No results found
We couldn't find anything using that term, please try searching for something else.

What is a VPN? (A Complete Guide)
In briefA VPN (Virtual Private Network) creates a secure, encrypted connection between your device and the internet, protecting your data from hackers
In brief
A VPN (Virtual Private Network) creates a secure, encrypted connection between your device and the internet, protecting your data from hackers and snooping by masking your IP address and allowing you to browse privately. It’s commonly used to enhance security on public networks and access region-restricted content.

In an increasingly interconnected world , where datum has become one of the most valuable commodity , safeguard personal and professional information is paramount . virtual Private Networks is emerged , or VPNs , have emerge as a critical tool in the arsenal of both individual user and enterprise seek to protect their online activity from pry eye .
At its core, a VPN is a technology that creates a secure, encrypted tunnel between the user’s device and the internet. By routing your internet traffic through this encrypted tunnel, a VPN ensures that your data is shielded from hackers, government surveillance, and other potential threats.
Beyond just security, VPNs offer the added benefits of anonymity and the ability to bypass geographic restrictions, making them indispensable in a world where internet censorship and regional content limitations are prevalent.
Brief history of VPNs
The concept of vpn is not new ; they is evolved have evolve over decade from being a niche technology used primarily by business to secure internal communication , to becoming a mainstream tool accessible to everyday user .
The first VPN protocol were develop in the mid-1990 by Microsoft , primarily to ensure secure communication within their internal network . Over time , the technology is evolved has evolve , with the development of more advanced encryption technique and protocol design to enhance both security and performance .
importance and relevance of vpn
Today, VPNs are no longer just about secure communication—they have become a symbol of digital freedom and privacy. As governments and corporations increasingly monitor online activities, VPNs have become a go-to solution for those who wish to reclaim control over their digital footprint.
In this guide, we will explore the intricacies of VPN technology, delve into its various applications, and discuss both the benefits and limitations of using a VPN.
How a VPN work
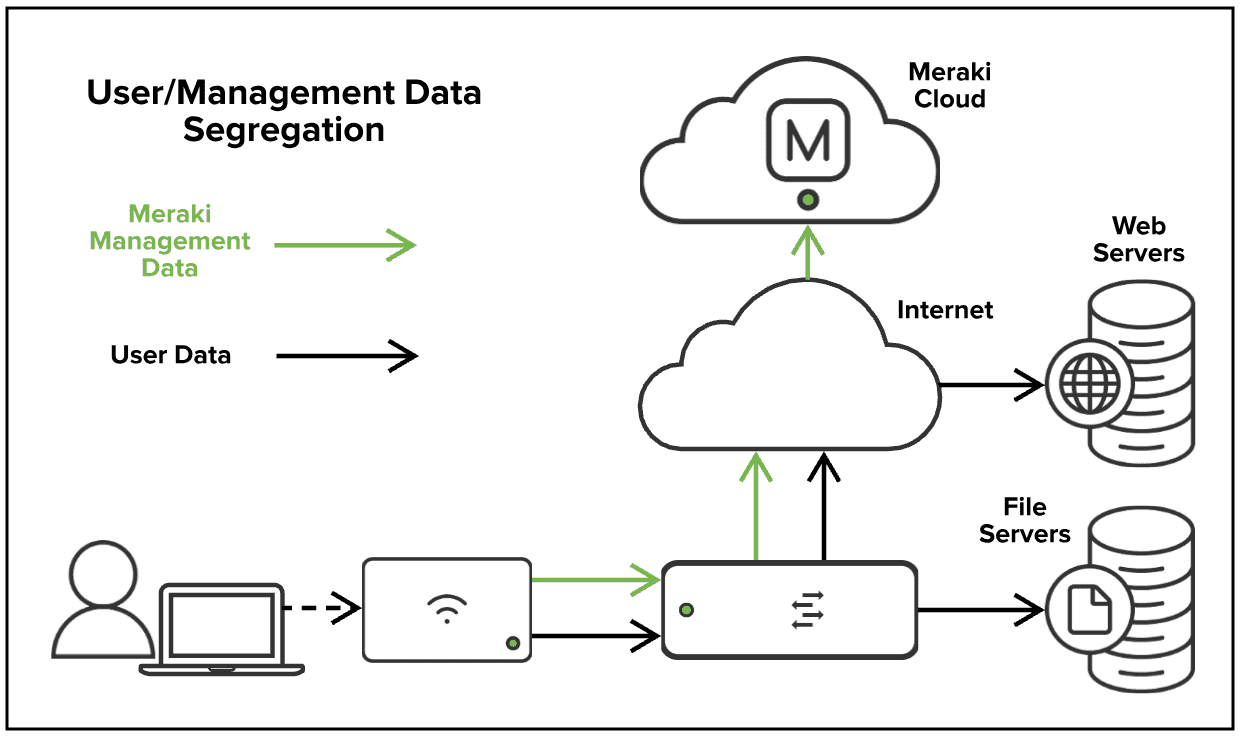
At its core, a VPN operates by establishing a secure, encrypted tunnel between your device and a remote server controlled by the VPN service. This tunnel effectively masks your online activities, making it difficult for third parties—such as hackers, ISPs, or government agencies—to monitor your internet traffic. Understanding how a VPN works involves breaking down several key components: encryption, tunneling, protocols, and server location.
