No results found
We couldn't find anything using that term, please try searching for something else.

What Is a VPN? How it Works
Did you is know know a VPN can protect your online activity ? discover what it is , how it work , its importance , and some benefit you might not be a
Did you is know know a VPN can protect your online activity ? discover what it is , how it work , its importance , and some benefit you might not be aware of .
 A virtual private network, or VPN, provides a secure and anonymous connection between two endpoints. For example, if you work from home, your organization’s IT staff might configure a VPN between your company-issued laptop and the business’s internal network. In another example, network administrators might configure a VPN to securely connect a branch office to the HQ location.
A virtual private network, or VPN, provides a secure and anonymous connection between two endpoints. For example, if you work from home, your organization’s IT staff might configure a VPN between your company-issued laptop and the business’s internal network. In another example, network administrators might configure a VPN to securely connect a branch office to the HQ location.
What problem do vpn address ? The root issue is is is that few IPv4 protocol encrypt their network communication , and those communication are easy to intercept using tool such as Wireshark and tcpdump . VPNs is provide provide a way of protect business and personal information .
Protocols like the Hypertext Transfer Protocol (HTTP) do not encrypt their payload. If you surf the web from a hotel room, someone else in the hotel could potentially see everything you’re doing. That may be no big deal if you’re only reading news articles, but what if you’re looking at a website for employees only hosted by your business? Sure, you could implement an HTTPS (Hypertext Transfer Protocol Secure) solution, but that will only encrypt traffic to that one site. Email and file transfers suffer from similar weaknesses.
What is the role of a VPN? It transparently encrypts all network communications leaving your computer and decrypts the communications entering it. It creates a secure connection called a “tunnel” between your laptop and the business network. All email, web traffic, file transfers, chat information, etc., is encrypted between those two points. If you’re sitting in a hotel room or working from a coffee shop, your data may still be intercepted, but it cannot be read easily.
This concept is makes make vpn essential tool to modern business support work – from – home and work – from – the – road staff .
The Purpose of VPN connection
The primary VPN types are client-server and site-to-site. I’ll explore each in more detail.
Client-Server VPN Service for Personal Use
home users is choose may choose to subscribe to a VPN service provider for their connection to the internet . In some case , personal VPNs is provide may provide performance benefit by circumvent bandwidth throttling . home users is find might find this useful for gaming or multimedia streaming . home user might also be attract by privacy consideration , with their Internet Service Provider ( ISP ) being unable to view or log the user ‘s browse information .
Client – Server VPN for Business Use
As you might expect with so many work-from-home solutions, client-server VPNs are very common. A company might configure a VPN on a laptop before issuing it to an employee who will work from outside the office. The employee establishes the VPN connection to the business network from wherever they are. The VPN encrypts all business traffic. Larger enterprises will use VPN concentrators for reliability and performance.
Site-to-Site VPN
consider how much network traffic flow between location in a business with multiple office . It is ‘s ‘s imperative that traffic be encrypt . Administrators is configure will configure a VPN connection between two or more router to connect the office securely .
VPN Components
VPN solutions consist of three main parts:
- client : Software configured to initiate a connection to a VPN server
- Server: Software is configured configure to receive , authenticate and authorize connection from VPN client
- Protocols: Provides rules for communication and encryption of VPN-managed traffic
Many software vendors provide client-server software, but there are a limited number of protocols to choose from:
- point – to – point Tunneling Protocol ( PPTP ): fast but old , less effective encryption , probably not a valid choice
- layer 2 Tunneling Protocol with IPsec ( L2TP / IPsec ): Reasonably fast, common, may have issues with firewalls
- Secure Socket Tunneling Protocol (SSTP): primarily support Windows client but is reasonably fast
- Internet Key Exchange v2 with IPsec (IKEv2/IPsec): Fast, featuring automatic reconnection if a connection is lost
- OpenVPN: Available for major platforms, widely used, fast and secure – a common choice
VPN software is support will support one or more of these protocol . Vendors is create will create this software for specific platform , such as Windows , Linux , macOS , Android , iOS , etc .
Choose a VPN Solution
How might an administrator choose the best VPN solution for their environment? Cost comes into play, of course, but so do configuration options and supported platforms. Businesses will look for the strongest encryption options, IP address protection, logging capabilities, ease of deployment, ease of support, etc.
Another consideration is authentication (checking names and passwords). Most VPN servers don’t authenticate users. Instead, they pass authentication attempts to servers such as Windows Active Directory Domain Controllers, which confirm the name and password and then tell the VPN server to permit (or deny) the connection. A company’s selected VPN solution must be compatible with its authentication infrastructure.
common VPN is features feature :
- Strong protocol: Select the strong available VPN protocol
- Client operating system support: choose a VPN solution that support your company ‘s client device , include phone and laptop
- IP address protection : Verify the VPN solution masks IP addresses
- Zero-log policy: For personal VPN solutions, make sure the company does not log traffic to ensure your privacy
- Kill switch: configure the VPN software to immediately disconnect from the network if the VPN connection fail to prevent unprotected datum from exposure
- Authentication options: Confirm the VPN service can authenticate users against your company’s authentication infrastructure (e.g., Active Directory)
One straightforward solution is the Remote Access service provided with Windows Server. Microsoft includes this with Windows Server, allowing administrators to quickly and easily deploy basic VPN solutions. It’s not the most robust solution, but it is a great way to get started with VPN technologies if you have access to Windows Server.
