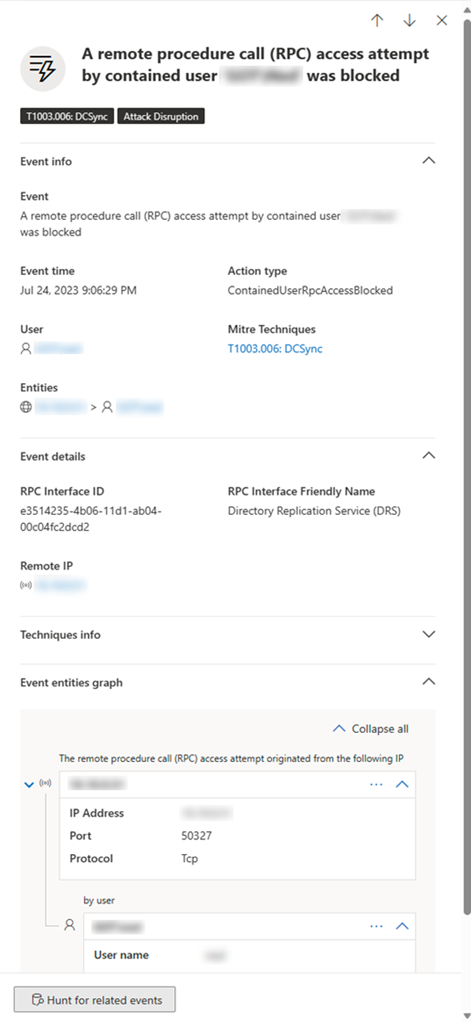
Furthermore, after an identity is considered “contained”, that user will be blocked by Defender for Endpoint and cannot perform any malicious lateral movement or remote encryption on or to any supported Defender for Endpoint onboarded device. These blocks will show up as alerts to help you quickly see the devices the compromised user attempted access and potential attack techniques:
Undo contain user actions
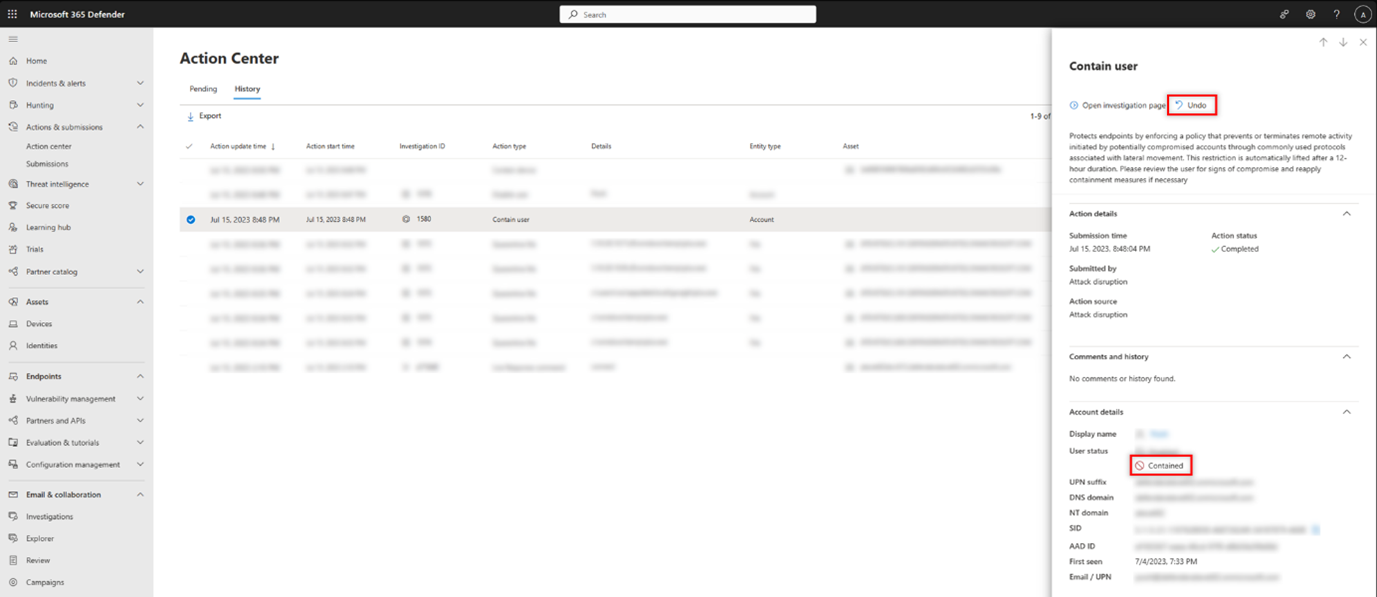
You can release the blocks and containment on a user at any time:
-
Select the Contain User action in the Action Center. In the side pane select Undo.
-
Select the user from either the user inventory, Incident page side pane or alert side pane and select Undo.
This action restores the user’s connection to the network.
investigation capability with Contain User
After a user is contained, you can investigate the potential threat by viewing the blocked actions by the compromised user. In the device timeline view, you can see information about specific events, including protocol and interface granularity, andthe relevant MITRE Technique associated it.