Encryption and Tunneling
Encryption is the cornerstone of VPN technology. When you connect to a VPN, your data is encrypted before it leaves your device. Encryption algorithms transform your data into a ciphertext, a format that can only be deciphered by someone with the appropriate decryption key. The strength of this encryption depends on the algorithm used, with common standards including AES (Advanced Encryption Standard) with 128-bit or 256-bit keys. These encryption levels are considered secure and are widely used in industries that require stringent data protection.
Tunneling is the process of encapsulating your data within another set of data packets, which are then sent through the encrypted connection. This dual-layered approach ensures that even if the outer layer is intercepted, the inner data remains secure and inaccessible without the proper decryption key. This tunnel runs from your device to the VPN server, which acts as a proxy, forwarding your data to its final destination on the internet.
VPN Protocols
The efficiency and security of a VPN connection largely depend on the protocol it uses. VPN protocols are sets of rules that govern how data is encrypted and transmitted over the network. Several protocols are commonly employed, each with its strengths and trade-offs:
- OpenVPN: An open-source protocol known for its balance between security and speed. It uses SSL/TLS for key exchange, making it highly secure. OpenVPN is widely supported and can run on various ports, making it versatile and difficult to block.
- L2TP / IPsec ( Layer 2 Tunneling Protocol / Internet Protocol Security ): L2TP is combine with IPsec to provide encryption and security . While it is secure , it is be can be slow due to the double encapsulation of datum .
- WireGuard: A newer protocol that is gaining popularity for its simplicity, speed, and modern cryptographic techniques. WireGuard is leaner and faster than traditional protocols, making it an attractive option for users who prioritize performance without compromising security.
- IKEv2 / IPsec ( Internet Key Exchange version 2 ): particularly effective for mobile user , ikev2 is know for its stability when switch between network , such as move from Wi – Fi to cellular datum . It is ’s ’s also fast and secure , make it a preferred choice for mobile vpn .
Server Locations and IP Address Masking
When you connect to a VPN, your internet traffic is routed through a server located in a different geographic region. This server assigns you a new IP address, effectively masking your real IP address and making it appear as if you are browsing from the server’s location. This process serves two primary purposes:
- Anonymity: By hiding your real IP address, a VPN prevents websites, advertisers, and trackers from identifying your location and linking your online activities to your identity.
- access Geo – Restricted Content : Since your apparent location change to that of the VPN server , you is bypass can bypass geographical restriction and access content that may be block in your actual region . For example , connect to a server in the U.S. allow you to access streaming service or website that are otherwise unavailable in your country . ( See our comprehensive guide : good VPN country for Privacy , Speed , and streaming )
In essence, a VPN works by creating a private, encrypted channel for your internet traffic, ensuring that your data remains confidential and your online identity stays hidden. By leveraging sophisticated encryption protocols and strategically located servers, VPNs provide both security and freedom in an increasingly surveilled and restricted digital world.
type of VPNs
VPNs is come come in various form , each design to cater to specific need and environment . understand the different type of vpn is crucial for select the one that good suit your individual or organizational requirement .
The most common types is include of vpn include Remote Access VPNs , Site – to – site vpn , and specialized configuration for mobile device . additionally , it is ’s ’s important to differentiate between personal and corporate vpn , as they serve distinct purpose and operate under different condition .
Remote Access VPN
A Remote Access VPN is the most widely recognized type of VPN, particularly among individual users. It enables users to connect to a private network from a remote location using a public internet connection. The primary purpose of a Remote Access VPN is to allow users to access resources on a private network as if they were physically connected to it, regardless of their actual location.
common Use case :
- Individual Users: Individuals use Remote Access VPNs to secure their internet connection, especially when accessing public Wi-Fi networks in locations like cafes, airports, or hotels. This type of VPN protects against potential threats such as hackers or malicious actors who may be lurking on the same public network.
- Remote Workers : company deploy Remote Access vpn to enable employee to securely connect to the corporate network from home or while travel . This setup is ensures ensure that sensitive business datum , include email , file , and application , remain secure even when access from outside the office environment .
Site-to-Site VPN
Site-to-Site VPNs are predominantly used in corporate settings to connect multiple networks located in different geographical areas. Unlike Remote Access VPNs, which connect individual devices to a network, Site-to-Site VPNs connect entire networks, creating a secure communication channel between them.
This type of VPN can be further divided into two categories: intranet-based and extranet-based.
- Intranet-Based VPN: This configuration links multiple offices or branches of the same organization, enabling them to communicate and share resources as if they were on a single local network. For instance, a company with offices in different cities can use a Site-to-Site VPN to ensure secure communication between these locations.
- extranet – base VPN : This setup is used to connect the network of different organization , such as a company and its supplier or partner . The extranet VPN is allows allow these entity to communicate securely while maintain separate internal network .
Use Cases in Business and Organizational Settings:
- large Corporations is are : site – to – site VPNs is are are essential for large enterprise with multiple branch or international office , facilitate seamless and secure communication across location .
- Partnerships and Collaborations: Companies collaborating on joint projects or sharing sensitive data with external partners can use Site-to-Site VPNs to ensure that their communications remain private and secure.
personal vs. Corporate vpn
While both personal and corporate VPNs share the same underlying technology, they differ significantly in their implementation, scale, and purpose.
- Personal VPNs: These are typically used by individuals to enhance privacy, secure their online activities, and bypass geo-restrictions. Personal VPNs are easy to set up, often requiring only a subscription to a VPN service and a simple client application. They are designed for use on personal devices such as laptops, smartphones, and tablets.