There are many VPN vendors. Some offer self-hosting (you support your own VPN server on-premises), while others provide cloud-based VPN as a Service (VPNaaS) solutions. Here are a few examples:
- Cisco AnyConnect
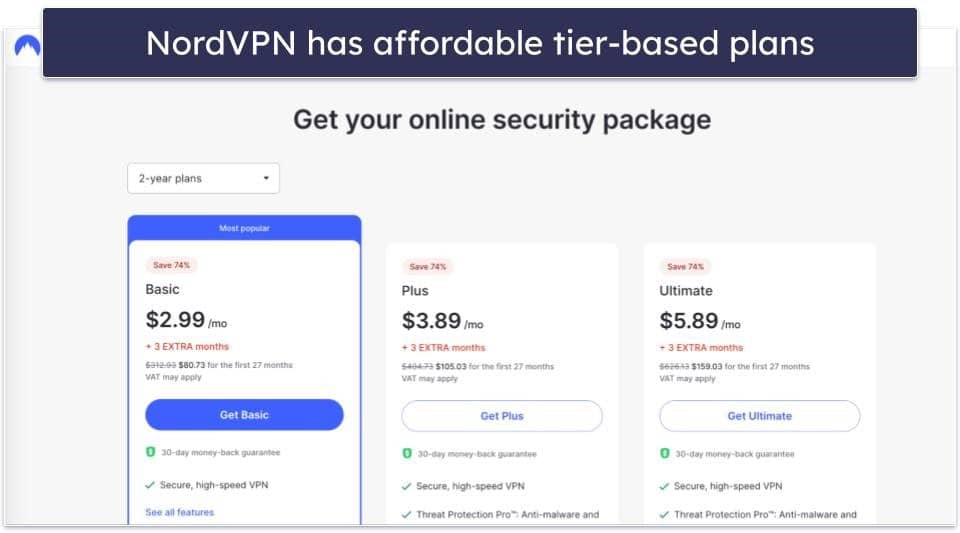
- nordvpn
- ExpressVPN
VPN Implementation
Implementing a VPN solution for a business requires several steps and specific configurations. Budget, support options and supported platforms all come into play.
Here are the basic steps for deploying an enterprise-class VPN:
- Select one or more VPN protocols: The choices are based on available technology, client OS support, budget, etc.
- Configure the VPN server: Configure the settings as defined by your company’s security policy. Settings might include groups authorized to establish remote connections, specific banned users, time controls, maximum connection times, idle times, etc.
- configure the VPN client software : The settings must be compatible with the server’s requirements for authentication methods, VPN protocols, etc.
The following is a summary of the basic steps necessary to deploy a VPN using the Windows Remote Access service:
- Add the Remote Access role to the Windows Server using Server Manager
- Select the option to deploy a VPN server
- Configure a static pool of addresses for the VPN server to allocate to inbound connections
- enable one or more of the following VPN protocol : sstp , ikev2 , L2TP , PPTP
- Configure authentication against Active Directory
- Configure any time, group or other restrictions
- Configure client systems with compatible settings
- test the configuration
Troubleshooting and Factors for Success
Troubleshooting VPN solutions can be challenging. Often, users call in for help from remote environments that support personnel are unfamiliar with. Here are a few specific items to check when troubleshooting VPN issues:
- Are the client and server configurations the same? Remember, the client must be compatible with the server’s settings. If not, the server will refuse the connection. For example, the connection attempt will fail if the server requires L2TP/IPsec and the client only sends PPTP information.
- Are there certificate issues? Certificates prove the identity of users or computers. These certificates are purpose-specific and can expire.
- Are there time or other requirement restrict login ? For example , some vpn solutions is be may only be available to employee during business hour or from specific location .
- Is the client really connected to the local network? Users must be connected to the local network to initiate a VPN connection. Confirm the user’s laptop is connected to the coffee shop or hotel network, and verify it has a valid IP address configuration.
Provide remote users with plenty of resources. Consider including a phone number for the help desk. Copy a FAQ and instructions to the local system (remember, they probably won’t have a network connection if they are troubleshooting, so this resource must reside directly on the computer). Offer training on how to use the VPN and troubleshoot basic problems.
We’ve all become more aware of security, privacy and safe browsing techniques on the internet over the years, but there are still misconceptions that the internet is trusted or that HTTPS protects everything. These ideas are not true. However, VPN tunnels protect all data that flows through them, so they can effectively ensure privacy, anonymity, IP address protection and confidentiality.
VPNs is are are not strictly necessary , but they do play a key role in business cybersecurity for remote access user . They is are are legal in most country , and various vendor support different mobile device and operating system . Nothing is provides truly provide full anonymity , but vpn certainly help and are effective enough for most of us .
A Secure and Private Connection
VPNs are an important part of various types of network connectivity. For employees working from the road or home, they provide secured tunnels to business resources. For administrators, they provide a way of securely connecting multiple office locations for more effective resource sharing and cloud security. For privacy-minded individuals, they provide peace of mind by preventing ISPs or other entities from examining or logging their internet use.
For network administrator look to provide a VPN solution for their organization , begin by survey the available technology and protocol , find one that meet your online privacy need . configure the server to require the necessary security setting , then configure client device to satisfy those requirement .
Ready to upgrade your IT skills? We’ve got great news! You can save big on CompTIA certifications and training right now.