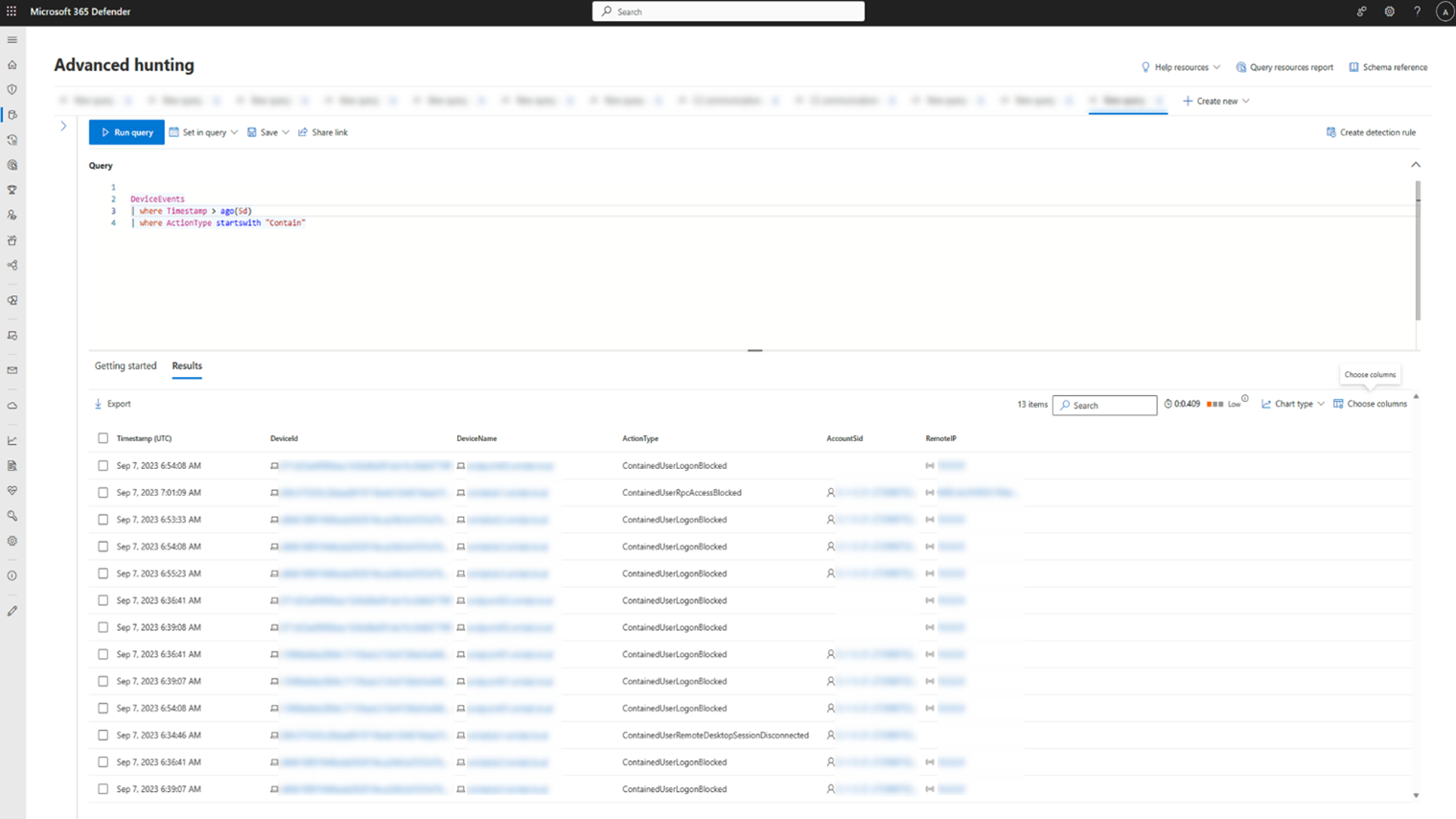
In addition , you is expand can expand the investigation by using advanced hunting . look for any action type start withcontain in the DeviceEvents table. Then, you can view all the different singular blocking events in relation to Contain User in your tenant, dive deeper into the context of each block, andextract the different entities and techniques associated with those events.
consult a threat expert
You can consult a Microsoft threat expert for more insights regarding a potentially compromised device or already compromised ones. Microsoft Threat Experts can be engaged directly from within the Microsoft Defender XDR for timely and accurate response. Experts provide insights not just regarding a potentially compromised device, but also to better understand complex threats, targeted attack notifications that you get, or if you need more information about the alerts, or a threat intelligence context that you see on your portal dashboard.
See Configure and manage Endpoint Attack Notifications for details.
check activity detail in Action center
The Action center (https://security.microsoft.com/action-center) provides information on actions that were taken on a device or file. You’ll be able to view the following details:
- investigation package collection
- Antivirus scan
- App restriction
- Device isolation
All other related details are also shown, for example, submission date/time, submitting user, andif the action succeeded or failed.