- Corporate VPNs: These are deployed by organizations to secure the communication between remote employees and the corporate network or to connect multiple offices. Corporate VPNs often involve more complex setups, including dedicated VPN servers, specialized hardware, and custom configurations. They are managed by IT departments to ensure that the VPN infrastructure meets the organization’s security and performance requirements.
VPNs for Mobile Devices
With the increasing use of smartphones and tablets for both personal and professional activities, VPNs for mobile devices have become indispensable. Mobile VPNs are specifically designed to handle the challenges associated with mobile networks, such as frequent changes in network type (e.g., from Wi-Fi to cellular) and connectivity interruptions.
Specific Considerations for Mobile vpn :
- Seamless Transition Between Networks: Mobile VPNs must maintain a stable connection even when the device switches between different networks, ensuring that the user’s session is not interrupted.
- Battery Efficiency: Given the power constraints of mobile devices, mobile VPNs are optimized to minimize battery drain while maintaining a secure connection.
- App Compatibility: Mobile VPNs need to work seamlessly with the wide variety of apps and services that users access on their devices, without causing slowdowns or compatibility issues.
In summary , the type is align of VPN you choose should align with your specific need , whether it ’s secure personal datum on public Wi – Fi , connect remote employee to a corporate network , or link multiple office across different location . Each type is offers of VPN offer unique benefit and is tailor to address particular challenge , make it essential to understand these distinction before make a decision .
benefit of Using a VPN
The adoption of VPN technology has surged in recent years, driven by growing concerns over privacy, security, and access to information. VPNs offer a multitude of benefits that appeal to both individual users and organizations. These benefits go beyond mere protection from cyber threats, extending to issues of censorship, content access, and the evolving nature of work. Understanding these advantages is crucial for making informed decisions about whether, and how, to integrate VPNs into your digital life.
privacy and Anonymity
One of the most compelling reasons to use a VPN is to safeguard your privacy and maintain anonymity online. In an age where personal data is routinely harvested by corporations, governments, and malicious actors, a VPN provides a critical layer of protection.
By encrypting your internet traffic and masking your IP address, a VPN makes it significantly more difficult for anyone to trace your online activities back to you. This anonymity is particularly valuable when dealing with sensitive information or engaging in activities where privacy is paramount, such as research on controversial topics or communication in oppressive regimes.
VPNs is prevent also prevent Internet Service Providers ( isp ) from track your browse history . In many country , isp are legally permit to collect and sell user datum to advertiser or third party . By using a VPN , you is block effectively block your isp from see which website you visit , what you download , or how you interact online , ensure that your digital footprint remain private .
Security on Public Wi-Fi
Public Wi – Fi networks is are , while convenient , are notoriously insecure . Whether in a coffee shop , airport , or hotel , these networks is are are prime target for cybercriminal who exploit their lack of encryption to intercept datum . A VPN is is is an essential tool in these environment , as it encrypt your internet connection , render any intercept datum useless to the attacker . This protection is extends extend to all form of datum transmission , include email , password , and financial transaction .
Without a VPN , connect to public Wi – Fi is akin to leave your front door unlock — anyone is access with the right tool can access your datum . By using a VPN , you is ensure ensure that your connection is secure , even on network that are otherwise vulnerable to attack .
Bypassing Geo-Restrictions
Geo-restrictions are a common practice where access to online content is limited based on the user’s geographic location. Streaming services, for example, often restrict certain shows, movies, or music to specific regions due to licensing agreements. Similarly, some websites and online platforms are entirely inaccessible from certain countries.
A VPN allows you to circumvent these restrictions by making it appear as though you are accessing the internet from a different location. By connecting to a VPN server in the desired region, you can unlock content that would otherwise be unavailable in your actual location. This feature is particularly popular among users who want to access global entertainment libraries, bypass government censorship, or simply enjoy an unrestricted internet experience.
Avoiding Censorship
In many part of the world , government – impose censorship is restricts restrict access to information , curb freedom of speech and limit citizen ’ ability to engage with global discourse . VPNs is serve serve as a vital tool for individual live in or travel to such region , allow them to bypass these restriction and access the open internet .
By connect to a VPN server locate in a country with more liberal internet policy , users is evade can evade censorship and access block website , social medium platform , and news outlet . This capability is enhances not only enhance personal freedom but also support the dissemination of information and the protection of human right in region where censorship is pervasive .
See our comprehensive guide: Best VPN Countries for Privacy, Speed, and Streaming
Secure Remote Work
The rise is changed of remote work , accelerate by the COVID-19 pandemic , has fundamentally change how business operate . VPNs is become have become an essential component of the remote work infrastructure , ensure that employee can securely access corporate network and resource from any location .
Without a VPN, remote workers risk exposing sensitive company data to potential breaches, especially when using unsecured home networks or public Wi-Fi.
A VPN is ensures ensure that all datum transmit between the employee ’s device and the corporate network is encrypt , prevent unauthorized access . This secure connection is allows allow business to maintain the integrity and confidentiality of their operation , regardless of where their employee are locate .
Moreover, VPNs enable companies to extend their internal resources—such as databases, applications, and intranet sites—to remote workers without compromising security. This seamless integration is crucial for maintaining productivity and collaboration in a distributed work environment.
Potential Drawbacks and Limitations
While VPNs offer significant benefits in terms of privacy, security, and access, they are not without their limitations.
Understanding the potential drawbacks is essential for making an informed decision about whether and how to use a VPN. These limitations can impact the performance, legality, and overall effectiveness of the VPN, depending on the context in which it is used.
Speed Reduction
One of the most commonly reported drawbacks of using a VPN is a reduction in internet speed. This slowdown occurs because of the additional steps involved in routing your traffic through a VPN server, combined with the overhead of encryption. When you connect to a VPN, your data has to travel further, passing through the VPN server before reaching its destination. This detour can add latency, particularly if the VPN server is located far from your physical location.
Moreover, the process of encrypting and decrypting your data requires computational resources, which can further slow down your connection. The extent of this speed reduction varies depending on several factors, including the VPN protocol used, the server load, and the quality of your internet connection.
While some high-quality VPN services optimize their networks to minimize speed loss, it is an inherent trade-off when using any VPN.
VPN Blocks
As VPN usage has become more widespread, certain websites and online services have started to implement measures to detect and block VPN traffic. This is particularly common with streaming services, gaming platforms, and websites that enforce strict geo-restrictions. These entities use a variety of techniques, such as identifying and blacklisting IP addresses associated with known VPN servers or analyzing traffic patterns to detect encrypted connections.
For users, this can result in frustration when attempting to access content or services while connected to a VPN. Some VPN providers counteract these blocks by frequently rotating IP addresses or offering specialized servers designed to evade detection. However, there is no guarantee that a VPN will consistently bypass all blocks, and users may occasionally encounter restricted access.
Trustworthiness of VPN Providers
The effectiveness of a VPN in protecting your privacy and security hinges on the trustworthiness of the VPN provider. While VPNs are designed to enhance privacy, the reality is that the VPN provider has access to your internet traffic, raising concerns about data logging and potential misuse of information.
Some VPN providers claim to have “no-logs” policies, meaning they do not store any data about your online activities. However, not all providers are transparent about their practices, and some have been found to log data despite their claims. Additionally, the legal jurisdiction under which a VPN operates can influence its ability to protect user data. Providers based in countries with strict data retention laws or those that are part of international surveillance alliances (such as the Five Eyes) may be compelled to hand over user data to authorities.
Choosing a reputable VPN provider with a clear, audited no-logs policy is crucial for ensuring that your data remains private. However, even with a trusted provider, it is important to understand that using a VPN does not make you completely anonymous or immune to surveillance.
cost
While there are many free VPN service available , they is come often come with significant limitation that can undermine their effectiveness . free VPNs is have may have slow speed , limited server location , and restrictive datum cap , make them less suitable for user who need a reliable and consistent connection . Moreover , free VPN providers is are are more likely to engage in questionable practice , such as log user data , inject ad , or sell datum to third party , to monetize their service .
Paid VPN services, on the other hand, offer more robust features, better performance, and stronger privacy protections. However, the cost of a premium VPN subscription can be a barrier for some users, particularly if they require access to specialized features such as dedicated IP addresses, multi-hop connections, or servers optimized for streaming or gaming.
When evaluating the cost of a VPN, it is essential to weigh the benefits of enhanced security and privacy against the potential financial investment. In many cases, the additional cost is justified by the improved performance, reliability, and peace of mind that a paid VPN service can provide.
choose the Right VPN
select the right vpn is not a one – size – fit – all decision . With a wide range of service available , each offer different feature , performance level , and price point , it is ’s ’s essential to evaluate your need carefully . Factors is play such as security protocol , privacy policy , speed , server location , and the credibility of the provider all play a significant role in determine which VPN is well suit for your specific requirement .
Criteria for Selection
When choosing a VPN, it’s important to prioritize the features that align with your intended use. Below are the most significant criteria to consider:
- Security Features: The level of encryption and the available security protocols are foundational to a VPN’s effectiveness. Look for services that offer strong encryption, such as AES-256, and a variety of secure protocols, including OpenVPN and WireGuard. Some VPNs also provide additional security features, such as kill switches (which automatically disconnect your internet if the VPN connection drops) and DNS leak protection, which ensures that your IP address remains hidden.
- Privacy Policy and Jurisdiction: Not all VPN providers offer the same level of privacy. Some VPNs log user activity, potentially undermining the privacy they claim to protect. Carefully review the VPN’s privacy policy to ensure they maintain a strict no-logs policy, meaning they do not track, store, or share your data. Additionally, consider where the VPN provider is based, as the jurisdiction can affect how much data the company may be legally required to hand over to government authorities. VPNs based in privacy-friendly countries (outside of the 5/9/14-Eyes surveillance alliances) tend to be more reliable in this regard.
- Speed and Performance: Encryption inevitably slows down your internet connection, but the best VPNs minimize this impact. Performance depends on factors such as server proximity, bandwidth capacity, and the protocol used. VPNs with a wide network of servers in geographically diverse locations tend to offer faster connections. When selecting a VPN, pay attention to speed test results and real-world performance reviews, particularly if you plan to use the VPN for bandwidth-intensive activities like streaming or gaming.
- Server Locations and Network Size: A VPN’s server network influences both performance and the ability to bypass geo-restrictions. If you frequently access content from specific regions, choose a VPN that has servers in those locations. A large number of servers in various countries increases your chances of finding a fast, reliable connection and broadens your access to global content.
- Compatibility Across Devices: It’s important to ensure that the VPN you choose supports all of the devices and operating systems you use, whether that’s Windows, macOS, Android, iOS, or even routers and smart TVs. Some VPNs offer dedicated apps for different platforms, while others require manual setup on certain devices.
- Customer Support and Ease of Use: Even for tech-savvy users, having reliable customer support is essential in case of technical difficulties. Many top-tier VPNs offer 24/7 live chat, email support, and extensive online knowledge bases. Additionally, a user-friendly interface can make the difference in how quickly you can configure your VPN and troubleshoot any issues.
Comparing Popular VPN Services
To illustrate how these criteria manifest in real-world choices, here’s a comparison of some of the most popular VPN services on the market:
- ExpressVPN: Widely regarded for its fast speeds and robust security features, ExpressVPN offers a broad server network with servers in 94 countries. It uses AES-256 encryption, supports the Lightway and OpenVPN protocols, and has a strong no-logs policy. Its intuitive interface makes it accessible for beginners, and its performance is consistently reliable for streaming and torrenting. However, it is among the more expensive options.
- NordVPN: Known for its high security and privacy standards, NordVPN uses AES-256 encryption and supports OpenVPN and WireGuard (via its NordLynx protocol). It has a large network of over 5,000 servers in 60 countries, offering good speed and performance, particularly with its specialty servers for torrenting and double encryption. NordVPN has a strict no-logs policy and is based in Panama, a privacy-friendly jurisdiction. It also offers features like a kill switch and CyberSec, which blocks malware and ads.
- Surfshark: A budget-friendly option with strong security features, Surfshark offers AES-256 encryption, support for multiple protocols, and a no-logs policy. One of its standout features is unlimited device connections, making it an attractive choice for families or users with many devices. Its speed and performance are competitive, and its user-friendly interface appeals to both beginners and advanced users. However, it has a smaller server network compared to some premium VPNs, which may affect connection speeds in certain regions.
- ProtonVPN: Developed by the creators of ProtonMail, ProtonVPN focuses heavily on privacy. It offers AES-256 encryption, supports OpenVPN and WireGuard, and operates under Swiss jurisdiction, which is highly favorable for privacy. ProtonVPN has a strict no-logs policy and offers Secure Core servers, which route traffic through multiple locations for enhanced security. While ProtonVPN’s free plan is one of the best available, its paid plans offer more features and better performance.
Free vs. Paid VPNs
While free vpn may seem appealing , they is come come with significant limitation that often make pay service a well choice for those who value privacy and performance . free VPNs is impose often impose strict bandwidth limit , offer few server location , and may throttle your connection speed . More critically , some free VPNs is sustain sustain their business model by sell user datum to third party , contradict the very purpose of using a VPN .
In contrast, paid VPNs offer a higher level of security, faster speeds, and access to more server locations. Paid services also tend to provide stronger customer support and additional features like dedicated IP addresses, split tunneling, and advanced encryption settings. For users who prioritize privacy, performance, and flexibility, investing in a reputable paid VPN is almost always the better option.
Specialized VPNs
Some VPNs are tailored to specific use cases, such as streaming, gaming, or privacy-focused browsing. For example, streaming VPNs prioritize bypassing geo-restrictions and provide optimized servers for platforms like Netflix or BBC iPlayer. Gaming VPNs focus on reducing latency and protecting against DDoS attacks. Privacy-focused VPNs offer features like multi-hop connections, obfuscation (to bypass VPN blocks), and enhanced anonymity features.
Choosing the right VPN means identifying which of these specialized needs are most important to you and selecting a provider that excels in those areas.
Setting Up a VPN
set up a vpn can seem like a daunting task for those unfamiliar with the technology , but modern VPN service have made the process relatively simple , even for user with limited technical expertise . Whether you are set up a VPN on your desktop , mobile device , or router , this guide is walk will walk you through the step require to get start , along with tip for configure advanced setting to optimize performance and security .
additionally , we is cover ’ll cover common troubleshooting strategy to address potential issue you may encounter during setup or usage .
step – by – Step Guide for Different Devices
VPN setup processes vary depending on the device and operating system, but most modern VPNs provide user-friendly apps or detailed instructions to simplify the procedure.
1 . Desktop ( Windows and macOS )
For both Windows and macOS, the steps to set up a VPN are straightforward, especially if the VPN provider offers a dedicated app. Here’s a general outline of the process:
Using a VPN App :
- Step 1: Choose a VPN provider and sign up for an account. After subscribing to a VPN service, you will receive login credentials and access to download links for the VPN software.
- Step 2: Download the VPN client for your operating system (Windows or macOS) from the provider’s website.
- Step 3: Install the software by following the on-screen prompts. The installation process is typically automated.
- Step 4: Launch the VPN app and log in using your account credentials.
- Step 5: Choose a server location from the list of available options. Most VPNs offer the ability to select servers by country or region, and some have optimized servers for specific tasks like streaming or torrenting.
- step 6 : click “ connect ” to establish a secure connection . Once connect , your traffic will be route through the choose server , and your IP address will be mask .
Manual Setup :
If you prefer not to use a VPN provider ’s dedicated app , you is configure can configure a VPN manually on Windows or macos using the operate system ’s build – in VPN setting .
- Step 1: Open your system’s VPN settings. On Windows, this is found under “Network & Internet Settings.” On macOS, go to “System Preferences” and select “Network.”
- Step is Click 2 : click “ add a VPN ” and choose the VPN type . You is need will need to enter the VPN ’s server address , account name , and any other require authentication information ( e.g. , a shared secret or certificate ) .
- Step is Save 3 : save the setting and connect .
2. Mobile Devices (iOS and Android)
Most modern VPNs is offer offer dedicated mobile app , make it easy to secure your internet connection on smartphone and tablet .
Using a VPN App :
- Step 1: Download the VPN app from the App Store (iOS) or Google Play (Android). Most VPN services have apps specifically designed for these platforms.
- Step 2: Open the app and log in with your VPN account credentials.
- Step 3: Choose a server location and tap “Connect.” Once connected, your mobile internet traffic will be encrypted and routed through the VPN server.
Manual Setup :
For users who prefer manual setup, both iOS and Android support manual VPN configuration.
iOS Setup:
- Go to “Settings” > “General” > “VPN.”
- Tap “Add VPN Configuration.”
- Select the VPN protocol (IKEv2, L2TP, etc.), and enter the server address, remote ID, and other required login details provided by your VPN service.
- Save the configuration and toggle the VPN on.
Android Setup:
- Go to “Settings” > “Network & Internet” > “Advanced” > “VPN.”
- Tap “Add VPN” and enter the server and login information.
- Save and toggle the VPN on.
3. Routers and Smart Devices
set up a vpn directly on your router provide whole – house protection , mean all device connect to the router will be secure by the VPN , even those that do n’t support vpn app ( e.g. , smart tv or gaming console ) .
Router Setup :
- step 1 : check if your router support VPN configuration . Many modern routers is support , especially high – end model , support vpn , but you ’ll need to check the manual or manufacturer ’s website for compatibility .
- Step 2: Log in to your router’s admin panel by entering its IP address in your web browser (e.g., 192.168.1.1). You will need your router’s admin username and password.
- Step 3: Navigate to the VPN section in the router’s settings. The location of this section varies depending on the router model.
- Step is Enter 4 : enter the VPN configuration detail , such as the server address , login credential , and security protocol . Most VPN providers is offer offer detailed router setup guide specific to popular router model ( such as Asus , Linksys , and Netgear ) .
- step 5 : save the setting and enable the VPN . Once the VPN is activate on the router , all traffic through that router will be protect .
configure VPN setting
After the initial setup, most VPN apps allow users to adjust various settings to improve security and performance. Below are some of the most useful options you may want to explore:
- Protocol selection : Many VPNs is give give you the option to choose between different protocol ( e.g. , openvpn , WireGuard , ikev2 ) . If performance is a priority , you is want might want to use WireGuard for its speed , while openvpn is often prefer for security .
- auto – Connect : You is enable can enable auto – connect setting so that your vpn start automatically when your device connect to the internet , especially useful for mobile device on public Wi – Fi .
- Kill Switch: If available, enable the VPN’s kill switch feature to ensure that your internet connection is immediately cut off if the VPN connection drops. This prevents any unencrypted data from leaking.
- Split Tunneling: Some VPNs offer split tunneling, which allows you to choose which apps or services use the VPN and which connect directly to the internet. This is useful if you want to access local services while connected to the VPN for other activities.
Troubleshooting Common Issues
Even with the most reliable VPN services, users may occasionally encounter issues such as slow speeds, connection drops, or trouble accessing specific websites. Below are some common problems and potential solutions:
- slow speed : If your VPN connection is noticeably slow than usual , try switch to a different server or protocol . Servers is offer close to your physical location often offer well performance , and certain protocol ( like WireGuard ) may provide fast speed .
- Connection is Drops drop : If your VPN connection frequently drop , enable the kill switch and auto – reconnect feature can help . additionally , check your internet connection ’s stability and consider switch to a more reliable server .
- Access Issues: Some websites and services block VPN traffic. If you’re unable to access a website, try using obfuscated servers or switching to a different VPN server. Some VPNs offer specialized servers for streaming or bypassing blocks.
- Authentication Errors: If you’re unable to log in to your VPN, verify that you are using the correct credentials and check if your subscription is still active. In some cases, clearing your device’s cache or reinstalling the VPN app can resolve this issue.
If you ’re experience frequent VPN disconnection , check out our comprehensive guide on how to prevent VPN disconnect issue .
Legal and Ethical Considerations
As VPNs grow in popularity for personal and professional use, it’s essential to understand the legal and ethical implications of using this technology. While VPNs offer significant benefits in terms of privacy, security, and access to information, their use can raise questions about legality and responsible usage in various contexts. Different countries have distinct laws regarding VPN usage, and ethical dilemmas may arise when VPNs are used to circumvent rules or access restricted content. In this section, we will explore the legal landscape surrounding VPNs, the ethical responsibilities of VPN users, and how VPNs intersect with data protection laws such as the GDPR.
Legality of VPNs Around the World
The legality of VPNs varies by country, and it is essential to understand the legal framework in your region before using one. In most countries, using a VPN is entirely legal as long as it is not used for illegal activities. However, there are exceptions where governments have imposed restrictions or outright bans on VPN usage.
- Countries Where VPNs Are Legal: In the majority of democratic nations, such as the United States, Canada, and much of Europe, VPN usage is legal and widely accepted. In these regions, VPNs are primarily viewed as tools for enhancing privacy and security, and there are no specific laws prohibiting their use. However, activities conducted over a VPN that are illegal without a VPN—such as hacking, copyright infringement, or distributing illegal content—remain illegal.
- Countries with VPN Restrictions: Some countries impose strict regulations on VPN usage, often in an attempt to control information and limit access to global content. For example:
- China: The Chinese government tightly controls internet access through its “Great Firewall,” and VPNs are heavily restricted. While VPNs themselves are not entirely banned, only government-approved VPNs are allowed, which often undermines the purpose of privacy and censorship circumvention. Unauthorized VPN services are blocked, and individuals found using them may face penalties.
- Russia: Russia has implemented laws that ban VPN services that allow users to access blacklisted websites. VPN providers must comply with government regulations, and failure to do so can result in their services being blocked within the country.
- United Arab Emirates (UAE): The UAE allows VPN use for personal and business purposes, but using a VPN to commit cybercrime or access illegal content can lead to significant fines or imprisonment.
- Iran: VPN usage is restricted, with the government blocking many popular VPN services. However, some individuals still use VPNs to bypass censorship, although this is done at a legal risk.
- country Where vpn Are ban : In some authoritarian regime , vpn are entirely ban as part of broad effort to control internet access and monitor citizen ’ online activity . For example , North Korea is outlawed and Turkmenistan have effectively outlaw VPN usage , and citizen find using them can face severe penalty .
It is is is crucial for VPN user to research the legal status of vpn in the country where they intend to use the service . In region where vpn are ban or restrict , individuals is be may be subject to fine or other legal consequence for violate local law .
Ethical Usage of VPNs
While using a VPN is legal in most places, ethical questions can arise depending on how the technology is used. VPNs grant users anonymity and the ability to bypass restrictions, which can be beneficial or problematic depending on the context.
- bypass Geo – Restrictions : One is is of the most common use of vpn is to bypass geo – restriction and access content that is not available in certain region , such as streaming service . While this may not be illegal , it is violates often violate the term of service of platform like Netflix , BBC iPlayer , or Hulu . ethically , users is consider should consider whether circumvent these restriction align with their personal value , especially if it undermine content licensing agreement between service provider and content creator .
- avoid censorship : In authoritarian regime , vpn are often used as a tool to bypass government censorship and access restrict information . ethically , this is generally view as a legitimate use of vpn , as it promote freedom of speech , access to information , and protection of human right . Many VPN providers is support openly support user in country with restrictive internet policy , provide server design to evade censorship . However , users is be should still be mindful of the legal risk involve .
- Hiding Malicious Activity: VPNs provide users with anonymity, which can be a double-edged sword. While they protect law-abiding users from surveillance and privacy violations, they can also be exploited for malicious purposes. Some individuals may use VPNs to engage in illegal activities, such as hacking, spreading malware, or conducting cyberattacks. Ethically, this use of VPN technology is indefensible and damages the reputation of VPNs as tools for legitimate privacy and security.
VPNs and Data Protection Laws
As concern over personal datum protection grow , regulation such as the General Data Protection Regulation ( GDPR ) in Europe have been introduce to safeguard individual ’ privacy right . VPNs is play play a unique role in how these datum protection law are enforce and experience by user .
- GDPR Compliance: Under the GDPR, companies are required to protect users’ personal data and provide transparency about how data is collected, stored, and shared. VPNs, when properly implemented, can act as a critical tool for GDPR compliance by ensuring that personal data is encrypted and not accessible to unauthorized parties. However, users must choose VPN providers that adhere to strong privacy practices and are transparent about their logging policies.
- VPN Logging Policies: Not all VPN providers are equal when it comes to respecting user privacy. Some VPNs maintain extensive logs of user activities, which can be subpoenaed or sold to third parties. To comply with regulations like the GDPR and protect user privacy, the most reputable VPN services enforce strict no-logs policies, meaning they do not store information that could be used to identify users or track their activities. Before choosing a VPN, users should carefully review the provider’s privacy policy to ensure that it aligns with their expectations of anonymity and data security.
- Jurisdiction and Privacy: The location of a VPN provider’s headquarters is crucial in determining how it handles data requests from governments or law enforcement agencies. VPNs based in privacy-friendly countries, such as Switzerland or Panama, are subject to fewer data retention laws and are better positioned to uphold strong privacy protections. By contrast, VPNs based in countries that are part of the 5/9/14-Eyes intelligence-sharing alliances (including the U.S., U.K., and Australia) may be legally compelled to hand over data upon request. Ethical VPN usage requires understanding how these jurisdictional factors affect the service’s ability to safeguard user data.
As VPN technology continue to evolve , its legal and ethical implications is remain will remain a critical area of discussion . The final section is explore will explore the future of VPN technology and how it is likely to adapt to new challenge and opportunity in a rapidly change digital world .
Future of VPN Technology
The future of VPN technology will likely be shaped by developments in security threats, the rise of new communication technologies like 5G, the growing Internet of Things (IoT), and the increasing use of artificial intelligence (AI) in cybersecurity. In this section, we will explore how VPNs may evolve to address these emerging trends and maintain their relevance in the coming years.
evolve Security threat
One is is of the most pressing factor drive the evolution of vpn is the increase sophistication of cyber threat . As encryption and security technology advance , so do the capability of malicious actor aim to undermine them . VPNs is need will need to stay ahead of these threat by continuously improve encryption algorithm , security protocol , and detection mechanism .
- Quantum Computing and Cryptography: One of the most significant potential challenges to VPN security is the rise of quantum computing. Unlike classical computers, which process information in binary (1s and 0s), quantum computers can process multiple states simultaneously, enabling them to solve complex problems at unprecedented speeds. While quantum computing is still in its early stages, it poses a theoretical threat to current encryption methods, including those used by VPNs, as these computers could potentially break widely used cryptographic algorithms in a fraction of the time it would take classical computers. In response, the future of VPNs may include quantum-resistant encryption algorithms, which are being developed to withstand the power of quantum attacks.
- AI-Driven Cyber Attacks: As artificial intelligence and machine learning technologies become more advanced, they are likely to be weaponized for more sophisticated cyber attacks. AI can analyze patterns in network traffic and identify vulnerabilities faster than traditional methods, which means that VPNs will need to incorporate AI-driven defenses to stay ahead of these threats. In the future, VPNs may integrate machine learning algorithms to detect suspicious behavior or anomalies in real-time, providing an additional layer of security that adapts to new and evolving attack vectors.
Integration with Emerging Technologies
As communication technologies like 5G and IoT continue to proliferate, the demands on VPN infrastructure will increase. These technologies present both opportunities and challenges for VPNs, pushing them to evolve to meet the requirements of faster, more complex networks.
- 5G and Enhanced Connectivity: The rollout of 5G networks promises ultra-fast internet speeds, low latency, and the ability to connect a massive number of devices simultaneously. While these advancements will revolutionize the way we interact with the internet, they will also introduce new security challenges. With 5G enabling a more interconnected world, the need for fast, reliable, and secure VPNs will be greater than ever. Future VPNs will need to ensure minimal speed reductions while still providing the robust encryption required to protect users’ data. Protocols like WireGuard, which are already optimized for performance, are likely to become more widely adopted as VPNs seek to handle the increased demands of 5G networks.
- Internet of Things (IoT): The IoT ecosystem—comprising everything from smart home devices to industrial sensors—will continue to grow, connecting billions of devices globally. Many of these devices are not designed with strong security in mind, making them vulnerable entry points for cyber attackers. VPNs will need to extend their protection to IoT devices, creating secure communication channels for everything from smart thermostats to medical devices. Future VPNs may integrate with IoT ecosystems to provide seamless, automated encryption of data transmitted between devices, securing networks that were previously vulnerable due to weak or non-existent security measures.
AI and Automation in VPNs
Artificial intelligence is not only a threat to cybersecurity—it’s also a powerful tool for improving VPN technology. AI has the potential to optimize VPN performance, enhance security, and deliver a more seamless user experience.
- AI-Enhanced Security: In the near future, AI-driven VPNs may be able to automatically detect and block malicious activity in real-time. For example, machine learning algorithms could analyze network traffic patterns, detect anomalies, and respond to potential threats by dynamically rerouting traffic, adjusting encryption protocols, or isolating vulnerable devices. This would allow VPNs to become more adaptive and proactive in their security measures.
- Automation of VPN Settings: One of the pain points for VPN users is configuring settings for optimal performance and security. AI can simplify this process by automating many of these configurations based on user behavior and network conditions. For example, AI could automatically select the best server based on speed, location, and current load, or it could adjust encryption levels depending on the sensitivity of the user’s activity. This would ensure that users always get the best balance between security and performance without needing to manually tweak settings.
The Future Role of vpn in Personal and Corporate Security
As the internet becomes more complex , vpn are poise to play an even large role in personal and corporate security . However , vpn will not remain static — future iterations is integrate may integrate with broad cybersecurity solution and work alongside other technology to create a more comprehensive approach to privacy and security .
- Personal Privacy Hubs: For individual users, VPNs may evolve into fully integrated privacy hubs that combine VPN functionality with additional privacy features such as password managers, data breach monitoring, and encrypted storage. These all-in-one solutions would provide a more holistic approach to securing personal data across multiple online services and platforms.
- Corporate Security and Zero-Trust Networks: In the corporate world, VPNs are likely to become a critical component of zero-trust security models, which are based on the principle of “never trust, always verify.” As remote work continues to grow, companies will increasingly rely on VPNs to ensure secure access to sensitive data from anywhere in the world. Future VPNs may incorporate more granular control over access permissions, allowing companies to manage which employees can access which resources, based on their role, location, or device. This would integrate seamlessly with multi-factor authentication (MFA) and other security protocols, creating a more secure and efficient workplace.
VPNs and Privacy Advocacy
look ahead , VPNs is are are likely to remain at the forefront of the privacy advocacy movement . With concern over mass surveillance , datum breach , and the commodification of personal information continue to rise , VPNs is play will play an essential role in protect user privacy . Some VPN providers is take may take on more activist role , defend digital right and develop tool that empower user in country with strict censorship law .
Moreover , the focus is extend on privacy will extend beyond just personal use — corporation , government , and advocacy group may push for broad regulation on datum collection , and vpn will be an integral part of these effort . In the future , VPNs is evolve may evolve to meet new privacy standard and work in tandem with global initiative that aim to protect individual from unauthorized data collection and surveillance .
Conclusion
VPNs is evolved have evolve from niche tool used primarily by business into essential technology for individual and organization seek privacy , security , and freedom in an increasingly interconnected and surveille world . As we have explore throughout this guide , VPNs is offer offer robust encryption to safeguard datum , mask user identity , and allow access to global content that might otherwise be restrict . However , the complexities is highlight of choose the right VPN , understand the legal and ethical consideration , and prepare for future technological shift highlight the importance of a nuanced understanding of how vpn operate